Epiceditor – Cross-Site Scripting(CVE-2017-6589)
EPSS
Percentile
77.7%
EpicEditor Introduction
EpicEditor is an embeddable JavaScript Markdown editor with split fullscreen editing, live previewing, automatic draft saving, offline support, and more. For developers, it offers a robust API, can be easily themed, and allows you to swap out the bundled Markdown parser with anything you throw at it.
The project url:https://github.com/OscarGodson/EpicEditor
Causes of Vulnerability
EpicEditor uses marked.js(https://github.com/chjj/marked) to render the page, but does not filter the input tags, resulting in an XSS vulnerability.
TEST version
EpicEditor-0.2.2
Vulnerability reproduction
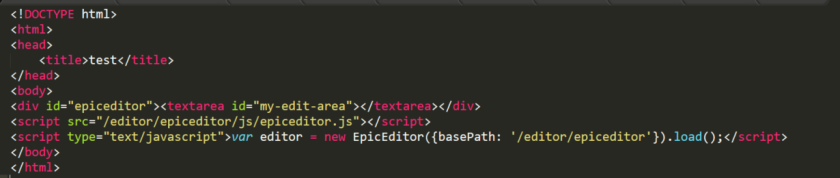
Create new test.html, reference edipeditor.js
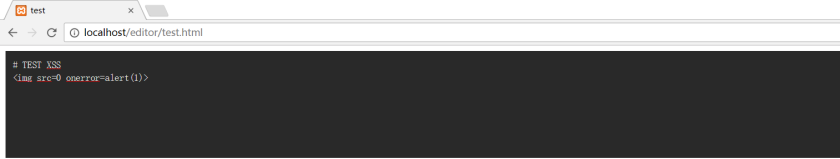
And then visit test.html, in the editor,<img src>, click on the preview, the results as shown below
Bug fixes
marked.defaults = {
gfm: true,
tables: true,
breaks: false,
pedantic: false,
sanitize: false,
silent: false,
highlight: null
};
Set sanitize to true, or call marked.setOptions ({sanitize: true}) in the previous render;