WordPress Database Reset Plugin Vulnerability (CVE-2020-7047, CVE-2020-7048)
0.007 Low
EPSS
Percentile
80.8%
A vulnerability recently disclosed by Wordfence and published as CVE-2020-7047 and CVE-2020-7048 allows an attacker to take over vulnerable WordPress-based websites.
Functionality in the WP Database Reset plugin introduced the vulnerability, which allows any unauthenticated user to reset any table in the database to its initial state when it was installed, deleting all the content in the database.
Details about the vulnerability can be found at CVE-2020-7047 and CVE-2020-7048.
It is also possible for an attacker to completely take over the target application. Given that all the data can be deleted from the database, an attacker can delete the designated WordPress admin and take over the role and become administrator of the website.
The vulnerability affects the WordPress Database Reset plugin versions prior to 3.15.
About the WordPress Database Reset Plugin
WordPress is a popular content management system (CMS). It is designed to emphasize accessibility, performance, security, and ease of use. The WordPress plugin, WP Database Reset, is used to reset databases used by WordPress installations. The plugin gives users the option of not having to go through the WordPress installation in order to reset the database.
Detecting the Vulnerability with Qualys WAS
Qualys has published QID 150274 for Qualys Web Application Scanning (WAS) that implements a passive detection of vulnerabilities present in the affected WordPress plugin.
QID 150274 : WordPress Database Reset Plugin Vulnerability
Remediation
To remediate the vulnerabilities, upgrade to latest version of the WP Database Reset plugin.
Protection with Qualys WAF
If you’re unable to upgrade the plugin and are a Qualys Web Application Firewall (WAF) customer, you can create custom rules to detect and block attacks that try to exploit this vulnerability.
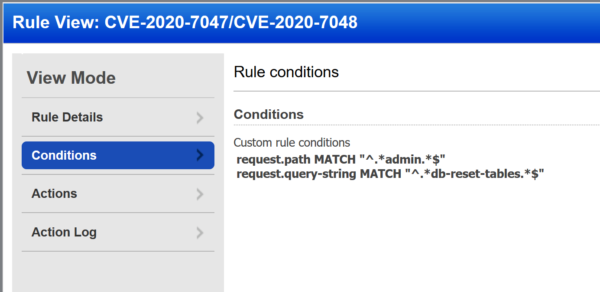
Specifically, set these two conditions:
request.path MATCH "^.*admin.*$"
request.query-string MATCH "^.*db-reset-tables.*$"
And then set Actions to “Block & Log”, and attach the rule to the vulnerable app.
For more information, refer to Custom Rules in the Qualys WAF Getting Started Guide.