
Microsoft and Adobe Patch Tuesday, May 2023 Security Update Review
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.6 High
CVSS2
Access Vector
NETWORK
Access Complexity
HIGH
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:H/Au:N/C:C/I:C/A:C
0.396 Low
EPSS
Percentile
96.7%
Microsoft has addressed 49 vulnerabilities in its May Patch Tuesday edition. The security advisories cover various vulnerabilities in different products, features, and roles. Let's guide you through this month's Patch Tuesday details.
Microsoft Patch Tuesday for May 2023
Microsoft has also addressed twozero-day vulnerabilities known to be exploited in the wild. Sixof these 49 vulnerabilities****are rated as critical and32as important. In this month's Patch Tuesday, security updates addressed11 vulnerabilities in Microsoft Edge (Chromium-based).
This month's Patch Tuesday edition includes updates for vulnerabilities in Microsoft Office and Components; Microsoft Graphics Component, Microsoft Bluetooth Driver, Windows Secure Boot, Windows Secure Socket Tunneling Protocol (SSTP), Windows LDAP - Lightweight Directory Access Protocol, Windows Win32K, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The May 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 1 | Important: 1 |
| Denial of Service Vulnerability | 5 | Important: 5 |
| Elevation of Privilege Vulnerability | 8 | Important: 8 |
| Information Disclosure Vulnerability | 8 | Important: 8 |
| Remote Code Execution Vulnerability | 12 | Critical: 6 |
| Important: 6 | ||
| Security Feature Bypass Vulnerability | 4 | Important: 4 |
| Microsoft Edge (Chromium-based) | 11 |
Adobe Patches for May 2023
Adobe has released only one security advisory for May. The advisory addresses 14 critical and important vulnerabilities in Adobe Substance 3D Painter. Successful exploitation of the vulnerabilities could lead to arbitrary code execution and memory leaks in the current user's context.
Zero-day Vulnerabilities Patched in May Patch Tuesday Edition
CVE-2023-29336: Win32k Elevation of Privilege Vulnerability
The vulnerability exists in Win32k, a Windows Core Library, and is known to be exploited in the wild. An attacker with local access may exploit this vulnerability in a low-complexity attack without needing any privileges. An attacker could gain SYSTEM privileges on the affected system after successful exploitation.
CISA has added the CVE-2023-29336 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before May 30, 2023.
CVE-2023-24932: Secure Boot Security Feature Bypass Vulnerability
Secure Boot is a crucial security feature that helps prevent malicious software from loading while the computer boots. This security standard maintains computers' safety by ensuring that the device boots only using trusted software provided by the Original Equipment Manufacturer (OEM).
An attacker with physical access or administrative permissions to a target device may exploit this vulnerability to install an affected boot policy. On successful exploitation, an attacker can bypass the Secure Boot.
Other Critical Severity Vulnerabilities Patched in May Patch Tuesday Edition
CVE-2023-28283: Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
The Lightweight Directory Access Protocol (LDAP) operates a layer above the TCP/IP stack. The directory service protocol helps connect, browse, and edit online directories. The LDAP directory service is based on a client-server model that enables access to an existing directory. LDAP stores data in the LDAP directory and authenticates users to access the directory.
An unauthenticated attacker must win a race condition to exploit this vulnerability. On successful exploitation, an attacker could perform remote code execution within the context of the LDAP service with the help of a specially crafted set of LDAP requests.
CVE-2023-24941:** **Windows Network File System Remote Code Execution Vulnerability
Network File System (NFS) offers a file-sharing solution for enterprises with heterogeneous environments, including Windows and non-Windows computers. The NFS protocol helps transfer files between Windows computers, Linux or UNIX.
The vulnerability affects the NFSV4. A local attacker with network access can exploit this vulnerability by making an unauthenticated, specially crafted call to a Network File System (NFS) service that triggers remote code execution.
CVE-2023-24903**:**Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability
Secure Socket Tunneling Protocol (SSTP) is a type of virtual private network (VPN) tunnel. The protocol helps to transport PPP traffic through an SSL/TLS channel. SSL/TLS provides transport-level security with encryption and traffic integrity checking.
An attacker must win a race condition to exploit this vulnerability. To exploit this vulnerability, an attacker may send a specially crafted malicious SSTP packet to an SSTP server. On successful exploitation, the attacker may perform remote code execution on the server side.
CVE-2023-24943: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Pragmatic General Multicast (PGM) is a multicast computer network transport protocol appropriate for multi-receiver file transfer applications. PGM provides a reliable sequence of packets to multiple recipients simultaneously.
Only PGM Server is vulnerable to this flaw. When the Windows Message Queuing service runs in a PGM Server environment, an attacker may send a specially crafted file over the network to achieve remote code execution and trigger malicious code.
CVE-2023-29325: Windows OLE Remote Code Execution Vulnerability
OLE (Object Linking and Embedding) is a mechanism to help users create and edit documents containing "objects" made by multiple applications. Sound clips, spreadsheets, and bitmaps are examples of OLE document components.
There are two prerequisites for the exploitation of this vulnerability:
- Winning a race condition
- Taking additional actions before exploitation to prepare the target environment.
An attacker could exploit this vulnerability in an email attack by sending a specially crafted email. A user may be tricked into opening a specifically crafted email using an affected version of Microsoft Outlook, or a victim's Outlook application could preview a specially crafted email. As a result, an attacker may perform remote code execution on the victim's computer.
CVE-2023-24955: Microsoft SharePoint Server Remote Code Execution Vulnerability
Microsoft SharePoint is a web-based document management and collaboration platform that strengthens teamwork. The application helps in sharing files, data, news, and resources.
An attacker is required to authenticate as a Site Owner to exploit this vulnerability. The vulnerability will allow an attacker to perform remote code execution on the SharePoint Server.
Other Microsoft Vulnerability Highlights
- CVE-2023-24902, an elevation of privilege vulnerability in Win32k that may allow an attacker to gainSYSTEM privileges on successful exploitation.
- CVE-2023-24949, Windows kernel elevation of privilege vulnerability with which an attacker could gainSYSTEM privileges on affected systems.
- CVE-2023-24950, the spoofing vulnerability, allows a privileged attacker to create a site on a vulnerable SharePoint server. An attacker may cause the server to leak its NTLM hash on successful exploitation.
- CVE-2023-24954, an authenticated attacker may exploit this vulnerability to disclose user tokens and other potentially sensitive information. An attacker could gain the Domain SID prefix for the targeted site on successful exploitation.
- CVE-2023-29324, the elevation of privilege vulnerability in MSHTML, a browser engine that renders web pages frequently connected to Internet Explorer. Even though the Internet Explorer (IE) 11 desktop application has reached the end of support, MSHTML vulnerabilities are still very much relevant today because the legacy browser engine is still used in various Windows applications. An attacker must take additional actions before exploitation to prepare the target environment. On successful exploitation, an attacker could gainAdministrator privileges.
Microsoft Release Summary
This month's release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Microsoft Teams, Windows SMB, Windows NTLM, Windows NFS Portmapper, Windows Installer, Remote Desktop Client, Reliable Multicast Transport Driver (RMCAST), Windows Network File System, Windows Remote Procedure Call Runtime, Windows iSCSI Target Service, Windows Backup Engine, Windows Kernel, Windows RDP Client, Windows MSHTML Platform, Windows OLE, Visual Studio Code, Microsoft Windows Codecs Library, and SysInternals.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:110434 OR qid:110435 OR qid:378477 OR qid:92012 OR qid:92014 OR qid:92015 OR qid:92016 OR qid:92017 OR qid:92018)
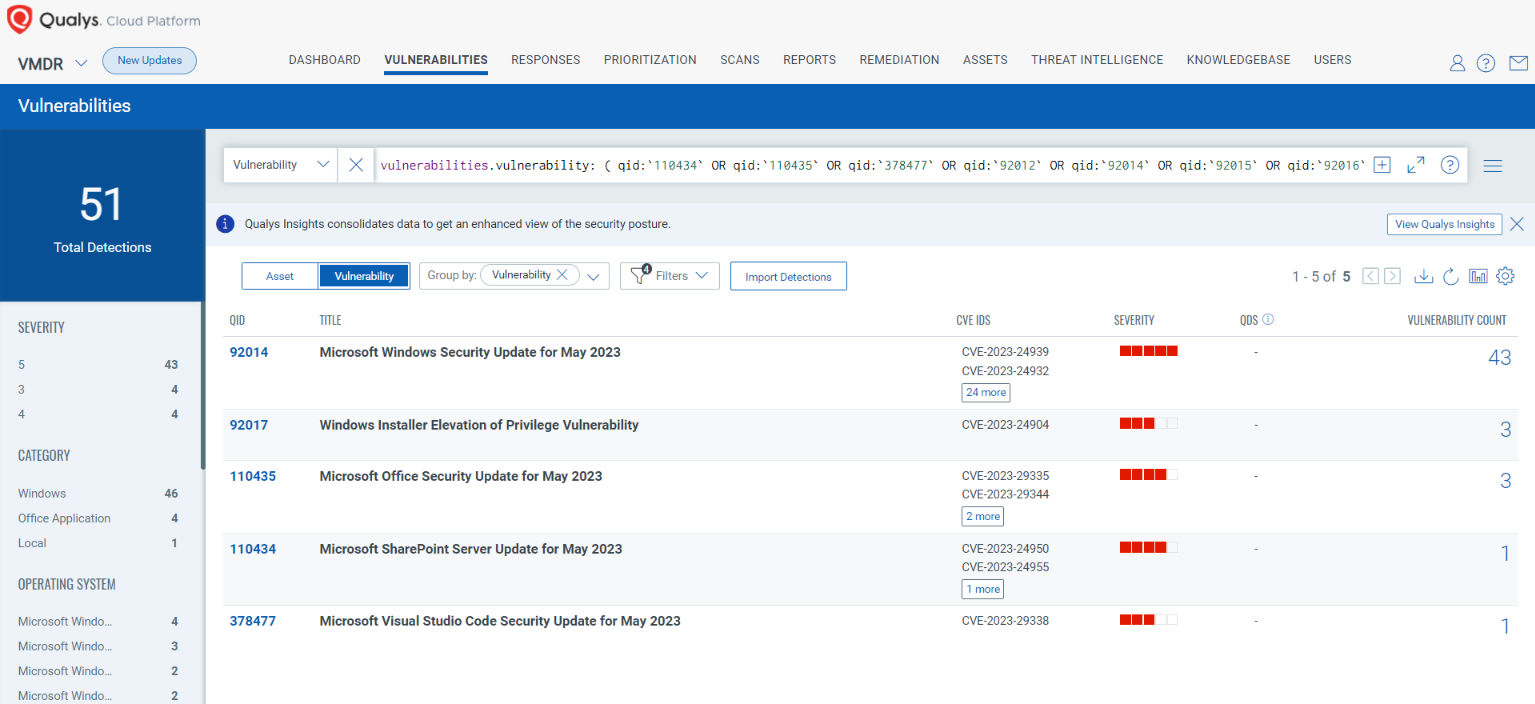
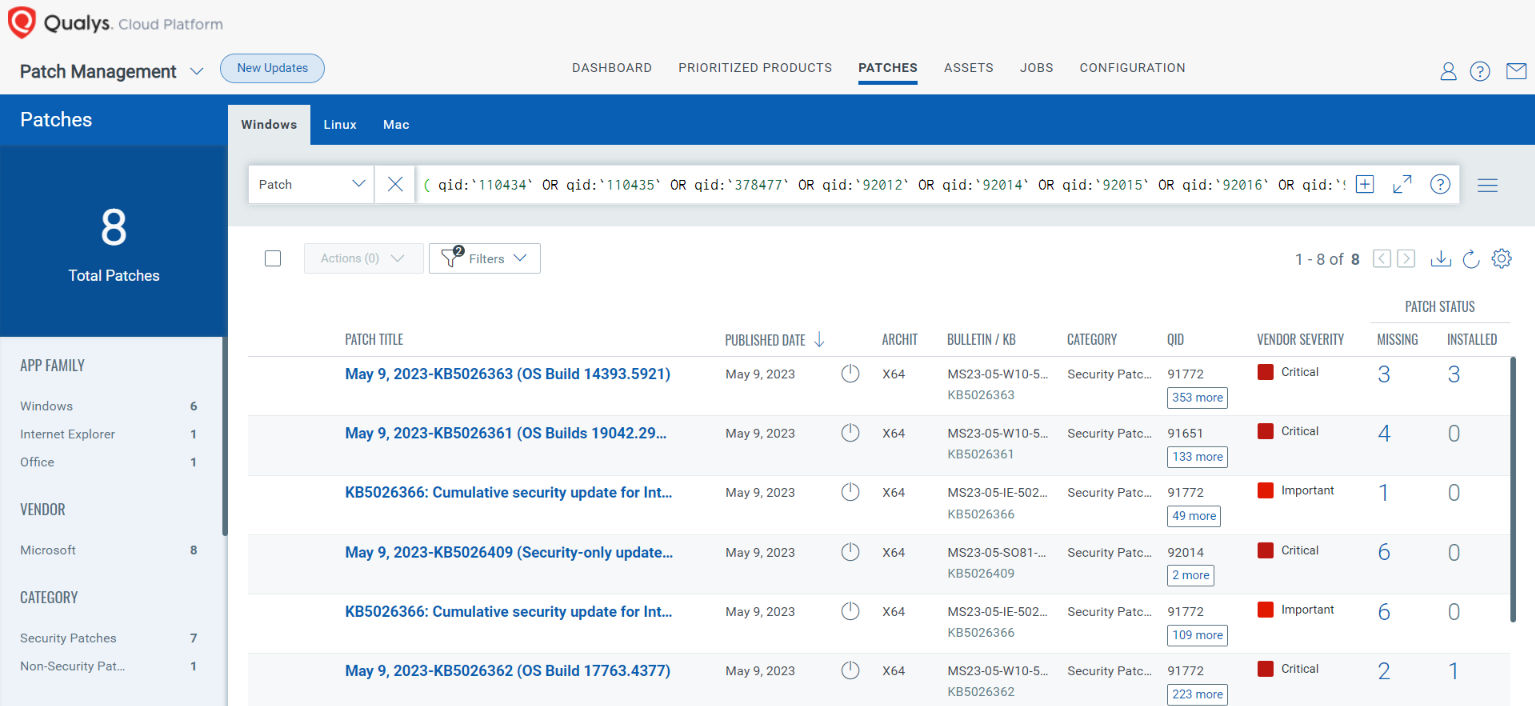
Rapid Response withPatch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:110434 OR qid:110435 OR qid:378477 OR qid:92012 OR qid:92014 OR qid:92015 OR qid:92016 OR qid:92017 OR qid:92018)
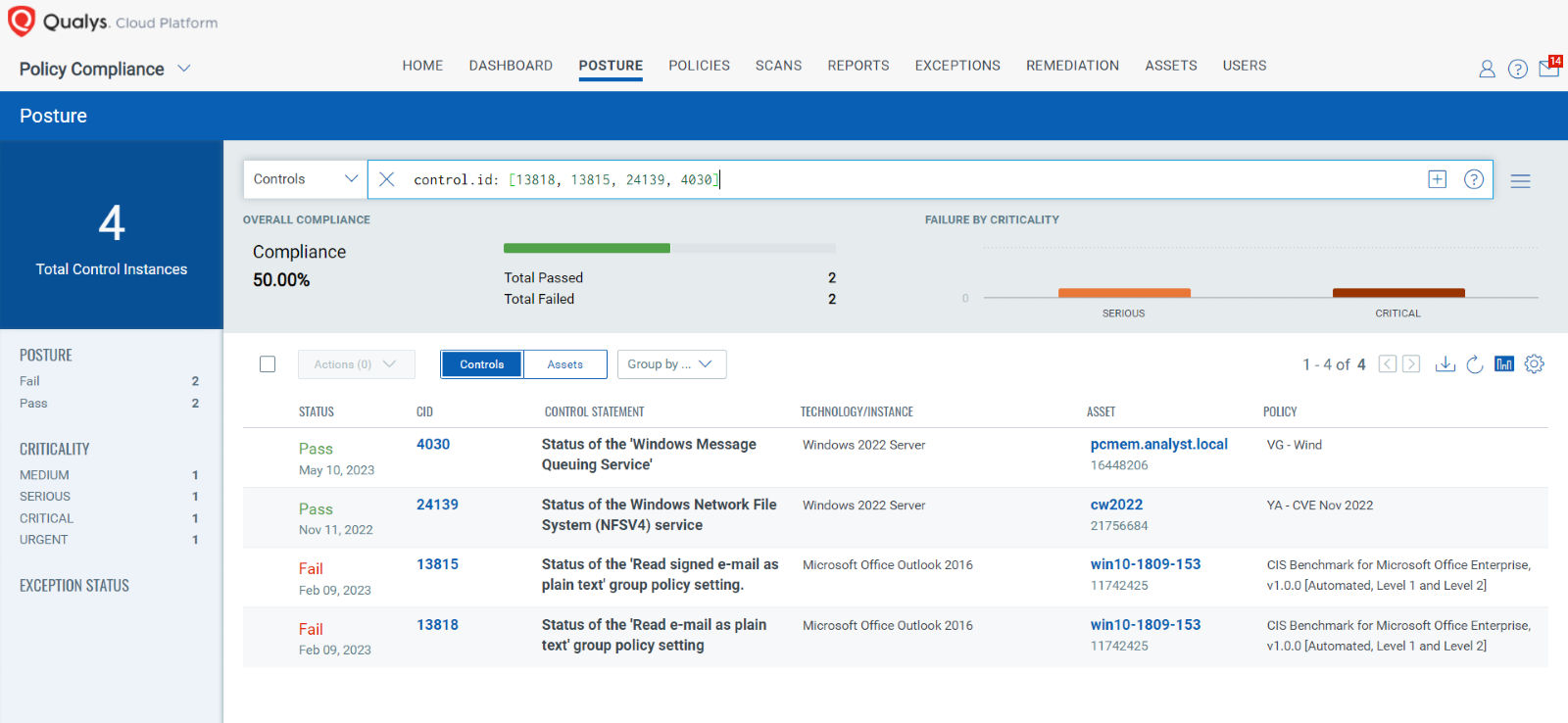
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is sometimes used temporarily for achieving a task or goal when the usual or planned method isn't working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-29325: Windows OLE Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1 / 7.3.
Policy Compliance Control IDs (CIDs):
13818 Status of the 'Read e-mail as plain text' group policy setting
13815 Status of the 'Read signed e-mail as plain text' group policy setting
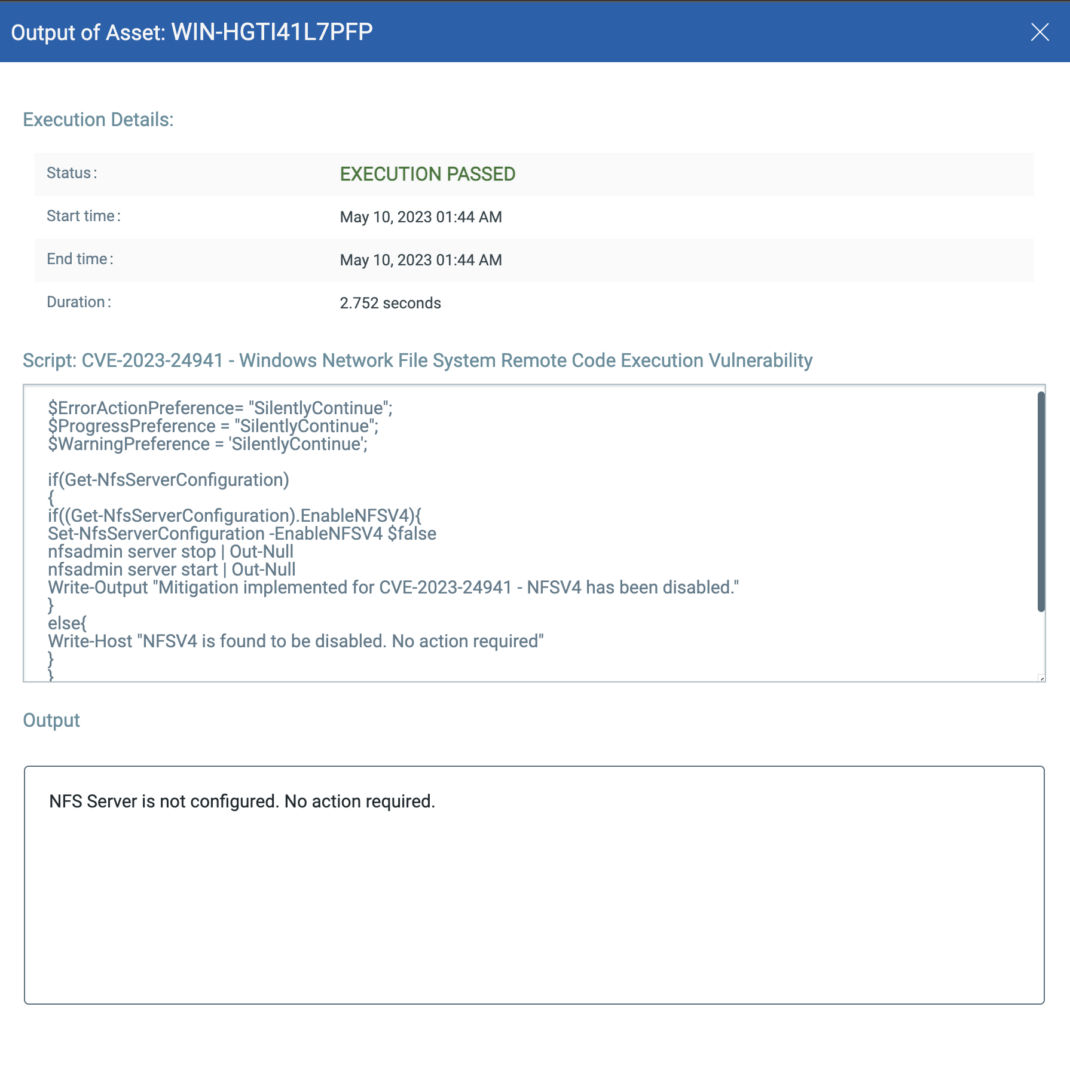
CVE-2023-24941: Windows Network File System Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8 / 8.5.
Policy Compliance Control IDs (CIDs):
24139 Status of the Windows Network File System (NFSV4) service
CVE-2023-24943: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8 / 8.5.
Policy Compliance Control IDs (CIDs):
4030 Status of the 'Windows Message Queuing Service'
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [13818, 13815, 24139, 4030]
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
CVE-2023-24932: Secure Boot Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 6.7/10.
This CVE needs a patch as well as post patch config change.
Steps for revocations:
1. Apply both revocations from the script.
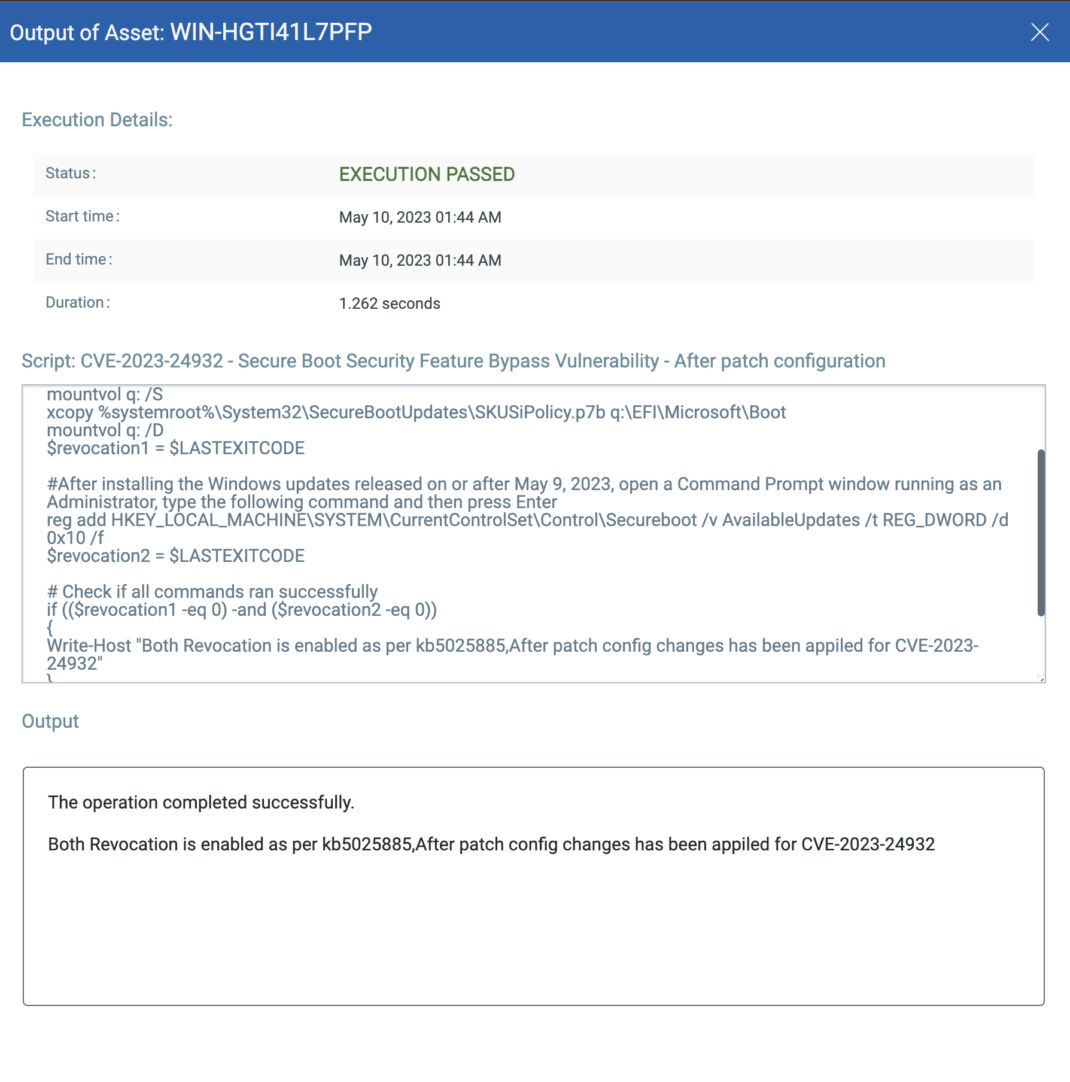
2. Restart the asset.
3. Verify the installation and revocation list from the script.
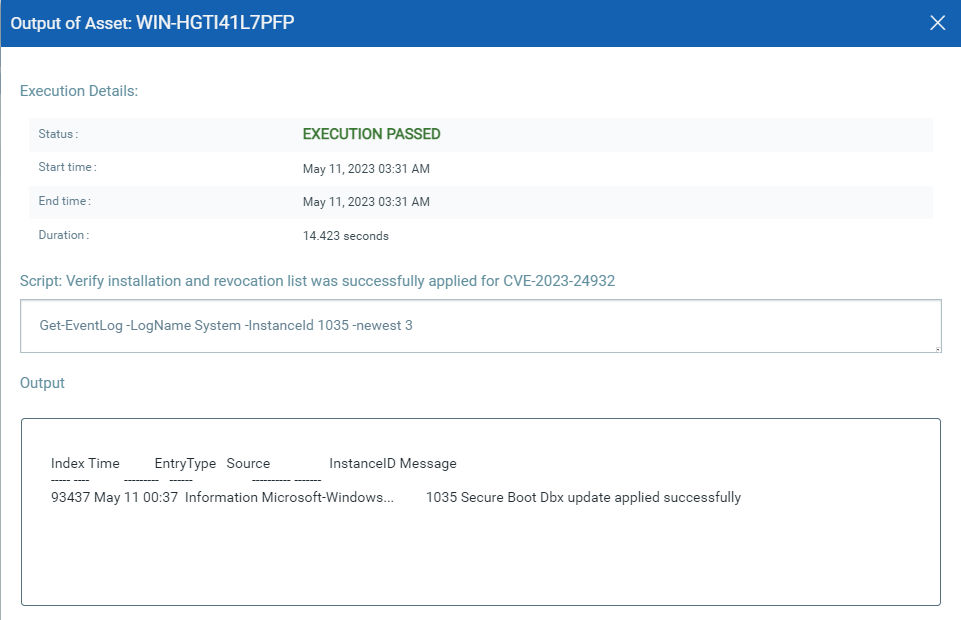
4. Wait for Five mins and then restart again.
Important: An additional restart is required to fully initialize the revocation protections.
Caution: Once the mitigation for this issue is enabled on a device, meaning the revocations have been applied, it cannot be reverted if you continue to use Secure Boot on that device. Even reformatting of the disk will not remove the revocations if they have already been applied. Please be aware of all the possible implications and test thoroughly before applying the revocations that are outlined in this article to your device.
CVE-2023-24941: Windows Network File System Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
CVE-2013-3900: WinVerifyTrust Signature Validation Vulnerability
This CVE is updated on 9 May 2023****
This vulnerability has a CVSSv3.1 score of 7.4/10.** **This CVE needs to enable **Cert Padding****Check **as per MSRC recommendation.
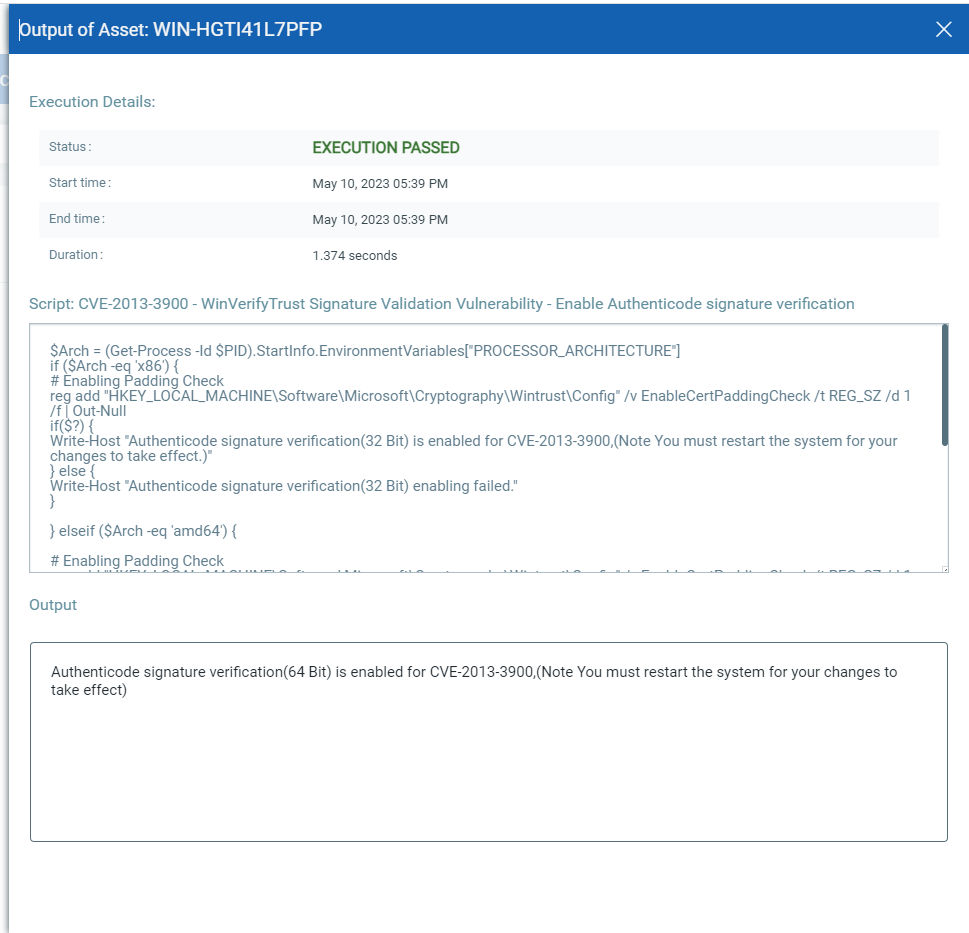
**Note:**Scripts will be available in the CAR script library.
The next Patch Tuesday falls on June 13, and we'll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the 'This Month in Vulnerabilities and Patches webinar.'
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month's high-impact vulnerabilities, including those that are part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.6 High
CVSS2
Access Vector
NETWORK
Access Complexity
HIGH
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:H/Au:N/C:C/I:C/A:C
0.396 Low
EPSS
Percentile
96.7%