
Oracle Patch Tuesday, July 2023 Security Update Review
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.863 High
EPSS
Percentile
98.1%
Oracle has released its third quarterly edition of Critical Patch Update, which contains a group of patches for 508 security vulnerabilities. Some of the vulnerabilities addressed this month impact more than one product. These patches address vulnerabilities in Oracle code and third-party components included in Oracle products.
During Q3 2023 Oracle Critical Patch Update, the Oracle Financial Services Applications received the highest number of 147 patches, constituting 29% of the total patches released. Oracle Communications and Oracle Fusion Middleware followed, with 77 and 60 patches, respectively.
449 of the 508, i.e.,88% of security patches, are for non-Oracle CVEs, which are security fixes for issues in third-party products such as open-source components included and exploitable in the context of their Oracle product distributions.
In these security updates, Oracle has covered product families, including Oracle Database Server, Oracle Application Express, Oracle Essbase, Oracle GoldenGate, Oracle Graph Server and Client, Oracle Spatial Studio, Oracle TimesTen In-Memory Database, Oracle Commerce, Oracle Communications Applications, Oracle Communications, Oracle Construction and Engineering, Oracle E-Business Suite, Oracle Enterprise Manager, Oracle Financial Services Applications, Oracle Food and Beverage Applications, Oracle Fusion Middleware, Oracle Analytics, Oracle Health Sciences Applications, Oracle Hospitality Applications, Oracle Hyperion, Oracle Insurance Applications, Oracle Java SE, Oracle JD Edwards, Oracle MySQL, Oracle PeopleSoft, Oracle Policy Automation, Oracle Retail Applications, Oracle Siebel CRM, Oracle Supply Chain, Oracle Systems, Oracle Utilities Applications, Oracle Virtualization.
Qualys QID Coverage
Qualys has released 12 QIDs mentioned in the table below:
| QIDs | Title |
|---|---|
| 378680 | Oracle Managed Virtualization (VM) VirtualBox Windows Multiple Vulnerabilities (CPUJUL2023) |
| 378679 | Oracle Managed Virtualization (VM) VirtualBox Linux Multiple Vulnerabilities (CPUJUL2023) |
| 378678 | Oracle MySQL Connector Critical Patch Update (CPU) July 2023 (CPUJULY2023) |
| 378677 | Oracle Hypertext Transfer Protocol Server (HTTP Server) Server Multiple Vulnerabilities (CPUJUL2023) |
| 378675 | Oracle Coherence July 2023 Critical Patch Update (CPUJUL2023) |
| 378673 | Oracle Java Standard Edition (SE) Critical Patch Update - July 2023 (CPUJUL2023) |
| 87546 | Oracle WebLogic Server Multiple Vulnerabilities (CPUJUL2023) |
| 296101 | Oracle Solaris 11.4 Support Repository Update (SRU) 59.138.2 Missing (CPUJUL2023) |
| 20354 | Oracle Database 19c Critical Patch Update - July 2023 |
| 20355 | Oracle Database 21c Critical Patch Update - July 2023 |
| 20356 | Oracle Database 19c Critical OJVM Patch Update - July 2023 |
| 20357 | Oracle MySQL July 2023 Critical Patch Update (CPUJULY2023) |
Note: The table will be updated with the additional QIDs once released.
Notable Oracle Vulnerabilities Patched
Oracle Financial Services Applications
This Critical Patch Update for Oracle Financial Services Applications contains 147 security patches.** 115** of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-1471, CVE-2022-46364, CVE-2022-45047, and CVE-2022-31692 in different Oracle Financial Services Applications products have the highest CVSS score of 9.8.
Oracle Communications
The Critical Patch Update for Oracle Communications contains 77 new security patches for Oracle Communications. Out of which, 57 vulnerabilities may be remotely exploitable without authentication.
CVE-2023-20862, CVE-2022-37434, CVE-2022-1471, CVE-2023-20873, and CVE-2022-36944 in different products of Oracle Communications have the highest CVSS score of 9.8.
Oracle Fusion Middleware
The Critical Patch Update for Oracle Fusion Middleware contains 60 new security patches. 40 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-42920, CVE-2022-45047, CVE-2023-25690, CVE-2021-42575, CVE-2022-41853, CVE-2021-43113, and CVE-2023-26119 in different products of Oracle Fusion Middleware have the highest CVSS score of 9.8.
Oracle MySQL
The Critical Patch Update contains 24 new security patches for Oracle MySQL. 11 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2023-20862 has the highest CVSS score of 9.8. The vulnerability affects MySQL Enterprise Monitor version 8.0.34 and prior.
Oracle Analytics
The Critical Patch Update contains 32 new security patches for Oracle MySQL. 23 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-46364, CVE-2022-29361, CVE-2019-17531, CVE-2019-13990, CVE-2022-1471, and CVE-2022-33980 in BI Publisher and Oracle Business Intelligence Enterprise Edition have the highest CVSS score of 9.8.
Oracle Communications Applications
The Critical Patch Update for Oracle Communications Applications contains 40 new security patches, and 30 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-1471, CVE-2021-42575, CVE-2022-46364, CVE-2022-31692, CVE-2023-20873, and CVE-2023-20862 in different products of Oracle Communications Applications have the highest CVSS score of 9.8.
Oracle Database Server
The Critical Patch Update for Oracle Database Products contains fivenew security patches. One of these vulnerabilities may be remotely exploitable without authentication. On the other hand, one of these patches applies to client-only installations, i.e., installations that do not have the Oracle Database Server installed.
The Oracle Database Server products and versions affected by vulnerabilities are:
- Oracle Text (LibExpat), version 21.3 through 21.10
- OML4PY (cryptography), version 21.3 through 21.10
- Java VM, version 19.3 through 19.19 and 21.3 through 21.10
Oracle Utilities Applications
The Critical Patch Update for Oracle Utilities Applications contains 14 new security patches. 12 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-1471, CVE-2023-20873, and CVE-2023-20862 in Oracle Utilities Testing Accelerator and Oracle Utilities Network Management System have the highest CVSS score of 9.8.
Oracle Supply Chain
The Critical Patch Update for Oracle Supply Chain contains 13new security patches. 11 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-37434 and CVE-2022-27404 in Oracle Agile Engineering Data Management and Oracle AutoVue have the highest CVSS score of 9.8.
Oracle Retail Applications
The Critical Patch Update contains 11new security patches for Oracle Retail Applications. 8 of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-37434 in Oracle Retail Advanced Inventory Planning has the highest CVSS score of 9.8.
Oracle Commerce
The Critical Patch Update contains 8new security patches for Oracle Commerce. All of these vulnerabilities may be remotely exploitable without authentication.
The Oracle Commerce products and versions affected by vulnerabilities are:
- Oracle Commerce Guided Search, version 11.3.2
- Oracle Commerce Platform, version 11.3.0, 11.3.1, and 11.3.2
Oracle E-Business Suite
The Critical Patch Update contains five new security patches for Oracle E-Business Suite. Three of these vulnerabilities may be remotely exploitable without authentication.
The highest CVSS Score of vulnerabilities affecting Oracle E-Business Suite is 6.5.
The Oracle E-Business Suite products and versions affected by vulnerabilities are:
- Oracle Scripting versions 12.2.3 through 12.2.12
- Oracle Applications Framework versions 12.2.3 through 12.2.12
- Oracle Applications Technology versions 12.2.3 through 12.2.12
- Oracle Self-Service Human Resources versions 12.2.3 through 12.2.12
- Oracle Web Applications Desktop Integrator versions 12.2.3 through 12.2.12
Oracle Enterprise Manager
The Critical Patch Update contains eight new security patches for Oracle Enterprise Manager. Six of these vulnerabilities may be remotely exploitable without authentication.
CVE-2022-23305 and CVE-2023-25690 in Oracle Application Testing Suite and Oracle Enterprise Manager Ops Center have the highest CVSS score of 9.8.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous Knowledgebase (KB) updates.
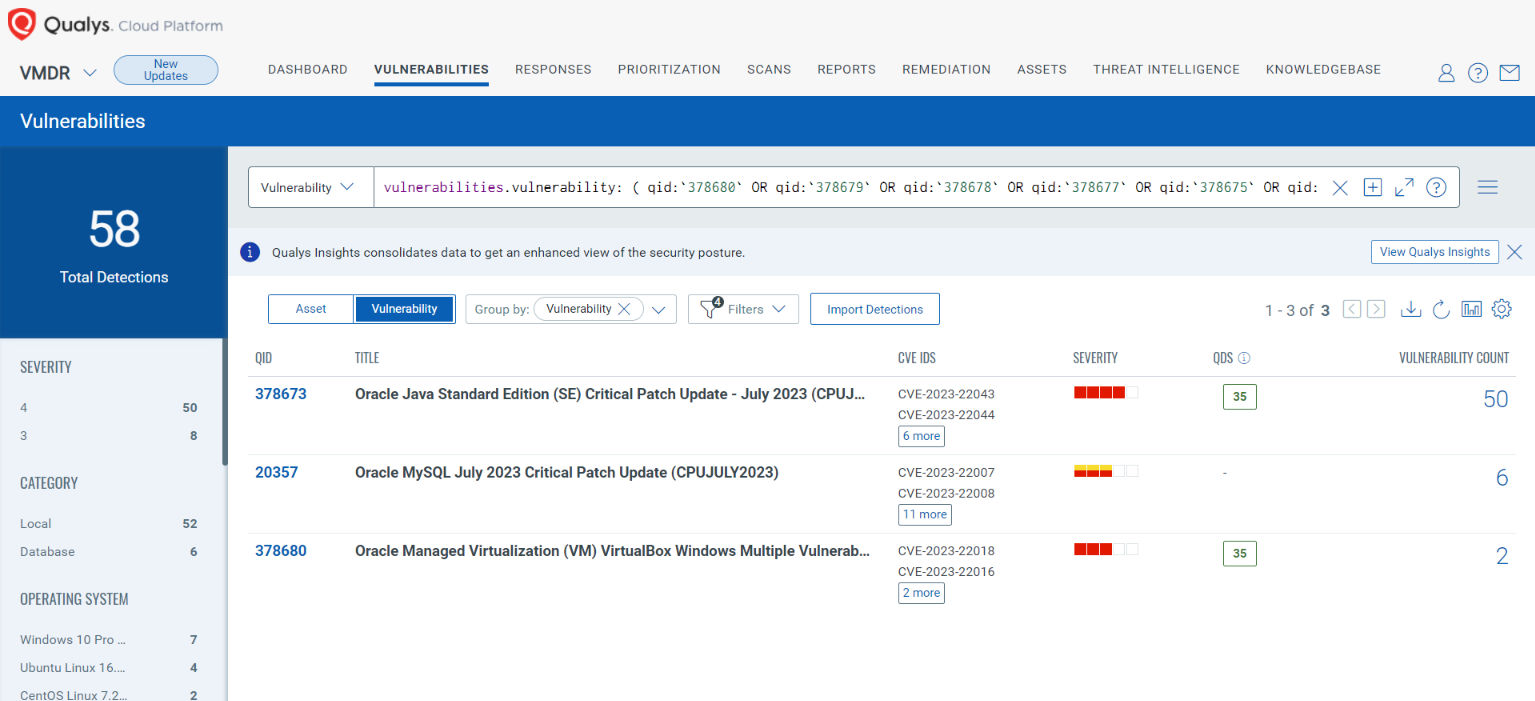
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:378680 OR qid:378679 OR qid:378678 OR qid:378677 OR qid:378675 OR qid:378673 OR qid:87546 OR qid:296101 OR qid:20354 OR qid:20355 OR qid:20356 OR qid:20357 )
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
vulnerabilities.vulnerability: ( qid:378680 OR qid:378679 OR qid:378678 OR qid:378677 OR qid:378675 OR qid:378673 OR qid:87546 OR qid:296101 OR qid:20354 OR qid:20355 OR qid:20356 OR qid:20357 )

9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.863 High
EPSS
Percentile
98.1%