
2024 Cybersecurity Trends: What’s Observable Already?
7.4 High
AI Score
Confidence
Low
2024 has already witnessed a staggering number of cyber incidents, with over 29.5 billion records breached across 4,645 publicly disclosed incidents in January alone, according to the IT Governance Security Spotlight. Moreover, CVEs are growing significantly year over year, with 13% growth from 2022 to last year, and an expected 25% increase from 2023 to 2024. With such growth in vulnerabilities, staying on top of the latest trends that attackers may be using is vital.
So, what trends are we observing so far in 2024?
Ransomware-as-a-Service (RaaS)
Among the most significant trends is the proliferation of Ransomware-as-a-Service (RaaS), which has democratized the tools necessary for cyber-attacks, making it easier for less skilled attackers to launch ransomware campaigns. Ready-to-use ransomware has lowered the barrier to entry for committing cybercrimes, leading to an increased attack volume. The rise of RaaS stresses the need for robust, multi-layered security strategies to measure, map, and prioritize vulnerabilities with a focus on ransomware attacks. One critical aspect of countering RaaS threats involves reducing the window of opportunity for cyber attackers to exploit outdated systems. Security teams must focus on patching vulnerable external-facing assets, including web servers, email systems, and cloud-based services, which are often the first targets in ransomware attacks. To mitigate risks related to software processing internet data—such as browsers, plugins, and document readers—automated patch management can significantly enhance the effectiveness and timeliness of patches without manual intervention.
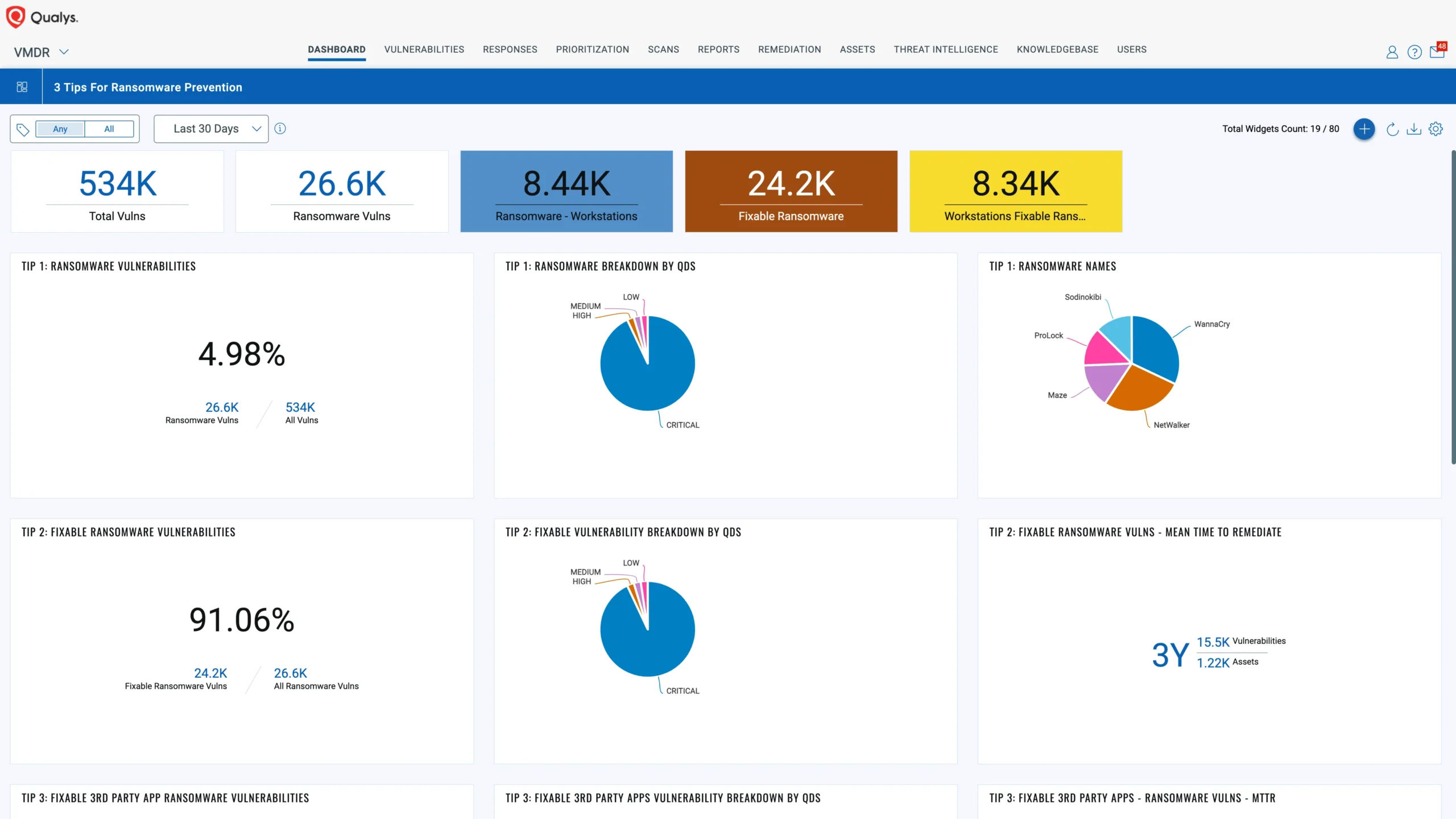 Figure 1: Qualys VMDR Ransomware Prevention Dashboard.
Figure 1: Qualys VMDR Ransomware Prevention Dashboard.
Software Supply Chain Attacks
Supply chain attacks have also surged, exploiting interconnected networks to compromise systems and data at various points in the production and distribution process. The reason for this rising trend, outside of being lucrative and debilitating to its victims, rests in the fact that software supply chains are often poorly managed and fraught with embedded open-source software (OSS) with unpatched vulnerabilities—making it a prime target for attackers. This trend highlights the critical need for streamlined approaches to managing your inventory of software components and inherently linking software management processes with security hygiene oversight between IT and security teams.
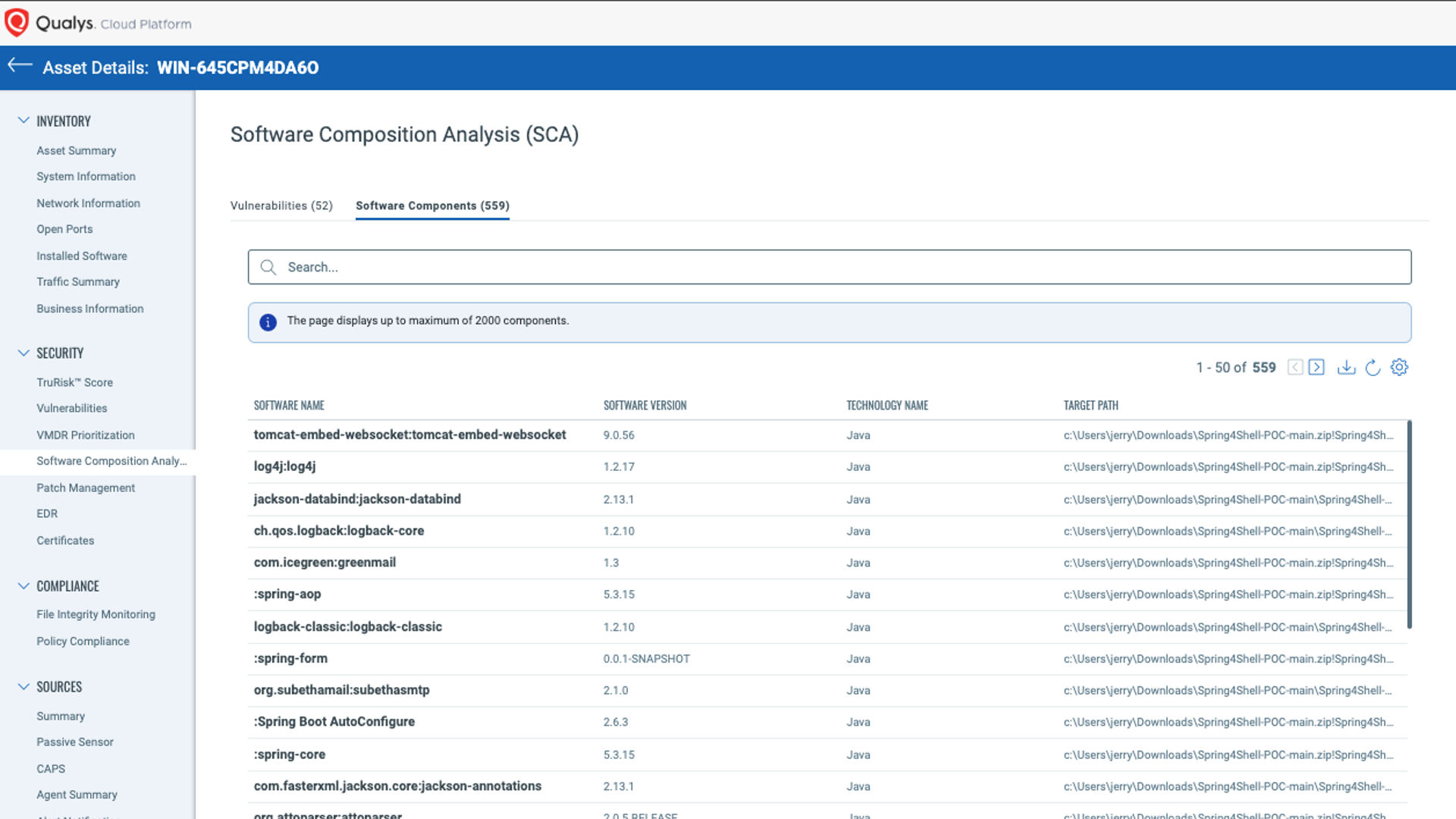 Figure 2: Quickly identify risk associated with OSS components with Qualys Software Composition Analysis (SCA).
Figure 2: Quickly identify risk associated with OSS components with Qualys Software Composition Analysis (SCA).
Advanced Persistent Threats (APTs)
The exploitation of zero-day vulnerabilities by Advanced Persistent Threats (APTs) remains a concern, particularly given rising global tensions attached to degrading China-US relations, the Ukrainian conflict, and the common offenders of Iran and North Korea. These attacks underscore the need for rapid patching and proactive security measures to mitigate risks as non-government entities increasingly become targets of nation-state actors looking to harm critical parts of commerce, such as telecom service access and digital payments. For example, by downing a mobile carrier for a matter of hours, an attacker can cost a regional economy billions of dollars by interrupting payment exchanges, ride-sharing services, and more.
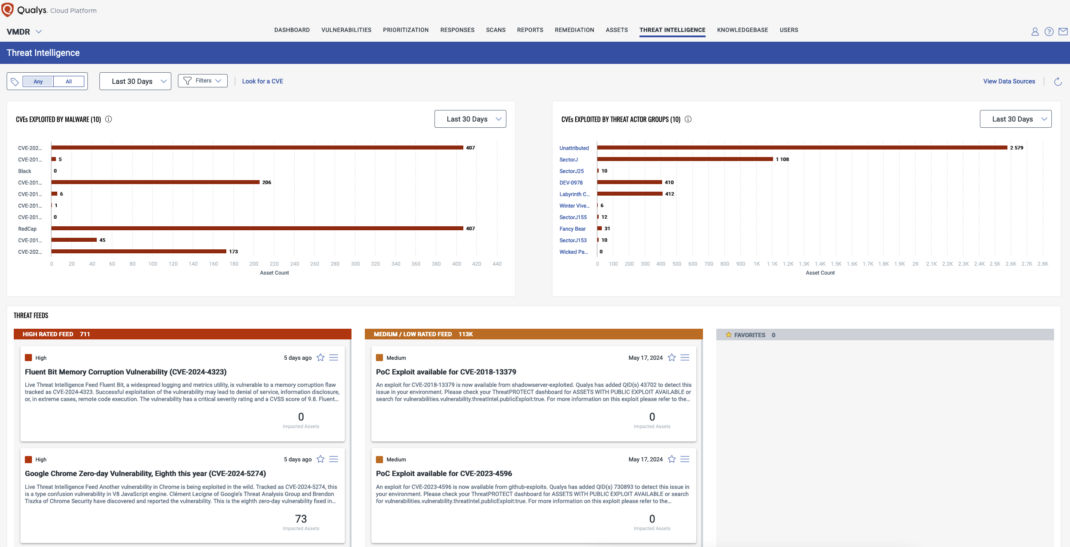 Figure 3: Qualys VMDR Threat Intelligence: Relevant CVEs, Trending Exploits, and Immediate Fixes Against Active Threat Actors.
Figure 3: Qualys VMDR Threat Intelligence: Relevant CVEs, Trending Exploits, and Immediate Fixes Against Active Threat Actors.
Cloud Security
Cloud security has emerged as both a trend and a key challenge. As businesses continue to migrate to cloud-based environments, attackers are exploiting vulnerabilities in cloud services, such as misconfigurations and inadequate access controls. This necessitates enhanced cloud security practices and advanced mitigation actions that can scale across a hybrid enterprise. Regretfully, many larger businesses and enterprise organizations have fallen victim to a fragmented approach to cybersecurity oversight with separate point solutions used to manage assets on-premises vs. in the cloud. This approach, outside of being a bit archaic and costly, increases the complexity of analyzing the cyber risk associated with assets in the cloud vs. assets elsewhere, thus inhibiting response.
AI-Enabled Attacks
Lastly, cybercriminals' use of artificial intelligence (AI) is a growing concern. AI technologies, such as generative AI, could enhance phishing attacks, making them more targeted and difficult to detect. Moreover, the potential for criminals to develop their own AI models trained on malicious code is particularly worrying, suggesting a future where malware is more sophisticated and harder to defend against.
Going Forward
Considering these trends, the role of today’s security practitioner is changing from an analyst to an alert facilitator, bouncing from security platform to IT service management tool in order to keep up. From the perspective of someone who has grown up alongside the cybersecurity industry, the industry must shift from a growth-by-acronym model that offers customers a plethora of point solutions that solve only parts of what a security stakeholder must concern themselves with. This approach has served better to bloat budgets for CTOs and create a tool sprawl for security practitioners to manage – sometimes not so well.
Going forward, it is imperative for the industry to focus on developing solutions that consolidate cybersecurity and risk management to facilitate proactive posture management using advanced technologies like AI and machine learning—predicting and preventing attacks before they occur. In addition, increasing collaboration with other organizations, such as ITOps, is a key area of focus for customer-focused companies like Qualys, recognizing that improving MTTR and reducing cyber risk is the shared responsibility of IT and security organizations alike. Thus, security tooling and technologies that streamline IT-SecOps coordination, bolstered with AI-enabled threat intelligence, are going to be a requirement – not a best practice.
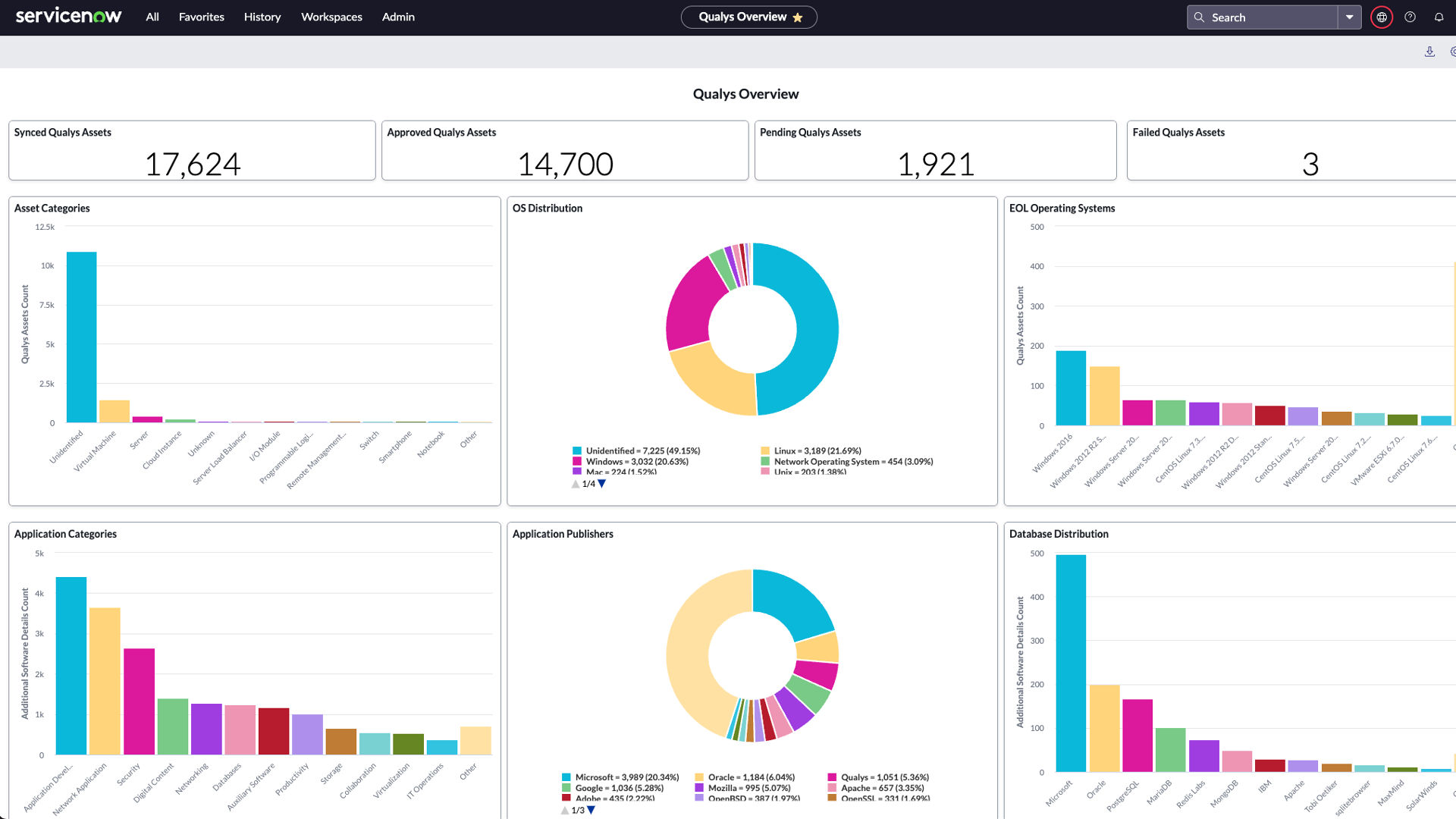 Figure 4: Qualys’ ServiceNow integration helps IT and security reduce MTTR by half.
Figure 4: Qualys’ ServiceNow integration helps IT and security reduce MTTR by half.
To learn more about the Qualys approach to the modern cybersecurity platform, visit our Enterprise TruRisk Platform page.
7.4 High
AI Score
Confidence
Low