
Microsoft and Adobe Patch Tuesday, September 2023 Security Update Review
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.571 Medium
EPSS
Percentile
97.3%
Microsoft has released the Patch Tuesday edition for September. This month's updates have addressed 66 security vulnerabilities (including Edge Chromium-based) in multiple products, features, and roles.
Microsoft Patch Tuesday for September 2023
Microsoft has addressed twozero-day publicly exploited vulnerabilities fixed in this month's updates. Fiveof these 66 vulnerabilitiesare rated as Critical and 58as Important. Microsoft has released patches to four vulnerabilities related to Microsoft Edge (Chromium-based) in this month's Patch Tuesday Edition.
Microsoft Patch Tuesday, September edition includes updates for vulnerabilities in Microsoft Office and Components, Microsoft Azure Kubernetes Service, Microsoft Dynamics, Microsoft Windows Codecs Library, Visual Studio Code, Windows Cloud Files Mini Filter Driver, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The September 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 5 | Important: 4 |
| Denial of Service Vulnerability | 3 | Important: 3 |
| Elevation of Privilege Vulnerability | 17 | Critical: 1 |
| Important: 16 | ||
| Information Disclosure Vulnerability | 9 | Important: 9 |
| Security Feature Bypass Vulnerability | 4 | Important: 4 |
| Remote Code Execution Vulnerability | 24 | Critical: 4 |
| Important: 19 |
Adobe Patches for September 2023
Adobe has released threesecurity advisories in this month's updates. The advisories addressed five vulnerabilities in Adobe Acrobat and Reader, Adobe Connect, and Adobe Experience Manager.
Adobe has addressed a zero-day vulnerability CVE-2023-26369 in Adobe Acrobat and Reader in this month’s Patch Tuesday. Adobe has mentioned in the advisory that they are aware of the active exploitation of the vulnerability. Successful exploitation of the vulnerability may lead to arbitrary code execution.
Zero-day Vulnerability Patched in September Patch Tuesday Edition
CVE-2023-36761: Microsoft Word Information Disclosure Vulnerability
Successful exploitation of this vulnerability could allow an attacker to disclose NTLM hashes. The NTLM hashes are encoded by converting the user's password into a 16-byte key using an MD4 hash function. The key is divided into two halves of 8 bytes. The key is used as input to three rounds of DES encryption that generates a 16-byte output representing the NTLM hash.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog, requesting users to patch it before October 3, 2023.
CVE-2023-36802: Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability
Microsoft Streaming Service Proxy is connected to a video service called Microsoft Stream. The service allows users to share information and improves communication and connectivity in a secure enterprise environment.
Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog, requesting users to patch it before October 3, 2023.
Other Critical Severity Vulnerabilities Patched in September Patch Tuesday Edition
CVE-2023-38148: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
Internet Connection Sharing (ICS) is a Windows service that enables one Internet-connected computer to share its Internet connection with other computers on a local area network (LAN).
The vulnerability is exploitable only when Internet Connection Sharing (ICS) is enabled. An attacker can only attack systems connected to the same network segment as them. Attacks cannot be carried out across multiple networks (for example, a WAN).
An unauthenticated attacker may exploit this vulnerability by sending a specially crafted network packet to the Internet Connection Sharing (ICS) Service.
CVE-2023-29332: Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability
Azure Kubernetes Service (AKS) has built-in code-to-cloud pipelines and guardrails that offer the fastest development and deployment of cloud-native apps in Azure data centers. The service provides unified management and governance for on-premises, edge, and multi-cloud Kubernetes clusters.
The vulnerability can be exploited remotely in a low-complexity attack by an attacker with no privileges required. An attacker could gain Cluster Administrator privileges on successful exploitation of the vulnerability.
CVE-2023-36792, CVE-2023-36793, and CVE-2023-36796: Visual Studio Remote Code Execution Vulnerability
Visual Code allows users to edit, debug, build, and publish an app. Visual Studio also provides compilers, code completion tools, graphical designers, and many more features to enhance software development.
To exploit the vulnerabilities, an attacker must convince a victim to download and open a specially crafted file from a website, leading to a local computer attack.
Other Microsoft Vulnerability Highlights
- CVE-2023-38161 and CVE-2023-36804 are elevation of privilege vulnerabilities in Windows GDI. The vulnerabilities may allow an attacker to gain SYSTEM privileges on successful exploitation.
- CVE-2023-38152 is an information disclosure vulnerability in the DHCP Server Service. Successful exploitation of the vulnerability may lead to the disclosure of initialized or uninitialized memory in the process heap.
- CVE-2023-38142 is an elevation of privilege vulnerability in Windows Kernel. The vulnerability may allow an attacker to gain SYSTEM privileges on successful exploitation.
- CVE-2023-38160 is an information disclosure vulnerability in Windows TCP/IP. Successful exploitation of the vulnerability would allow an attacker to read small portions of heap memory.
- CVE-2023-36777 is an information disclosure vulnerability in Microsoft Exchange Server. An attacker must be authenticated with LAN access and have credentials for a valid Exchange user to exploit the vulnerability. On successful exploitation, an attacker would disclose file content.
- CVE-2023-38143 and CVE-2023-38144 are elevation of privilege vulnerabilities in the Windows Common Log File System Driver. The vulnerabilities may allow an attacker to gain SYSTEM privileges on successful exploitation.
- CVE-2023-36756, CVE-2023-36745, and CVE-2023-36744 are remote code execution vulnerabilities in Microsoft Exchange Server. An attacker must be authenticated with LAN access and have credentials for a valid Exchange user to exploit the vulnerabilities. On successful exploitation, an attacker could trigger malicious code in the context of the server's account through a network call.
Microsoft Release Summary
This month's release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Microsoft Azure Kubernetes Service, Azure DevOps, Windows Cloud Files Mini Filter Driver, Microsoft Identity Linux Broker, 3D Viewer, Visual Studio Code, Microsoft Exchange Server, Visual Studio, 3D Builder, .NET Framework, .NET and Visual Studio, .NET Core & Visual Studio, Microsoft Dynamics Finance & Operations, Windows DHCP Server, Microsoft Streaming Service, Windows Kernel, Windows GDI, Windows Scripting, Microsoft Dynamics, Windows Common Log File System Driver, Windows Themes, Microsoft Windows Codecs Library, Windows Internet Connection Sharing (ICS), Windows TCP/IP, Azure HDInsights, and Windows Defender.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110446` OR qid:`110447` OR qid:`110448` OR qid:`378852` OR qid:`50129` OR qid:`92055` OR qid:`92056` OR qid:`92057` OR qid:`92058` OR qid:`92059` OR qid:`92060` OR qid:`92061` OR qid:`92062` OR qid:`92063` OR qid:`92064` OR qid:`92065` )
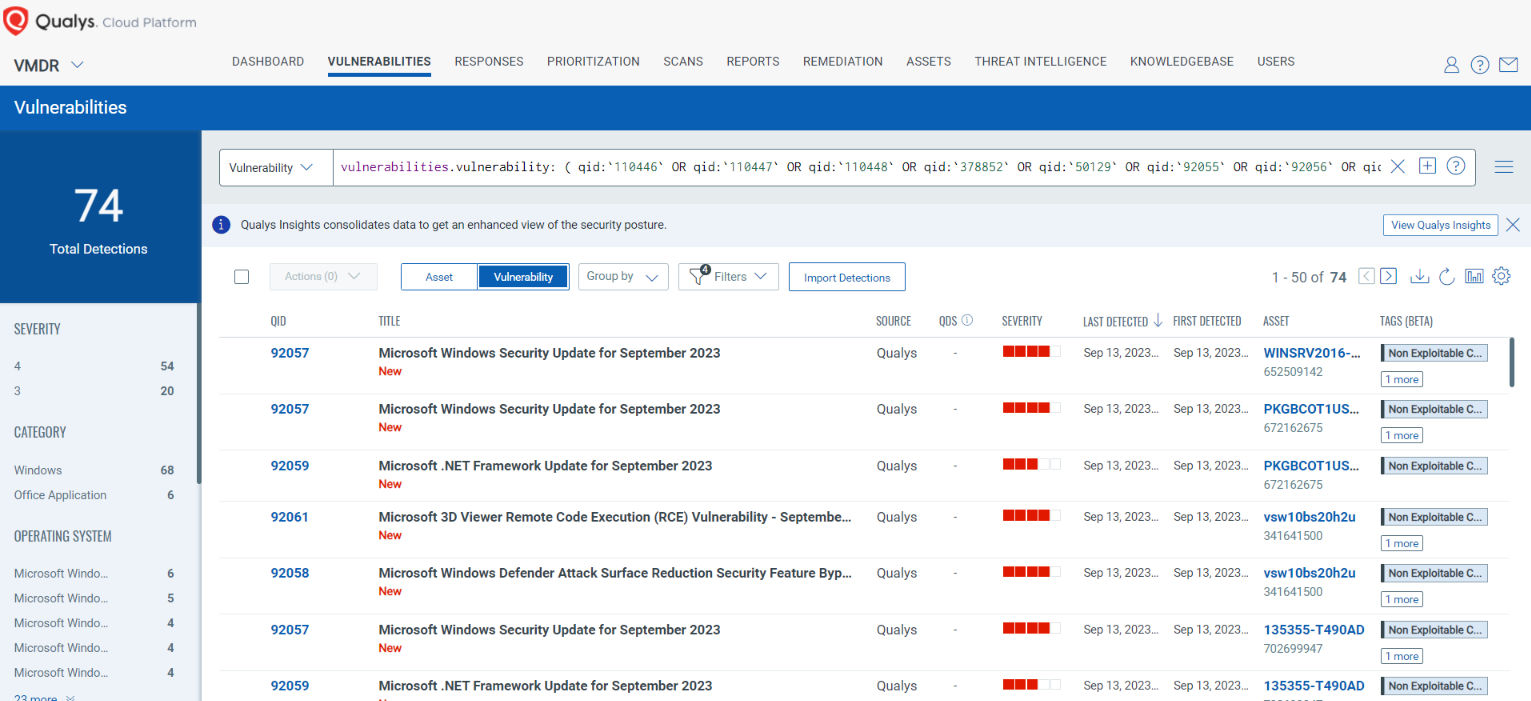
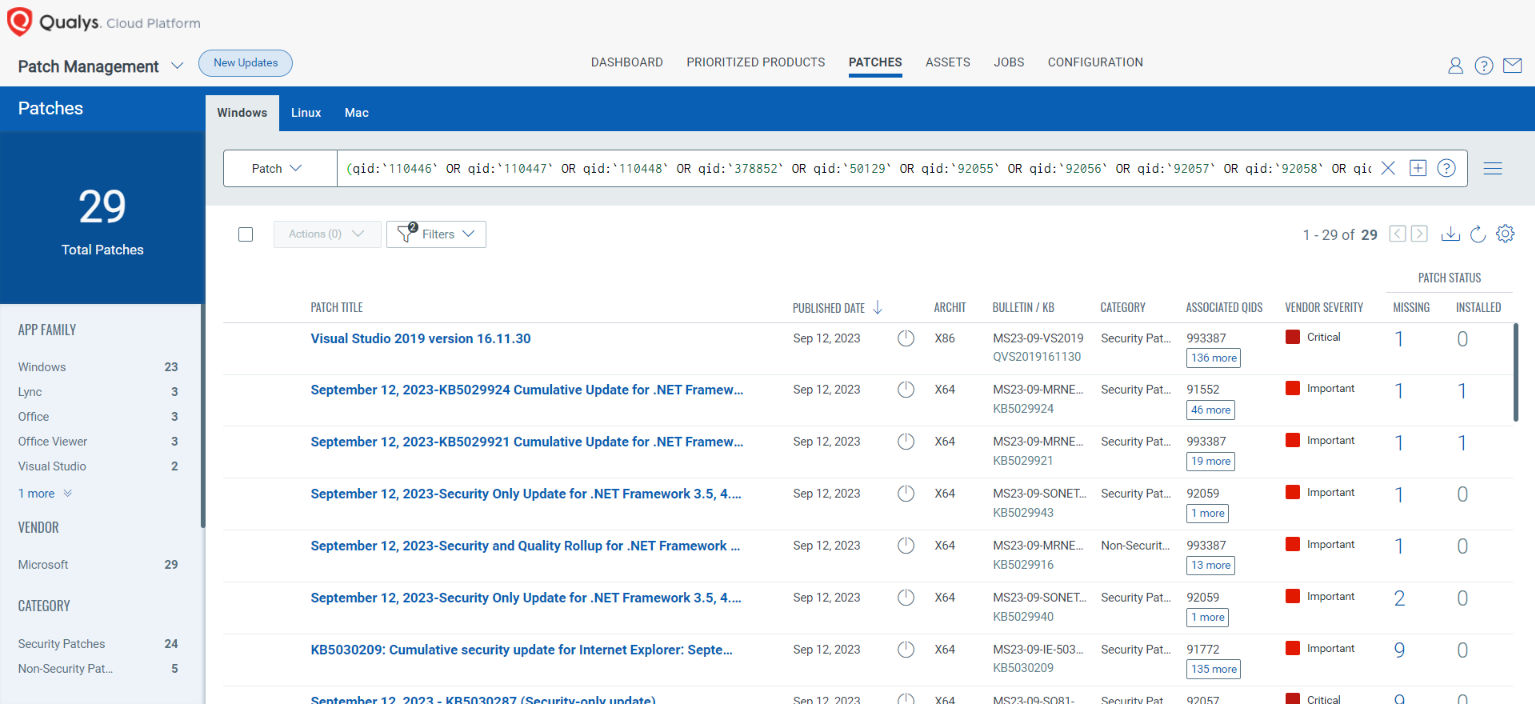
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110446` OR qid:`110447` OR qid:`110448` OR qid:`378852` OR qid:`50129` OR qid:`92055` OR qid:`92056` OR qid:`92057` OR qid:`92058` OR qid:`92059` OR qid:`92060` OR qid:`92061` OR qid:`92062` OR qid:`92063` OR qid:`92064` OR qid:`92065` )
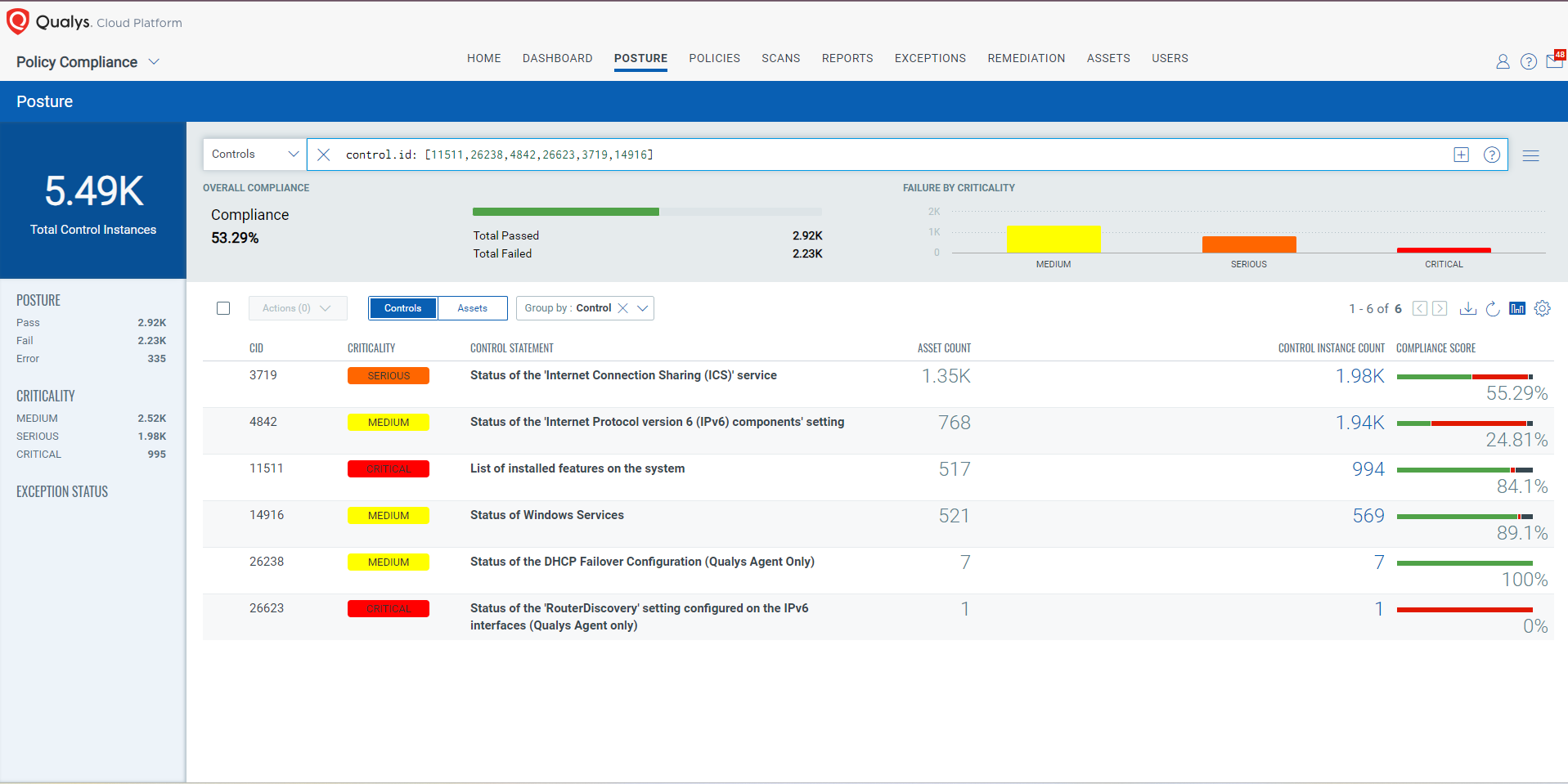
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance's Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/Patch) cannot be done now; these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is sometimes used temporarily for achieving a task or goal when the usual or planned method isn't working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
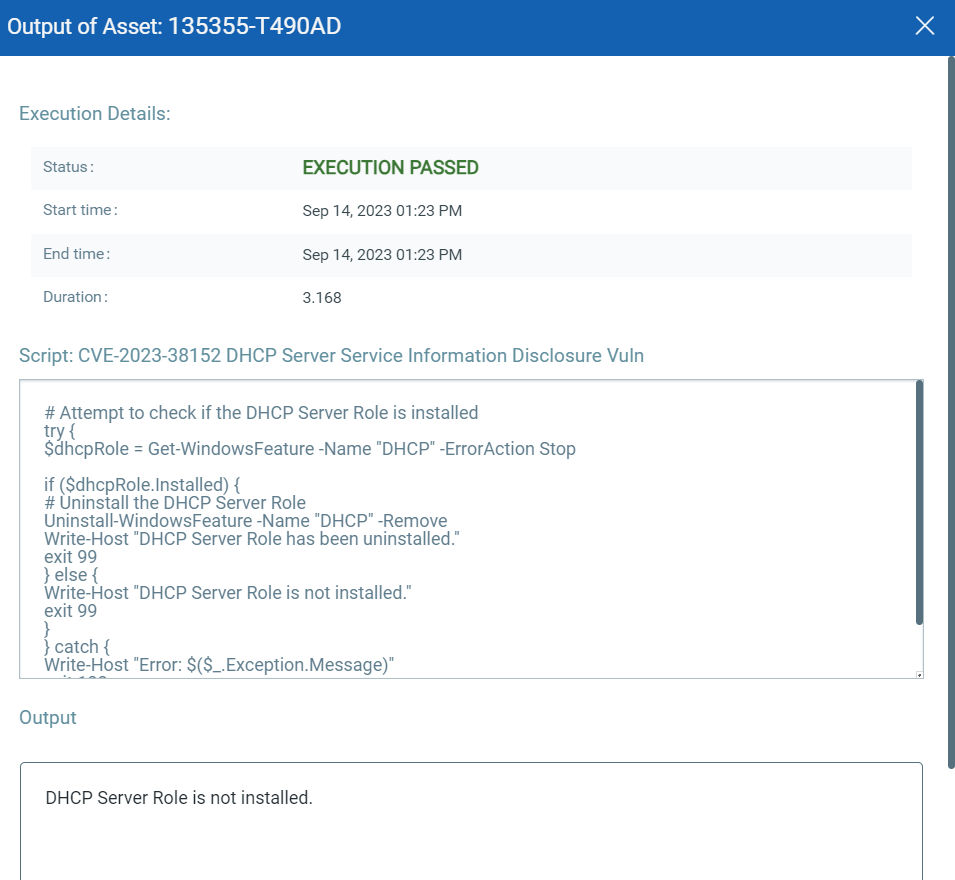
CVE-2023-36801, CVE-2023-38152: DHCP Server Service Information Disclosure Vulnerability
This vulnerability has a CVSS:3.1 5.3 / 4.6
Policy Compliance Control IDs (CIDs):
- 11511 List of installed features on the system
CVE-2023-38162: DHCP Server Service Denial of Service Vulnerability
This vulnerability has a CVSS:3.1 7.5 / 6.5
Policy Compliance Control IDs (CIDs):
- 26238 Status of the DHCP Failover Configuration (Qualys Agent Only)
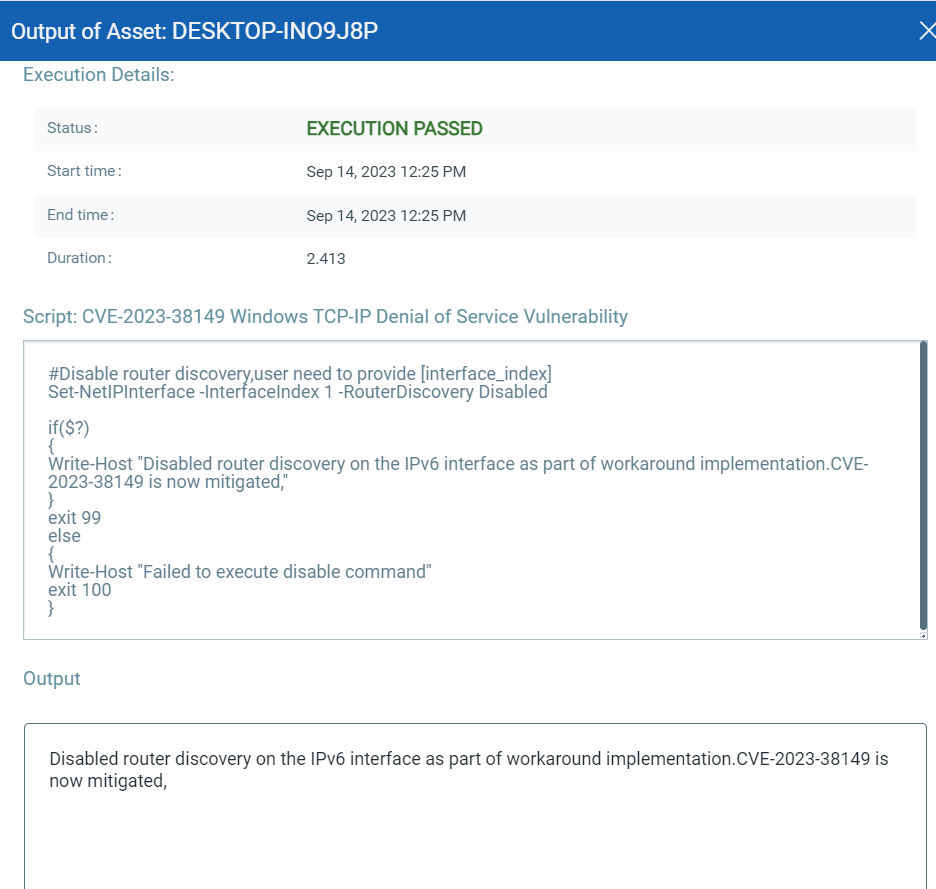
CVE-2023-38149: Windows TCP/IP Denial of Service Vulnerability
This vulnerability has a CVSS:3.1 7.5 / 6.5
Policy Compliance Control IDs (CIDs):
- 26623 Status of the 'RouterDiscovery' setting configured on the IPv6 interfaces (Qualys Agent only)
- 4842 Status of the 'Internet Protocol version 6 (IPv6) components' setting
CVE-2023-38148: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 8.8 / 7.7
- 3719 Status of the 'Internet Connection Sharing (ICS)' service
- 14916 Status of Windows Services
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [11511,26238,26623,3719,14916]
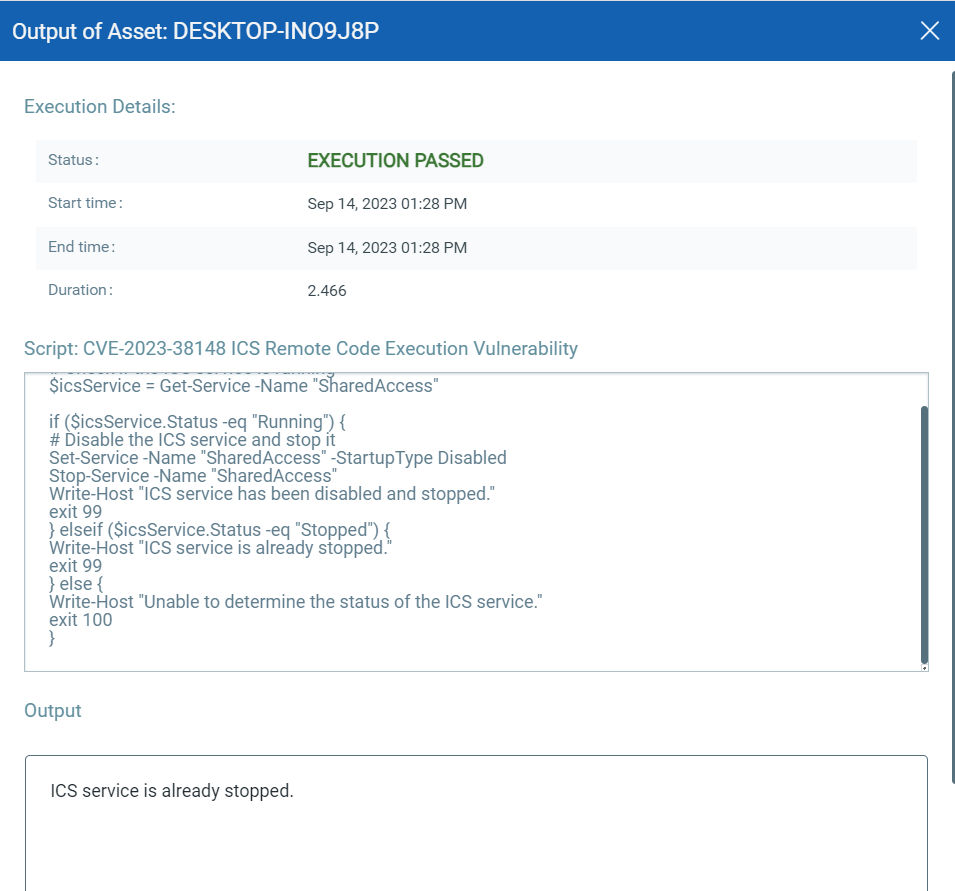
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
CVE-2023-38148: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
CVE-2023-38152: DHCP Server Service Information Disclosure Vulnerability
This vulnerability has a CVSSv3.1 score of 5.3/10.
CVE-2023-38149: Windows TCP/IP Denial of Service Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
The next Patch Tuesday falls on October 10, and we'll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the 'This Month in Vulnerabilities and Patch's webinar.'
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month's high-impact vulnerabilities, including those that are a part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.571 Medium
EPSS
Percentile
97.3%