CSAM Strengthens Attack Surface Coverage and Risk Assessment With Third-Party Connectors
6.8 Medium
AI Score
Confidence
Low
Organizations using Qualys CyberSecurity Asset Management (CSAM) can now import asset data from any external system into the Enterprise TruRisk Platform. With third-party connectors, you will identify any existing coverage gaps andadd business context to your unified inventory, helping you efficiently measure, communicate, and eliminate cyber risk across your entire attack surface.
This blog is the first in a series covering the import service management capabilities and the different connectors available for import.
Why import assets into Qualys?
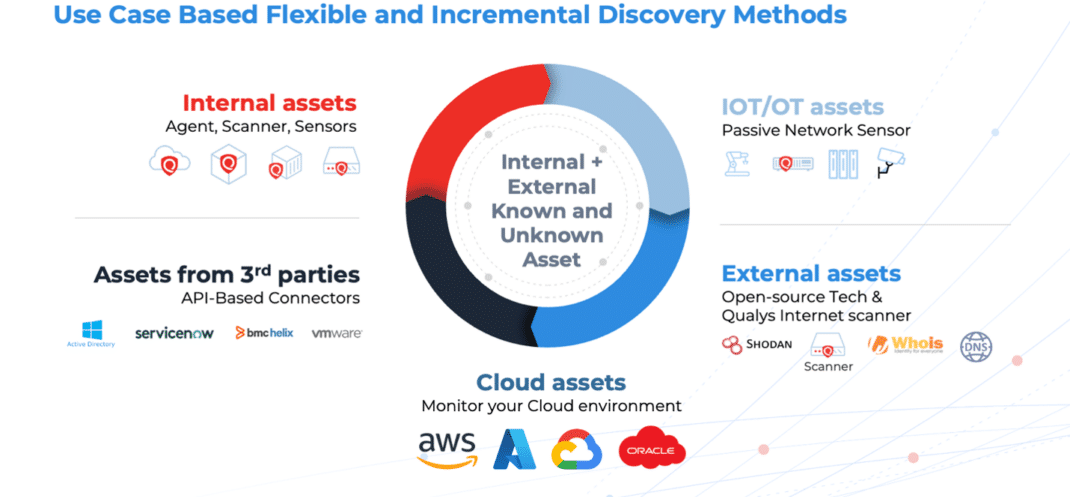
The Enterprise TruRisk Platform with CSAM provides industry-leading discovery methods for all your IT and OT assets - including Cloud Agents, IP Scanners, passive sensors, Cloud Connectors, and EASM scans.
While these Qualys-native discovery methods can cover your entire IT/OT asset landscape, there can be situations where additional asset inventory and related organizational/business context exist in external systems—such as after recent acquisitions or while you are still rolling out Qualys across your organization. Consolidating this data in one place improves risk assessment and reporting—particularly when it comes to questions from auditors about critical assets and comprehensive discovery.
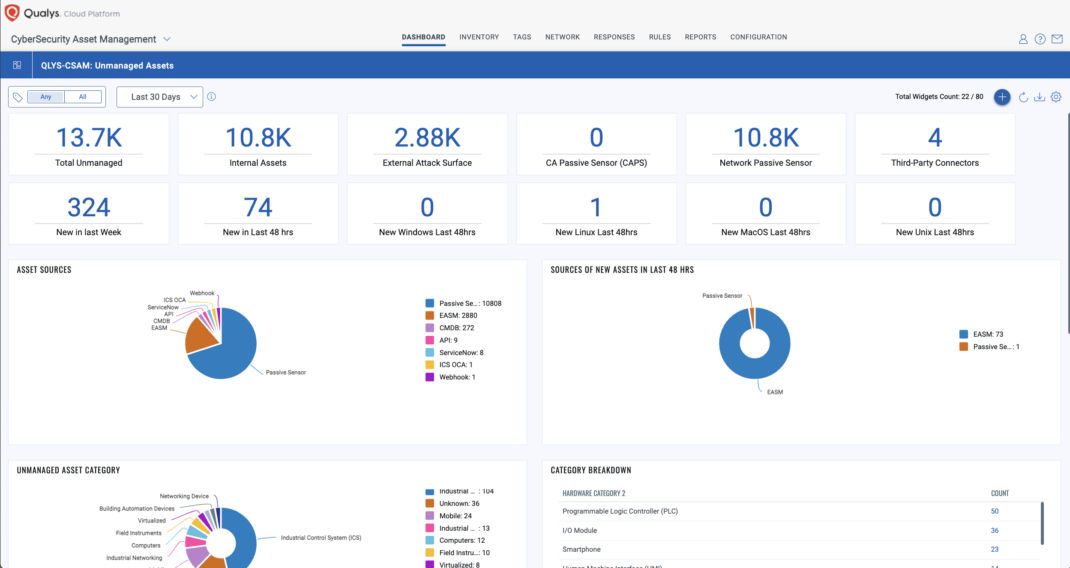
Now, in addition to attack surface coverage from Cloud Agents and scans, you can add unknown assets and business context from third-party sources to get a consolidated view of your entire IT and OT landscape. You can also monitor all assets missing from Qualys coverage using a dashboard like the one pictured below.
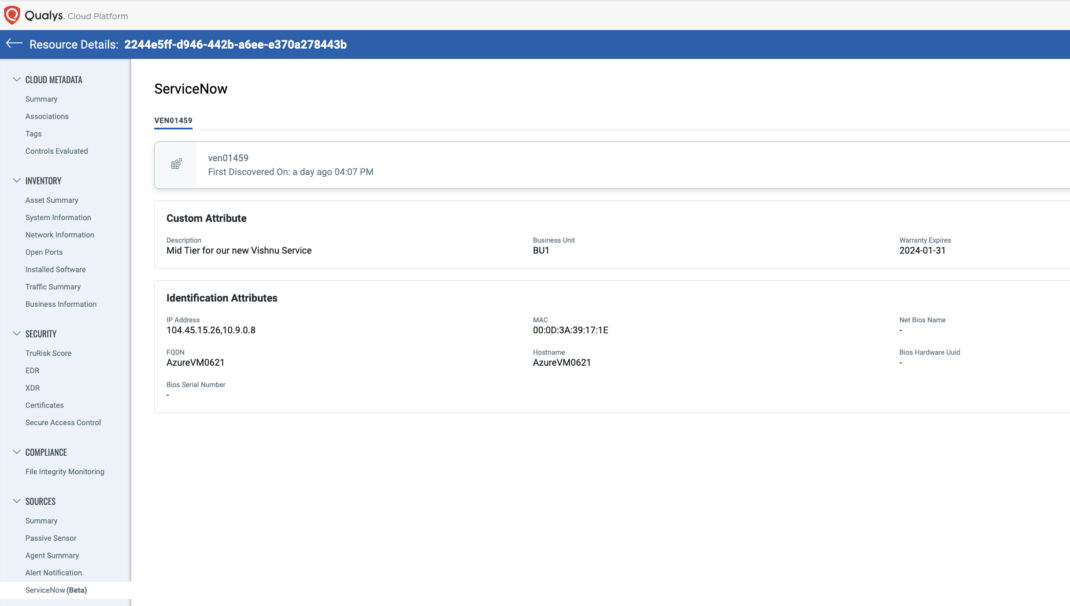
CSAM customers can also enrich existing Qualys assets with business context from external systems like Active Directory, or CMDBs like ServiceNow and BMC Helix, which can be quite valuable when remediating risk and working to achieve compliance goals. The example below shows custom attributes for Description, Business Unit, and Warranty Expiration from ServiceNow.
Custom attribute data can be queried and added to dashboards and reports so you can properly identify asset owners and other context needed during remediation and reporting.
Here are a few scenarios where this new import functionality can provide real-world value:
- As a result of mergers and acquisitions, you might have a whole other set of assets that need to be added to your VM program.
- You are capturing business information like asset criticality, ownership, and department in CMDBs like ServiceNow or BMC Helix and want Qualys to use that information for categorization and risk assessment.
- You want to leverage your existing AD metadata to bring Org context (such as OU and BU) to your Windows assets.
- You already have other systems with asset data and business context covering parts of your organization where you do not yet have Qualys deployed and want to secure those assets with Qualys.
Enabling Third-Party Asset Import
Third-party asset import is available for beta testing by customers with CSAM. You can request enablement by creating a Qualys Support case or by request to your Technical Account Manager (TAM).
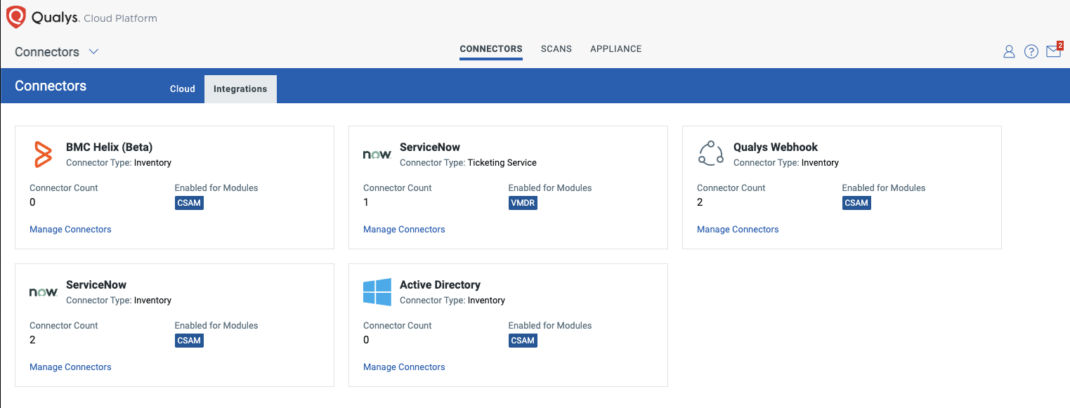
Once enabled, you will see the following connectors added to your subscription.
You can select the “Manage Connectors” link in any of the tiles to create and manage connectors. We will go into the details of creating the different connectors in subsequent blog posts.
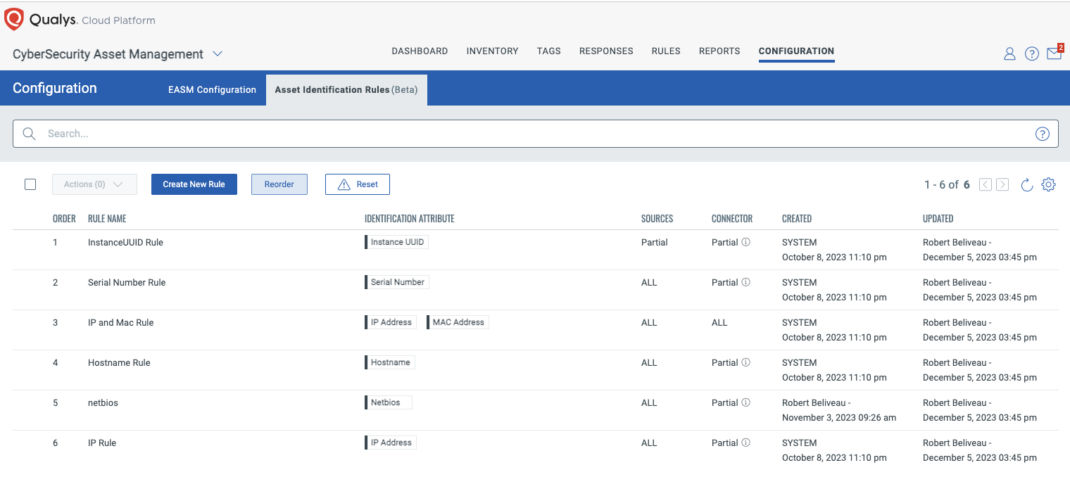
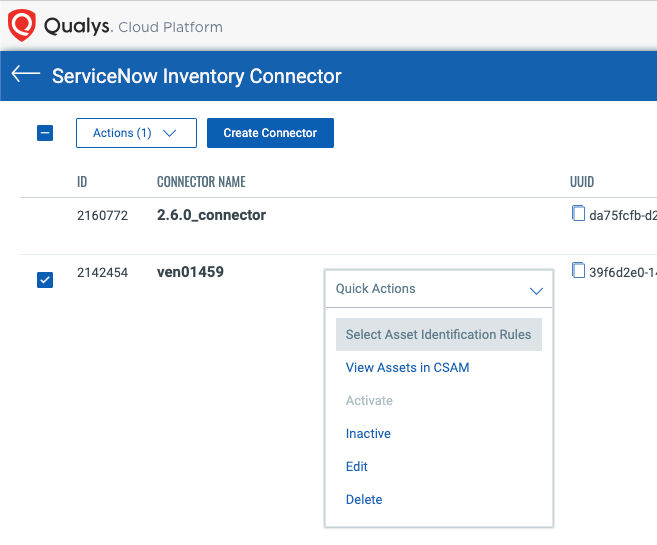
Asset Identification Rules
**_Asset Identification Rules _**in CSAM are used to match the imported data with existing Qualys assets, adding new assets and enriching existing assets as appropriate. If a rule match is found, the existing asset will be enriched with business context provided by the imported data. If no rule match is found, then a new “Unmanaged” asset can be created.
Under CSAM’s Configuration > Asset Identification Rules (Beta) screen, CSAM provides default rules like the ones below that you can customize to suit your needs.
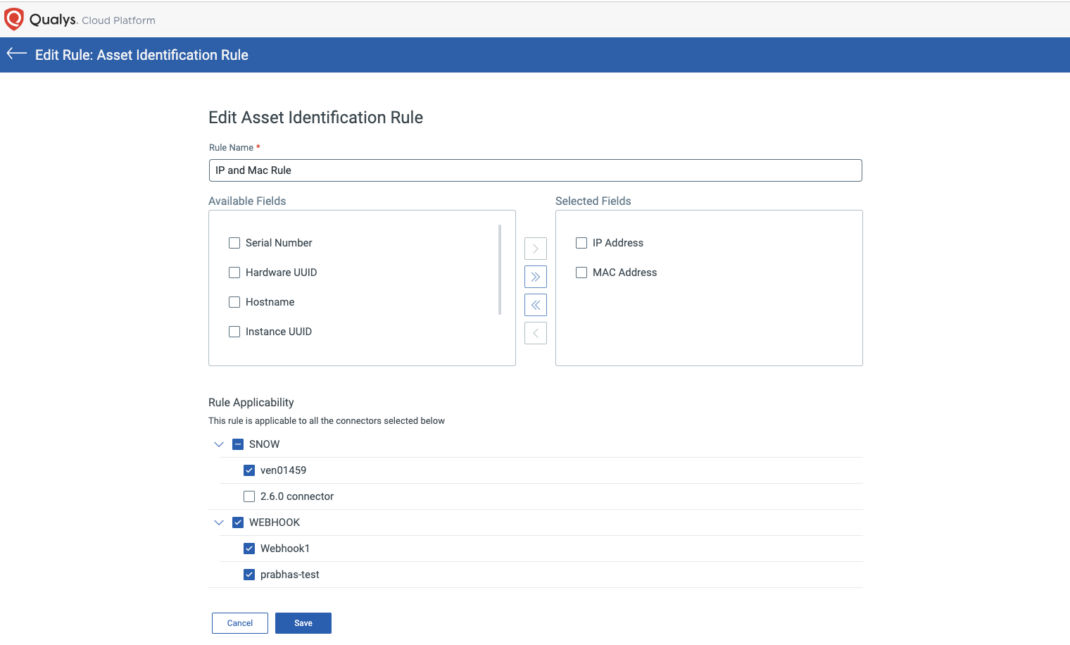
You can add and change the identifiers, set them to apply to some or all the different import sources and connectors, as well as reorder their priority. When the asset identification service receives asset data to import from a connector, the appropriate rules will be evaluated in the priority order specified.
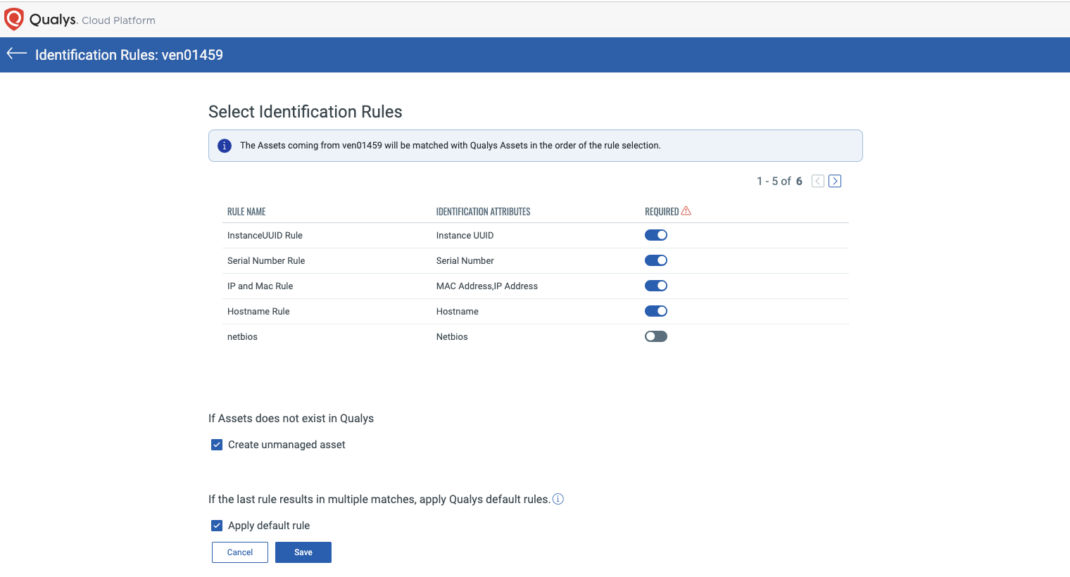
In the Connector module, you can set connector-specific rules. If you click the Select Asset Identification Rules option, the rules will be shown along with a switch to specify if the asset is REQUIRED to have the attribute for it to be imported, as well as an option to create unmanaged assets for assets without a match.
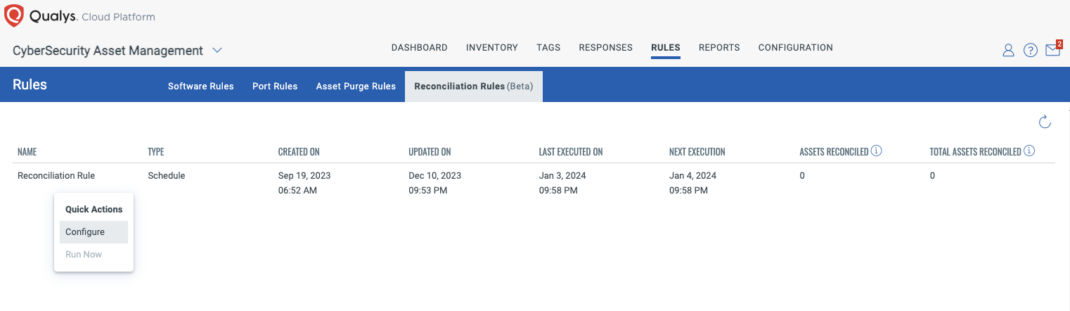
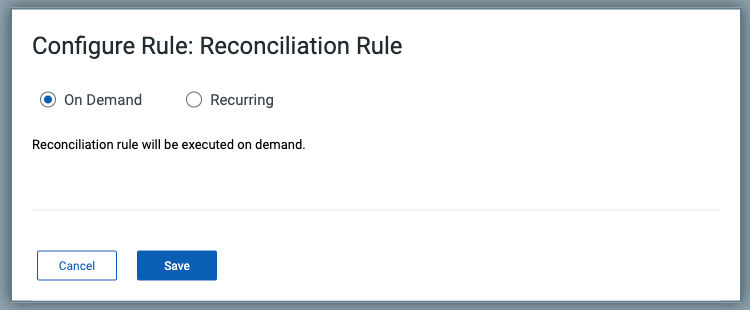
Reconciliation Rules
In certain scenarios, assets generated by third-party sources might not be merged with any existing managed assets. This lack of merging can occur when no rule identifies an existing asset. If Qualys itself later discovers the same asset, this can lead to the creation of two distinct Qualys assets.
To address this challenge, users can implement the Reconciliation process, which can be initiated on demand or scheduled for daily recurrence. This process merges the two assets, streamlining asset management and ensuring a cohesive asset identification system.
You can choose to run Reconciliation Rules on demand or set it to run on a recurring basis.
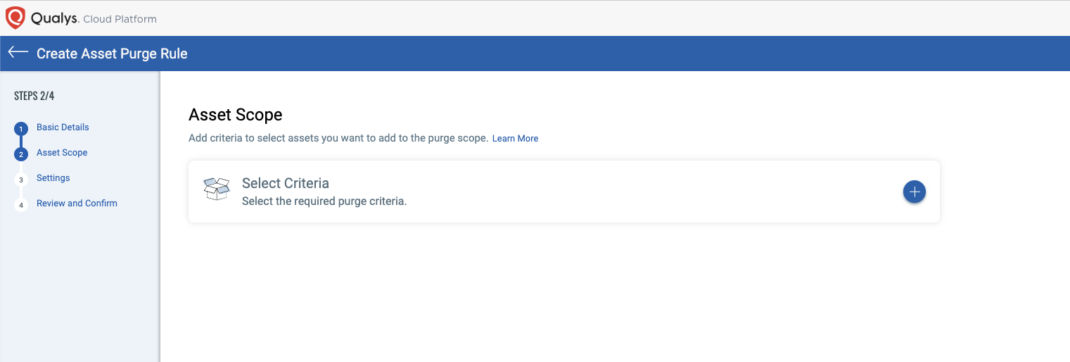
Purge Rules
It may be necessary to remove test data as you work on the import or maybe even clear out stale data. Qualys CSAM allows you to remove imported data using Purge Rules.
When you purge asset data using purge rules, you are only deleting the data associated with the connector specified. If that connector is the only source for an asset, the asset will be deleted; otherwise, the data provided by that connector is purged from the asset, leaving other source data for the asset intact.
When defining Purge Rules, select the new “Add Other Sources Criteria” option.
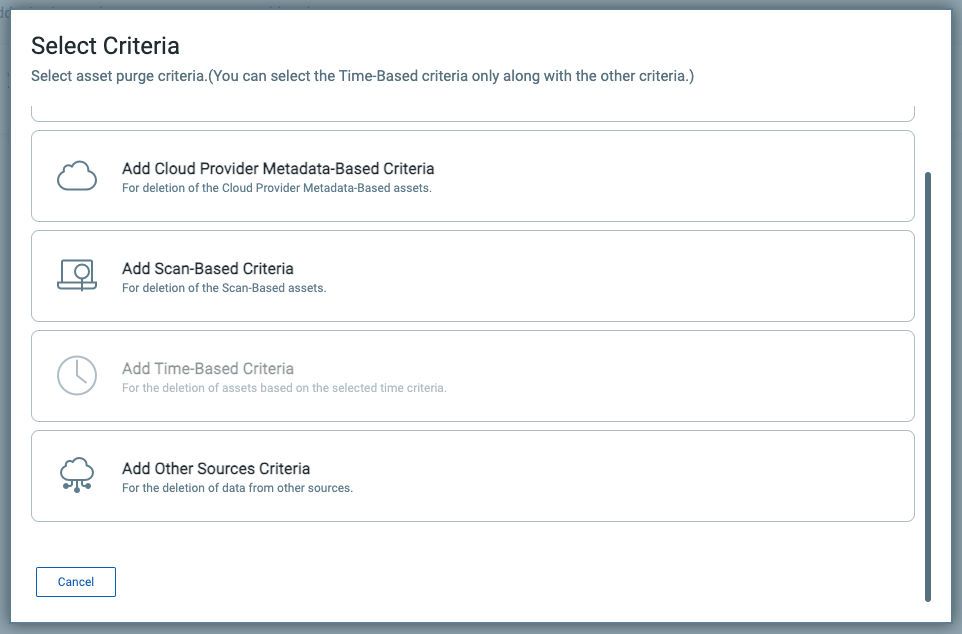
You can then select the specific connector used to import the assets and a few different criteria to select assets to purge.
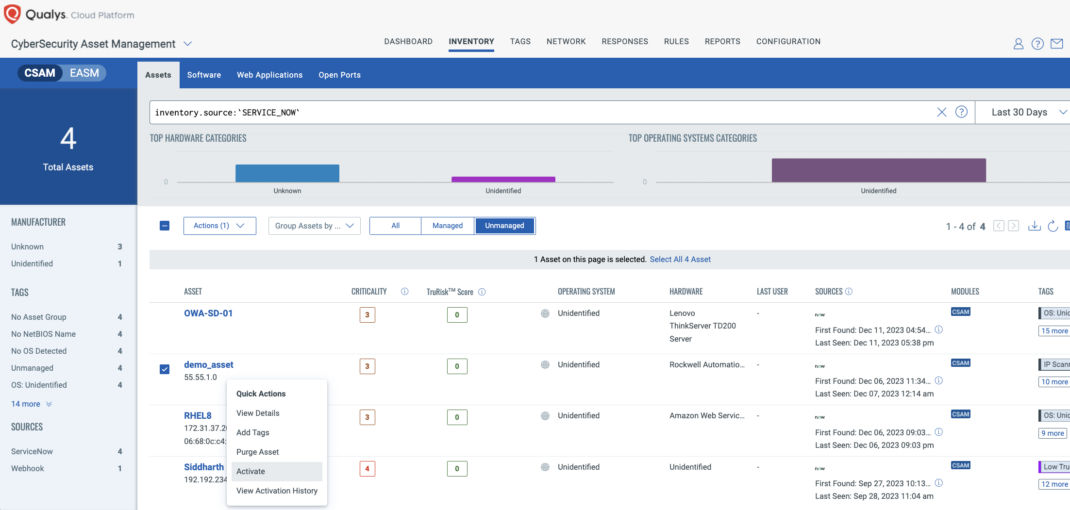
Activate assets for Qualys scans
After importing new assets using one of the new Qualys Connectors, they are created as “Unmanaged” assets, meaning assets visible in Qualys, but not being scanned by Qualys. With the Quick Actionsmenu, you can quickly Activate assets for VMDR, Certificate View, and Policy Compliance module scans, so you can quickly get them scanned and under management by Qualys.
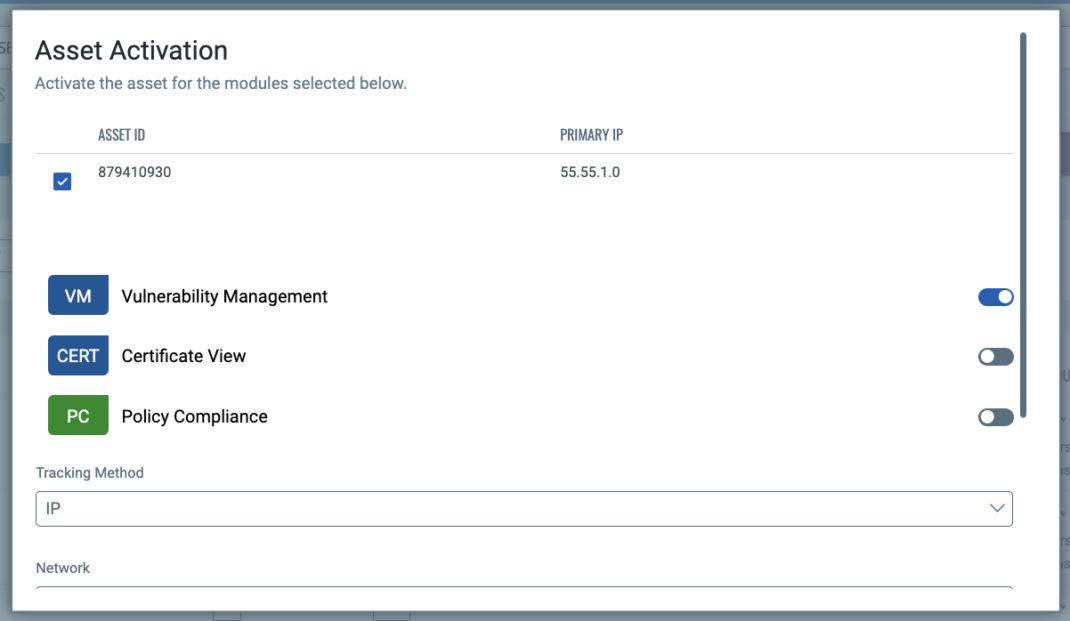
Close coverage gaps and enhance risk-based vulnerability management
Qualys CSAM is prioritizing third-party integrations for two primary reasons:
- Remove blind spots for assets housed in your CMDB, Active Directory, etc.
- Add business context and attributes to improve your understanding of the business risk associated with each asset.
CSAM is foundational for risk-based vulnerability management because it provides business context for both the internal and external attack surface, driving accurate TruRisk Scoring across your unique environment. This allows teams to measure cyber risk for each asset, communicate cyber risk to various stakeholders, and eliminate risk with confidence that their efforts are focused on the areas of highest impact.
Qualys CSAM provides you everything you need to manage the addition of third-party source data into your Qualys subscription—including the ability to import assets, identify matches, and create/update assets as appropriate. It also provides flexible controls for identification, reconciliation, and data cleanup, plus the ability to quickly activate assets for management.
That’s all for this introduction to Qualys CSAM’s new asset import services. Stay tuned for additional blogs in this series specific to the different connectors like ServiceNow, Active Directory, BMC Helix, and others.
Start pulling asset data from third-party sources with a 30-day trial of CyberSecurity Asset Management (CSAM)
Contributors
- Pablo Quiroga, Senior Director, Product Management, CSAM & EASM, Qualys
6.8 Medium
AI Score
Confidence
Low