
TotalCloud Insights: Securing Your Data—The Power of Encryption in Preventing Threats
7.2 High
AI Score
Confidence
High
Introduction
Did you know there is a 90% failure rate for encryption-related controls of MySQL Server in Microsoft Azure? The issue isn't confined to Azure; in Google Cloud Platform (GCP) environments there is a 98% failure rate of encryption-related controls for both compute engine and storage services. Amazon Web Services (AWS) is not exempt, with a LAMBDA failure rate of 71%, which indicates a significant gap in securing serverless functions, highlighting the need for users to enhance their understanding of encryption in these environments.
What Does This Mean?
In today's digital landscape, cloud computing platforms have become widespread. Organizations leverage the capabilities of cloud service providers like AWS, Azure, and GCP to store and process their data efficiently. Cloud service providers like the three mentioned above are responsible for the security "of the cloud" itself - the infrastructure, hardware, etc. However, customers bear responsibility for the security "in the cloud" - for safeguarding their sensitive data. As part of that responsibility, encrypting data in the cloud is fundamental, and implementing the best practices for AWS, Azure, and GCP is paramount.
Acknowledging the critical role of encryption in protecting your company's data in the cloud, it is crucial to understand both how to set up encryption properly and that setting up encryption incorrectly can leave your data exposed to potential threats. Many cloud service providers (CSPs) have made encryption a standard feature, free of charge. Enabling encryption is often as easy as checking a box in your settings. It is surprising how often users overlook this simple yet essential security measure.
In this blog post, we list some failure rates for key services across CSPs, give you a little background on cloud encryption, offer a real-world scenario, and then suggest best practices to help you employ encryption for enhanced cloud security.
Exploits That Arise Due to Lack of Encryption
The severe risks associated with poor security controls, like leaving data unencrypted, have been brought to light in recent years in several security incidents, including:
- An attack in January 2023 when a security researcher discovered that specific Google Cloud customers were utilizing unencrypted VM disks for critical workloads. Exploiting this misconfiguration, the researcher gained unauthorized access to customer financial information and intellectual property stored on these disks, resulting in the theft of sensitive data.
- Last year, when sensitive flight data, including flight charts and PII, was exposed due to the lack of security measures on an Amazon S3 bucket linked to PegasusEFB's EFB software, the software pilots use for navigation, to see crew information, etc. This breach could have been prevented by implementing security controls like encryption and access restrictions.
- The massive data breach Equifax suffered in 2017 due to the lack of data encryption, resulting in the exposure of the Personally Identifiable Information (PII) of over 148 million individuals. Encryption and proper monitoring could have significantly reduced the risk.
To avoid these kinds of incidents and ensure data protection, regulatory compliance, and mitigation of insider threats, it is crucial that organizations employ encryption best practices, including encrypting virtual machine (VM) disks using Customer-Supplied Encryption Keys (CSEKs) for critical VMs within any cloud platform ecosystem.
The Failure Rates of Encryption-Related Controls
We wanted to understand how we’re doing collectively in employing encryption and other related controls to see where we can improve the most. To that end, the Qualys research team analyzed encryption-related controls for widely used services across AWS, Azure, and GCP, revealing a fascinating landscape of strengths and areas needing improvement. In this analysis, "failure rates" refer to how often encryption-related controls failed for users of each cloud service.
AWS Encryption Controls:
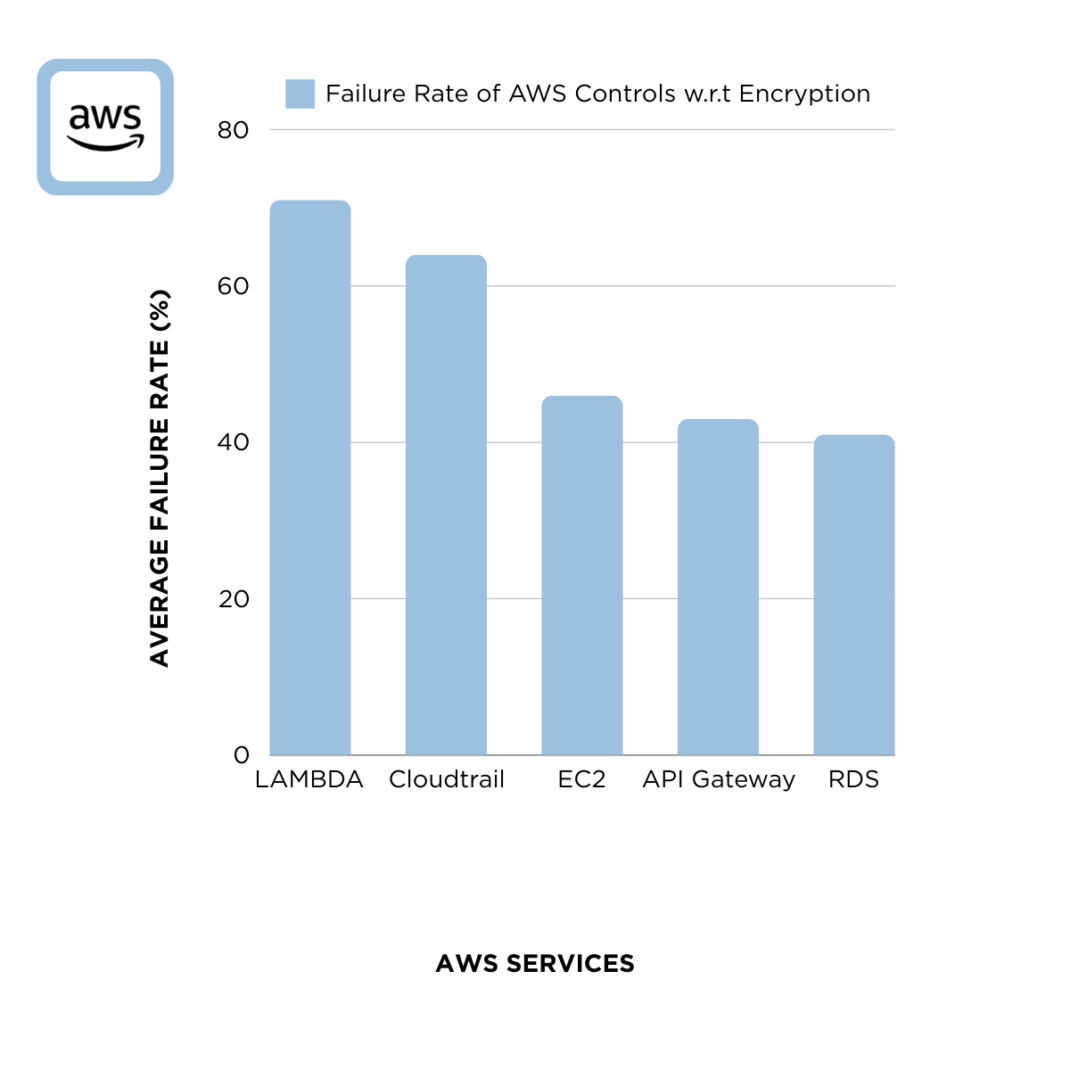 Figure 1: Failure Rate of AWS Controls with respect to encryption.
Figure 1: Failure Rate of AWS Controls with respect to encryption.
AWS reveals mixed results in implementing encryption best practices:
- LAMBDA: A 71% failure rate indicates a significant gap in securing serverless functions, highlighting the need for users to enhance their understanding of encryption in these environments.
- CloudTrail: With a 64% failure rate, potential vulnerabilities in logging and monitoring services are highlighted, underscoring the importance of improving encryption practices.
- EC2: A 46% failure rate suggests moderate concerns in virtual computing environments, where users could improve their grasp of encryption measures.
- API Gateway: A 43% failure rate reveals room for improvement in securing API endpoints, indicating a need for users to strengthen their encryption strategies.
- RDS: At 41%, managed database services show relatively better adherence to encryption practices, but there is still significant room for improvement and a need for increased focus on encryption protocols.
Azure Encryption Controls:
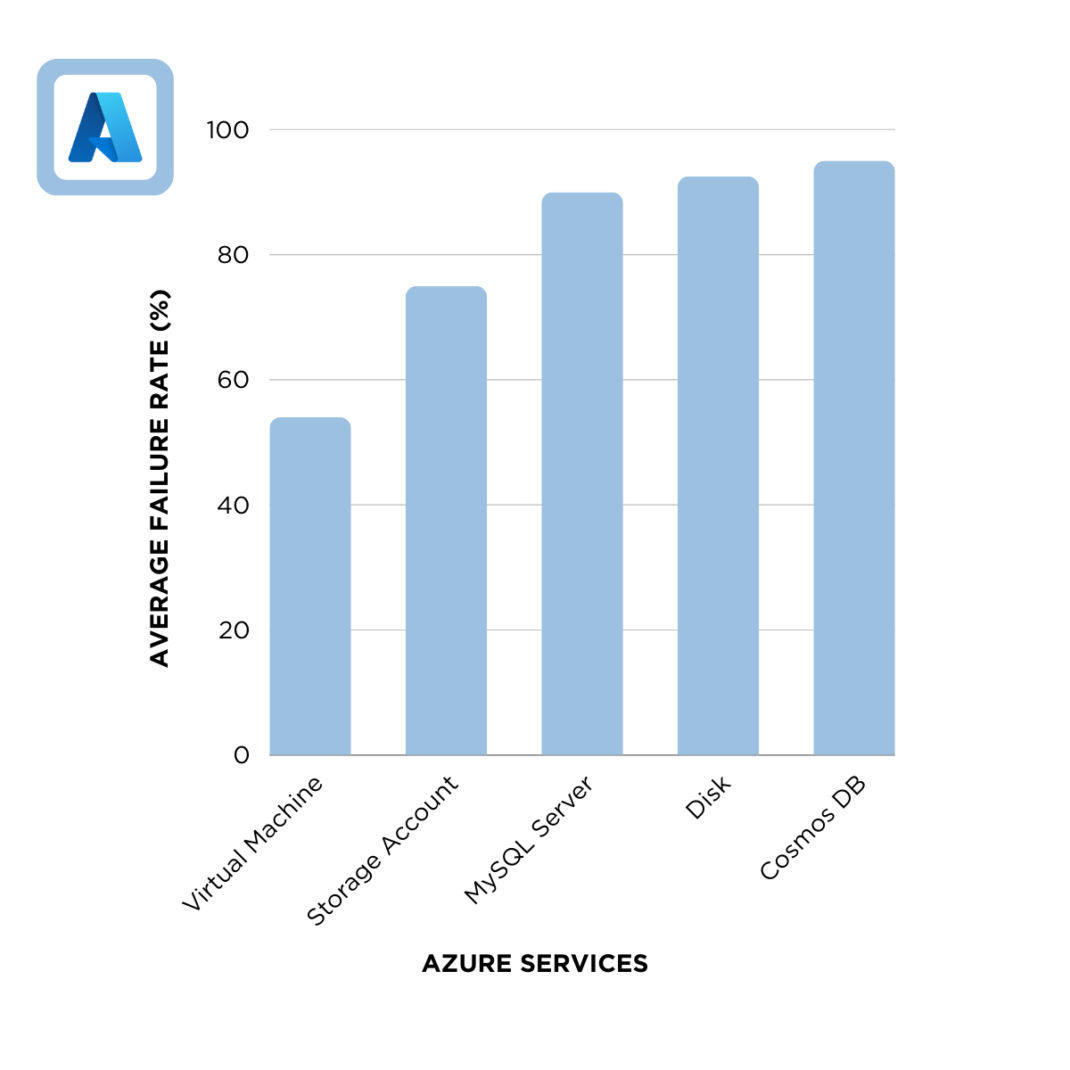 Figure 2: Failure Rate of Azure Controls with respect to encryption.
Figure 2: Failure Rate of Azure Controls with respect to encryption.
Azure demonstrates higher challenges in encryption across several key services, emphasizing a critical need for enhanced security measures:
- Virtual Machine: A 54% failure rate suggests a need for stronger encryption practices in virtualized resources, indicating that users should improve their understanding and application of encryption.
- Storage Account: With a 75% failure rate, significant risks to data storage solutions are evident, pointing to the necessity for users to enhance their grasp of encryption techniques.
- MySQL Server: A concerning 90% failure rate highlights major gaps in database server security, emphasizing the need for users to better understand and implement encryption best practices.
- Disk: At 93%, encryption practices in persistent storage devices are notably lacking, calling for users to significantly improve their encryption measures.
GCP Encryption Controls:****
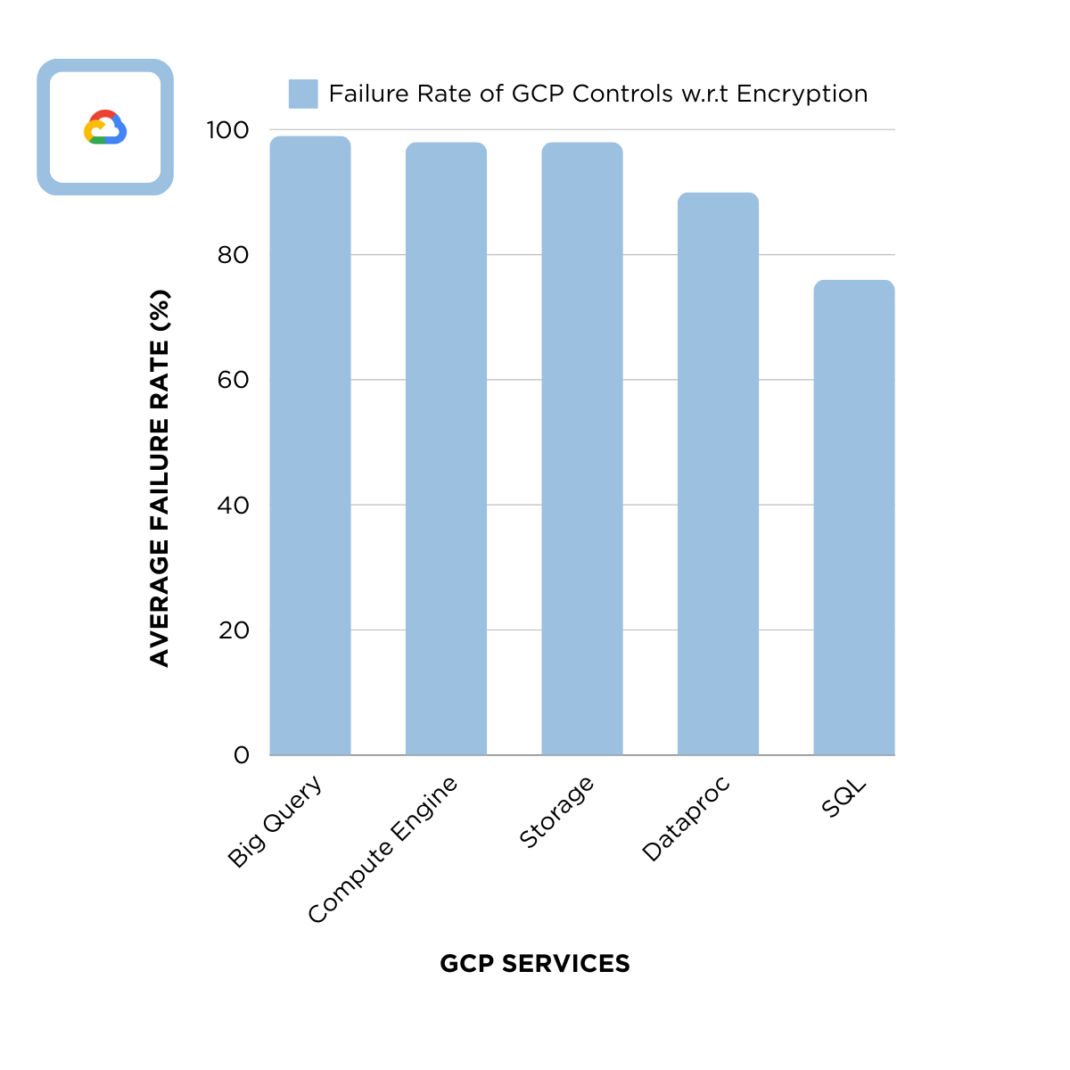 Figure 3: Failure Rate of GCP Controls with respect to encryption.
Figure 3: Failure Rate of GCP Controls with respect to encryption.
GCP exhibits alarmingly high failure rates in encryption practices, particularly in data processing and storage services:
- Big Query: A staggering 99% failure rate suggests widespread issues in securing data analytics services, highlighting an urgent need for users to better grasp encryption practices.
- Compute Engine: With a 98% failure rate, there are severe deficiencies in encrypting virtual machines, underscoring the necessity for users to improve their understanding of encryption.
- Storage: Another 98% failure rate points to significant vulnerabilities in cloud storage, indicating that users need to substantially enhance encryption strategies.
- Dataproc: A 90% failure rate highlights substantial risks in data processing services, emphasizing the importance for users to increase their grasp of encryption measures.
- SQL: At 76%, there are considerable gaps in securing SQL databases, suggesting that users need to focus more on understanding and implementing robust encryption practices.
These insights highlight the pressing need for a stronger grasp of encryption practices across all cloud platforms. Addressing these areas of weakness is crucial for enhancing security and safeguarding data against emerging threats.
What Is Cloud Encryption, and How Does It Safeguard Your Data?
With the failure rates above, we thought it worth diving into cloud encryption, and why and how it’s crucial to safeguarding data. Cloud encryption is a data security process that converts readable data (plaintext) into an unreadable format (ciphertext) before it is sent to or stored in the cloud.
Cloud encryption ensures the protection of sensitive information, whether it is in transit over the internet or at rest in cloud storage. Encryption algorithms are employed to transform data of any type into an encoded format that is only decipherable with a specific decryption key. This means that even if an unauthorized entity intercepts or tries to steal the data, it remains useless to them unless they possess the decryption key.
There are two primary states in which cloud encryption works:
- Encrypting Data in Transit: This protects data as it moves between locations, often outside secure networks, making it vulnerable to interception. Typically, data in transit is automatically encrypted/decrypted using the HTTPS protocol with SSL.
- Encrypting Data at Rest: This ensures that data stored in the cloud is virtually useless to anyone without the encryption key, even if lost, stolen, or mistakenly exposed. Keys are exclusively available to authorized users, and software applications manage encryption/decryption for data at rest.
There are two primary types of data encryption used in the cloud:
- Symmetric Encryption: In this method, the same key is used for both encryption and decryption, making it faster but somewhat less secure because anyone with access to the encryption key can decode the data. It is often used for bulk data encryption.
- **Asymmetric Encryption:******This approach uses two keys, a public key and a private key, for encoding and decoding data. While these keys are related, they are not the same. Asymmetric encryption is more secure because public keys cannot expose private keys, and private keys do not need to be transmitted. It also serves as a form of authentication, allowing a sender to prove the origin of a file with a private key.
The Benefits of Cloud Data Encryption
Below are some of the ways cloud encryption ensures your data remains impervious to potential threats.
- Ensures Round the Clock Data Protection: Data is ever-changing, and attackers never rest, so the need to protect it is constant. Cloud encryption ensures your data is safeguarded 24/7, whether in transit or at rest in the cloud. This constant protection minimizes the risk and keeps your data safe.
- Mitigates Insider Threats: Insider threats can be as damaging as external ones. Cloud encryption is a robust defense mechanism that limits access to sensitive data exclusively to authorized personnel. This significantly reduces the risk of insider threats and ensures your data remains in trusted hands.
- Overcomes Insecure APIs: Application Programming Interfaces (APIs) are essential for modern cloud-based applications, but they often pose data security risks. Cloud encryption mitigates the risk by ensuring that even if APIs are compromised, the data they handle remains indecipherable without the encryption keys.
- Maintains Organizational Integrity: Data breaches can be disastrous for data security as well as an organization's reputation and integrity. Cloud encryption provides an added layer of defense that can prevent data breaches from happening. And if your data remains secure, then you’ll never need to publicly disclose a breach, preserving your organization's reputation.
- Ensures Protection for Multiple Devices: In today's mobile and remote work environment, data is accessed from many devices. Cloud encryption ensures that data remains secure regardless of the device used. This flexibility is invaluable for businesses embracing the digital age.
- Ensures Compliance and Regulatory Requirements: Compliance with data protection regulations is a non-negotiable aspect of modern business. Cloud encryption aligns with stringent encryption standards mandated by rules and regulations like HIPAA, PCI DSS, and FIPS. This not only keeps your data safe but also keeps your organization in compliance with the law.
In summary, cloud encryption is a fundamental data protection measure in cloud environments, ensuring data security and privacy during transit and at rest through encryption algorithms. When it comes to safeguarding your valuable data, cloud encryption emerges as the stalwart defender you need, and there are many benefits of cloud encryption in elevating your data security.
Scenario-based Example of Security Risks
The image below will give insight into how cloud-based environments are usually designed. The environment is based on the AWS cloud and depicts data exchange among different resources.
The Amazon Virtual Private Cloud (Amazon VPC) consists of 2 subnets, one public and the other a private subnet, each containing an Elastic Compute Cloud (EC2) instance. The public EC2 instance stores some data in Amazon Relational Database Service (Amazon RDS), fetched quickly by the AWS Lambda service and sent to the Amazon S3 bucket.
The S3 bucket hosts static website content that is distributed using the Amazon CloudFront service.
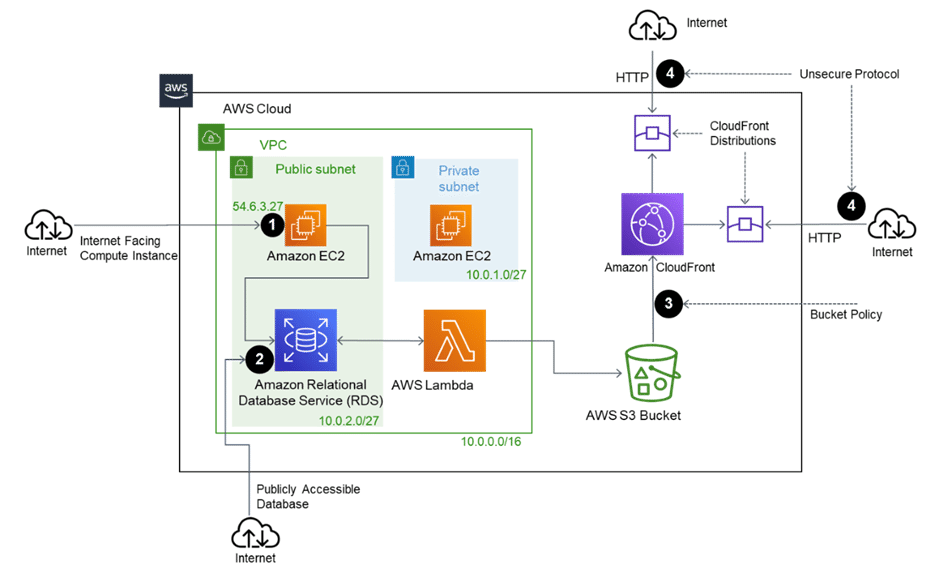
Below are some points that highlight the areas in this scenario where security risks, including lack of encryption, might be present:
- The EC2 instance is public-facing, making it accessible over the internet. The instance can also connect to the RDS database, which, if not password-protected, can be used to access the stored data.
- Similarly, the RDS database is also publicly accessible, and if not protected, the lack of encryption can expose the stored data.
- The S3 Bucket Policy governs the permissions on the bucket. If not restricted, it allows anyone to access and manipulate the data residing in the S3 bucket. The bucket policies should also enforce encryption of data in transit.
- S3 Bucket hosts static website content delivered using CloudFront distributions over HTTP protocol. The insecure protocol makes the website and any information it hosts vulnerable to attack.
To prevent the risks presented by lack of or poor encryption in this scenario and others presented in a multi-cloud environment, it’s best to employ certain security best practices.
Security Best Practices for Data Encryption
Below are some security best practices for data encryption in various CSPs, along with Qualys Control IDs (also called CIDs), that will help strengthen the cloud security posture of these CSPs.
Amazon Web Services (AWS):
- Use AWS Key Management Service (KMS): AWS KMS allows you to create and control encryption keys for your data. You can use it to encrypt data at rest, in transit, and manage access.
Qualys TotalCloud Control ID: 203 - Enable Server-Side Encryption: Use server-side encryption options for services like Amazon S3, RDS, and EBS. AWS handles key management and encryption for you.
_Qualys TotalCloud Control ID: 168 _ - Implement Encryption in Transit: Use protocols like SSL/TLS to encrypt data in transit. This is crucial for securing data between your AWS services and clients.
_Qualys TotalCloud Control ID: 252 _
Microsoft Azure:
- Azure Key Vault: Use Azure Key Vault for secure key management. It provides a central repository for your encryption keys and secrets.
_Qualys TotalCloud Control ID: 50230 _ - Transport Layer Security (TLS): Configure your applications to use TLS for data in transit. Azure provides tools for creating and managing SSL certificates.
_Qualys TotalCloud _Control ID: 50365
Google Cloud Platform (GCP):
- Google Cloud Key Management Service (KMS): Use Google Cloud KMS to create and manage encryption keys for your data.
_Qualys TotalCloud Control ID: 52005 _ - Data Encryption at Rest: Enable encryption at rest for Google Cloud Storage and Google Compute Engine. GCP handles the key management.
_Qualys TotalCloud Control ID: 52117 _
Enhancing Cloud Security with Qualys TotalCloud
In our research, we examined data from big cloud service providers like AWS, Azure, and GCP. We found that many basic security settings are often overlooked by the cloud users. This oversight is significant for cloud protection. It may occur due to a lack of security planning, unfamiliarity with the latest technology, or unawareness of the associated risks. Employing security best practices for data protection like those above can help ensure better encryption and with it, better data security. Or, a solution like TotalCloud can be employed to do the work for you.
Within its robust cloud native application protection platform (CNAPP), Qualys TotalCloud provides complete cloud security posture management (CSPM) capabilities and helps organizations keep their cloud safe and understand gaps in their security configuration and how to remediate them.
How Qualys TotalCloud Can Help Mitigate the Misconfiguration
Qualys TotalCloud provides various in-house encryption-based security controls that ensure resources like Amazon S3, Database instances, VM (Virtual Machine) disks, etc., are compliant. If not, these misconfigurations are highlighted accordingly.
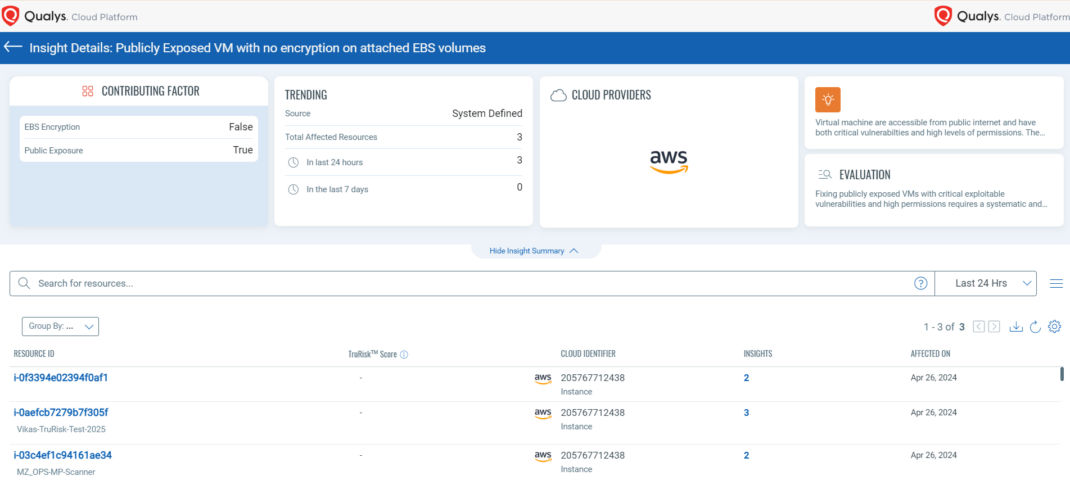 Figure 5: Qualys TotalCloud TruRisk Insight details show a Publicly Exposed VM with no encryption on attached EBS volumes.
Figure 5: Qualys TotalCloud TruRisk Insight details show a Publicly Exposed VM with no encryption on attached EBS volumes. 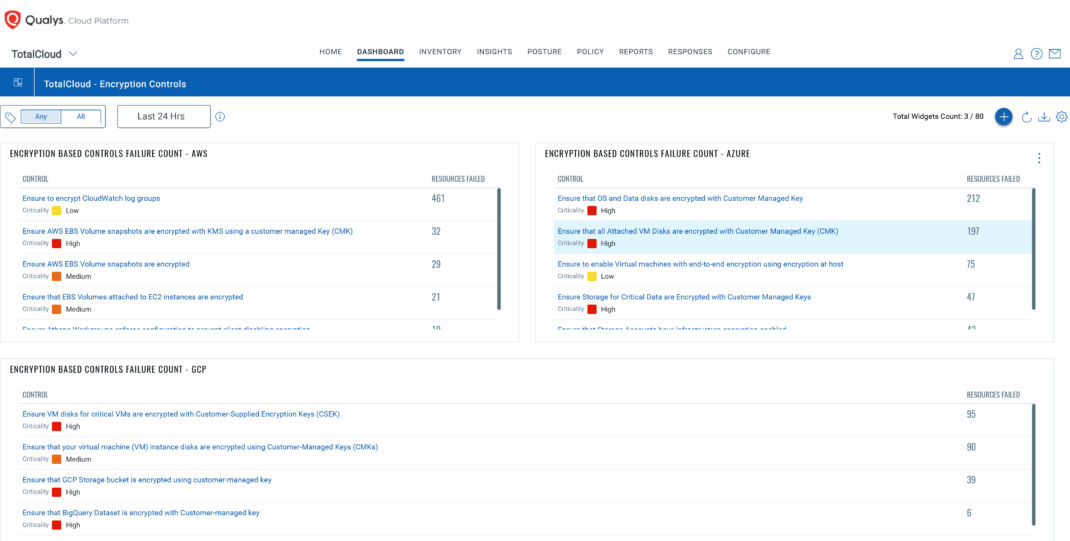 Figure 6: TotalCloud Dashboard highlighting top failing encryption-related controls for AWS, Azure, and GCP.
Figure 6: TotalCloud Dashboard highlighting top failing encryption-related controls for AWS, Azure, and GCP.
The above image shows a Qualys TotalCloud dashboard with controls based on encryption across multiple CSPs. Some of the controls make sure that services have encryption enabled and are safe from attacks:
- “Ensure AWS EBS Volume snapshots are encrypted with KMS using a customer-managed Key (CMK).”
- “Ensure that the GCP Storage bucket is encrypted using a customer-managed key.”
- “Ensure that "OS (Operating System) and Data" disks are encrypted with Customer Managed Key.”
Conclusion
Data encryption is a fundamental component of cloud security. By implementing best practices for data encryption in AWS, Azure, and GCP, you can ensure your data's confidentiality, integrity, and availability. These best practices protect your organization from data breaches and enhance customer trust and compliance with data protection regulations. Make data security a priority in your cloud strategy to reap the benefits of the cloud without compromising safety.
Start your Qualys TotalCloud experience to continuously discover resources across AWS, Microsoft Azure, and GCP and ensure they comply with your basic security needs. Qualys TotalCloud allows you to create custom controls with the help of a user-friendly UI and deploy them on the fly so that you can start evaluating your resources ASAP.
7.2 High
AI Score
Confidence
High