
Conti Ransomware
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Conti is a sophisticated Ransomware-as-a-Service (RaaS) model first detected in December 2019. Since its inception, its use has grown rapidly and has even displaced the use of other RaaS tools like Ryuk. The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) issued a warning about Conti in Sept 2021, noting that they had observed it being used in more than 400 cyberattacks globally, though concentrated in North America and Europe.
The most common initial infection vectors used are spear phishing and RDP (Remote Desktop Protocol) services. Phishing emails work either through malicious attachments, such as Word documents with an embedded macro that can be used to drop/download BazarLoader, Trickbot, IceID trojans, or via social engineering tactics employed to get the victim to provide additional information or access credentials. Following initial access, attackers download and execute a Cobalt Strike beacon DLL to gather information about domain admin accounts. Additionally, threat actors use Kerberos attacks to attempt to get admin hash in order to conduct brute force attacks.
A Conti affiliate recently leaked what has been dubbed the Conti playbook. The playbook revealed that Conti actors also exploit vulnerabilities in unpatched assets to escalate privileges and move laterally across a victim’s network. They check for the "PrintNightmare" vulnerability (CVE-2021-34527) in Windows Print spooler service, EternalBlue vulnerability (CVE-2017-0144) in Microsoft Windows Server Message Block, and the "Zerologon" vulnerability (CVE-2020-1472) in Microsoft Active Directory Domain Controller. The playbook has been translated from Russian to English by security researchers and has provided other useful Indicators of Compromise (IoC).
Conti actors also use the RouterScan tool to identify router devices in a provided range of IPs and attempt to find logins/passwords from a standard list available with the RouterScan tool. They then install AnyDesk or Atera on the target machine to maintain an open communication channel. Like other ransomware attacks, Conti actors exfiltrate data from victims’ networks to cloud storage services like MEGA and then deploy Conti ransomware. To upload data on cloud storage Conti uses open-source Rclone command-line software. They use a double extortion approach in which they demand a ransom to release the encrypted data or threaten to publicly release it if a ransom is not paid. They may also sell the data to the highest bidder.
Technical Details:
Conti ransomware uses obfuscation. The most notable use is to hide various Windows API calls used by the malware. It is common for some malware to lookup API calls during execution. Initially, it brings import module names then decrypts the API names and gets their addresses.
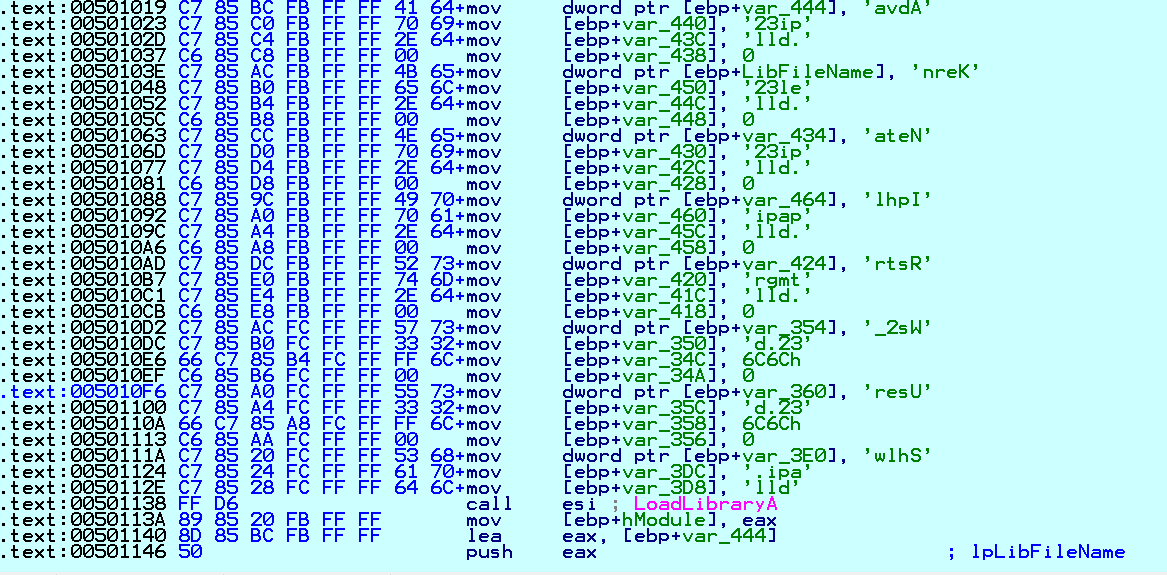 Fig. 1 De-obfuscation of Windows API
Fig. 1 De-obfuscation of Windows API
Conti uses a unique String Decryption Routine that is applied to almost every string text or API name used by the malware as shown in Fig. 2:
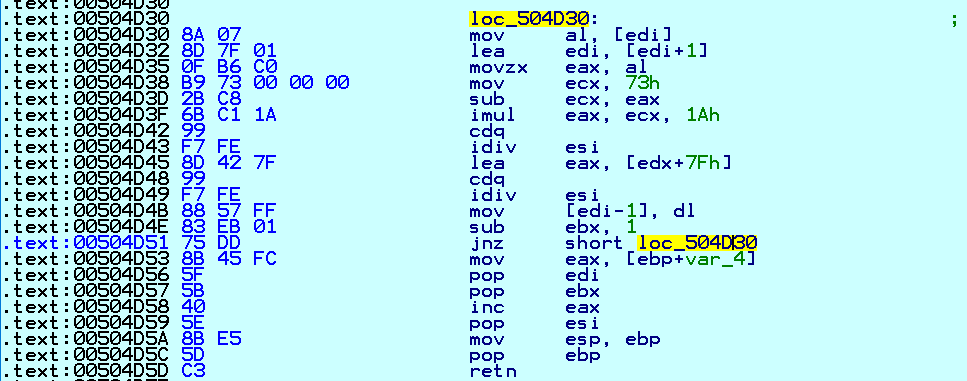 Fig. 2 String Decryption Routine
Fig. 2 String Decryption Routine
After getting API addresses, it calls for CreateMutexA API with the Mutex Value of "CONTI" as shown below in Fig. 3:
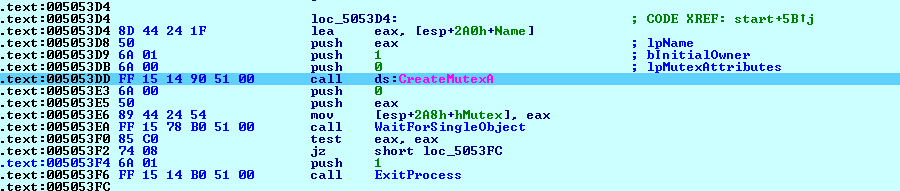 Fig. 3 Create Mutex
Fig. 3 Create Mutex
It deletes Windows Volume Shadow Copies and also resizes shadow storage for drives C to H:
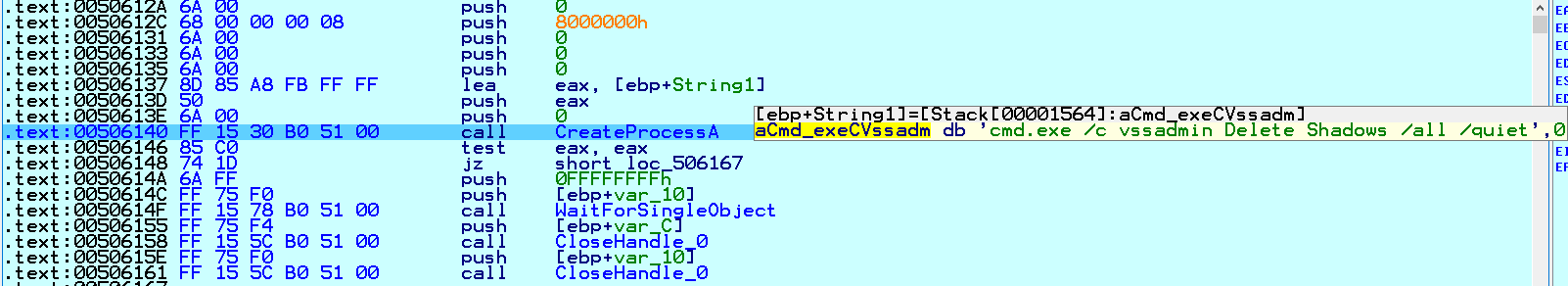 Fig. 4 Deletes Windows Volume Shadow Copy
Fig. 4 Deletes Windows Volume Shadow Copy
Next, Conti executes commands for stopping potential Windows Services related to antivirus, security, backup, database, and email solutions:
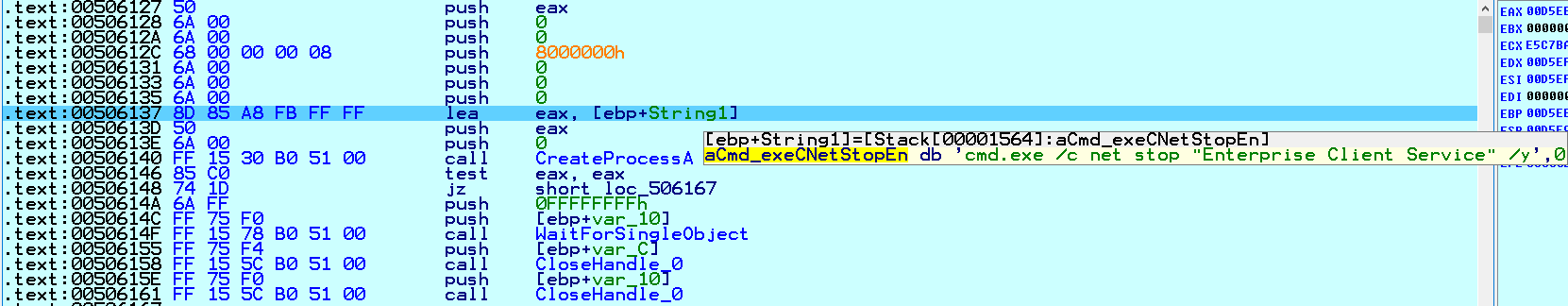 Fig. 5 Stop Potential Windows Services
Fig. 5 Stop Potential Windows Services
The table below contains the names of the Windows Services that Conti stopped by calling the code in Fig. 5 in the loop.
| MSSQL$BKUPEXEC | MSSQL$SQLEXPRESS | MSSQLFDLauncher$SHAREPOINT |
|---|---|---|
| MSSQL$ECWDB2 | MSSQL$SYSTEM_BGC | MSSQLFDLauncher$SQL_2008 |
| MSSQL$PRACTICEMGT | MSSQL$TPS | MSSQLFDLauncher$SYSTEM_BGC |
| MSSQL$PRACTTICEBGC | MSSQL$TPSAMA | MSSQLFDLauncher$TPS |
| MSSQL$PROD | MSSQL$VEEAMSQL2008R2 | MSSQLFDLauncher$TPSAMA |
| MSSQL$PROFXENGAGEMENT | MSSQL$VEEAMSQL2008R2 | MSSQLSERVER |
| MSSQL$SBSMONITORING | MSSQL$VEEAMSQL2012 | MSSQLServerADHelper |
| MSSQL$SHAREPOINT | MSSQLFDLauncher | MSSQLServerADHelper100 |
| MSSQL$SOPHOS | MSSQLFDLauncher$PROFXENGAGEMENT | MSSQLServerOLAPService |
| MSSQL$SQL_2008 | MSSQLFDLauncher$SBSMONITORING | MySQL57 |
| Acronis VSS Provider | Mfemms | DCAgent |
| AcronisAgent | Mfevtp | EhttpSrv |
| AcrSch2Svc | MMS | Ekrn |
| Antivirus | Mozyprobackup | Enterprise Client Service |
| ARSM | MsDtsServer | EPSecurityService |
| AVP | MsDtsServer100 | EPUpdateService |
| BackupExecAgentAccelerator | MsDtsServer110 | EraserSvc11710 |
| BackupExecAgentBrowser | MSExchangeES | EsgShKernel |
| BackupExecDeviceMediaService | MSExchangeIS | ESHASRV |
| BackupExecJobEngine | MSExchangeMGMT | FA_Scheduler |
| BackupExecManagementService | MSExchangeMTA | MSOLAP$TPSAMA |
| BackupExecRPCService | MSExchangeSA | McShield |
| BackupExecVSSProvider | MSExchangeSRS | McTaskManager |
| Bedbg | msftesql$PROD | Mfefire |
| IISAdmin | MSOLAP$SQL_2008 | Klnagent |
| IMAP4Svc | MSOLAP$SYSTEM_BGC | MSOLAP$TPS |
Conti also leverages the Windows Restart Manager to close applications and services that are running in order to make them available for encryption and to maximize the damage:
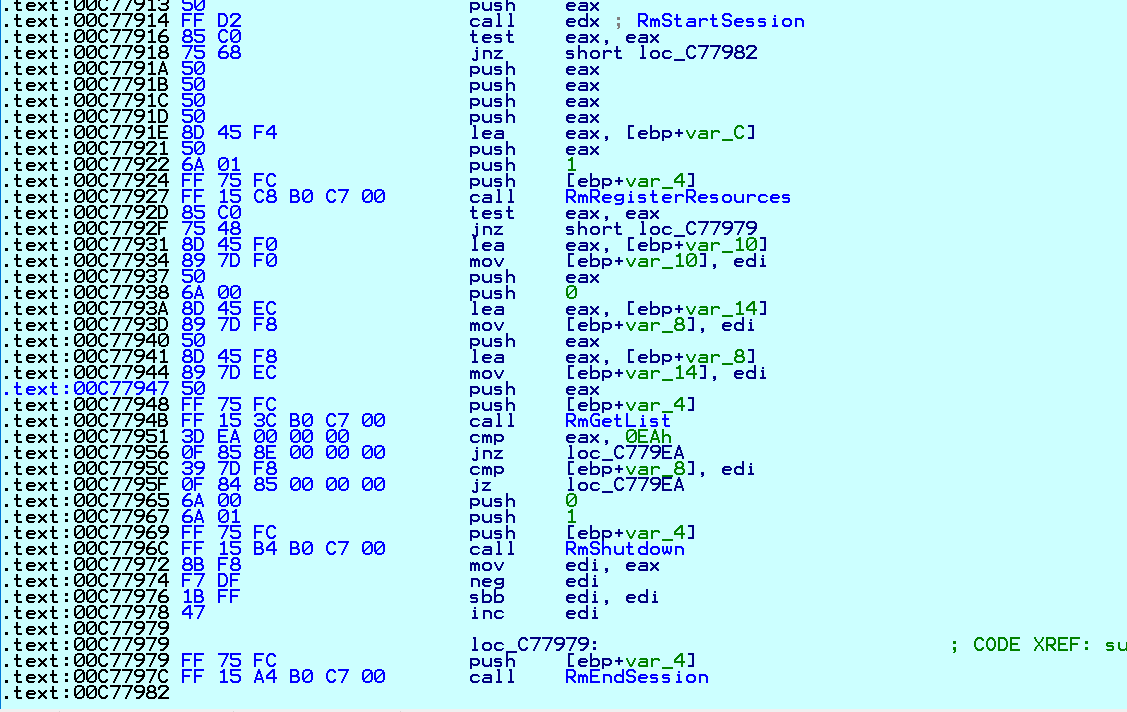 Fig. 6 Unlock files with Windows Restart Manager
Fig. 6 Unlock files with Windows Restart Manager
It collects information about drives and drive types present on compromised systems:
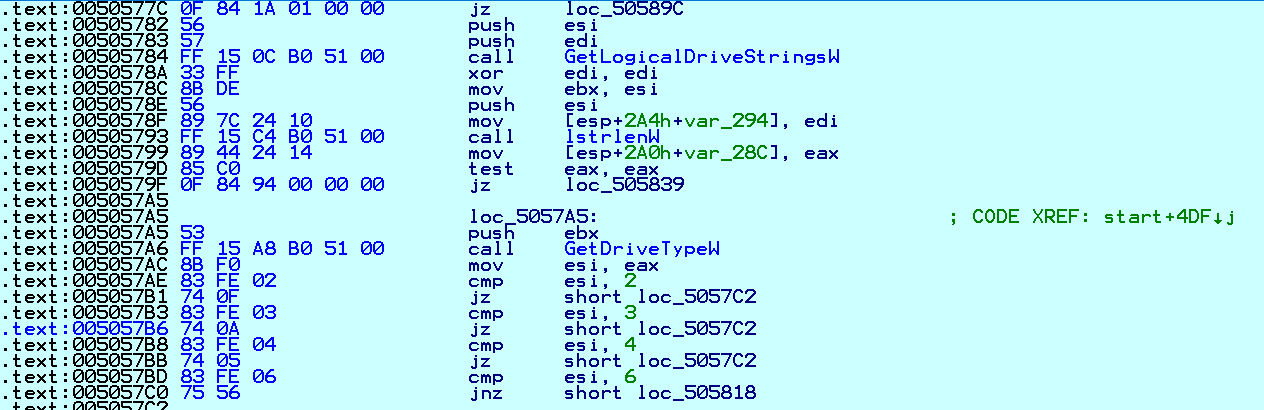 Fig. 7 Collect Drives Information
Fig. 7 Collect Drives Information
As shown in Fig. 8, Conti uses multi-threaded tactics. It calls CreateIoCompletionPort API to create multiple instances of worker threads into memory to wait for data. Once the file listing is completed, it is passed to the worker threads. Utilizing the computing power of multi-core CPUs, the data is quickly encrypted:
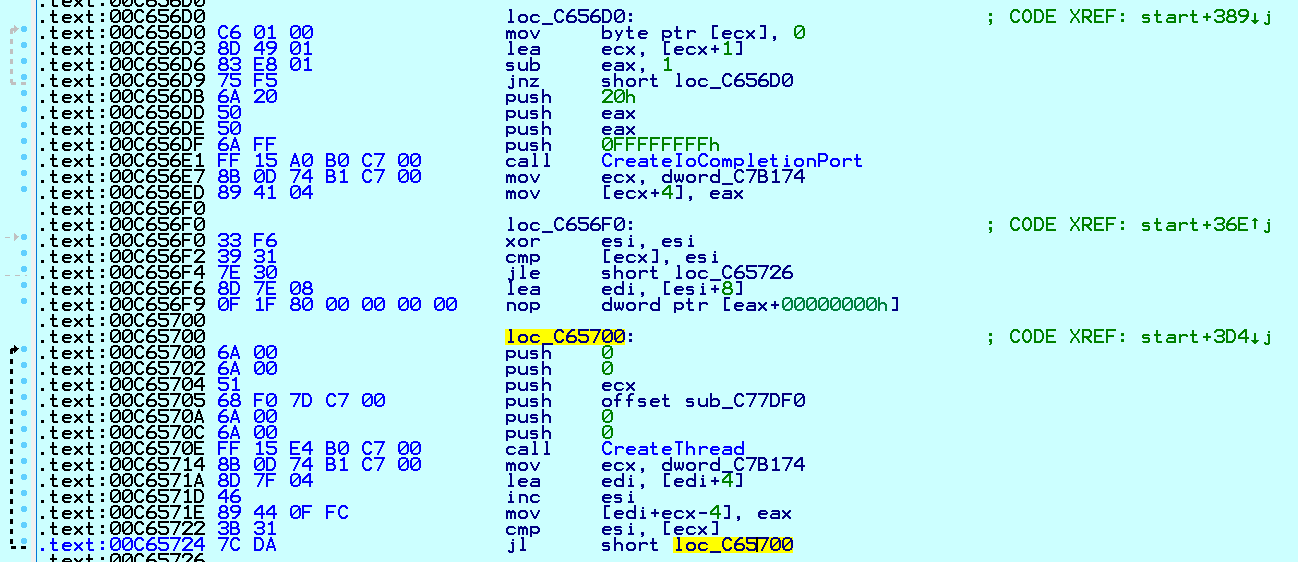 Fig. 8 Implementation of Multi-threaded Processing
Fig. 8 Implementation of Multi-threaded Processing  Fig. 9 Multiple Threads Perform File Encryption
Fig. 9 Multiple Threads Perform File Encryption
Conti then iterates files on the local system and those on remote SMB network shares to determine what data to encrypt. It looks for folders and drives shared on remote systems using NetShareEnum API. If the remote share is accessible, it encrypts the files present in that share:
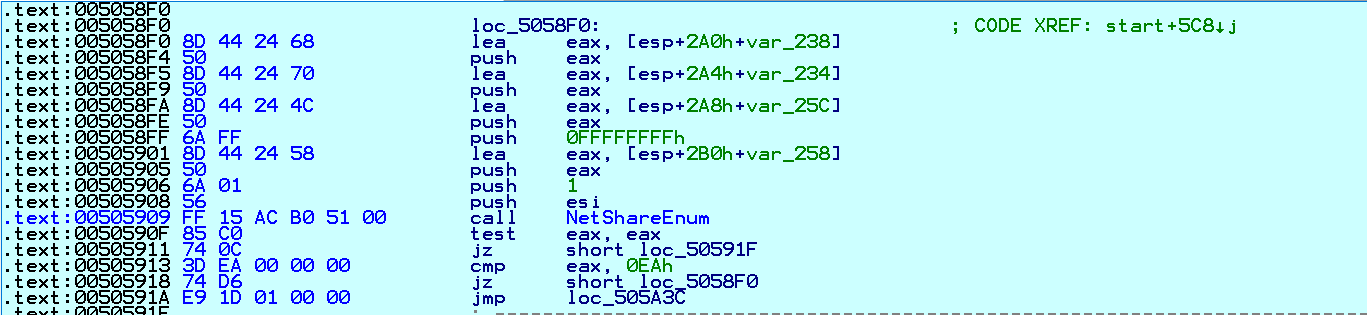 Fig. 10 Getting Info of Remote Shares
Fig. 10 Getting Info of Remote Shares
It collects ARP cache information from the local system using the GetIpNetTable API. ARP cache information is a list of all the systems with which the computer recently communicated. It checks for "172.", "192.168." etc., on the collected IP list. If an IP address is in a different range it skips that system from encryption:
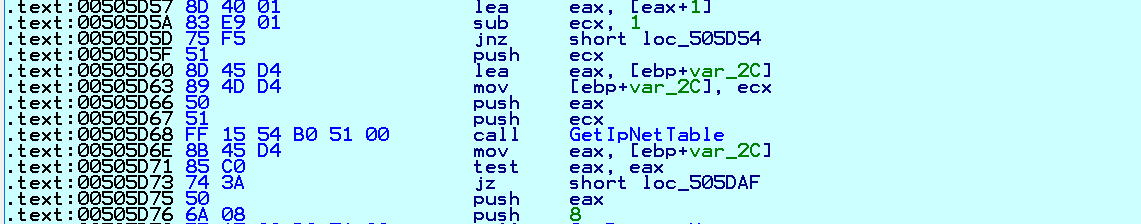 Fig. 11 Collect ARP Cache Information
Fig. 11 Collect ARP Cache Information
It uses an AES-256 encryption key per file with a hard-codedRAS-4096 public encryption key. As shown in Fig. 12, the 0x6610 parameter is used while calling the CryptGenKey API. 0x6610 is the value of the CALG_AES_256 identifier and is only alg_id:
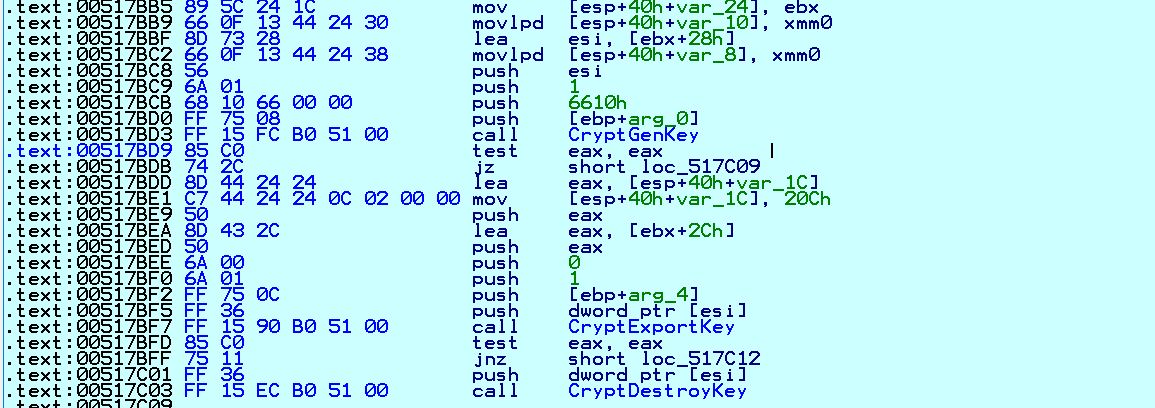 Fig. 12 Create CALG_AES_256 Key
Fig. 12 Create CALG_AES_256 Key
Conti has a unique feature that allows attackers to perform file encryption in command line mode:
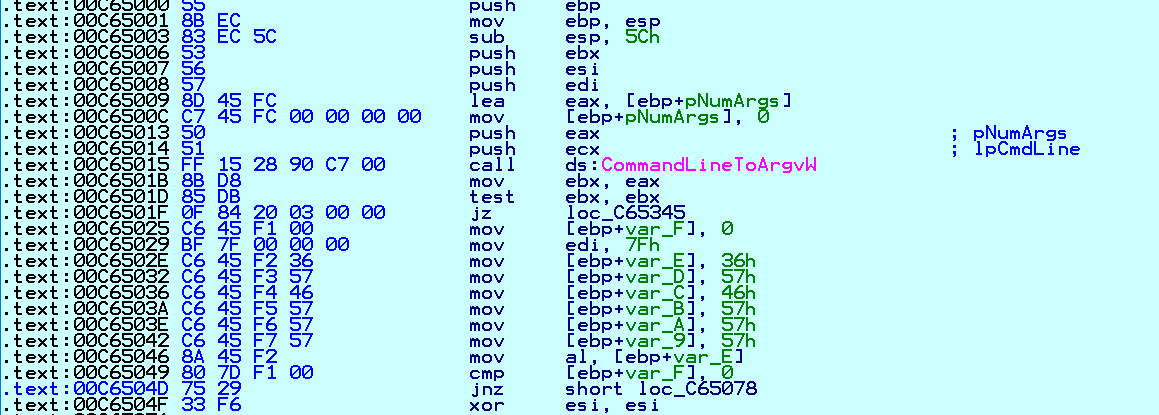 Fig. 13 Command Line Mode of Operation
Fig. 13 Command Line Mode of Operation
Modes of Operation
Conti allows 2 command line modes--encrypt-mode and - h:
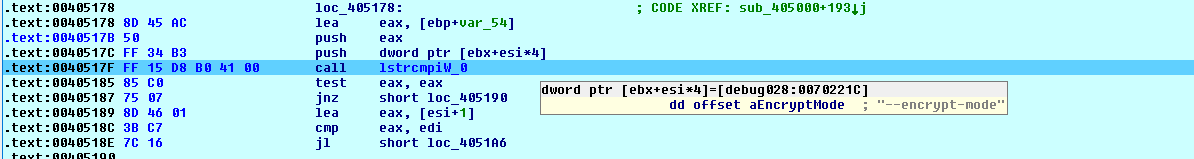 Fig. 14 Command Line
Fig. 14 Command Line --encrypt-mode Mode
--encrypt-mod marks which files are encrypted. There are 3 options for its value:all, local, and network. By default, ransomware runs with the all parameter:
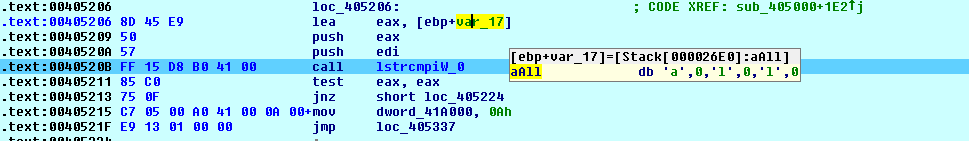 Fig. 15 Command Line
Fig. 15 Command Line --encrypt-mode with Value all
In all, encryption carried out for - local and network. network means that shared resources on the local network will be encrypted:
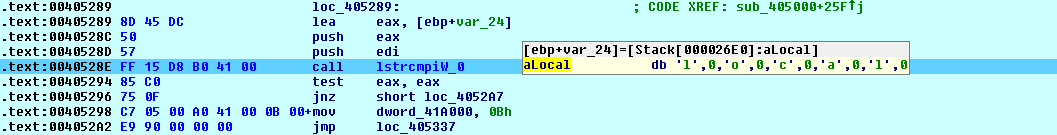 Fig. 16 Command Line
Fig. 16 Command Line --encrypt-mode Mode with Value local 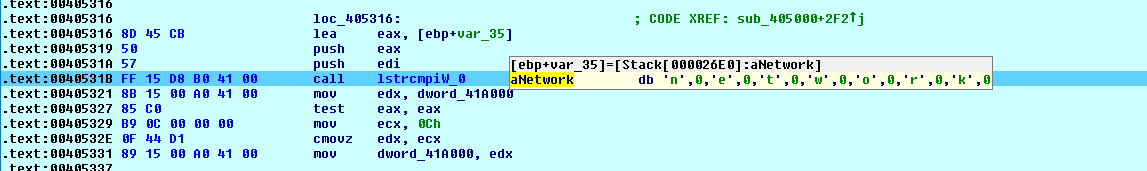 Fig. 17 Command Line
Fig. 17 Command Line --encrypt-mode Mode with Value network
In command line -h mode, the parameter may contain the name of a file that lists the DNS and NetBIOS addresses of remote servers. The malware will then build a list of folders to ignore during encryption:
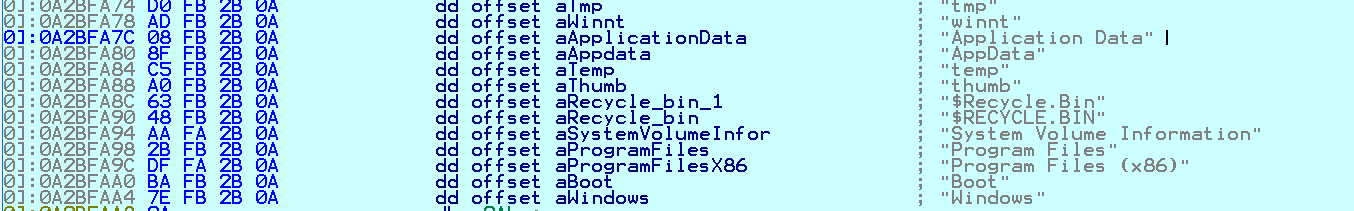 Fig. 18 Folders Ignored in Encryption
Fig. 18 Folders Ignored in Encryption
It skips the following extensions during encryption: .exe, .dll, .sys, .lnk, and .CONTI. It appends the file extension .CONTI and creates a ransom note named CONTI_README.txt in every folder to notify users about the infection:
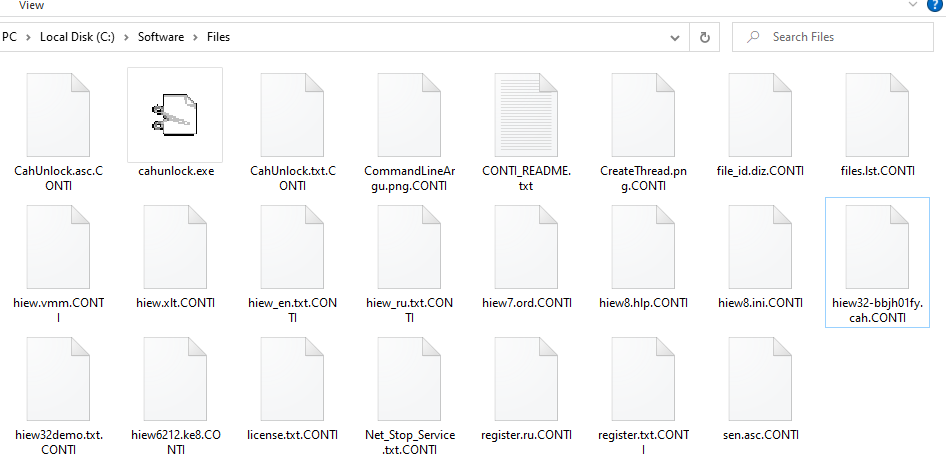 Fig. 19 __CONTI” Extension Appended to Files
Fig. 19 __CONTI” Extension Appended to Files
The Ransom Note:
The ransom note and the note’s file information are present in the resource of malware files:
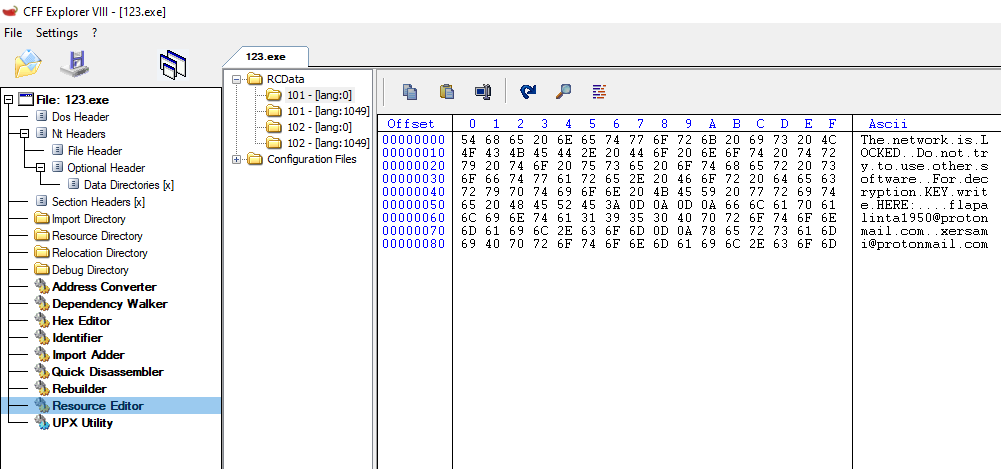 Fig. 20 Ransom Note Content
Fig. 20 Ransom Note Content 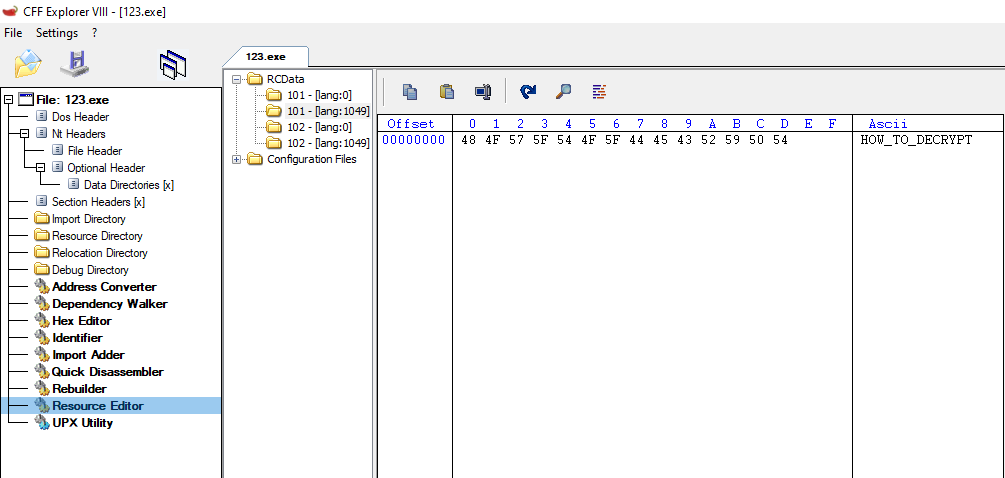 Fig. 21 Ransom Note Name
Fig. 21 Ransom Note Name
It calls the LoadResource API to get ransom note-related information:
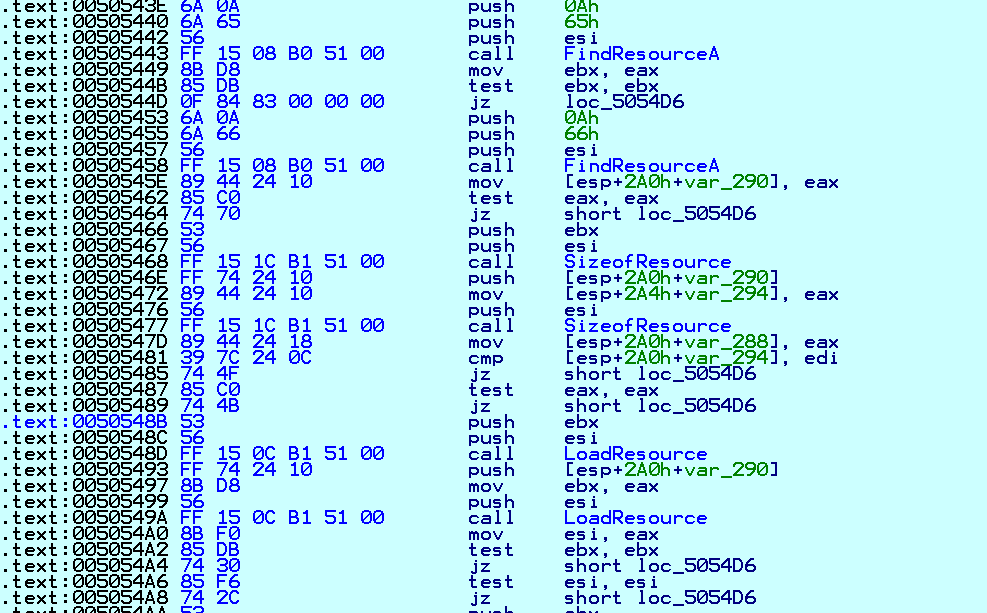 Fig. 22 Code to Collect Data Related to the Ransom Note
Fig. 22 Code to Collect Data Related to the Ransom Note
The ransom note contains 2 email addresses to get in touch with the attackers. The addresses are unique for each victim:
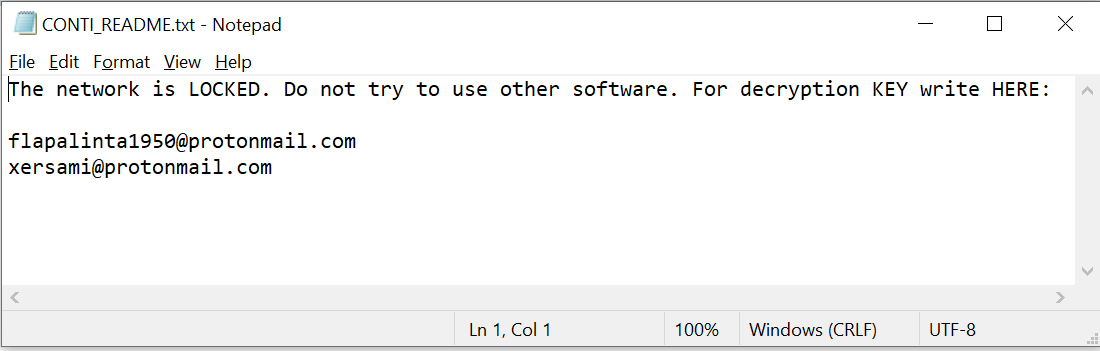 Fig. 23 Ransom Note
Fig. 23 Ransom Note
IoC:
eae876886f19ba384f55778634a35a1d975414e83f22f6111e3e792f706301fe
TTP Map:
| Initial Access | Execution | Persistence | Privilege Escalation | Defense Evasion | Credential Access | Discovery | Lateral Movement | Collection | Command and control | Exfiltration | Impact |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Valid Accounts (T1078) | Command and Scripting Interpreter: Windows Command Shell (T1059.003) | Valid Accounts (T1078) | Process Injection: Dynamic-link Library Injection (T1055.001) | Obfuscated Files or Information (T1027) | Brute Force (T1110) | System Network Configuration Discovery (T1016) | Remote Services: SMB/Windows Admin Shares (T1021.002) | Archive Collected Data: Archive via Utility (T1560.001) | Remote file copy (T1105) | Exfiltration Over Web Service: Exfiltration to Cloud Storage (T1567.002) | Data Encrypted for Impact (T1486) |
| Phishing: Spearphishing Attachment (T1566.001) | Native Application Programming Interface (API)(T1106) | External Remote Services (T1133) | Valid accounts: domain accounts (T1078.002) | Process Injection: Dynamic-link Library Injection (T1055.001) | Steal or Forge Kerberos Tickets: Kerberoasting (T1558.003) | System Network Connections Discovery (T1049) | Taint Shared Content (T1080) | Service Stop (T1489) | |||
| Phishing: Spearphishing Link (T1566.002) | Windows Management Instrumentation (T1047) | Scheduled task/job: scheduled task (T1053.005) | Deobfuscate/Decode Files or Information (T1140) | OS credential dumping (T1003) | Process Discovery (T1057) | Exploitation of Remote Services (T1210) | Inhibit System Recovery (T1490) | ||||
| Exploit public-facing application (T1190) | User execution (T1204) | Startup item (T1165) | Impair defenses: disable or modify tools (T1562.001) | Credentials from password stores (T1555) | File and Directory Discovery (T1083) | Lateral tool transfer (T1570) | |||||
| Scheduled task/job: scheduled task (T1053.005) | Boot or logon autostart execution: Winlogon Helper DLL (T1547.004) | Network Share Discovery (T1135) | |||||||||
| Command and Scripting Interpreter: PowerShell (T1059.001) | Remote System Discovery (T1018) | ||||||||||
| Network Service Scanning (T1046) | |||||||||||
| Permission groups discovery: domain groups (T1069.002) | |||||||||||
| System information discovery (T1082) | |||||||||||
| System owner/user discovery (T1033) | |||||||||||
| Security software discovery (T1063) | |||||||||||
| Account Discovery: Local Account (T1087.001) | |||||||||||
| Permissions Group Discovery: Local Groups (T1069.001) | |||||||||||
Summary
To defend against threats, Qualys recommends good cyber hygiene practices, and moving to a preventative approach by keeping network configurations, backup, application access, and patching up-to-date.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C