
Microsoft and Adobe Patch Tuesday, March 2024 Security Update Review
8.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
HIGH
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
9 High
AI Score
Confidence
High
5.1 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
HIGH
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:H/Au:N/C:P/I:P/A:P
0.001 Low
EPSS
Percentile
38.0%
Welcome to another insightful dive into Microsoft's Patch Tuesday! This month's security updates address a significant number of CVEs, underscoring the ongoing battle against digital vulnerabilities. We invite you to join us to review and discuss the details of these security updates and patches.
Microsoft Patch Tuesday for March 2024
Microsoft Patch Tuesday's March 2024 edition addressed 64 vulnerabilities, includingtwo critical and58important severity vulnerabilities. In this month's security updates, Microsoft has not addressed any zero-day vulnerabilities known to be exploited in the wild. Microsoft has also addressedfour vulnerabilities in Microsoft Edge (Chromium-based). The vulnerabilities have been patched earlier this month.
Microsoft Patch Tuesday, March edition includes updates for vulnerabilities in Microsoft Office and Components, SQL Server, Visual Studio Code, .NET, Microsoft Azure Kubernetes Service, Windows Hyper-V, Windows OLE, Windows Installer, Microsoft Graphics Component, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The March 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 2 | Important: 2 |
| Denial of Service Vulnerability | 6 | Critical: 1 |
| Important: 5 | ||
| Elevation of Privilege Vulnerability | 24 | Important: 24 |
| Information Disclosure Vulnerability | 6 | Important: 6 |
| Remote Code Execution Vulnerability | 18 | Critical: 1 |
| Important: 17 | ||
| Security Feature Bypass Vulnerability | 3 | Important: 3 |
Adobe Patches for March 2024
Adobe has released** six** security advisories to address 58 vulnerabilities in Adobe Experience Manager, Adobe Premiere Pro, Adobe ColdFusion, Adobe Bridge, Adobe Lightroom, and Adobe Animate. Out of 58, eight vulnerabilities are given critical severity ratings. On successful exploitation, the vulnerabilities may lead to memory leaks, potential code execution, security feature bypass, and arbitrary file system read.
Other Critical Severity Vulnerabilities Patched in March Patch Tuesday Edition
CVE-2024-21407: Windows Hyper-V Remote Code Execution Vulnerability
An authenticated attacker on a guest VM must send specially crafted file operation requests to hardware resources to perform remote code execution on the host server. Successful exploitation of this vulnerability requires an attacker to gather information specific to the environment and take additional actions before exploitation to prepare the target environment.
CVE-2024-21408: Windows Hyper-V Denial of Service Vulnerability
Windows Hyper-V allows hardware virtualization. IT professionals and software developers use virtualization to test software on multiple operating systems. Hyper-V enables working professionals to perform these tasks smoothly. With the help of Hyper-V, one can create virtual hard drives, virtual switches, and numerous different virtual devices, all of which can be added to virtual machines.
Microsoft has not published any information about the vulnerability.
Other Microsoft Vulnerability Highlights
- CVE-2024-21433 is an elevation of privilege vulnerability in Windows Print Spooler. To exploit the vulnerability, an attacker is required to win a race condition. Upon successful exploitation, an attacker could gain SYSTEM privilege.
- CVE-2024-21437 is an elevation of privilege vulnerability in the Windows Graphics Component. Upon successful exploitation, an attacker could gain SYSTEM privilege.
- CVE-2024-26160 is an information disclosure vulnerability in Windows Cloud Files Mini Filter Driver. An attacker may disclose the contents of Kernel memory after successfully exploiting the vulnerability.
- CVE-2024-26170 is an elevation of privilege vulnerability in the Windows Composite Image File System (CimFS). Upon successful exploitation, an attacker could gain SYSTEM privilege.
- CVE-2024-26182 is an elevation of privilege vulnerability in the Windows Kernel. Upon successful exploitation, an attacker could gain SYSTEM privilege.
- CVE-2024-26185 is a tempering vulnerability in the Windows Compressed Folder. An attacker would have to convince users to click a link, typically through an enticement in an email or instant message, and then convince them to open the specially crafted file.
Microsoft Release Summary
This month's release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Defender, Open Management Infrastructure, Microsoft Authenticator, Skype for Consumer, Software for Open Networking in the Cloud (SONiC), Microsoft Dynamics, Azure SDK, Microsoft Office SharePoint, Windows Kerberos, Windows USB Hub Driver, Windows USB Serial Driver, Windows Hypervisor-Protected Code Integrity, Windows Update Stack, Windows Print Spooler Components, Microsoft Windows SCSI Class System File, Windows AllJoyn API, Windows Telephony Server, Windows ODBC Driver, Microsoft WDAC OLE DB provider for SQL, Windows USB Print Driver, Windows Kernel, Windows NTFS, Microsoft Teams for Android, Microsoft WDAC ODBC Driver, Windows Cloud Files Mini Filter Driver, Microsoft Edge for Android, Windows Error Reporting, Windows Composite Image File System, Windows Compressed Folder, Microsoft QUIC, Windows Standards-Based Storage Management Service, Microsoft Exchange Server, Microsoft Office, Microsoft Intune, and Azure Data Studio.
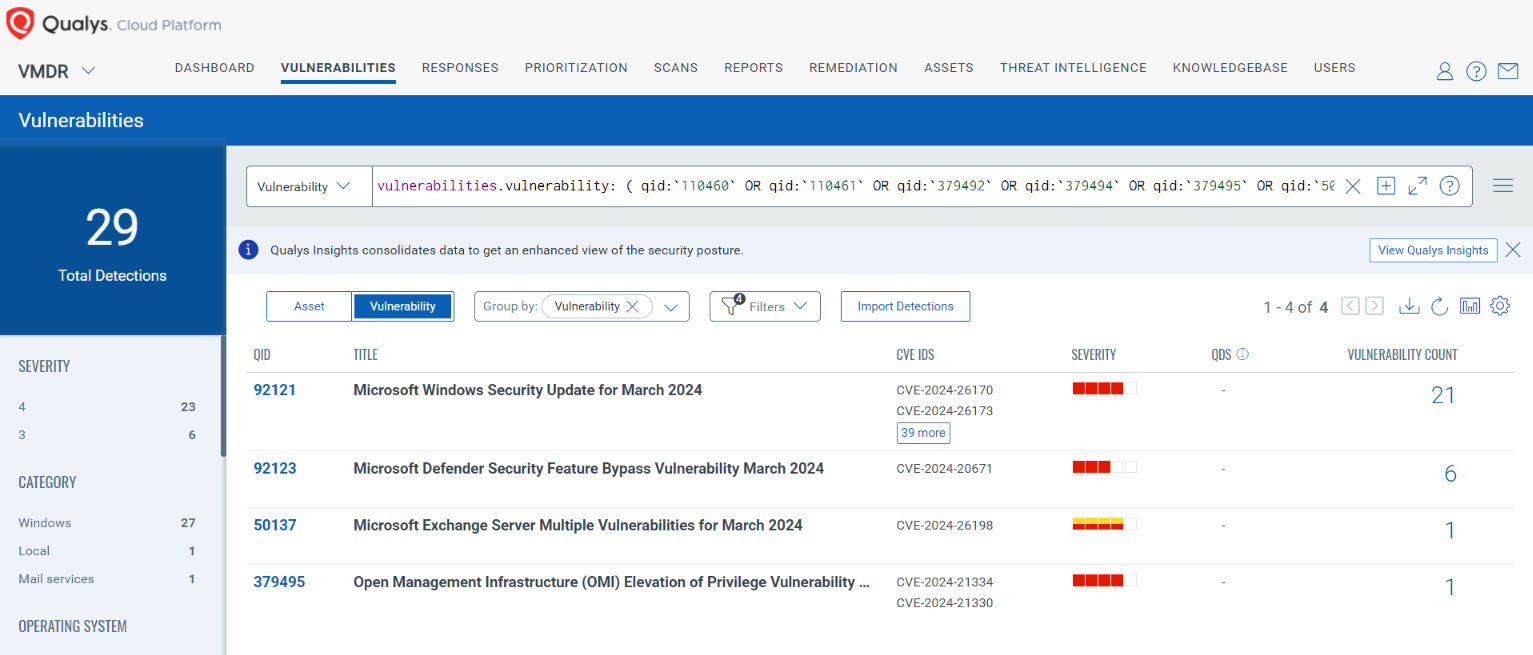
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
_vulnerabilities.vulnerability: ( qid:`110460` OR qid:`110461` OR qid:`379492` OR qid:`379494` OR qid:`379495` OR qid:`50137` OR qid:`92121` OR qid:`92122` OR qid:`92123` OR qid:`92124` OR qid:`92126` OR qid:`92127`)_
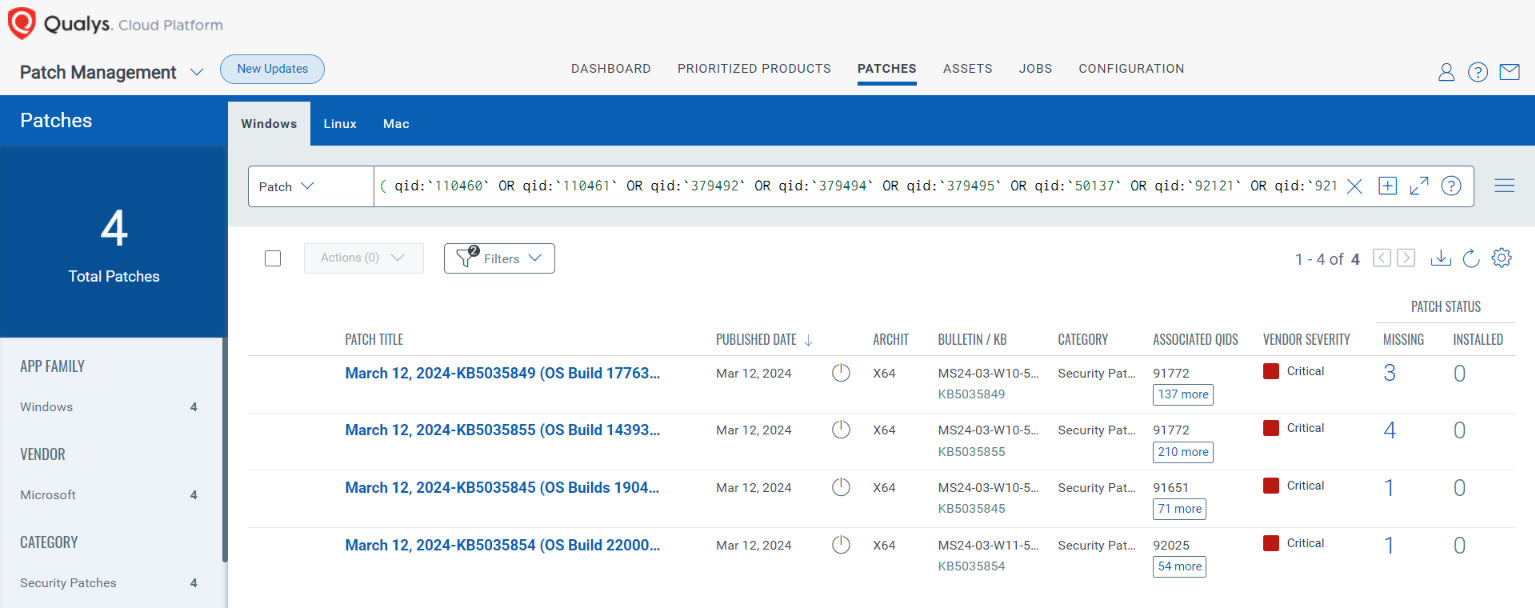
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
_( qid:`110460` OR qid:`110461` OR qid:`379492` OR qid:`379494` OR qid:`379495` OR qid:`50137` OR qid:`92121` OR qid:`92122` OR qid:`92123` OR qid:`92124` OR qid:`92126` OR qid:`92127`)_
The next Patch Tuesday falls on April 9, and we'll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the 'This Month in Vulnerabilities and Patch's webinar.'
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month's high-impact vulnerabilities, including those that are a part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
8.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
HIGH
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
9 High
AI Score
Confidence
High
5.1 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
HIGH
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:H/Au:N/C:P/I:P/A:P
0.001 Low
EPSS
Percentile
38.0%