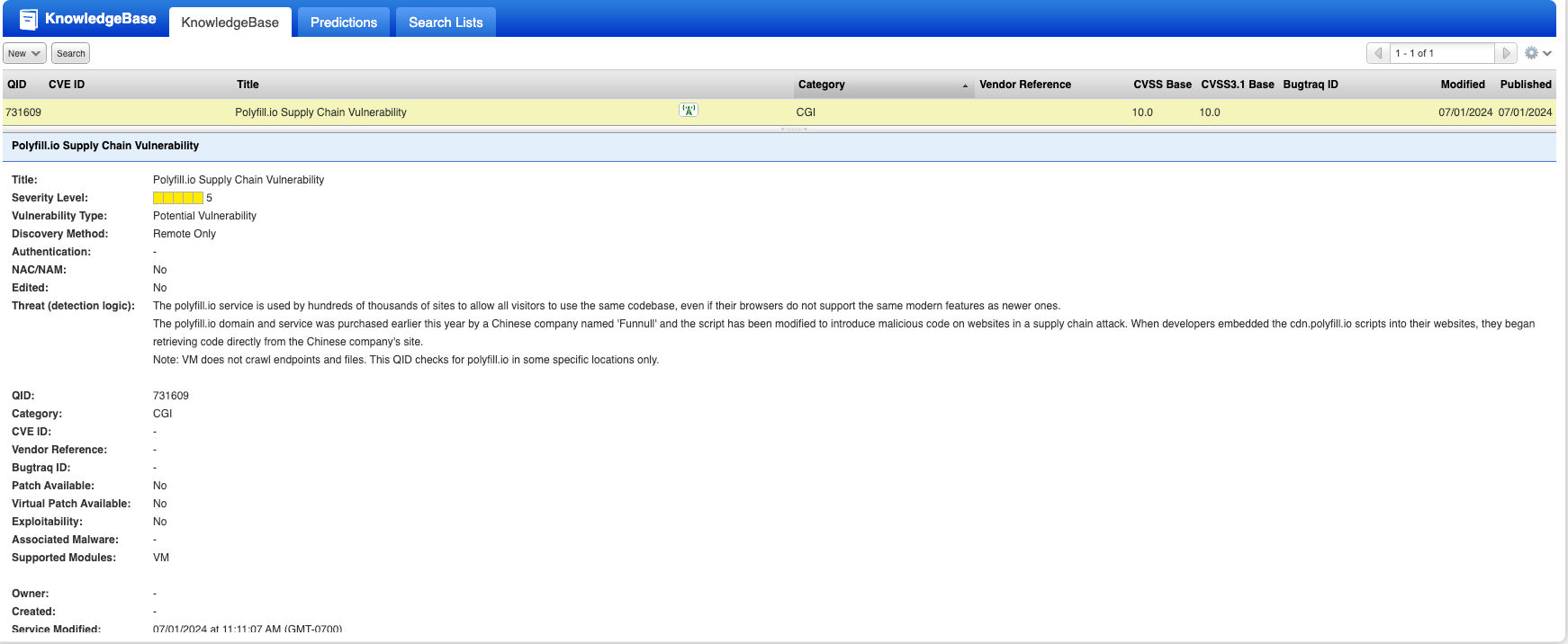
Polyfill.io Supply Chain Attack
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
LOW
Integrity Impact
NONE
Availability Impact
LOW
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:L
AI Score
Confidence
High
EPSS
Percentile
29.0%
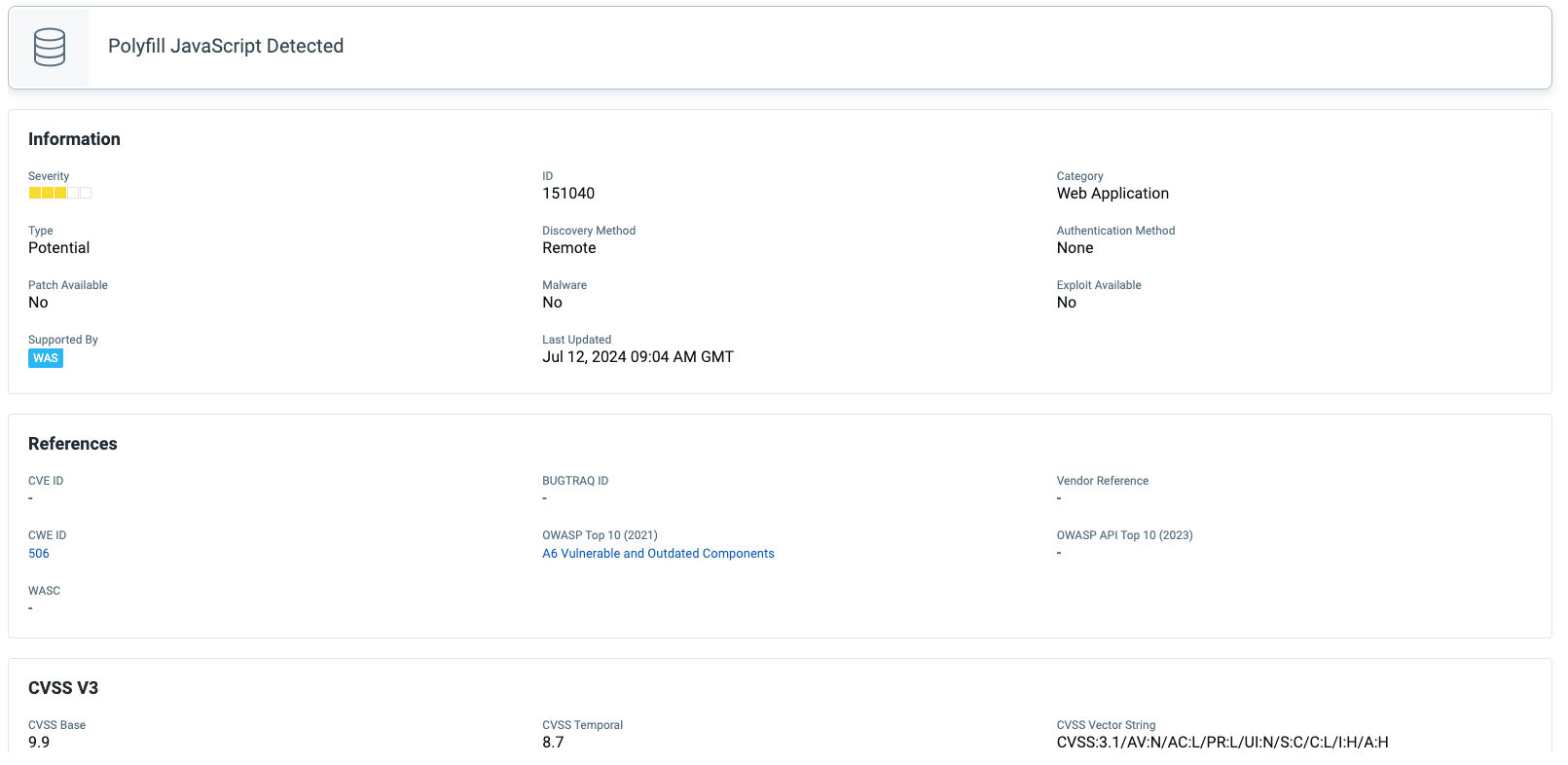
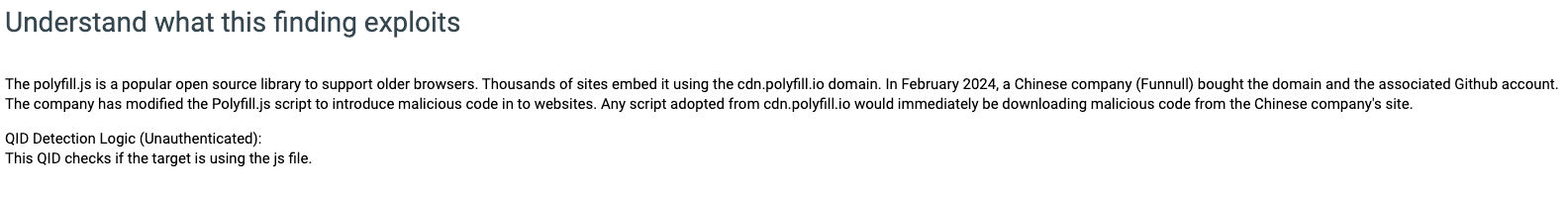
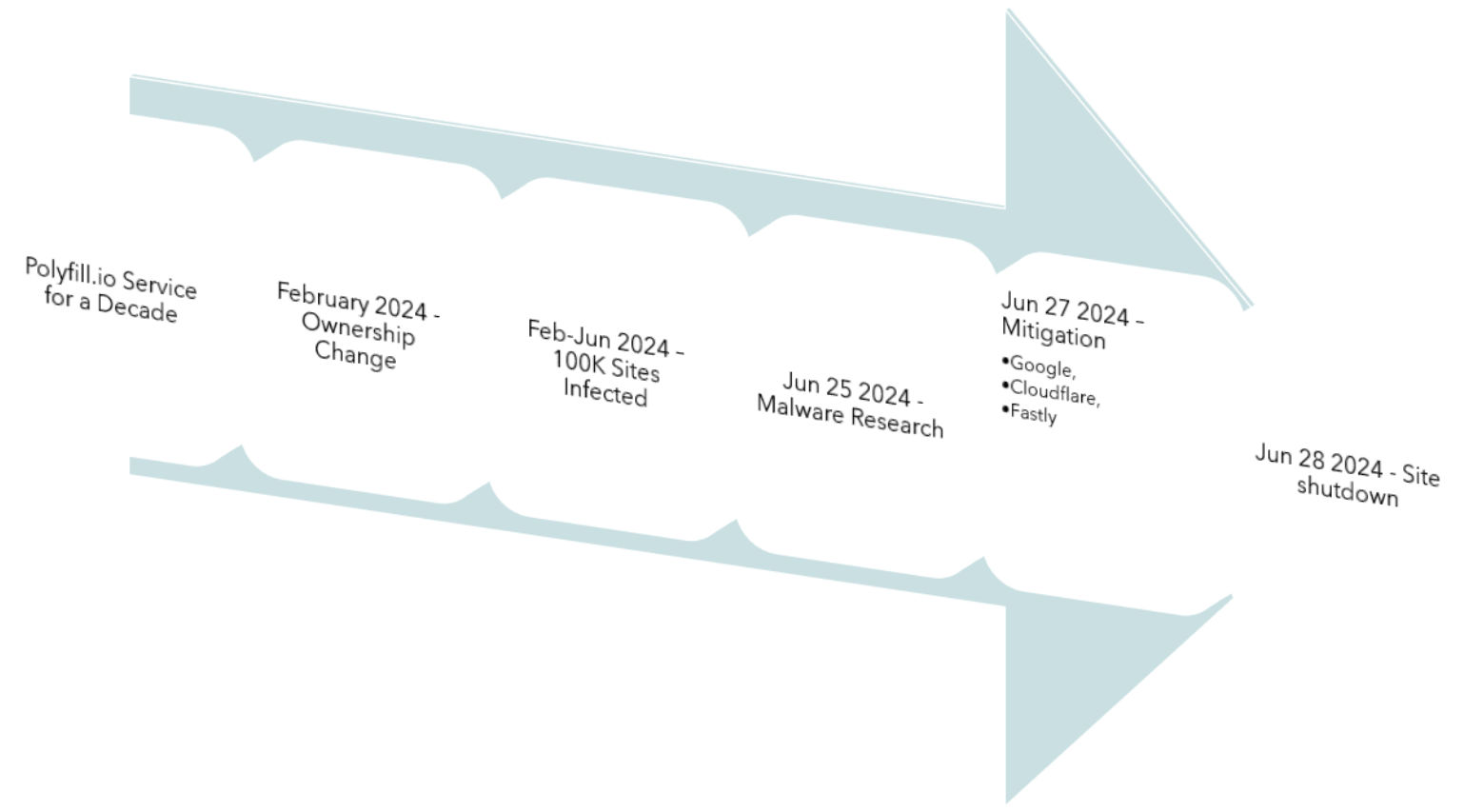
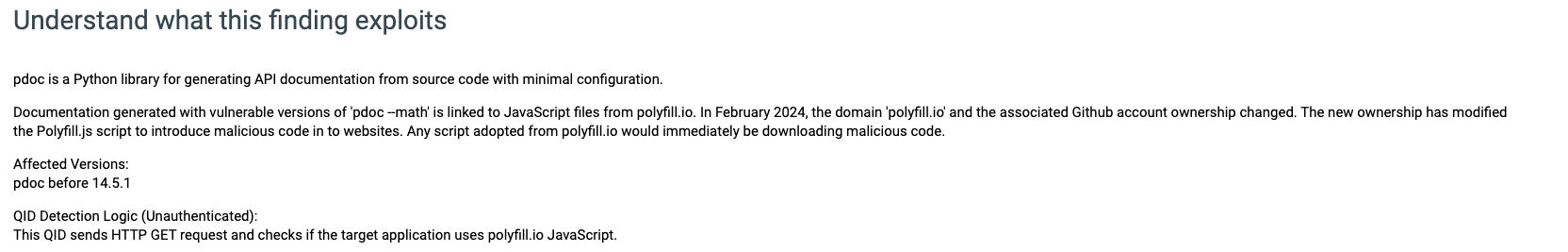
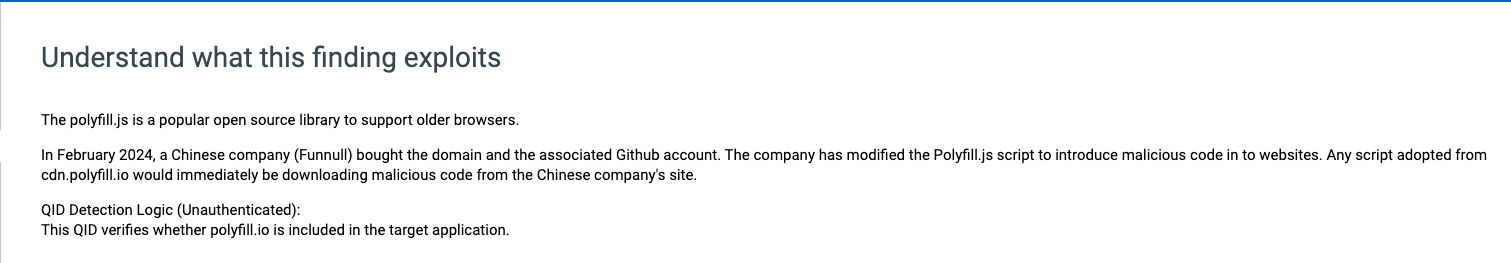
The polyfill.js is a popular open-source library that helps older browsers support functionality in newer browsers. Thousands of sites embed it using the cdn[.]polyfill[.]io domain. In February 2024, a Chinese company (Funnull) bought the domain and the GitHub account. The company has modified Polyfill.js so malicious code would be inserted into websites that embedded scripts from cdn.polyfill[.]io. Any script adopted from cdn.polyfill[.]io would immediately download malicious code from the Chinese company's site. Some of the known outcomes that result in supply chain attack are:
- user would be redirected to scam sites,
- allow attackers to steal sensitive data,
- potentially perform code execution.
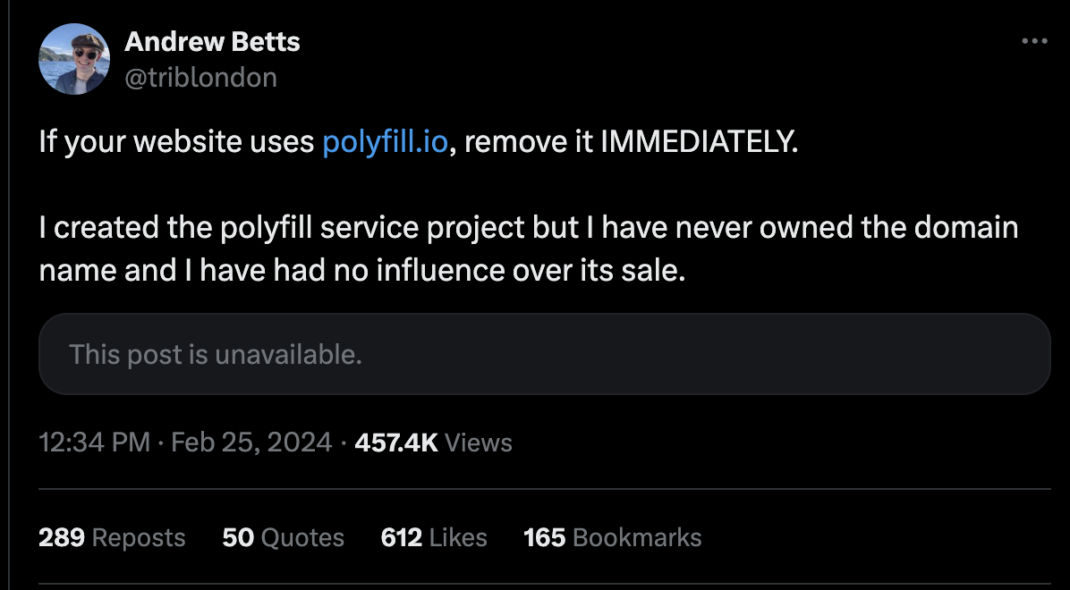
Given that modern browsers do not require Polyfill, the original Polyfill author, Andrew Betts, recommends not to use Polyfill at all. All websites should remove any references to polyfill.io. Recommended alternatives are CDN such as Cloudflare and Fastly.
Impacted Domains:
- cdn.polyfill.io
- bootcdn.net
- bootcss.com
- staticfile.net
- staticfile.org
- unionadjs.com
- xhsbpza.com
- union.macoms.la
- newcrbpc.com
The extent of damage is hard to quantify. Listed below are a subset of indicators to watch out for in your organization if your site is compromised:
- https://kuurza.com/redirect?from=bitget
- https://www.googie-anaiytics.com/html/checkcachehw.js
- https://www.googie-anaiytics.com/ga.js
- https://cdn.bootcss.com/highlight.js/9.7.0/highlight.min.js
- https://union.macoms.la/jquery.min-4.0.2.js
- https://newcrbpc.com/redirect?from=bscbc
Polyfill.io Timeline:
How Could A Website Be Compromised?
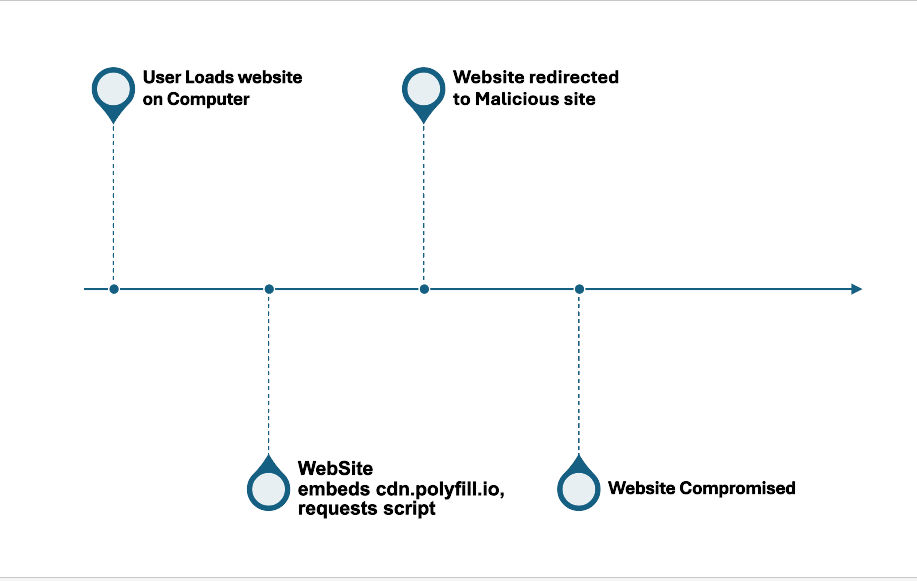
Efforts Done to Notify Users and Domain Owners:
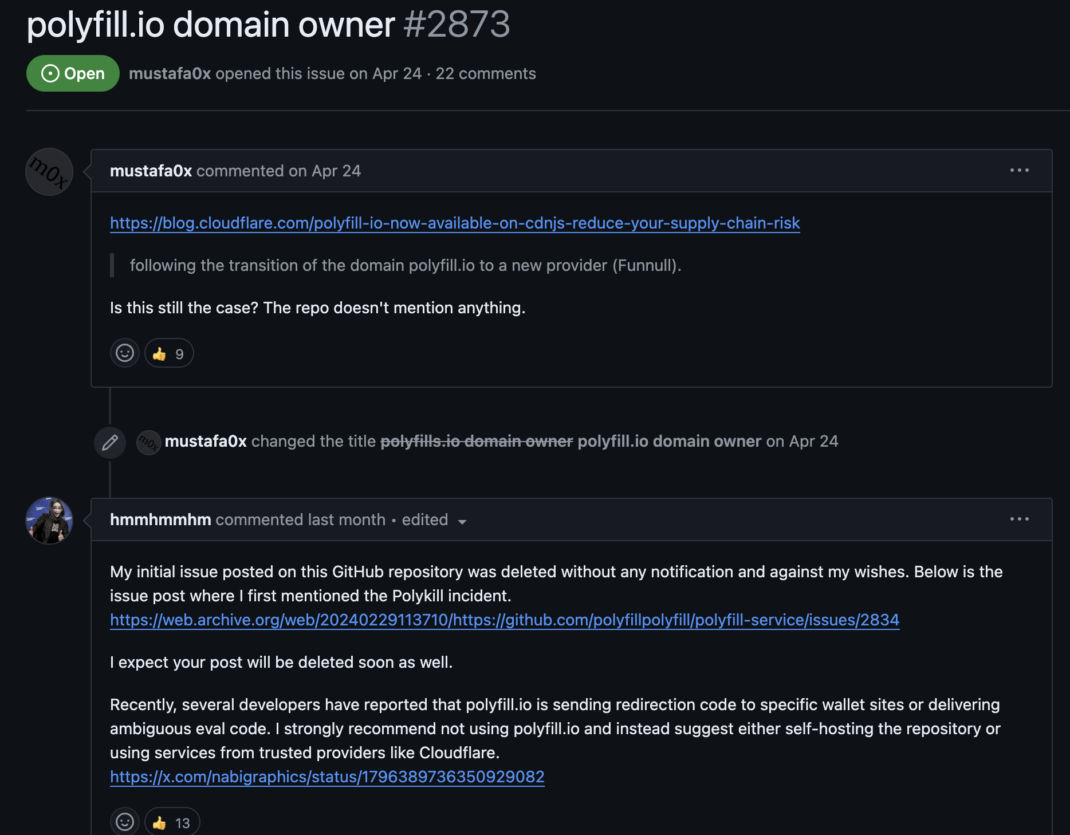
- Complaints in GitHub (take precaution going to links listed in the archive): "https://github.com/polyfillpolyfill/polyfill-service/issues/2873"
- Warnings were given from the original developer - <https://x.com/triblondon/status/1761852117579427975>
- Alerts from Google by blocking sites that use "polyfill.io"
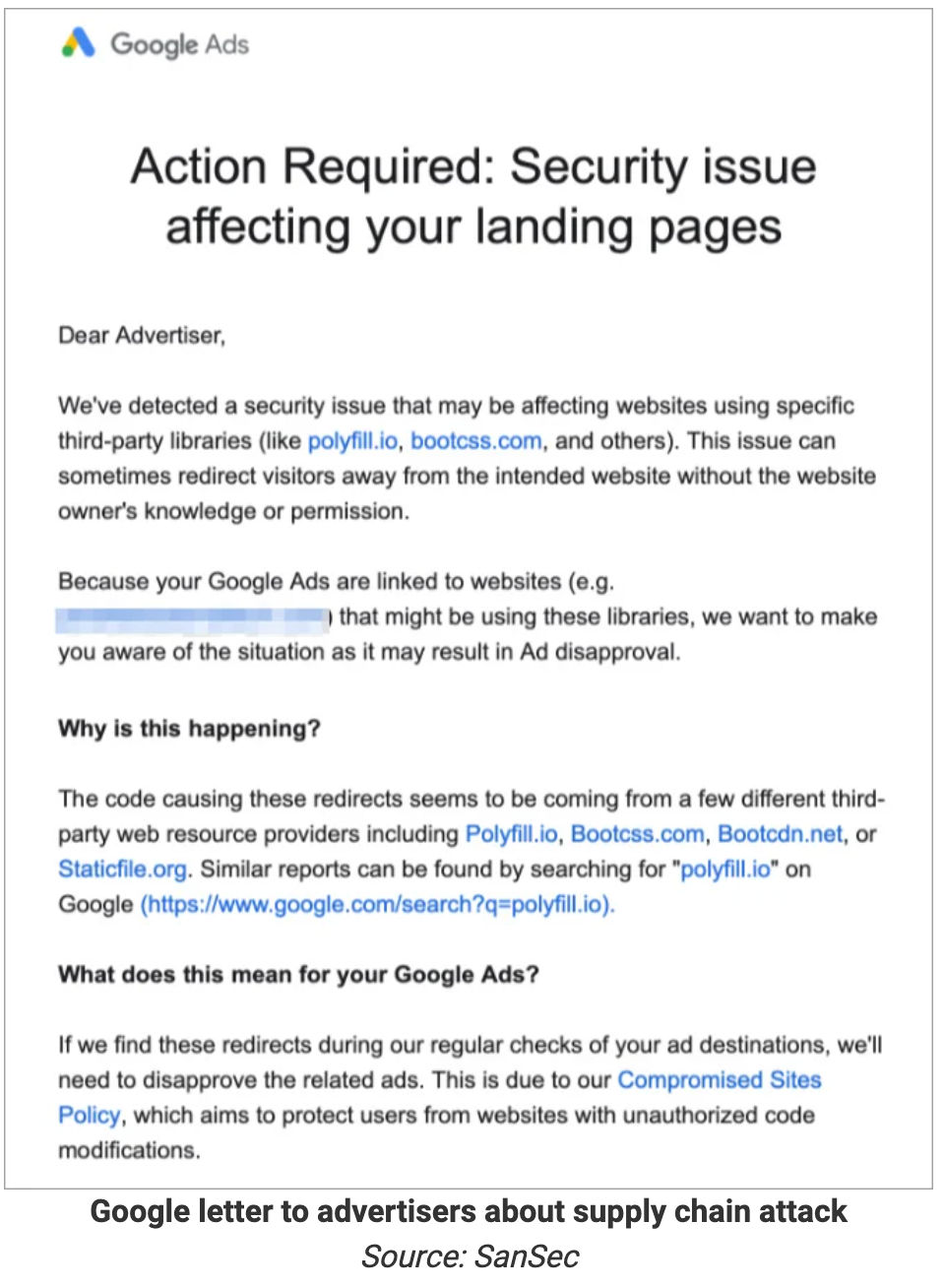
- Alternate solutions from Cloudflare, Fastly
Notifications and warnings were ignored, the complaints on GitHub were removed, and the altered script continued to redirect users to malicious sites.
Secure Your Website with Qualys:
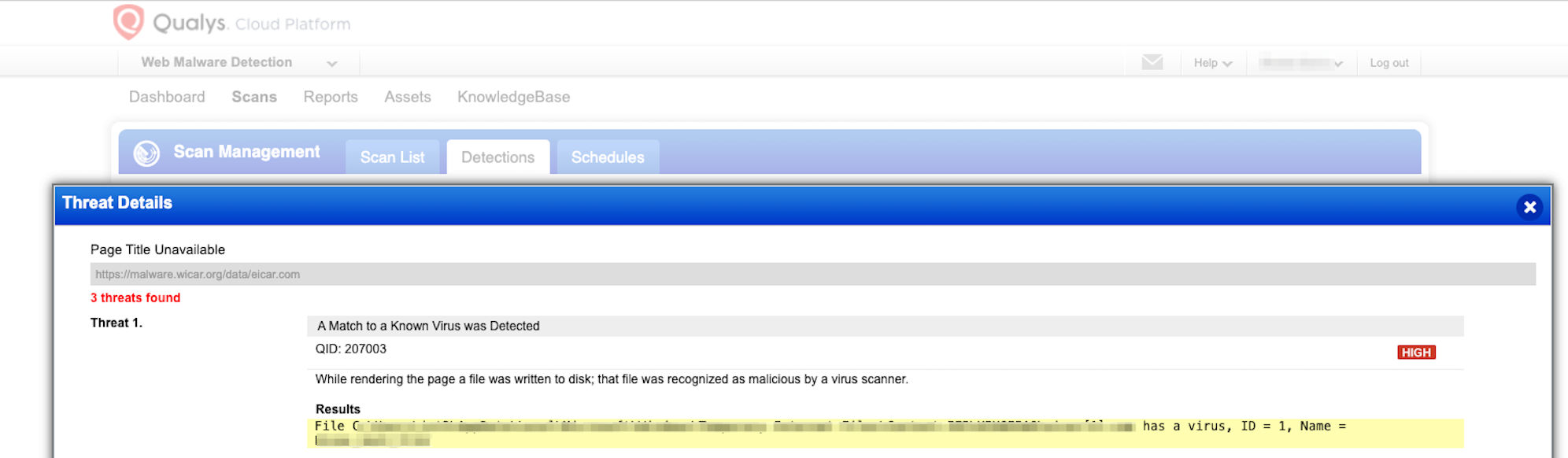
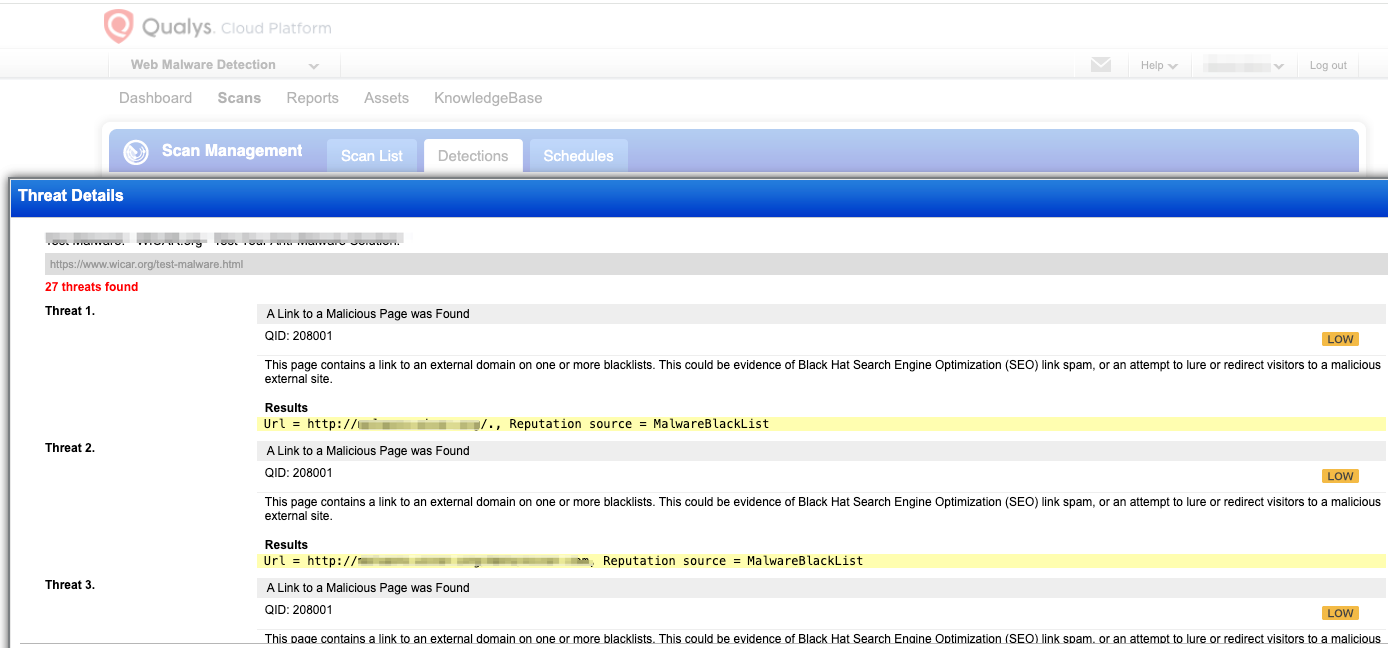
Qualys provides a comprehensive continuous solution to detect security issues in organizations. You can discover all your applications in your organization using CSAM to ensure all the assets are scanned. Given the nature of the attacks possible, we highly recommend organizations to launch VM, WAS and Web Malware scans to detect and remove the usage of scripts from the polyfill.io and impacted domains. The detection of your website being compromised is possible by launching a Web Malware scan.
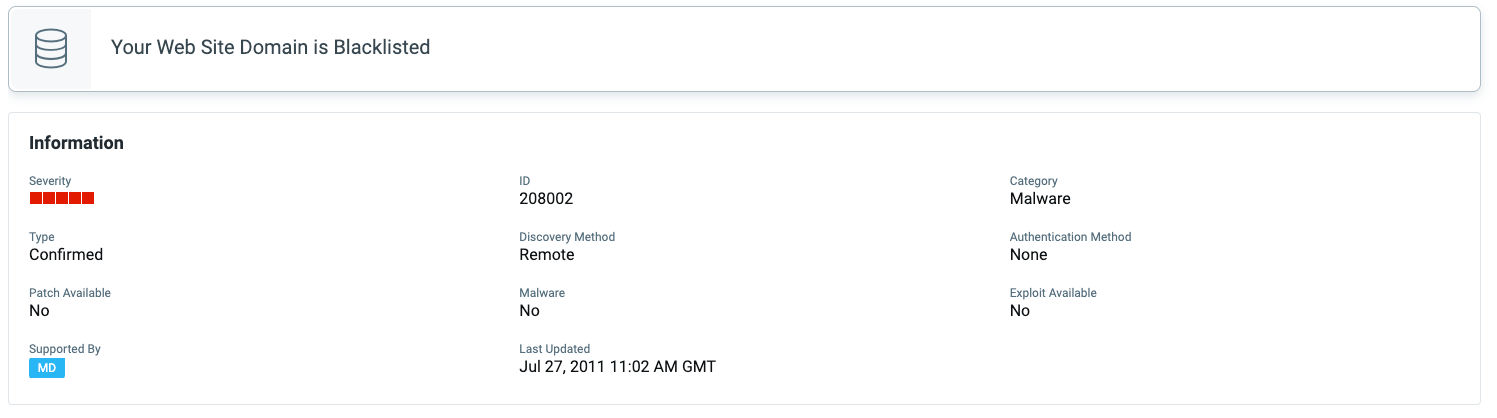
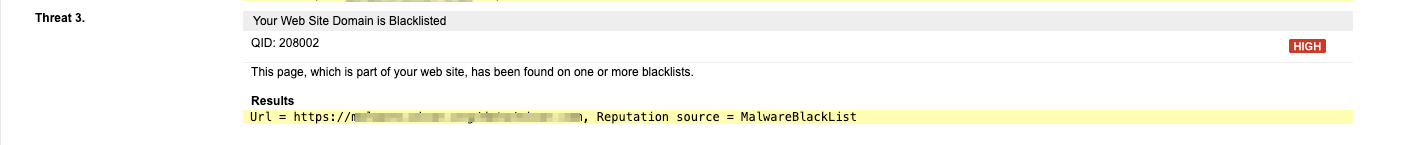
Qualys had existing QIDs that would have informed you of the possibility of the attack. Qualys has kept up with the research and released multiple detections to detect the usage of malicious domains and sites that have been compromised. If your scans report any of the following QIDs, please immediately follow the preventive measures we have provided in your reports.
VMDR Scan to detect if your assets are vulnerable:
- QID 731609: Polyfill.io Supply Chain Vulnerability
Web Application Scan to detect if your website is vulnerable:
-
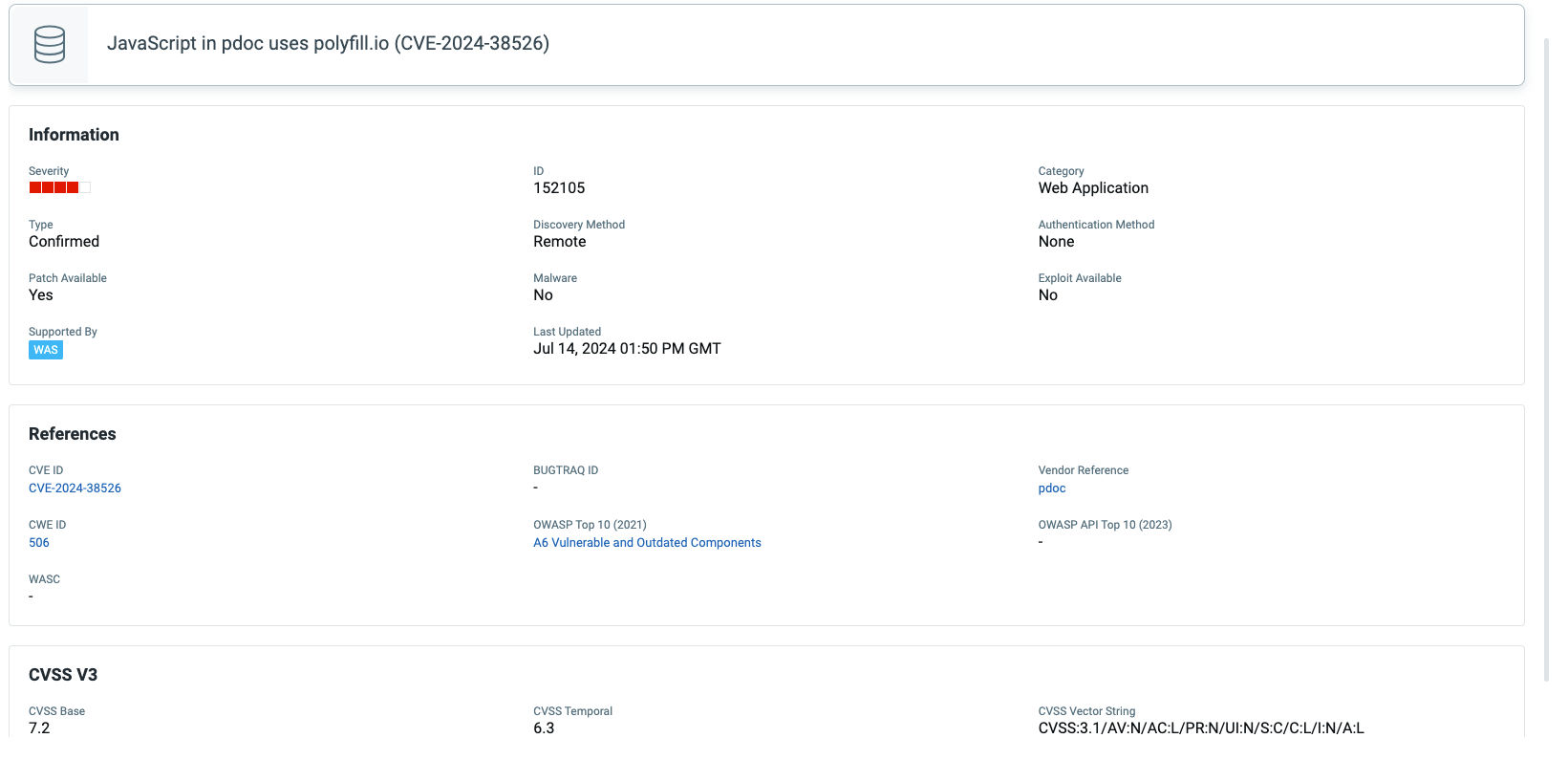
QID:152105: Javascript in pdoc uses polyfill.io (CVE-2024-38526)


-
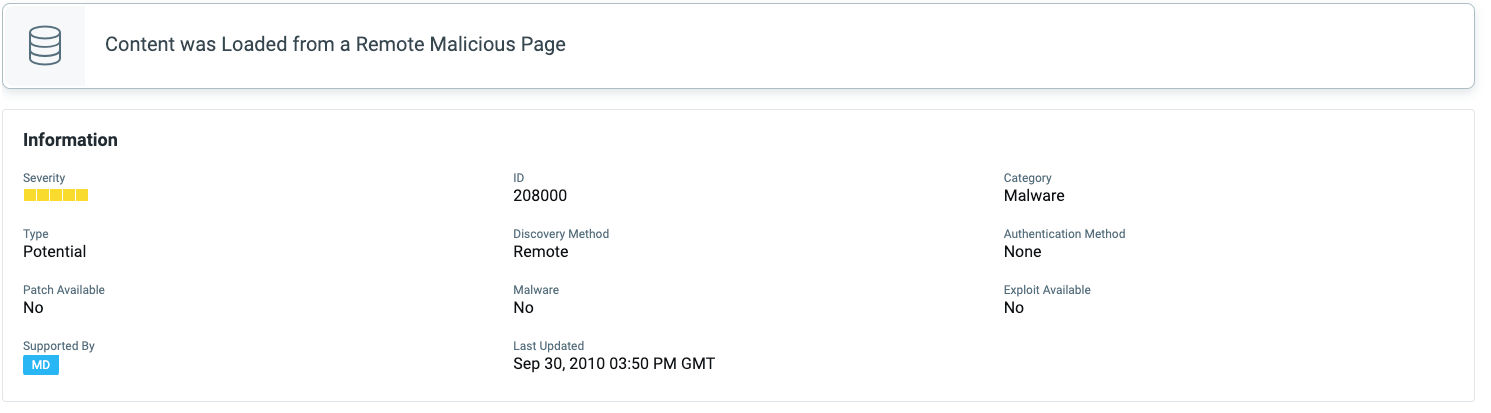
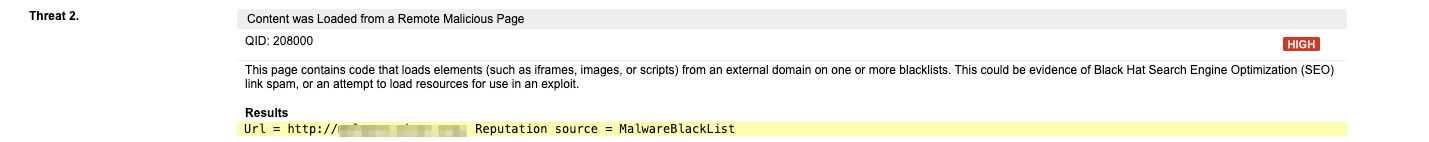
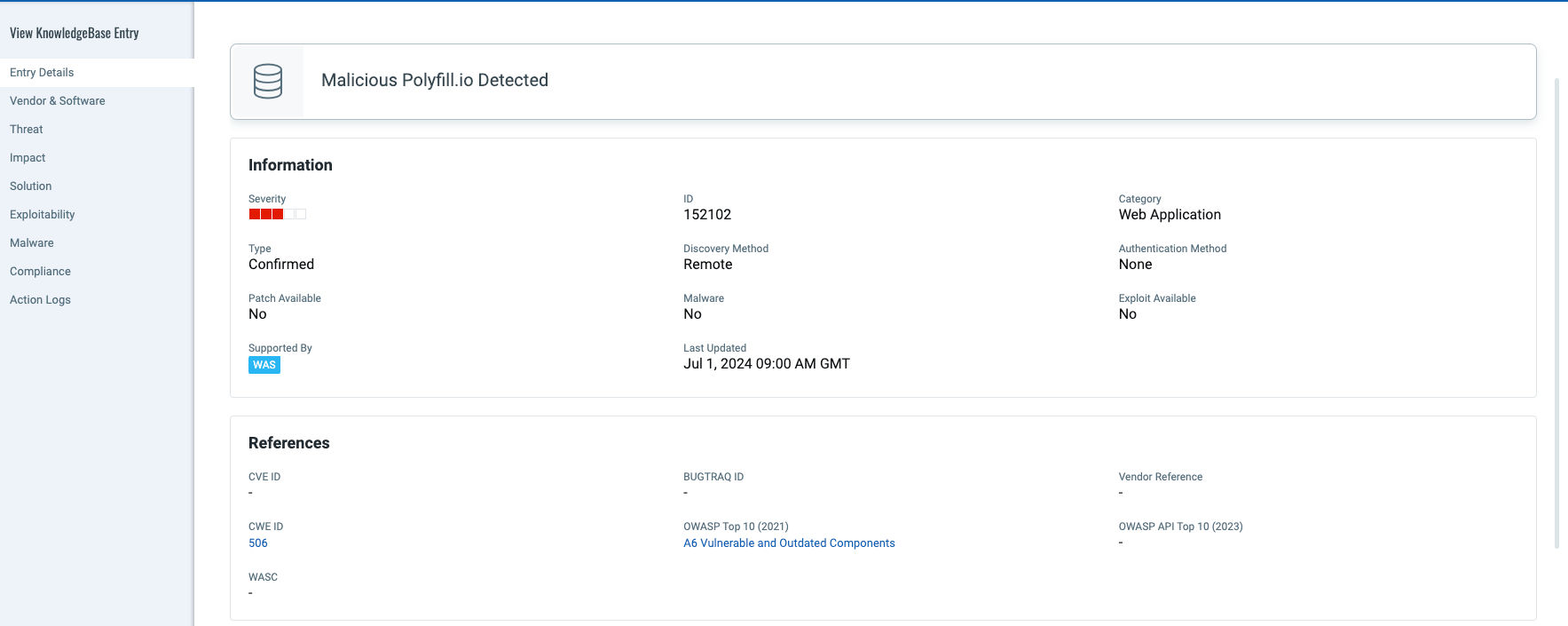
QID 152102: Malicious Polyfill.io Detected
-
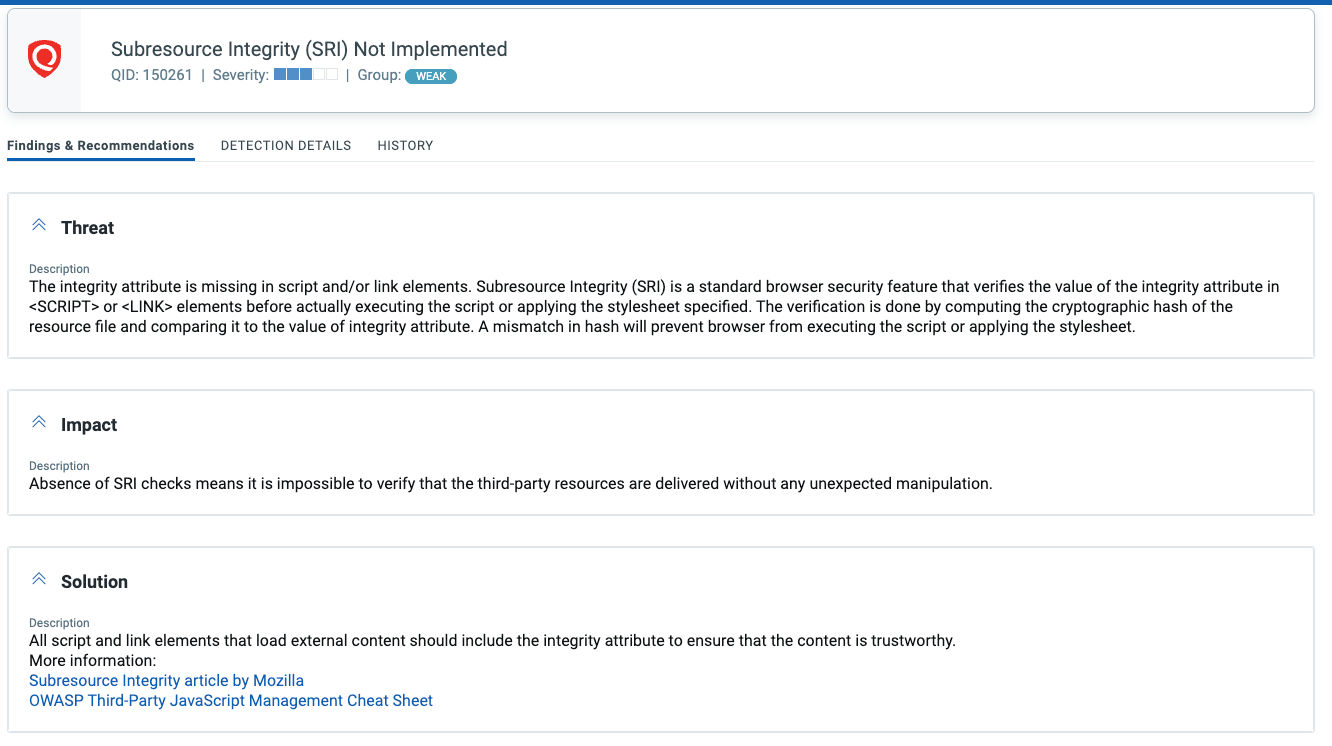
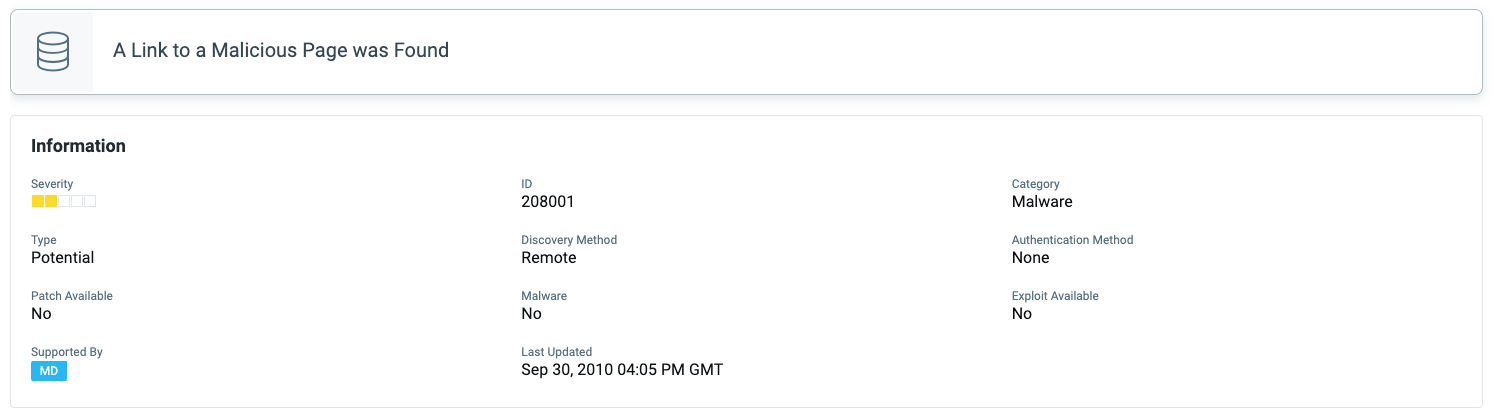
QID 150261: Subresource Integrity (SRI) Not Implemented
In anticipation of events such as these Qualys research had released a Subresource Integrity check in 2020. If you see this IG QID reported, please ensure you take precautions to include integrity attribute to all elements that load external content.
Web Malware Scan to detect malware on your website**:**
References:
- <https://sansec.io/research/polyfill-supply-chain-attack>
- <https://blog.cloudflare.com/automatically-replacing-polyfill-io-links-with-cloudflares-mirror-for-a-safer-internet>
- <https://community.fastly.com/t/new-options-for-polyfill-io-users/2540>
- <https://x.com/triblondon/status/1761852117579427975>
- <https://developer.mozilla.org/en-US/docs/Glossary/Polyfill>
- <https://www.securityweek.com/over-380k-hosts-still-referencing-malicious-polyfill-domain-censys/>
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
LOW
Integrity Impact
NONE
Availability Impact
LOW
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:L
AI Score
Confidence
High
EPSS
Percentile
29.0%