
Microsoft and Adobe Patch Tuesday, August 2023 Security Update Review
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.587 Medium
EPSS
Percentile
97.3%
Microsoft has released its August edition of Patch Tuesday. This month's updates have addressed 89 security vulnerabilities in multiple products, features, and roles.
Microsoft Patch Tuesday for August 2023
Microsoft has addressed two zero-day vulnerabilities known to be publicly exploited in this month's updates.Six of these 89 vulnerabilities****are rated as Critical and68 asImportant. Microsoft has addressed12 vulnerabilities related toMicrosoft Edge (Chromium-based) in this month's Patch Tuesday Edition.
Microsoft has also included two Defense in Depth Updates for Microsoft Office (ADV230003) and Memory Integrity System Readiness Scan Tool (ADV230004).
Microsoft Patch Tuesday, August edition includes updates for vulnerabilities in Microsoft Office and Components, .NET Core, .NET Framework, ASP.NET and Visual Studio, Azure Arc, Azure DevOps, Microsoft Windows Codecs Library, SQL Server, Windows Kernel, Windows LDAP - Lightweight Directory Access Protocol, Windows Message Queuing, Windows Mobile Device Management, Windows Projected File System, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The August 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 12 | Important: 12 |
| Denial of Service Vulnerability | 8 | Important: 8 |
| Elevation of Privilege Vulnerability | 18 | Important: 18 |
| Information Disclosure Vulnerability | 10 | Important: 10 |
| Security Feature Bypass Vulnerability | 4 | Important: 3 |
| Remote Code Execution Vulnerability | 23 | Critical: 6 |
| Important: 17 |
Adobe Patches for August 2023
Adobe has released four security advisories in this month’s updates. The advisories addressed37vulnerabilities in Adobe Acrobat and Reader, Adobe Commerce, Adobe Dimension, and Adobe XMP Toolkit SDK. Out of 37 vulnerabilities,19 are rated as critical. The critical severity vulnerabilities could lead to arbitrary code execution, memory leak, and security feature bypass.
Zero-day Vulnerabilities Patched in August Patch Tuesday Edition
CVE-2023-36884: Windows Search Remote Code Execution Vulnerability
Microsoft released OS updates in the last month's edition to address the vulnerability. In this month's updates, Microsoft has released an additional Defense in Depth Update (ADV230003) to stop the attack chain used in the exploitation of the vulnerability.
Microsoft has updated the title from Office and Windows HTML Remote Code Execution Vulnerability to**Windows Search Remote Code Execution Vulnerability **in this month's update.
An attacker may exploit the vulnerability in an email or instant message attack scenario by sending a specially crafted file. An attacker may plant a malicious file evading Mark of the Web (MOTW) defenses which can result in code execution on the victim system.
CVE-2023-38180: .NET and Visual Studio Denial of Service Vulnerability
The vulnerability may allow an attacker to perform a denial-of-service attack on a target system in a low-complexity attack without special privileges.
Microsoft has not provided any additional information regarding the vulnerability in the latest advisory.
CISA has added the CVE-2023-38180 to its Known Exploited Vulnerabilities Catalog requesting users to patch it before Aug 30, 2023.
Other Critical Severity Vulnerabilities Patched in August Patch Tuesday Edition
CVE-2023-29328, CVE-2023-29330: Microsoft Teams Remote Code Execution Vulnerability
An attacker is required to trick a user into joining a Teams meeting set up by them. It would allow the attacker to perform remote code execution in the context of the victim user. A successful remote attack performed by an attacker would enable them to access and alter user information. The attacker requires no privileges to perform the exploit.
CVE-2023-36910, CVE-2023-36911, & CVE-2023-35385: Microsoft Message Queuing Remote Code Execution Vulnerability
Message Queuing (MSMQ) is a protocol developed by Microsoft to ensure reliable communication between Windows computers across different networks, even when a host is temporarily not connected (by maintaining a message queue of undelivered messages).
To exploit this vulnerability, an attacker must send a specially crafted malicious MSMQ packet to an MSMQ server. An unauthenticated attacker may perform remote code execution on the target server by successfully exploiting the vulnerability.
CVE-2023-36895: Microsoft Outlook Remote Code Execution Vulnerability
To exploit the vulnerability, an attacker must convince a victim to download and open a specially crafted file from a website, leading to a local computer attack.
Other Microsoft Vulnerability Highlights
- CVE-2023-35359 is an elevation of privilege vulnerability that may allow an attacker to gainSYSTEM privileges. An attacker with local access to the targeted machine and the user may create folders and performance traces on the device with restricted privileges that normal users have by default.
- CVE-2023-36900 is an elevation of privilege vulnerability in the Windows Common Log File System Driver. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-35380, CVE-2023-35382, and CVE-2023-35386 are elevation of privilege vulnerabilities in the Windows Kernel. Successful exploitation of the vulnerabilities may allow an attacker to gainSYSTEM privileges.
- CVE-2023-35384 is a security feature bypass vulnerability in the Windows HTML Platforms. To exploit the vulnerability, an attacker must send the user a malicious file and convince them to open it. The vulnerability arises when the MSHTML platform fails to validate the correct Security Zone of requests for specific URLs. An attacker may exploit this to cause a user to access a URL in a less restricted Internet Security Zone than intended.
- CVE-2023-35388 and CVE-2023-38182 are remote code execution vulnerabilities affecting Microsoft Exchange Server. To exploit these vulnerabilities, the attacker must be authenticated with LAN access and have credentials for a valid Exchange user. On successful exploitation, an attacker may perform remote code execution via a PowerShell remoting session.
Microsoft Release Summary
This month's release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Memory Integrity System Readiness Scan Tool, Microsoft Exchange Server, Microsoft Teams, Windows Reliability Analysis Metrics Calculation Engine, Windows Fax and Scan Service, Windows HTML Platform, Windows Bluetooth A2DP driver, Microsoft Dynamics, Azure HDInsights, Reliability Analysis Metrics Calculation Engine, Microsoft WDAC OLE DB provider for SQL, Windows Group Policy, Tablet Windows User Interface, ASP.NET, Windows Common Log File System Driver, Windows System Assessment Tool, Windows Cloud Files Mini Filter Driver, Windows Wireless Wide Area Network Service, Windows Cryptographic Services, Windows Hyper-V, Windows Smart Card, Dynamics Business Central Control, and Windows Defender.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110443` OR qid:`110444` OR qid:`110445` OR qid:`378744` OR qid:`378755` OR qid:`50127` OR qid:`92042` OR qid:`92043` OR qid:`92044` OR qid:`92045` OR qid:`92046` OR qid:`92047` OR qid:`92049` OR qid:`92052` OR qid:`92053` )
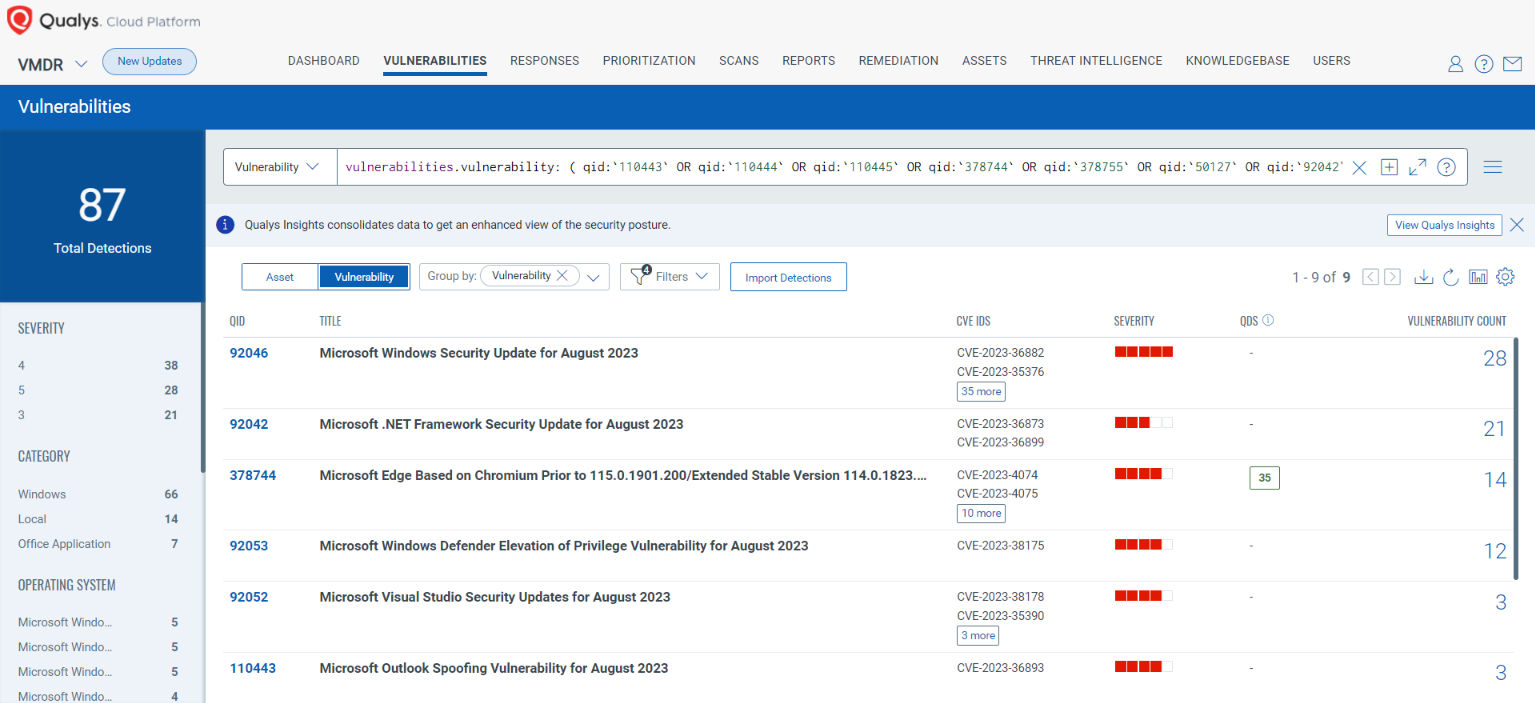
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110443` OR qid:`110444` OR qid:`110445` OR qid:`378744` OR qid:`378755` OR qid:`50127` OR qid:`92042` OR qid:`92043` OR qid:`92044` OR qid:`92045` OR qid:`92046` OR qid:`92047` OR qid:`92049` OR qid:`92052` OR qid:`92053` )

EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance's Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/Patch) cannot be done now; these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn't working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) has been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-35378: Windows Projected File System Elevation of Privilege Vulnerability
This vulnerability has a CVSS:3.1 7.0 / 6.1
Policy Compliance Control IDs (CIDs):
- 11511 List of installed features on the system
CVE-2023-35385, CVE-2023-36910, & CVE-2023-36911: Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 4030 Status of the 'Windows Message Queuing Service'
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
CVE-2023-21709: Microsoft Exchange Server Elevation of Privilege Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 13515 List installed IIS modules
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [4030,14916,14297,11511,13515]
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
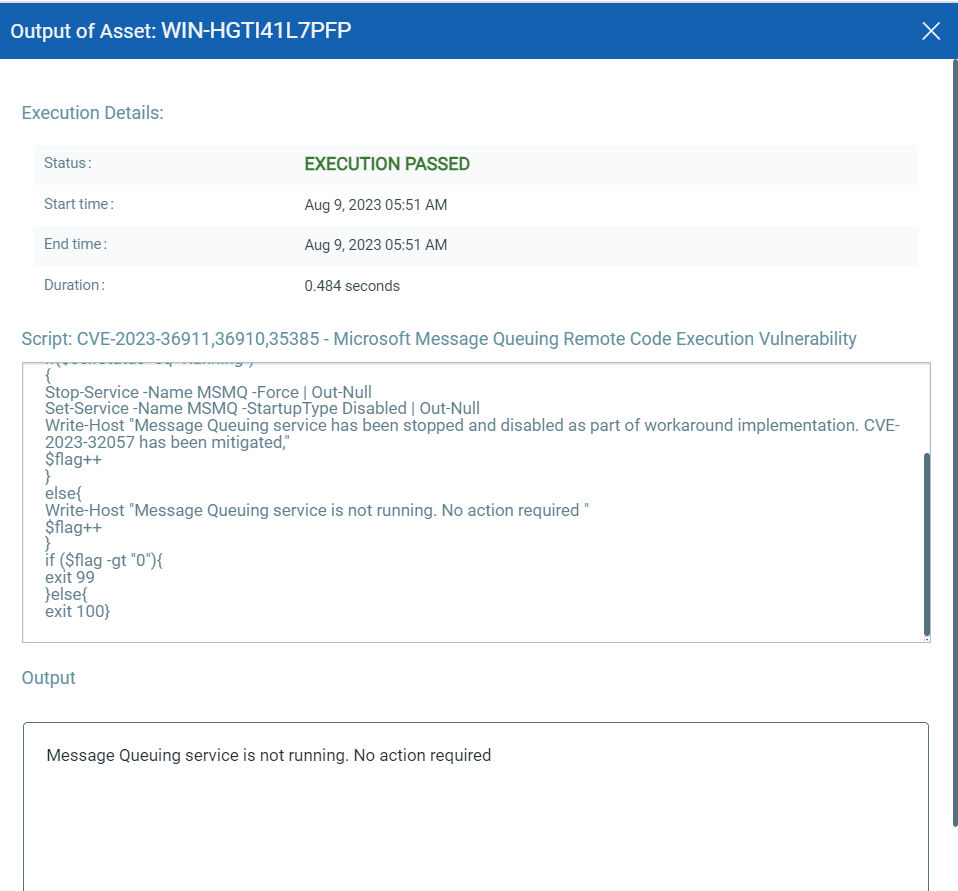
CVE-2023-35378: Windows Projected File System Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.0/10.
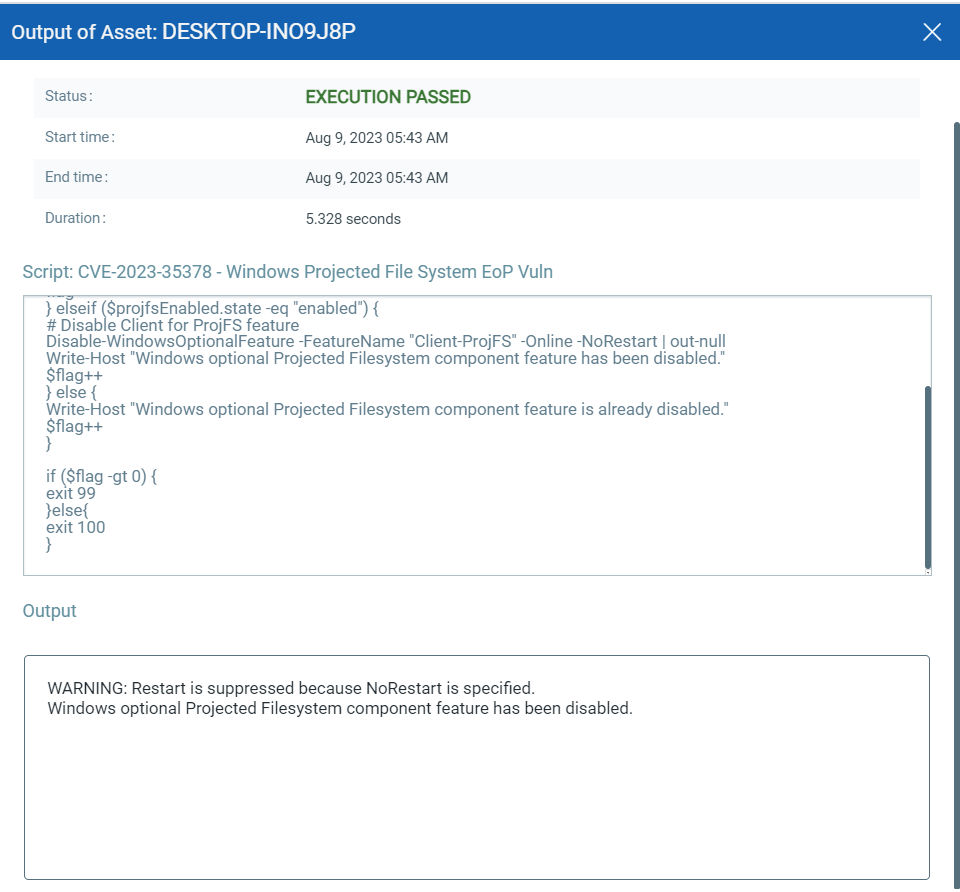
CVE-2023-36910, CVE-2023-36911, & CVE-2023-35385: Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
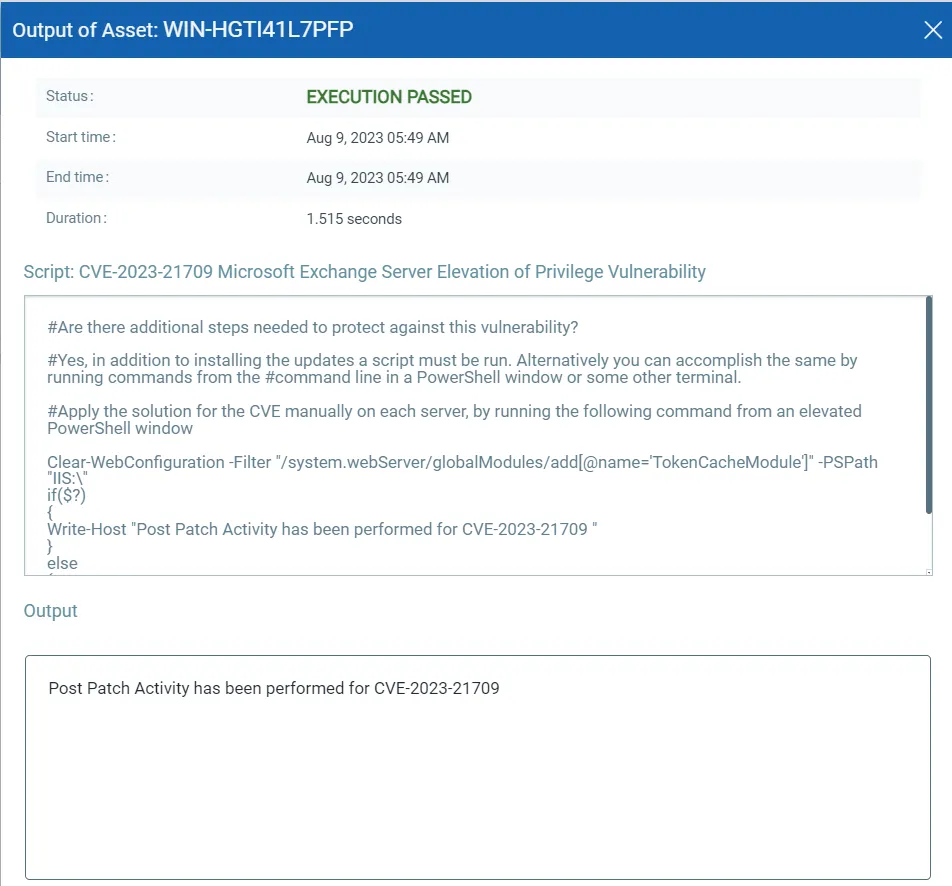
CVE-2023-21709: Microsoft Exchange Server Elevation of Privilege Vulnerability
Note: This is Post Patch Activity
This vulnerability has a CVSSv3.1 score of 9.8/10.
The next Patch Tuesday falls on September 12, and we'll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the 'This Month in Vulnerabilities and Patches webinar.'
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month's high-impact vulnerabilities, including those that are part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.587 Medium
EPSS
Percentile
97.3%
