How the Qualys Enterprise TruRisk™ Platform Supports CISA Vulnrichment
6.9 Medium
AI Score
Confidence
High
Introduction
In today's interconnected digital landscape, cybersecurity threats pose significant risks to organizations across various sectors. Recognizing the need for a structured approach to identify, prioritize, and address vulnerabilities, the Cybersecurity and Infrastructure Security Agency (CISA) has developed the “Vulnrichment Project.” This project is a public repository of CISA's enrichment of public CVE records by adding key SSVC (Stakeholder-Specific Vulnerability Categorization) decision points. SSVC uses a decision tree to evaluate if the security team should defer or act immediately on a vulnerability.
Qualys TruRisk already includes these decision points and more, generating a Qualys Detection Score (QDS) in the 0-100 range for every CVE, allowing defenders to manage their risks better.
The Background
Common Vulnerability Scoring System (CVSS) and Exploit Prediction Scoring System (EPSS)
Today, most enterprises prioritize vulnerabilities based on the Common Vulnerability Scoring System (CVSS) rating system. Yet a CVSS rating represents the technical severity of a vulnerability, not the risk it poses to any given organization. This has become an inefficient model, with over 52% of CVEs marked as high or critical. Because of this, organizations end up patching vulnerabilities that may not reduce risk for their specific and unique business.
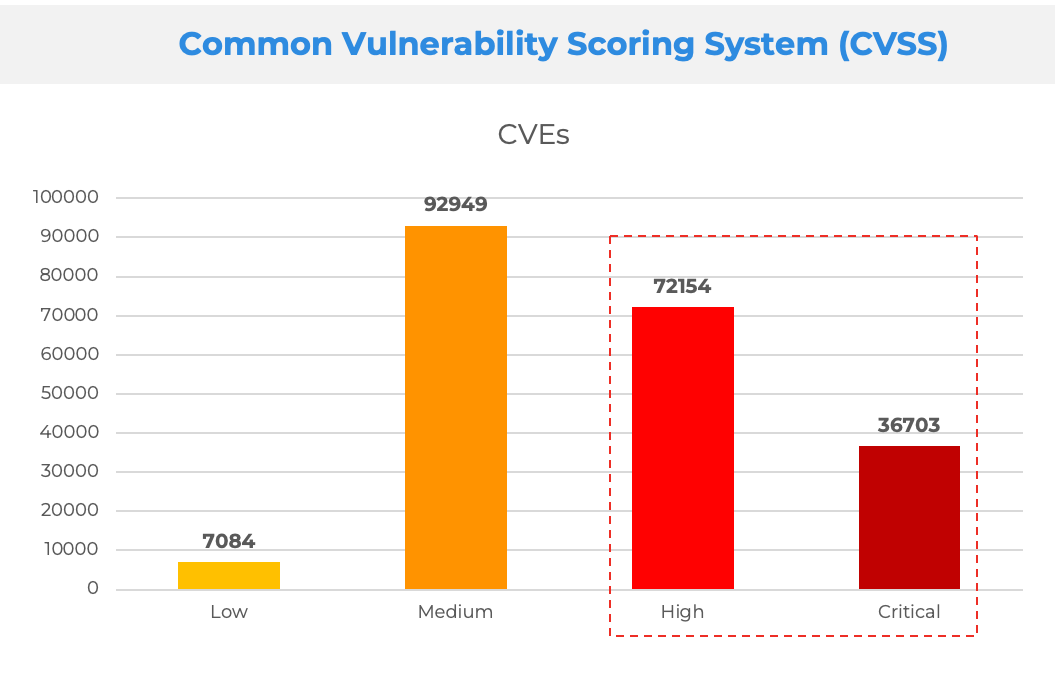
In comparison, when it comes to EPSS, only 2% of the vulnerabilities scored by EPSS are rated Critical or High Severity, and almost everything else is rated as Low even though we see clear evidence of being actively exploited in the wild.

Also, EPSS tends to lower the score if the patch is available for a CVE, even though the vulnerability might not be patched in your environment. And finally, CVEs that are not yet published by the NVD don’t even get an EPSS score. Although EPSS may be better than CVSS in terms of volume, it is still not enough to solve the prioritization challenges because we need to focus on reducing risk, not volume.
When CVEs are published, the NIST National Vulnerability Database (NVD) scores them to add essential metadata, including severity scores like CVSS and affected product details. Recently, NIST has experienced a significant slowdown in its analysis of CVEs, which leaves many organizations without additional data to evaluate vulnerabilities. In this context, CISA has stepped in with their new Vulnrichment project.
SSVC and the Vulnrichment Project
The CISA Vulnrichment project is the public repository of CISA's enrichment of public CVE records through CISA's Authorized Data Publisher (ADP) container. Currently, CISA is assessing new and recent CVEs and adding key SSVC decision points. Once scored, some higher-risk CVEs will also receive enrichment of CWE, CVSS, and CPE data points, where possible.
The SSVC framework is designed to address the limitations of traditional vulnerability management methods by focusing on stakeholder concerns and categorizing vulnerabilities accordingly. This process uses a decision tree that guides users through a series of questions to determine one of four possible outcomes:
- Track –does not require any action at this time. Remediate within standard update timelines.
- Track* - contains specific characteristics that may require closermonitoring for changes. Remediate within standard update timelines.
- Attend -requires attention from the organization's internal, supervisory-level individuals. Remediate sooner than standard update timelines.
- Act -requires immediate attention from the organization's internal, supervisory-level, and leadership-level individuals. Remediate as soon as possible.
The SSVC uses a decision tree to arrive at this result. This decision tree is comprised of a few sets of questions:
- Exploitable – Evidence of Active Exploitation of a Vulnerability. This measure determines the present state of exploitation of the vulnerability. Value: None, POC, Active.
- Automatable – This represents automating the exploitation events for vulnerability. Value: Yes, No.
- Technical Impact – Technical Impact of Exploiting the Vulnerability. It is similar to the Common Vulnerability Scoring System (CVSS) base score’s concept of “severity.” Value: Partial, Total.
- Mission Prevalence – Impact on assets that provide mission essential functions. This takes into account the criticality of the asset to the organization. Value: Minimal, Support, Essential.
- Well-Being – Impacts of the affected system compromise the physical, social, emotional, and psychological health of humans. Value: Minimal, Material, Irreversible.
Mission Prevalence and Well-Being are combined into ‘Mission and Well-Being’ and rated as Low, Medium, and High – reducing the depth of branches to four.
 Image Source: https://www.cisa.gov/ssvc-calculator
Image Source: https://www.cisa.gov/ssvc-calculator
How Qualys TruRisk supports Vulnrichment
Qualys TruRisk is a methodology that marries vulnerability (CVSS and EPSS) with real-time threat context as well as the application and business context. Qualys integrates with 25+ threat and exploit intelligence sources to incorporate a wide array of vulnerability intelligence into the risk assessment capabilities of TruRisk. The threat context includes elements like exploit maturity, malware type, exploit type, threat actors, CISA KEV, etc. The application and business context informs if the app is business-critical, where it is located, if it is internet-facing, how important the asset is, etc.
By merging all this information, the customer gets a multi-dimensional risk score for a CVE, giving the security team a 360-view of their risk.

Qualys TruRisk assists organizations in better prioritization and risk reduction. The core factors taken into account by the SSVC model, including exploitation status, technical impact, and business criticality, directly align with the key factors used by TruRisk for improved prioritization.
Qualys TruRisk
Qualys TruRisk is much more than measuring and prioritizing risk at a CVE level. The vision behind TruRisk is to empower security teams to measure accurately, communicate precisely, and eliminate effectively.
The TruRisk is also calculated at an asset level, a group of assets, or a business unit level. This flexibility to measure and prioritize risk allows security teams to focus on critical applications, like the checkout app, or focus on external attack surfaces to keep risk under an acceptable threshold.
Also, the platform also has smart workflows that allow security teams to communicate TruRisk to the right teams at the right level; for example, for executives, there are intuitive dashboards and TruRisk reports. Similarly, the operations team can smartly assign the work via existing ticketing systems. Finally, the auditors and compliance teams can benefit from compliance reporting.
Finally, the TruRisk platform allows the security team to eliminate risk using Qualys patching and compensating controls. This holistic approach of measure, communicate, and eliminate, fosters a virtuous cycle that enables teams to effectively manage risk across diverse environments.
Practical Benefits of the Qualys Detection Score (QDS)
Compared to CISA Vulnrichment
Currently, the CISA vulnrichment project only covers approximately 1,300 out of 240K+ vulnerabilities (~0.5% coverage). Security teams can use the SSVC framework to score the remaining vulnerabilities in-house. However, significant effort is required to build, implement, and maintain data pipelines to answer the questions for every CVE. In comparison, Qualys TruRisk generates QDS scores for close to 230K+ vulnerabilities, and they are calculated out of the box by the Qualys platform, which takes responsibility for creating data pipelines and marrying all the context. This significantly reduces the cost and burden in-house.
Also, using the SSVC framework, the security team might have many vulnerabilities in the “act” bucket. How do they prioritize within that bucket? Here, having a QDS score in the 0-100 range allows security users to prioritize within a bucket.
Like SSVC outcomes, the QDS scores are split into four categories – Low, Medium, High, and Critical: ranging from 1 to 100. Here are some examples of QDS score guidance that we give our customers and how they are aligned with the CISA SSVC guidelines:
| QDS Score | QDS Category | Description | Mapping to SSVC |
|---|---|---|---|
| 90-100 | Critical | CVSS Critical, exploited in the wild, weaponized exploit available, trending on social media, dark web | Act |
| 70-89 | High | CVSS Critical, exploited in the wild, weaponized exploit available, trending on social media, dark web | Attend |
| 40-69 | Medium | CVSS critical, no exploits available. | |
| CVSS High, a Proof of Concept (PoC) exploit is available | Track* | ||
| 1-39 | Low | CVSS Medium, a PoC exploit is available. | |
| CVSS Low, no PoC exploit available | Track |
Practical Examples
EPSS and CVSS
Below are a few examples highlighting the benefits of a multi-dimensional risk approach.
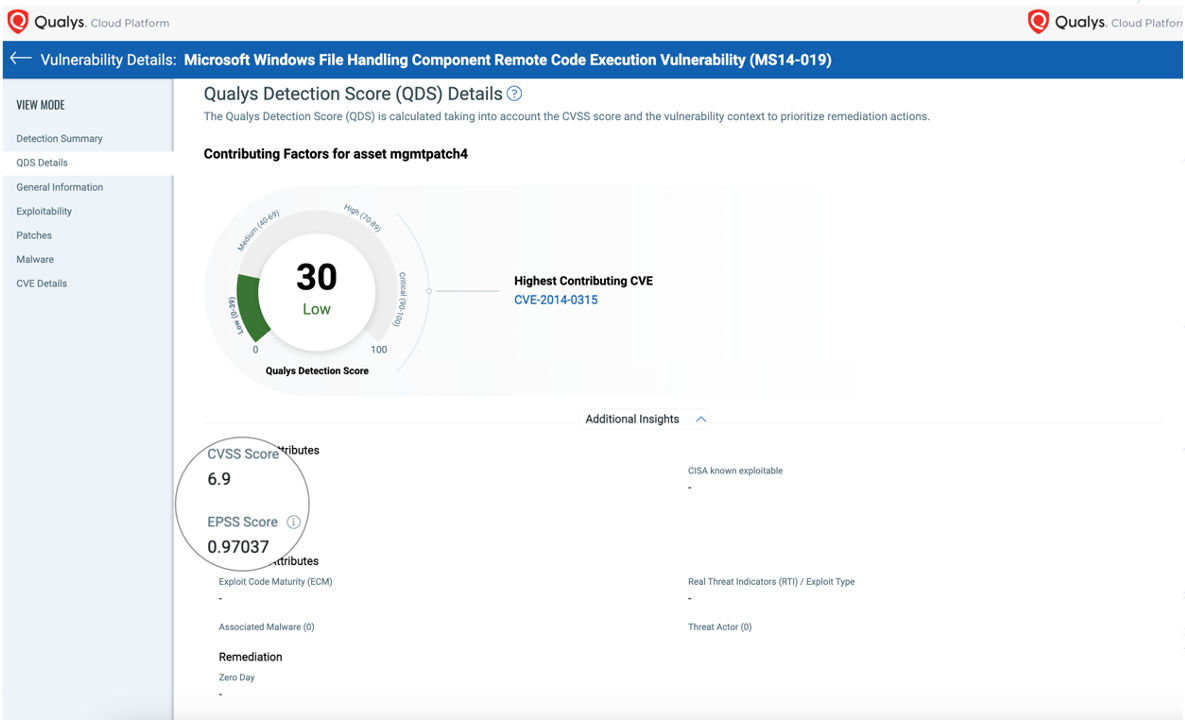
High CVSS/EPSS but Low QDS
Here is a vulnerability, Microsoft Windows File Handling Component RCE (MS14-019), with a medium-high CVSS score and a very high EPSS score. There is no evidence of exploitation. Even though EPSS and CVSS rate it high, QDS rates it as a low-risk CVE.
Low CVSS/EPSS but High QDS
On the contrary, there is another vulnerability, VMware Tools Authentication Bypass Vulnerability (VMSA-2023-0013), with low CVSS and EPSS scores. However, there is ample evidence that it is actively exploited and trending, hence it gets a critical QDS score.
CISA Vulnrichment Project
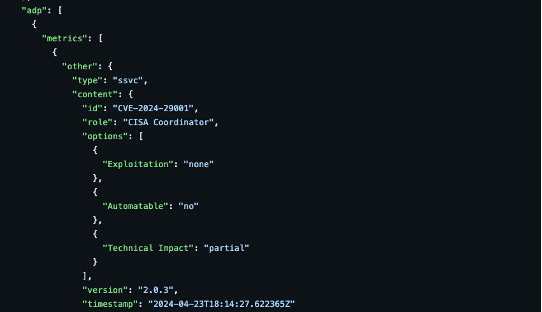
Here, a Microsoft vulnerability has an active exploitation, with total technical impact. This information is in line with what you see with QDS for the same CVE. There are threat actors involved, and the CVE is trending.

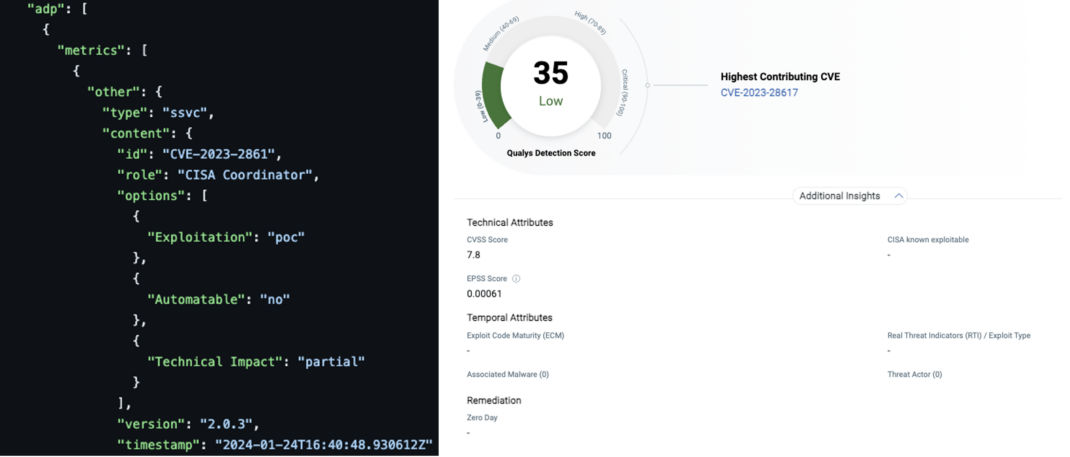
Similarly, another Linux CVE has a poc exploitation with partial impact. This information is in line with what you see with QDS for the same CVE. Also, no threat actor actively exploits the CVE; hence, the score is low.
Summary
In conclusion, the CISA Vulnrichment framework can be effective in improving the vulnerability management lifecycle. Unfortunately, it covers only ~1,300 CVEs or about 0.5% of the overall CVE landscape.
Qualys TruRisk uses vulnerability, threat, and business context to score CVEs. It integrates with 25+ threat and exploit intelligence sources to incorporate a wide array of vulnerability intelligence into the risk assessment capabilities of TruRisk. The real-time threat indicators cover most of the elements of Vulnrichment and allow customers to get the same outcome for all the CVEs.
For Qualys customers interested in implementing Vulnrichment/SSVC in their environments, the framework can be swiftly operationalized by adopting TruRisk. For new teams, you can get a free trial of Qualys VMDR with TruRisk.
6.9 Medium
AI Score
Confidence
High