
Microsoft and Adobe Patch Tuesday (August 2021) – Microsoft 51 Vulnerabilities with 7 Critical, Adobe 29 Vulnerabilities
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
4.6 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:L/AC:L/Au:N/C:P/I:P/A:P
Microsoft Patch Tuesday – August 2021
Microsoft patched 51 vulnerabilities in their August 2021 Patch Tuesday release, and 7 of them are rated as critical severity. Three 0-day vulnerability patches were included in the release.
Critical Microsoft Vulnerabilities Patched
CVE-2021-36942 - Windows LSA Spoofing Vulnerability
An unauthenticated attacker could call a method on the LSARPC interface and coerce the domain controller to authenticate against another server using NTLM. A malicious user can use this attack to take complete control over windows domain Per Microsoft, this vulnerability affects all servers, but domain controllers should be prioritized in terms of applying security updates.
CVE-2021-34481 – Windows Print Spooler Remote Code Execution Vulnerability
A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. This Patch Tuesday Microsoft released security updates to address this vulnerability and should be prioritized.
Three 0-Day Vulnerabilities Patched
- CVE-2021-36936 - Windows Print Spooler Remote Code Execution Vulnerability
- CVE-2021-36942 - Windows LSA Spoofing Vulnerability
- CVE-2021-36948 - Windows Update Medic Service Elevation of Privilege Vulnerability - This has been actively exploited, per Microsoft.
Qualys QIDs Providing Coverage
| QID | Title | Severity | CVE ID |
|---|---|---|---|
| 110388 | Microsoft SharePoint Enterprise Server Multiple Vulnerabilities August 2021 | Medium | CVE-2021-36940 |
| 110389 | Microsoft Office and Microsoft Office Services and Web Apps Security Update August 2021 | High | CVE-2021-34478, CVE-2021-36941 |
| 375798 | Microsoft Azure CycleCloud Elevation of Privilege Vulnerability August 2021 | Medium | CVE-2021-33762, CVE-2021-36943, KB3142345 |
| 91801 | Microsoft Dynamics Business Central Cross-Site (XSS) Scripting Vulnerability August 2021 | Medium | CVE-2021-36946 |
| 91802 | Microsoft Windows Security Update for August 2021 |
| High| CVE-2021-26424, CVE-2021-26425, CVE-2021-26426, CVE-2021-26431, CVE-2021-26432, CVE-2021-26433, CVE-2021-34480, CVE-2021-34483, CVE-2021-34484, CVE-2021-34486, CVE-2021-34487, CVE-2021-34530, CVE-2021-34533, CVE-2021-34534, CVE-2021-34535, CVE-2021-34536, CVE-2021-34537, CVE-2021-36926, CVE-2021-36927, CVE-2021-36932, CVE-2021-36933, CVE-2021-36936, CVE-2021-36937, CVE-2021-36938, CVE-2021-36947, CVE-2021-36948
91803| Microsoft Windows Local Security Authority (LSA) Spoofing Vulnerability August 2021 | High| CVE-2021-36942
91804| Microsoft Windows Defender Elevation of Privilege Vulnerability August 2021 | Medium| CVE-2021-34471
91805| Microsoft Windows 10 Update Assistant Elevation of Privilege Vulnerability August 2021 | Medium | CVE-2021-36945
91806| Microsoft Azure Active Directory Connect Authentication Bypass Vulnerability August 2021 | Medium| CVE-2021-36949
91774| Microsoft .NET Core and ASP.NET Core Security Update for August 2021 | High| CVE-2021-26423, CVE-2021-34485, CVE-2021-34532
91809| Microsoft Visual Studio Security Update for August 2021 | Medium| CVE-2021-26423, CVE-2021-34485, CVE-2021-34532
Adobe Patch Tuesday – August 2021
Adobe addressed 29 CVEs this Patch Tuesday impacting Adobe Connect and Magento product. The patches for Magento are labeled as Priority 2, while the remaining patches are set to Priority 3.
| Adobe Security Bulletin | QID | Severity | CVE ID |
|---|---|---|---|
| Adobe Connect Multiple Vulnerabilities (APSB21-66) | 730152 | Medium | CVE-2021-36061, CVE-2021-36062, CVE-2021-36063 |
Discover Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:91774 OR qid:91801 OR qid:91802 OR qid:91803 OR qid:91804 OR qid:91805 OR qid:91806 OR qid:91809 OR qid:375798 OR qid:110389 OR qid:110388 OR qid:730152)
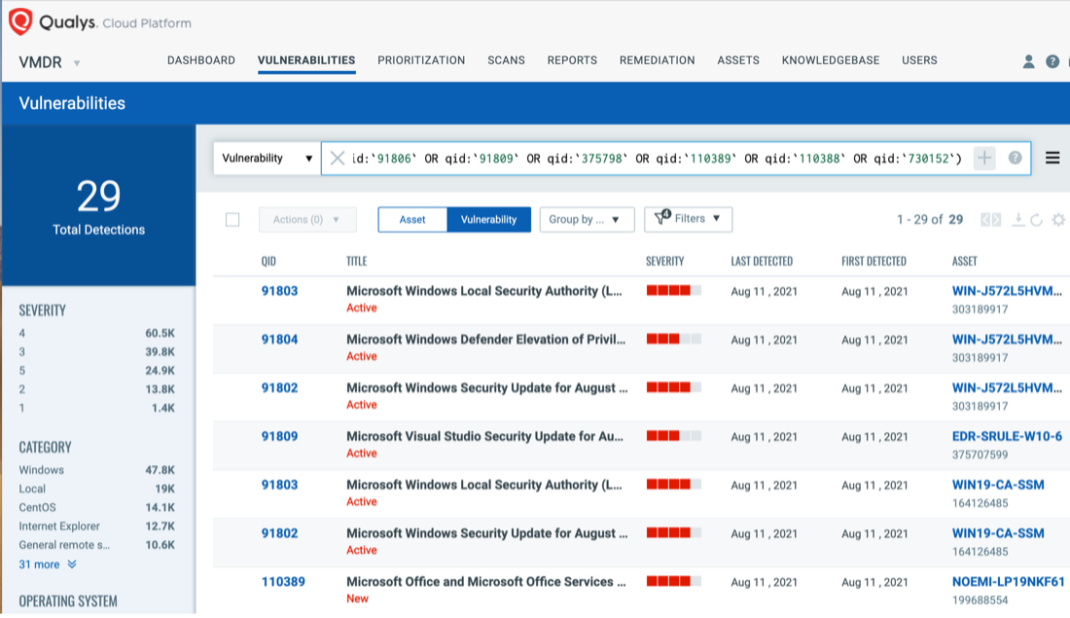
Respond by Patching
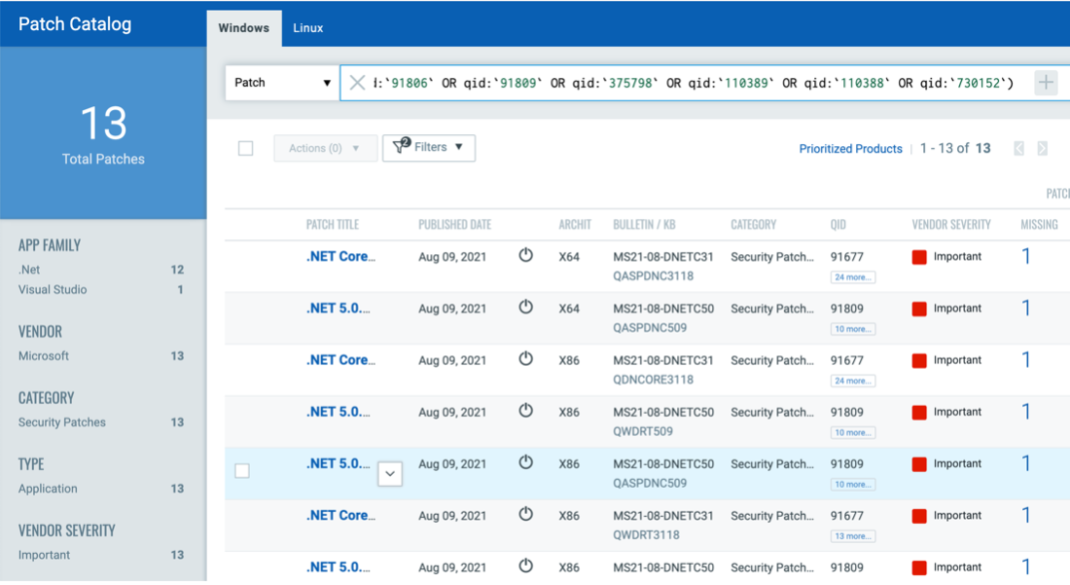
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday.
(qid:91774 OR qid:91801 OR qid:91802 OR qid:91803 OR qid:91804 OR qid:91805 OR qid:91806 OR qid:91809 OR qid:375798 OR qid:110389 OR qid:110388 OR qid:730152)
Patch Tuesday Dashboard
The current updated Patch Tuesday dashboards are available in Dashboard Toolbox: 2021 Patch Tuesday Dashboard.
Webinar Series: This Month in Vulnerabilities and Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series This Month in Vulnerabilities and Patches.
We discuss some of the key vulnerabilities disclosed in the past month and how to patch them:
- Microsoft Patch Tuesday, August 2021
- Adobe Patch Tuesday, August 2021
Join us live or watch on demand!
 Webinar August 12, 2021 or on demand.
Webinar August 12, 2021 or on demand.
About Patch Tuesday
Patch Tuesday QIDs are published at Security Alerts, typically late in the evening of Patch Tuesday, followed shortly after by PT dashboards.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
4.6 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:L/AC:L/Au:N/C:P/I:P/A:P