TruRisk™️ Insights – The Story Behind a TruRisk Score
7.7 High
AI Score
Confidence
Low
In the world of cloud and SaaS security, where risks arise not only from vulnerabilities but also from misconfigurations and various threats, the task of prioritizing and managing them becomes increasingly complex. It's not just about identifying vulnerabilities; it's also crucial to recognize and address the multitude of risks that stem from misconfigured systems and emerging threats. This broader perspective on risk is essential for maintaining robust cybersecurity in the cloud and ensuring that critical issues are addressed effectively and efficiently.
Understanding this expanded risk landscape, it becomes evident that conventional approaches to measuring risks for vulnerabilities, misconfigurations, and threats in a siloed way using siloed tools will fall short. This realization has led Qualys to build TotalCloud 2.0, a comprehensive cloud and SaaS security solution that can correlate and quantify risks from multiple sources to provide a unified prioritized view of risk.
2.0, a comprehensive cloud and SaaS security solution that can correlate and quantify risks from multiple sources to provide a unified prioritized view of risk.
 Figure 1: TotalCloud capabilities
Figure 1: TotalCloud capabilities
Qualys quantifies risk in two primary ways: ** **
- TruRisk Score is a quantified indicator of the level of risk.
- TruRisk Insights is a curated collection of risk factors that, when combined, significantly elevate the risk of a breach.
The TruRisk Score
The TruRisk Score uses a holistic approach that accounts for the variety and complexity of risks from all fronts - vulnerabilities, misconfigurations, and threats, and adds business context, such as asset criticality - to quantify risk. It is computed using sophisticated algorithms to analyze a multitude of factors to provide an actionable risk score. The TruRisk Score effectively bridges the gap between technical vulnerabilities and their business impact, making it easier for organizations to understand and act upon their security posture.
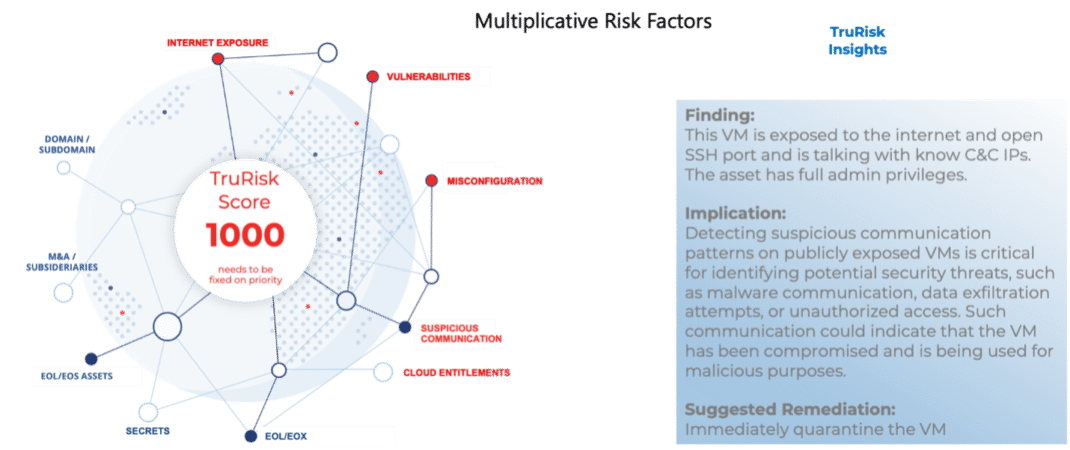 Figure 2: Relationship between TruRisk Score and TruRisk Insight
Figure 2: Relationship between TruRisk Score and TruRisk Insight
TruRisk Insights
TruRisk Insights is a story of the TruRisk Score - offering insights into the severity, potential impact, and context of each identified threat. This storytelling approach transforms abstract data into meaningful information, aiding decision-makers in understanding the 'why' behind each score. It scrutinizes the myriad factors contributing to a TruRisk score and emphasizes the most critical aspects that demand immediate attention. By doing so, TruRisk Insights empowers cybersecurity teams to not only identify but also to prioritize remediation efforts effectively, ensuring that resources are allocated to the areas of the highest impact.
Consider a common situation in organizations where all external-facing assets are deemed high-risk. This generalized approach complicates prioritization and increases the time for remediation. However, with TruRisk, we can distinguish the truly critical assets even among those with high scores (800+). But what about situations where numerous assets still fall into this high-risk category? This is where the TruRisk Insights proves invaluable. It doesn't just assess individual risk factors; it identifies combinations of risks that significantly increase the likelihood of a breach. TruRisk Insights then articulates these risks in clear terms and pinpoints the specific assets bearing these critical risk factors.
For instance, it can highlight assets vulnerable to port scans, a common precursor to exploiting remotely accessible vulnerabilities like Apache Struts 2. In such cases, TruRisk Insights would prioritize the hosts with critical vulnerabilities currently undergoing port scans, suggesting immediate patching. This fine-tuned approach not only identifies vulnerable systems but also narrows down the focus to those at imminent risk, exemplifying how TruRisk Insights effectively hones in on the most exploitable systems. With a single list of prioritized assets, the remediation efforts can be more focused and effective, reducing the mean time to remediation and allowing security teams to optimize their efforts and fix the most critical issues, first.
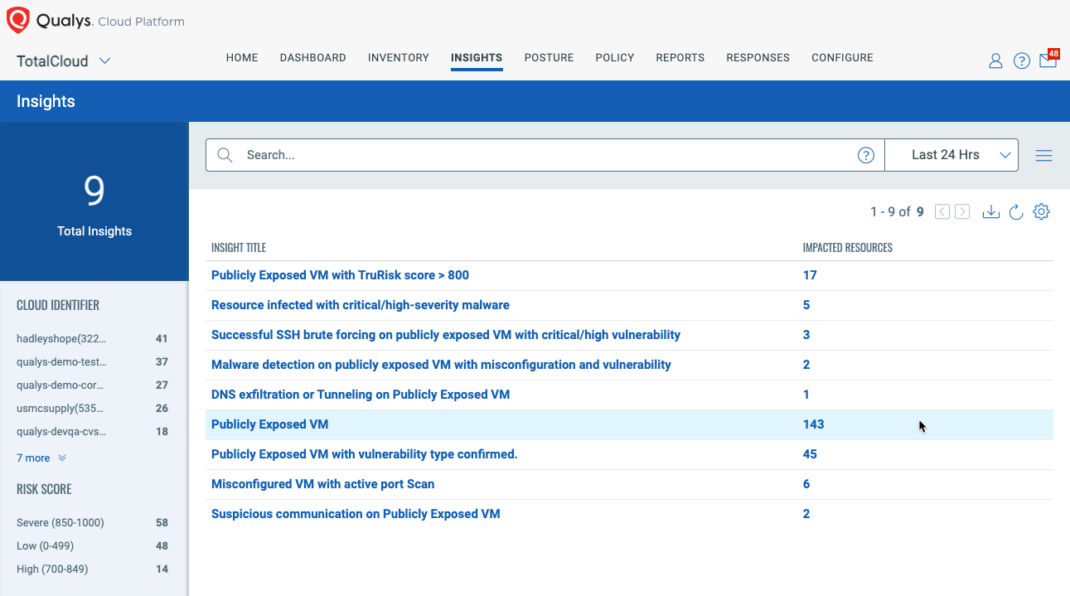
The most critical TruRisk Insights for public-facing workloads
TotalCloud has a number of out-of-the-box TruRisk Insights. The following are the most critical TruRisk Insights for the public-facing workloads:
Publicly exposed VM with TruRisk Score > 800
Publicly exposed virtual machines (VMs) represent a critical attack surface for cybercriminals. These VMs often harbor vulnerabilities that can be easily exploited due to their accessibility from the internet. The critical nature of identifying and mitigating risks associated with these VMs cannot be overstated, as they may serve as entry points for attackers to penetrate deeper into the cloud infrastructure. Such breaches can lead to data breaches, system compromises, and significant operational disruptions.
Within TotalCloud, each compute asset in the cloud is assigned a TruRisk score. A high TruRisk score signifies that the asset has a substantial financial impact on the organization if compromised and possesses one or more remotely exploitable high-severity vulnerabilities. Furthermore, it indicates that the vulnerability either has available exploits or is being actively exploited by malware. This insight integrates the public exposure attribute, evaluated using cloud asset metadata, with a high TruRisk score—calculated based on a comprehensive vulnerability assessment. This insight helps prioritize assets that require immediate remediation efforts.
Successful SSH brute forcing on publicly exposed VM with critical/high vulnerability****
SSH brute force attacks are a common method attackers use to gain unauthorized access to computer systems. If a publicly exposed virtual machine is successfully targeted by such an attack, it means there has been a failure in implementing basic security measures, such as strong password policies or SSH key authentication. Such an attack can result in the compromise of the targeted virtual machine. If the targeted virtual machine has a critical or high vulnerability, attackers can easily exploit those vulnerabilities to escalate privileges, deploy malware, or use the compromised system to launch further attacks within the network. It is crucial to prevent these attacks to maintain the security of cloud environments and safeguard against unauthorized access and data exfiltration.
This insight combines detections from TotalCloud CSPM, which will identify any firewall rules that allow exposure of port 22 and will identify the public-facing compute workloads, with the results of TotalCloud CWP vulnerability assessment and brute-force detections from TotalCloud CDR to identify workloads that are subject to these attacks.
Misconfigured VM with an active port scan
Misconfigurations are one of the leading causes of security breaches in cloud environments. VMs with misconfigurations, such as unnecessarily open ports or incorrect security settings, are vulnerable to exploitation. Active port scanning by attackers aims to discover these vulnerabilities, which can then be exploited to gain unauthorized access or disrupt services. Proactively identifying and remediating misconfigurations is essential to reduce the attack surface and prevent potential security incidents.
By integrating the findings from TotalCloud CSPM, which identifies compute workloads with open ports, with TotalCloud CDR's detections for those workloads, this insight sheds light on potentially misconfigured firewall rules.
Suspicious communication on publicly exposed VM
Detecting suspicious communication patterns on publicly exposed VMs is critical for identifying potential security threats, such as malware communication, data exfiltration attempts, or unauthorized access. Such communication could indicate that the VM has been compromised and is being used for malicious purposes. Monitoring and analyzing network traffic for anomalies allows organizations to respond quickly to potential threats, minimizing the risk of data breaches and ensuring the security of cloud workloads against advanced persistent threats and other cyberattacks.
TotalCloud CDR offers a 100% agentless method to monitor network activity on compute workloads. Utilizing network activity and flow logs, combined with threat feeds and ML-based learning, CDR identifies, with high confidence, workloads that are potentially compromised.
Malware detection on publicly exposed VM
Publicly exposed VMs are attractive targets for malware attacks due to their accessibility. Malware on these VMs can lead to a range of security issues, including data theft, ransomware, and further propagation of malware within the cloud environment. Detecting and addressing malware infections promptly is crucial to protecting sensitive information and maintaining operational continuity. Regular security audits, vulnerability management, and employing endpoint protection solutions are vital for detecting and mitigating malware threats before they can cause significant damage.
Traditional malware detection tools often fall short in cloud scenarios because they are tailored for endpoint contexts and utilize signature-based approaches, which are susceptible to evasion by slight modifications of the malware. In contrast, TotalCloud CDR employs an ML-based approach that does not depend on signatures, thus significantly reducing the chances of evasion by malware variants. Additionally, TotalCloud CDR is specifically optimized for server workloads, enabling it to detect threats well in advance of many competing products.
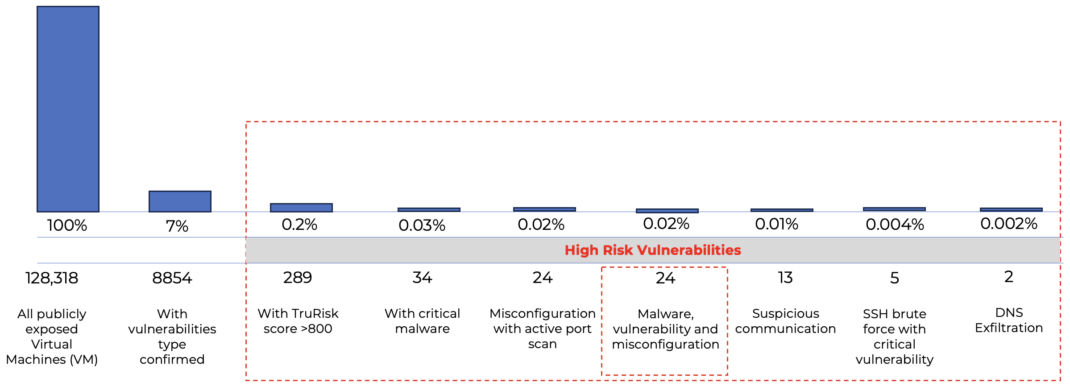
TruRisk Insights has significantly streamlined the identification of high-risk assets for our customers. Based on the Qualys Threat Research Unit's (TRU) analysis of anonymized data from customers that have enabled the CSPM and CDR capabilities, 10% of total workloads in public clouds are internet-facing, posing potential external threats. With TruRisk Insights, we've been able to focus on the most critical issues, pinpointing 0.2% of assets that possess critical exploitable vulnerabilities. These assets are prioritized due to their high severity and the potential for exploitation, making them urgent in terms of risk management. This efficient prioritization process aids customers in rapidly addressing the most significant threats to their cloud-hosted workloads.
We are starting the TruRisk Insights journey with this TotalCloud 2.0 release. We expect to add a lot more insights in the upcoming months, including the capability to create your own insights.
To experience TruRisk Insights, sign up for a 30-day, no-cost trial of TotalCloud 2.0 with TruRisk Insights today.
7.7 High
AI Score
Confidence
Low