
How to tell if a VPN app added your Windows device to a botnet
7.2 High
AI Score
Confidence
Low
On May 29, 2024, the US Department of Justice (DOJ) announced it had dismantled what was likely the world’s largest botnet ever. This botnet, called “911 S5,” infected systems at over 19 million IP addresses across more than 190 countries. The main sources of income for the operators, who stole a billions of dollars across a decade, came from committing pandemic and unemployment fraud, and by selling access to child exploitation materials.
The botnet operator generated millions of dollars by offering cybercriminals access to these infected IP addresses. As part of this operation, a Chinese national, YunHe Wang, was arrested. Wang is reportedly the proprietor of the popular service.
Of the infected Windows devices, 613,841 IP addresses were located in the United States. The DOJ also called the botnet a residential proxy service. Residential proxy networks allow someone in control to rent out a residential IP address which then can be used as a relay for their internet communications. This allows them to hide their true location behind the residential proxy. Cybercriminals used this service to engage in cyberattacks, large-scale fraud, child exploitation, harassment, bomb threats, and export violations.
To set up this botnet, Wang and his associates provided users with free, illegitimate VPN applications that were created to connect to the 911 S5 service. Unaware of the proxy backdoor, once users downloaded and installed these VPN applications, they unknowingly became part of the 911 S5 botnet.
Sometimes the VPN applications were bundled with games and other software and installed without user consent.
For this reason, the FBI has published a public service announcement (PSA) to help users find out if they have been affected by this botnet.
Users can start by going over this list of malicious VPN applications associated with the 911 S5 botnet:
- MaskVPN
- DewVPN
- PaladinVPN
- ProxyGate
- ShieldVPN
- ShineVPN
If you have one of these VPN applications installed, sometimes you can find an uninstaller located under the Start menu option of the VPN application. If present, you can use that uninstall option.
If the application doesn't present you with an uninstall option, then follow the steps below to attempt to uninstall the application:
- Click on the Start menu (Windows button) and type “Add or remove programs” to bring up the "Add and Remove Programs" menu.
- Search for the name of the malicious VPN application.
- Once you find the application in the list, click on the application name, and select the “Uninstall” option.
Once you have uninstalled the application, you will want to make sure it’s no longer active. To do that, open the Windows Task manager. Press Control+Alt+Delete on the keyboard and select the “Task Manager” option or right-click on the Start menu (Windows button) and select the "Task Manager" option.
In Task Manager look under the "Process" tab for the following processes:
- MaskVPN (mask_svc.exe)
- DewVPN (dew_svc.exe)
- PaladinVPN (pldsvc.exe)
- ProxyGate (proxygate.exe, cloud.exe)
- ShieldVPN (shieldsvc.exe)
- ShineVPN (shsvc.exe)
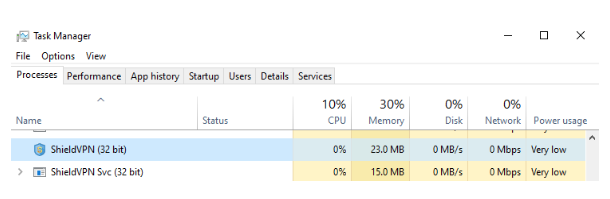 Example by FBI showing processes associated with ShieldVPN in Task Manager
Example by FBI showing processes associated with ShieldVPN in Task Manager
If found, select the service related to one of the identified malicious software applications running in the process tab and select the option “End task” to attempt to stop the process from running.
Or, download Malwarebytes Premium (there is a free trial) and run a scan.
Whether you're using the free or paid version of the app, you can manually run a scan to check for threats on your device.
- Open the app.
- On the main dashboard, click the Scanbutton.
- A progress page appears while the scan runs.
- After the scan finishes, it displays the Threat scan summary.
* If the scan detected no threats: ClickDone.
* If the scan detected threats on your device: Review the threats found on your computer. From here, you can manually quarantine threats by selecting a detection and clickingQuarantine. - Click View Report or**View Scan Report **to see a history of prior scans. After viewing the threat report, close the scanner window.
If neither of these options, including the Malwarebytes scan, resolve the problem, the FBI has more elaborate instructions. You can also contact the Malwarebytes Support team to assist you.
We don't just report on privacy—we offer you the option to use it.
Privacy risks should never spread beyond a headline. Keep your online privacy yours by using Malwarebytes Privacy VPN.
7.2 High
AI Score
Confidence
Low