Ivanti vulnerabilities now actively exploited in massive numbers
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
HIGH
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
7.4 High
AI Score
Confidence
Low
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N
0.964 High
EPSS
Percentile
99.5%
Last week we wrote about two vulnerabilities in all supported versions of Ivanti Connect Secure and Ivanti Policy Secure Gateways that were being actively exploited.
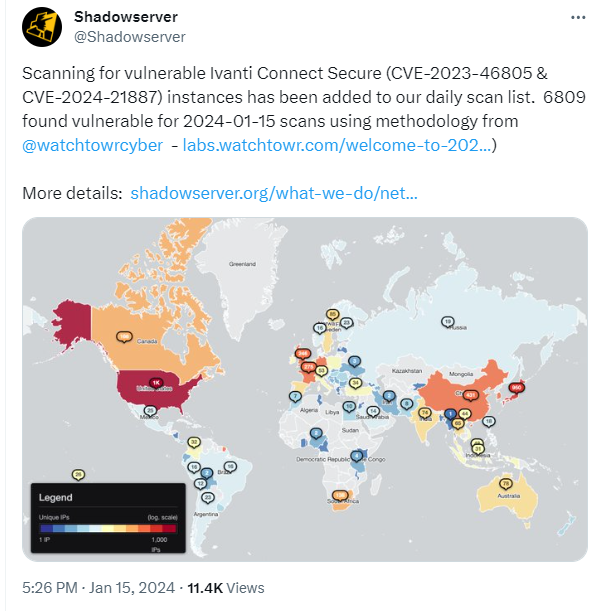
The researchers that discovered the active exploitation are warning that these attacks are now very widespread.
> "Victims are globally distributed and vary greatly in size, from small businesses to some of the largest organizations in the world, including multiple Fortune 500 companies across multiple industry verticals."
At first, the scans by the researchers showed only limited exploitation. But later they observed scans made by an unknown party that revealed compromised devices which had a different variant of the web shell on them. The latest numbers indicate some 1700 compromised devices.
The fact that there are no patches available and users were asked to apply a workaround and monitor their network traffic for suspicious activity, may have contributed to the slow response to the sounded alarms. Almost 7000 devices remain vulnerable according to the latest count.
The workaround requires importing a mitigation.release.20240107.1.xml file which can be obtained via the download portal (login required). The XML file is in the zipped format, so you’ll need to unzip and then import the XML file.
- Navigate to Maintenance >Import/Export>Import XML * Use theBrowse button to point to the unzipped XML file
- Click the Import Button
Importing this XML into any one node of a Cluster is enough. A FAQ and more detailed instructions can be found in the Ivanti advisory article.
It is important to note that applying the workaround or a patch, when they are made available, is not enough to undo the effects of an attack.
To find out whether your devices have been compromised, you can run the Integrity Checker Tool provided by Ivanti. This integrity tool allows an administrator to verify the integrity of the ICS / IPS Image installed on Virtual or Hardware Appliances This tool checks the complete file system and finds any additional/modified file(s).
We don’t just report on vulnerabilities—we identify them, and prioritize action.
Cybersecurity risks should never spread beyond a headline. Keep vulnerabilities in tow by using ThreatDown Vulnerability and Patch Management.
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
HIGH
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
7.4 High
AI Score
Confidence
Low
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N
0.964 High
EPSS
Percentile
99.5%