Lenovo VIBE, Moto, and ZUK Mobile Phone Remote Code Execution Vulnerability - Lenovo Support US
0.013 Low
EPSS
Percentile
86.0%
Lenovo Security Advisory: LEN-15374
Potential Impact: Remote code execution
Severity: High
Scope of Impact: The following mobile phones: all Lenovo VIBE and ZUK devices, and the Moto M (XT1663) and Moto E3 (XT1706) distributed by Lenovo.
CVE Identifier: CVE-2017-3758, CVE-2017-3759, CVE-2017-3760, CVE-2017-3761
Summary Description:
Vulnerabilities have been identified in the Lenovo Service Framework (LSF) Android application which is used by several different Android applications on Lenovo devices. The LSF is used to receive push notifications from Lenovo servers such as product promotions (e.g., app download recommendations), news, notices, surveys, and the like. In some cases, the push notifications are used to facilitate emergency app repairs and upgrades. The identified vulnerabilities could potentially be exploited by malware to download code onto the device from an arbitrary server resulting in remote code execution.
- CVE-2017-3758 – Improper access controls on several Android components in the Lenovo Service Framework application can be exploited to enable remote code execution.
- CVE-2017-3759 – The Lenovo Service Framework Android application accepts some responses from the server without proper validation. This exposes the application to man-in-the-middle attacks leading to possible remote code execution.
- CVE-2017-3760 – The Lenovo Service Framework Android application uses a set of nonsecure credentials when performing integrity verification of downloaded applications and/or data. This exposes the application to man-in-the-middle attacks leading to possible remote code execution.
- CVE-2017-3761 – The Lenovo Service Framework Android application executes some system commands without proper sanitization of external input. In certain cases, this could lead to command injection which, in turn, could lead to remote code execution.
Mitigation Strategy for Consumers (what you should do to protect yourself):
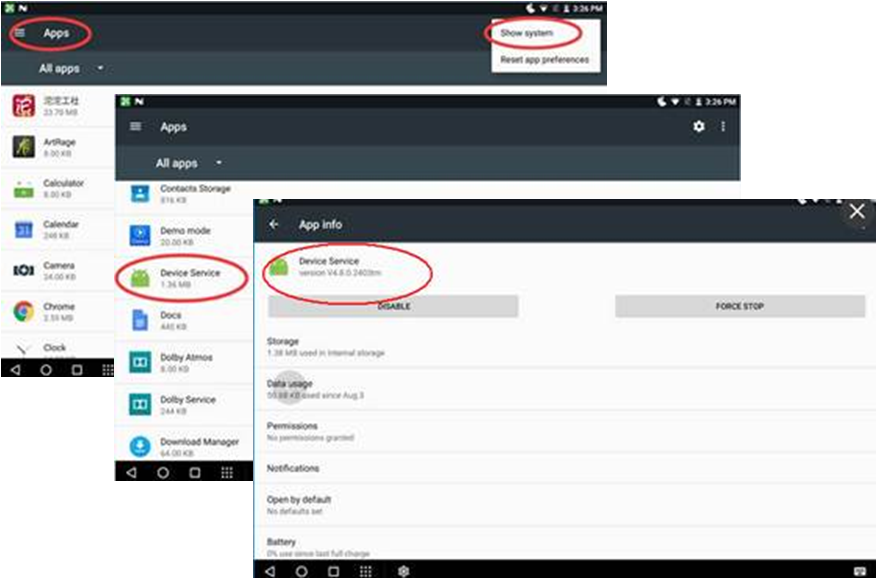
The vulnerabilities have been addressed in version V4.8.0.2403; users can verify that they have the correct version by opening the menu Settings–>Apps–>Device Service
If users discover that they still have a vulnerable version of the application, they can download the patched version from: <https://support.lenovo.com/us/en/solutions/ht505318>
.Product Impact:
The Lenovo Service Framework is installed on the following mobile phones: all Lenovo VIBE and ZUK devices, and the Moto M (XT1663) and Moto E3 (XT1706) distributed by Lenovo
Acknowledgements:
Lenovo thanks security researcher Imre Rad.
For a complete list of all Lenovo Product Security Advisories, click here.
Revision History:
Revision
|
Date
|
Description
—|—|—
2 | 10/17/2017 | Updated first paragraph under Mitigation Strategy for Consumers.
1
|
10/05/2017
|
Initial release.
For the most up to date information, please remain current with updates and advisories from Lenovo regarding your equipment and software. The information provided in this advisory is provided on as “as is” basis without any warranty or guarantee of any kind. Lenovo reserves the right to change or update this advisory at any time.
0.013 Low
EPSS
Percentile
86.0%