WEF - Wi-Fi Exploitation Framework
A fully offensive framework to the 802.11 networks and protocols with different types of attacks for WPA and WEP, automated hash cracking, bluetooth hacking and much more.
- I recommend you my alfa adapter: Alfa AWUS036ACM, which works really great with both, 2.4 and 5 Ghz
Tested and supported in Kali Linux,Parrot OS,Arch LinuxandUbuntu
However it’s not finished and may have issues, try it at your own risk.
If you have any issue please, contact me or create a issue
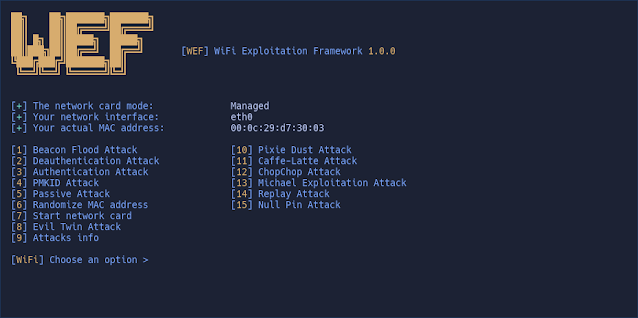
SUPPORTED ATTACKS:
- Deauthentication Attack
- Authentication Attack
- Beacon Flood Attack
- PKMID Attack
- EvilTwin Attack
- Passive/Stealthy Attack
- Pixie Dust Attack
- Null Pin Attack
- Chopchop Attack
- Replay Attack
- Michael Exploitation Attack
- Caffe-Latte Attack
- Jamming, Reading and Writing bluetooth connections
- GPS Spoofing with HackRF
FEATURES:
- Log generator
- WPA/WPA2, WPS and WEP Attacks
- Auto handshake cracking
- Multiple templates for EvilTwin attack
- Check monitor mode and it status
- 2Ghz and 5Ghz attacks
- Custom wordlist selector
- Auto detect requirements
- Bluetooth support (Jamming, Reading, Writing)
USAGE:
> Common usage of the framework
wef -i wlan0 # Your interface name might be different
or
wef --interface wlan0
Once the application is working, type ‘help’ to view more functions and useful info.
If you don’t want to scan APs with every attack you can do something like this:
set name my-wifi # To especify the name to attack
set time 60 # To define the total duration of the attacks that ask for the time
set packets 15 # To define the amount of packets that some attacks will send
REQUIREMENTS:
> Don’t install them manually, WEF takes care of that if you don’t already have them
aircrack-ng
reaver
mdk4
macchanger
hashcat
xterm
hcxtools
pixiewps
python3
btlejack
crackle
php
hostadp
dnsmasq
INSTALLATION:
Checkout the Wiki
DEMO:
> Demo on a Parrot OS with Kitty terminal
Created by D3Ext
> Extra
If you are using bspwm, you can add this line to your bspwmrc for launching the xterm windows always beeing in floating mode (for a prettier design)
bspc rule -a XTerm state=floating
Copyright © 2022, D3Ext