Cve-Collector - Simple Latest CVE Collector
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.6 High
AI Score
Confidence
Low
0.001 Low
EPSS
Percentile
39.3%
Simple Latest CVE Collector Written in Python
- There are various methods for collecting the latest CVE (Common Vulnerabilities and Exposures) information.
- This code was created to provide guidance on how to collect, what information to include, and how to code when creating a CVE collector.
- The code provided here is one of many ways to implement a CVE collector.
- It is written using a method that involves crawling a specific website, parsing HTML elements, and retrieving the data.
This collector uses a search query on <https://www.cvedetails.com> to collect information on vulnerabilities with a severity score of 6 or higher.
- It creates a simple delimiter-based file to function as a database (no DBMS required).
- When a new CVE is discovered, it retrieves “vulnerability details” as well.
- Set the
cvss_min_scorevariable.
- set this variable by combining search queries on the <https://www.cvedetails.com/vulnerability-search.php> page.
- Add addtional code to receive results, such as a
webhook.
- The location for calling this code is marked as “Send the result to webhook.”
- If you want to run it automatically, register it in
crontab or a similar scheduler.
# python3 main.py
*2023-10-10 11:05:33.370262*
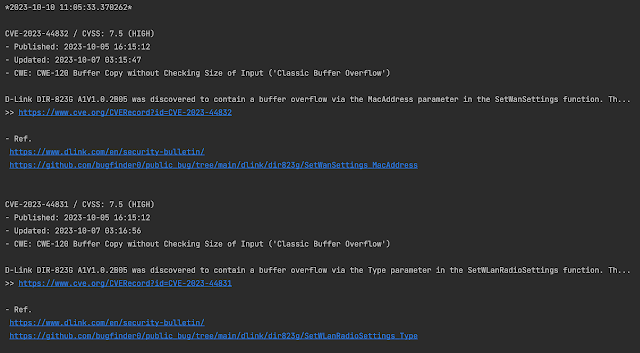
1. CVE-2023-44832 / CVSS: 7.5 (HIGH)
- Published: 2023-10-05 16:15:12
- Updated: 2023-10-07 03:15:47
- CWE: CWE-120 Buffer Copy without Checking Size of Input ('Classic Buffer Overflow')
D-Link DIR-823G A1V1.0.2B05 was discovered to contain a [buffer overflow](<https://www.kitploit.com/search/label/Buffer%20Overflow> "buffer overflow" ) via the MacAddress parameter in the SetWanSettings function. Th...
>> https://vulners.com/cve/CVE-2023-44832
- Ref.
(1) https://www.dlink.com/en/security-bulletin/
(2) https://github.com/bugfinder0/public_bug/tree/main/dlink/dir823g/SetWanSettings_MacAddress
2. CVE-2023-44831 / CVSS: 7.5 (HIGH)
- Published: 2023-10-05 16:15:12
- Updated: 2023-10-07 03:16:56
- CWE: CWE-120 Buffer Copy without Checking Size of Input ('Classic Buffer Overflow')
D-Lin k DIR-823G A1V1.0.2B05 was discovered to contain a buffer overflow via the Type parameter in the SetWLanRadioSettings function. Th...
>> https://vulners.com/cve/CVE-2023-44831
- Ref.
(1) https://www.dlink.com/en/security-bulletin/
(2) https://github.com/bugfinder0/public_bug/tree/main/dlink/dir823g/SetWLanRadioSettings_Type
(delimiter-based file database)
# vim feeds.db
1|2023-10-10 09:24:21.496744|0d239fa87be656389c035db1c3f5ec6ca3ec7448|CVE-2023-45613|2023-10-09 11:15:11|6.8|MEDIUM|CWE-295 Improper Certificate Validation
2|2023-10-10 09:24:27.073851|30ebff007cca946a16e5140adef5a9d5db11eee8|CVE-2023-45612|2023-10-09 11:15:11|8.6|HIGH|CWE-611 Improper Restriction of XML External Entity Reference
3|2023-10-10 09:24:32.650234|815b51259333ed88193fb3beb62c9176e07e4bd8|CVE-2023-45303|2023-10-06 19:15:13|8.4|HIGH|Not found CWE ids for CVE-2023-45303
4|2023-10-10 09:24:38.369632|39f98184087b8998547bba41c0ccf2f3ad61f527|CVE-2023-45248|2023-10-09 12:15:10|6.6|MEDIUM|CWE-427 Uncontrolled Search Path Element
5|2023-10-10 09:24:43.936863|60083d8626b0b1a59ef6fa16caec2b4fd1f7a6d7|CVE-2023-45247|2023-10-09 12:15:10|7.1|HIGH|CWE-862 Missing Authorization
6|2023-10-10 09:24:49.472179|82611add9de44e5807b8f8324bdfb065f6d4177a|CVE-2023-45246|2023-10-06 11:15:11|7.1|HIGH|CWE-287 Improper Authentication
7|20 23-10-10 09:24:55.049191|b78014cd7ca54988265b19d51d90ef935d2362cf|CVE-2023-45244|2023-10-06 10:15:18|7.1|HIGH|CWE-862 Missing Authorization
The methods for collecting CVE (Common Vulnerabilities and Exposures) information are divided into different stages. They are primarily categorized into two
(1) Method for retrieving CVE information after vulnerability analysis and risk assessment have been completed.
- This method involves collecting CVE information after all the processes have been completed.
- Naturally, there is a time lag of several days (it is slower).
(2) Method for retrieving CVE information at the stage when it is included as a vulnerability.
- This refers to the stage immediately after a CVE ID has been assigned and the vulnerability has been publicly disclosed.
- At this stage, there may only be basic information about the vulnerability, or the CVSS score may not have been evaluated, and there may be a lack of necessary content such as reference documents.
- This code is designed to parse HTML elements from cvedetails.com, so it may not function correctly if the HTML page structure changes.
- In case of errors during parsing, exception handling has been included, so if it doesn’t work as expected, please inspect the HTML source for any changes.
- Get free latest infomation. If useful to someone, Free for all to the last. (absolutely no paid)
- ID 2 is the channel created using this repository source code.
- If you find this helpful, please the **“star”** to support further improvements.
References
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.6 High
AI Score
Confidence
Low
0.001 Low
EPSS
Percentile
39.3%