Missing Function Level Access Control
EPSS
Percentile
64.9%
Vulnerability Type
Missing Function Level Access Control
Affected URL
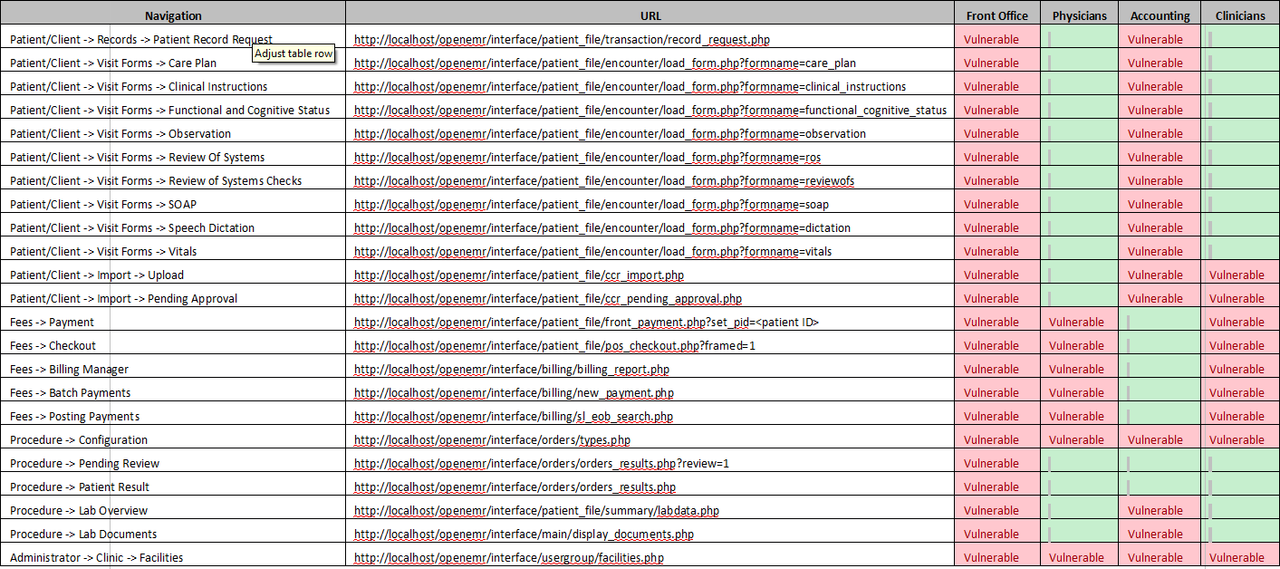
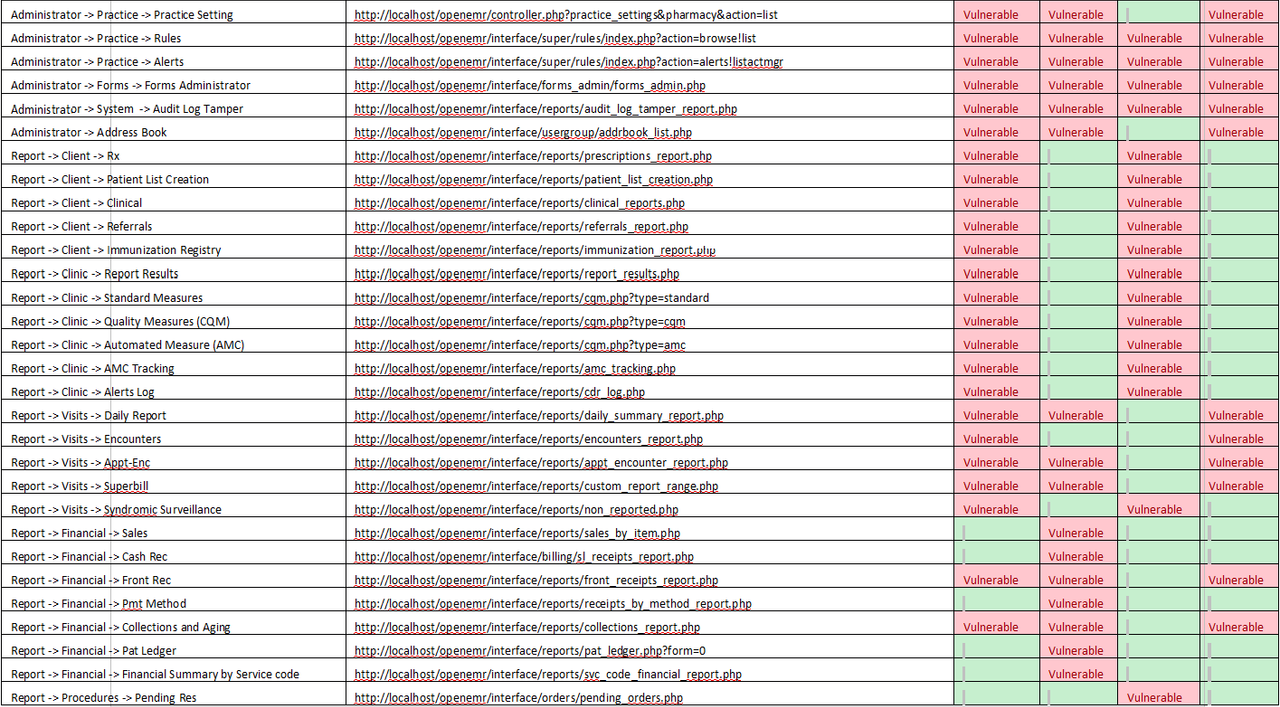
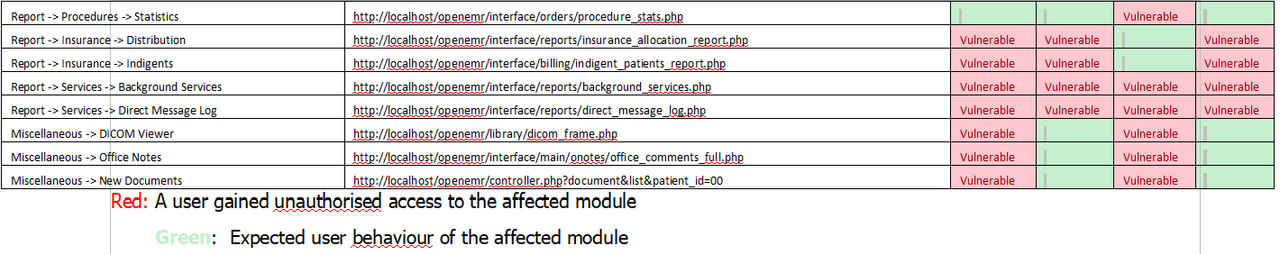
62 vulnerable instances as listed in Table 1
Authentication Required?
Yes
Issue Summary
Web applications usually only show functionality that a user has the need for and right to use in the UI. However, this is not the case for the OpenEMR. Non-privilege users (Accounting, Front-Office, Physician & Clinician) can directly browse to the administrator modules to compromise the confidentiality and integrity of the application. Additionally, the promiscuous privileges of user roles (Accounting, Front-Office, Physician & Clinician) allow users to access each other modules without restriction as listed in Table 1.
Recommendation
Disallow access to all functions in the application by default, then review the user roles matrix of the OpenEMR and apply access only to those users and other parts of the application that are permitted to use it. Don’t rely on the security by obscurity such as hiding buttons and links to functionality within the UI.
Credits
Aden Yap Chuen Zhen ([email protected])
Rizan, Sheikh ([email protected])
Ali Radzali ([email protected])
Issue Reproduction
Login as a user (e.g., Front Office). Choose and browse any of the URL that appear “Vulnerable” belong to user (e.g., Front Office) shown in the Error! Reference source not found… Below are several examples of the affected instances:
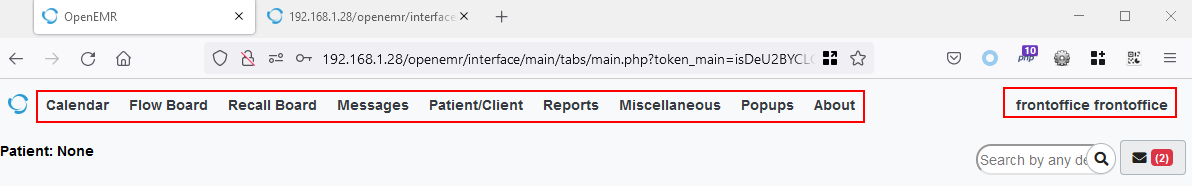
Figure 1: The Modules belong to Front Office user
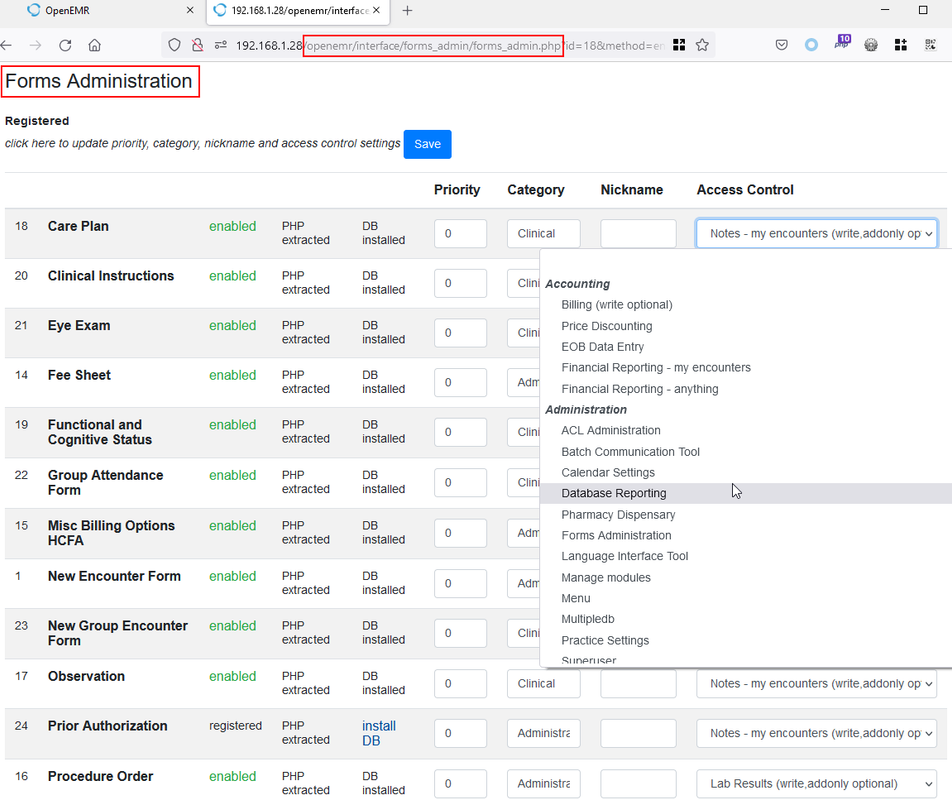
Figure 2: Front Office gained unauthorised access to “Administrator -> Forms -> Forms Administrator”: http://localhost/openemr/interface/forms_admin/forms_admin.php
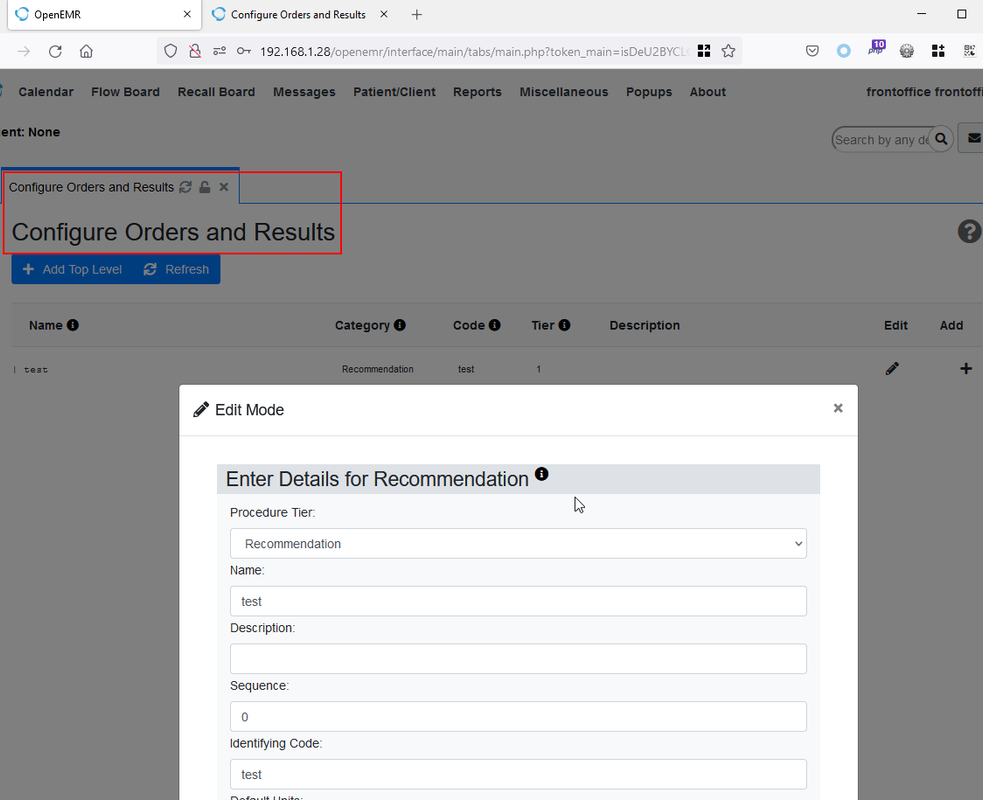
Figure 3: Accessed to Admin Module “Procedure -> Configuration”: http://localhost/openemr/interface/orders/types.php via window load module after tampered the endpoint using BurpSuite
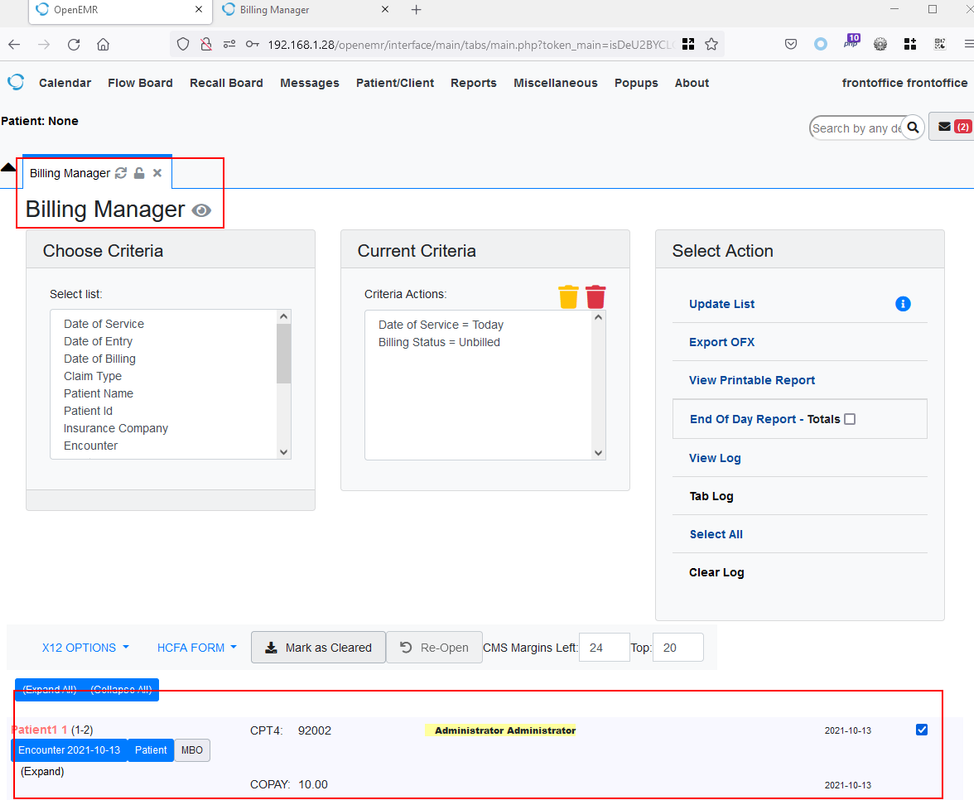
Figure 4: Front Office gained unauthorised access to Accounting module “Fees -> Billing Manager”: http://localhost/openemr/interface/billing/billing_report.php
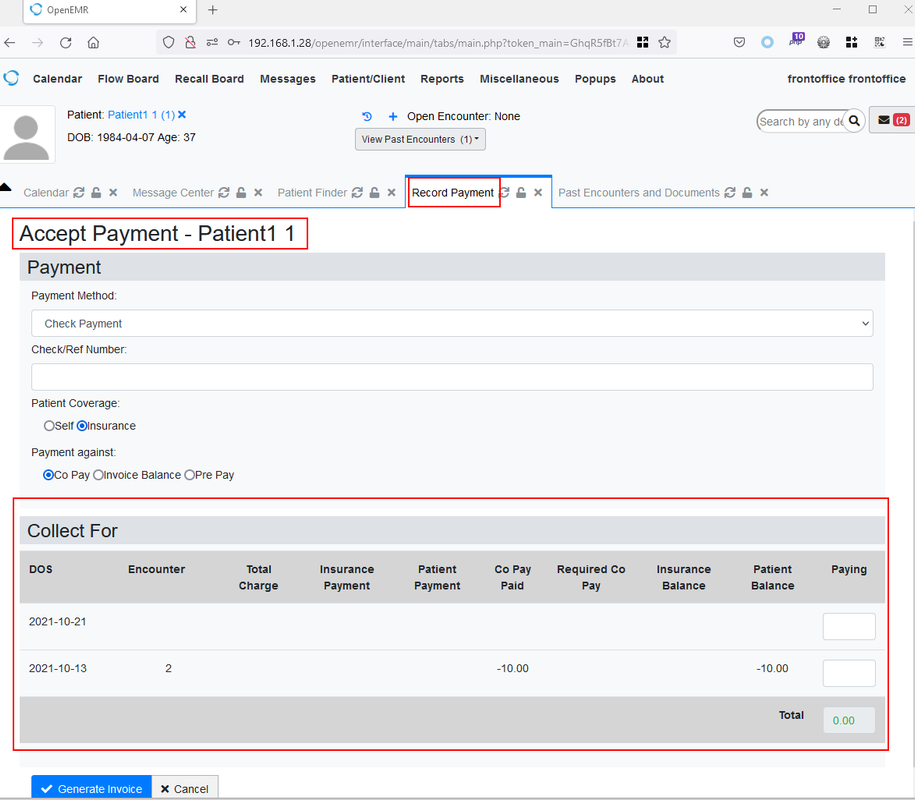
Figure 5: Front Office gained unauthorised access to Accounting module “Fees -> Payment”: http://localhost/openemr/interface/billing/billing_report.php