DOM-based Cross-Site Scripting (XSS) in OpenEMR 7.0.0 and below at White list files
EPSS
Percentile
73.3%
Description
We would like to report the vulnerability we found during software testing. The OpenEMR 7.0.0 (latest version) and below version; Open Source electronic health records and medical practice management application; has DOM-based Cross-Site Scripting (XSS) vulnerability in the add-manually-input field on white list file page that never been reported before (We’ve checked from CVE Official website).
Vulnerability Type
DOM-based Cross-Site Scripting (XSS)
Affected Page/URL
> https://<openemrurl>/interface/super/manage_site_files.php
Sample XSS Payload
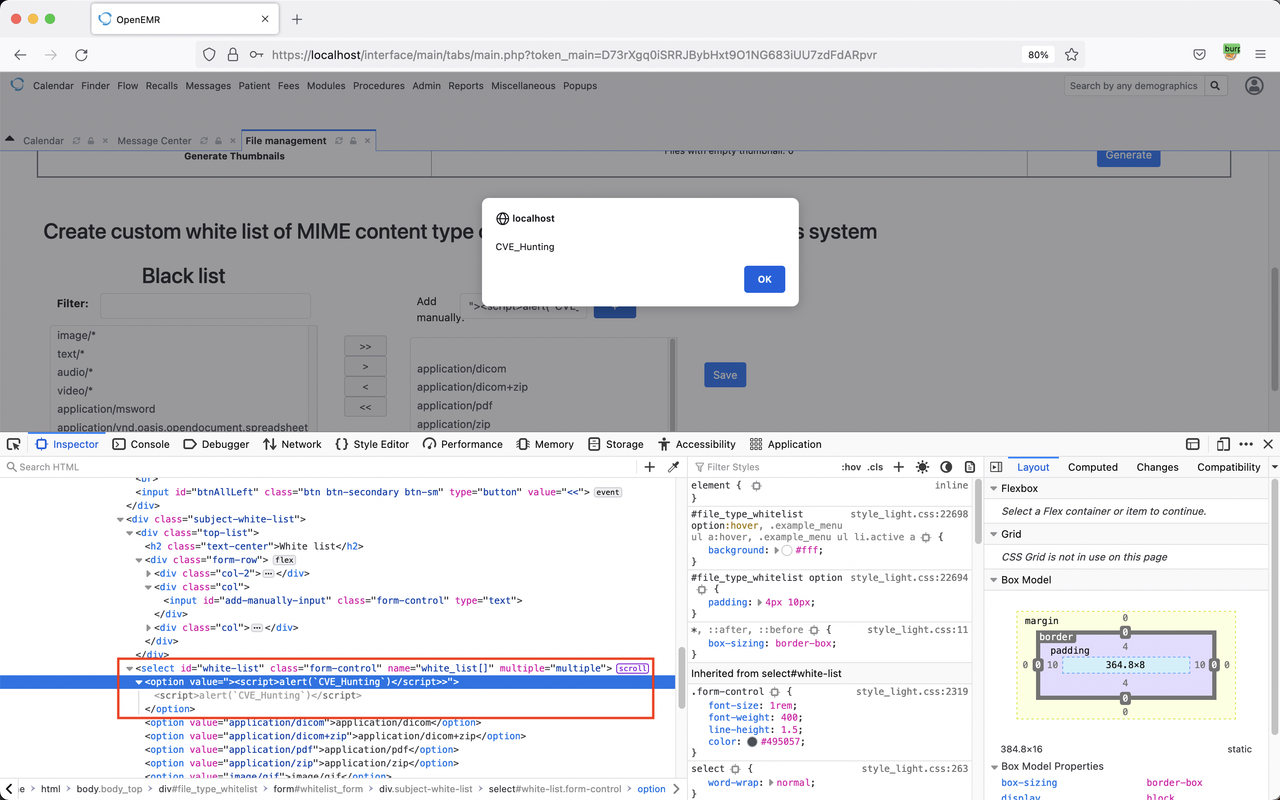
"><script>alert(`CVE_Hunting`)</script>
Vulnerable Source Code
> /var/www/localhost/htdocs/openemr/interface/super/manage_site_files.php (Please see more details in the occurrences section)
Implication
Client-side scripts are used extensively by modern web applications. They perform from simple functions (such as the formatting of text) up to full manipulation of client-side data and Operating System interaction.
Unlike traditional Cross-Site Scripting (XSS), where the client is able to inject scripts into a request and have the server return the script to the client, DOM XSS does not require that a request be sent to the server and may be abused entirely within the loaded page.
This occurs when elements of the DOM (known as the sources) are able to be manipulated to contain untrusted data, which the client-side scripts (known as the sinks) use or execute an unsafe way.
Scanner has discovered that by inserting an HTML element into the page’s DOM inputs (sources), it was possible to then have the HTML element rendered as part of the page by the sink.
Recommendation
Client-side document rewriting, redirection, or other sensitive action, using untrusted data, should be avoided wherever possible, as these may not be inspected by server side filtering.
To remedy DOM XSS vulnerabilities where these sensitive document actions must be used, it is essential to
- Ensure any untrusted data is treated as text, as opposed to being interpreted as code or mark-up within the page.
- Escape untrusted data prior to being used within the page. Escaping methods will vary depending on where the untrusted data is being used. (See references for details.)
- Use
document.createElement,element.setAttribute,element.appendChild, etc. to build dynamic interfaces as opposed to HTML rendering methods such asdocument.write,document.writeIn,element.innerHTML, orelement.outerHTMLetc.
Discoverer/Reporters
- Ammarit Thongthua, Rattapon Jitprajong and Nattakit Intarasorn from Secure D Center Research Team
Example PoC Screenshots
OpenEMR Version 6.1.0
OpenEMR Version 7.0.0
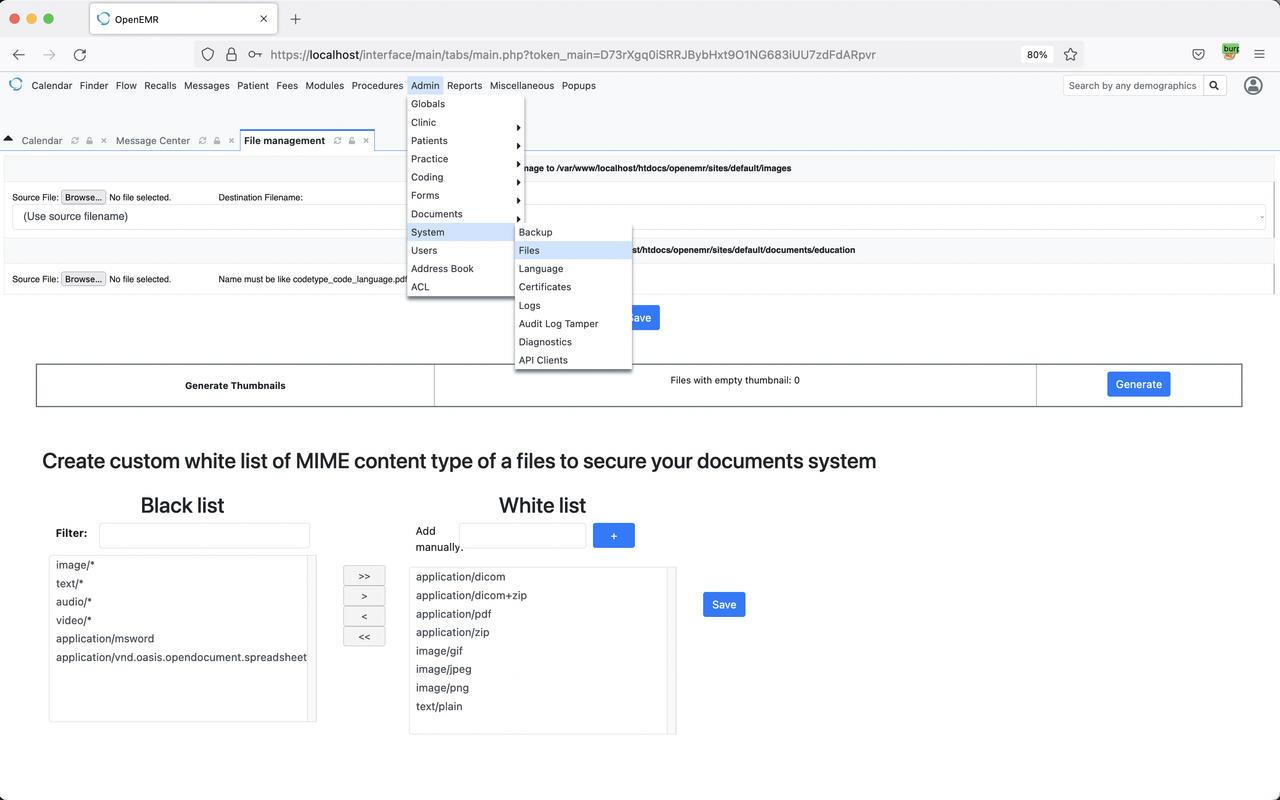
Admin > System > Files
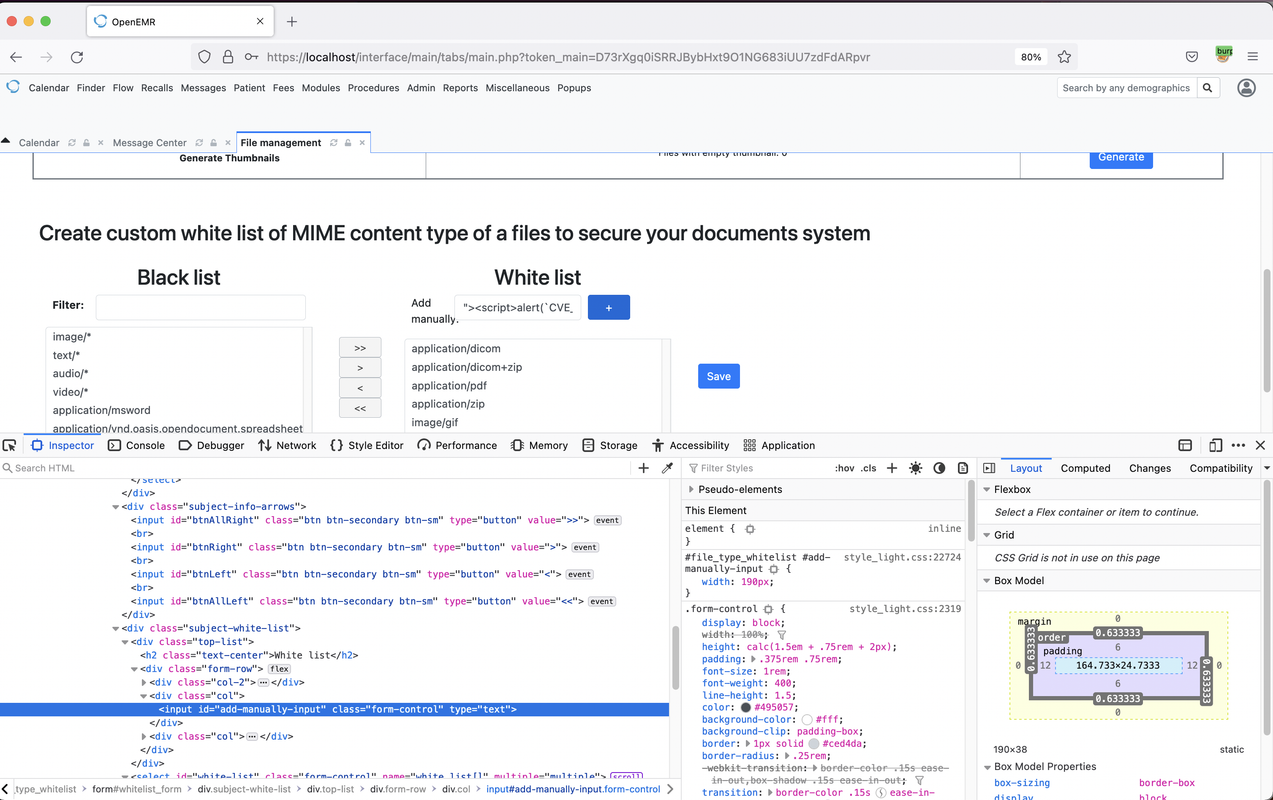
At the White list we Injected malicious JavaScript Payload in to {add-manually-input} with Sample XSS Payload
"><script>alert(`CVE_Hunting`)</script>