Reflected Cross Site Scripting
0.003 Low
EPSS
Percentile
69.2%
Vulnerability Type
Reflected Cross Site-Scripting (XSS)
Affected URL
https://localhost/openemr-6.0.0/interface/main/calendar/index.php
Affected Parameters
“newname”
Authentication Required?
Yes
Issue Summary
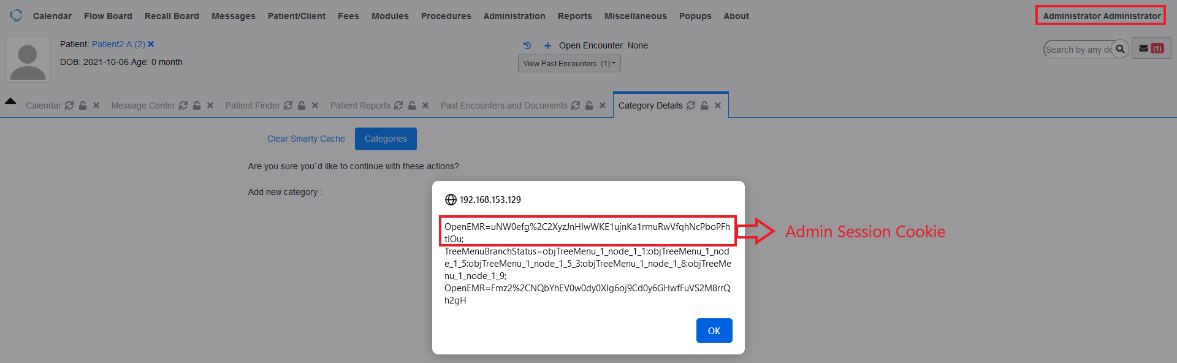
A reflected XSS vulnerability found in “/interface/main/calendar/index.php” that allows Admin user to inject arbitrary web script in one parameter (newname). The XSS payload will be reflected in the Confirmation page after the user click on Save for the new categories in Calendar.
Recommendation
Ensure to HTML encode before inserting any untrusted data into HTML element content. Ensure all inputs entered by user should be sanitized and validated before processing and storage.
Inputs should be filtered by the application, for example removing special characters such as < and > as well as special words such as script.
Credits
Aden Yap Chuen Zhen ([email protected])
Rizan, Sheikh ([email protected])
Ali Radzali ([email protected])
Issue Reproduction
Login as an Admin. Click on Administration > Clinic > Calendar and click on Categories after that.
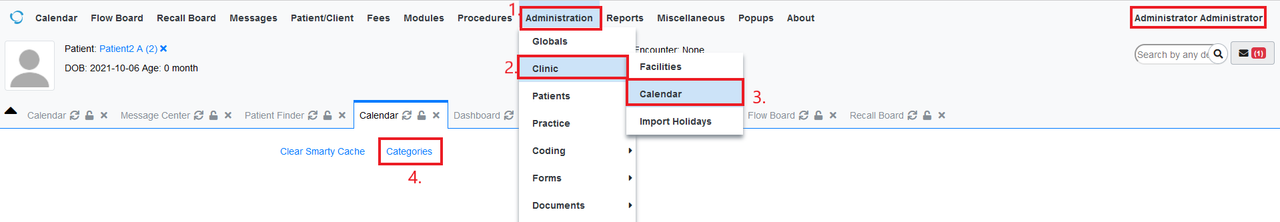
Figure 1: Login as Admin and Go to Calendar (Under Administration)
In New Category, insert this payload in the Name input box. Once done, click on Save.
<script>alert(document.cookie)</script>
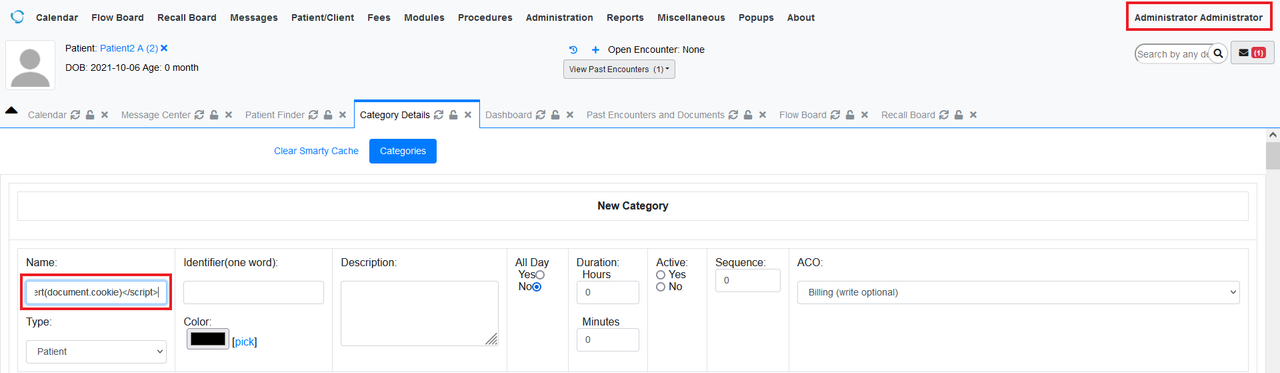
Figure 2: Insert Payload in Name
The XSS will be reflected on the confirmation page with the user cookies.