
Randori discovered Zero-day in Palo Alto’s GlobalProtect Firewall, affecting ~10,000 assets.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
Outline
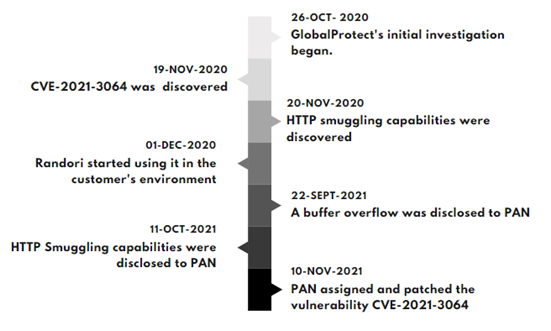
Palo Alto Networks (PAN) released an update on November 10, 2021, that patched CVE-2021-3064, which was discovered and disclosed by Randori. This vulnerability affects PAN firewalls that use the GlobalProtect Portal VPN, and it allows for unauthenticated remote code execution on susceptible product installations. The vulnerability affects all versions of PAN-OS 8.1 prior to 8.1.17, and Randori has discovered over 10,000 vulnerable instances on internet-facing assets.
Disclosure Timeline
Technical Overview
The researchers were able to successfully exploit the following systems that have GlobalProtect enabled and accessible:
- Palo Alto Networks PA-5220
- PAN-OS 8.1.16
- ASLR enabled in firmware for this device
- Palo Alto Networks PA-VM
- PAN-OS 8.1.15
- ASLR disabled in firmware for this device
Vulnerability & Exploit Details
The CVE-2021-3064 vulnerability is a buffer overflow that occurs while parsing user-supplied information into a fixed-length position on the stack. Without using an HTTP smuggling approach, the troublesome code is not accessible from the outside world. An unauthenticated network-based attacker can disrupt system operations and potentially execute arbitrary code with root privileges by exploiting a memory corruption vulnerability in Palo Alto Networks GlobalProtect portal and gateway interfaces. To exploit this vulnerability, the attacker must have network access to the GlobalProtect interface.
An attacker must have network access to the device on the GlobalProtect service port(default port 443) in order to exploit this issue. This port is frequently accessible over the Internet since the impacted product is a VPN portal. Exploitation is challenging but not impossible on devices that have ASLR enabled. Due to the lack of ASLR on virtualized devices, exploitation is considerably easier.
Mitigation and Patch Information
- A patch issued by the PAN should be used.
- PAN has also made Threat Prevention signatures 91820 and 91855 accessible for use by organizations to avoid exploitation until a software upgrade is scheduled.
- Organizations that do not use the PAN firewall's VPN features should immediately disable GlobalProtect.
References
Randori Report - <https://www.randori.com/blog/cve-2021-3064/>
Palo Alto Networks Security Advisory- <https://security.paloaltonetworks.com/CVE-2021-3064>
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C