
Are you a victim of the Conti Ransomware?
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
THREAT LEVEL: Red.
For a detailed advisory, download the pdf file here.
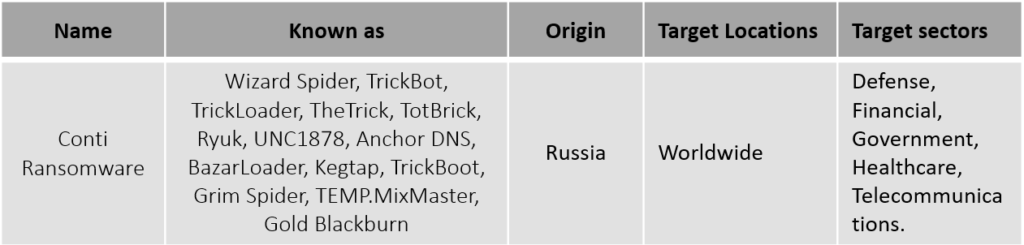
Conti Ransomware targets enterprises who have not patched their systems by exploiting old vulnerabilities. Conti Ransomware steals sensitive information from businesses and demands a ransom in exchange. CISA has issued a warning about the rise in Conti ransomware attacks. To avoid becoming a victim of Conti ransomware, the Hive Pro Threat Research team suggested you patch these vulnerabilities.
The techniques used by the Conti includes:
- T1078 - Valid Accounts
- T1133 - External Remote Services
- T1566.001 - Phishing: Spearphishing Attachment
- T1566.002 - Phishing: Spearphishing Link
- T1059.003 - Command and Scripting Interpreter: Windows Command Shell
- T1106 - Native API
- T1055.001 - Process Injection: Dynamic-link Library Injection
- T1027 - Obfuscated Files or Information
- T1140 - Deobfuscate/Decode Files or Information
- T1110 - Brute Force
- T1558.003 - Steal or Forge Kerberos Tickets: Kerberoasting
- T1016 - System Network Configuration Discovery
- T1049 - System Network Connections Discovery
- T1057 - Process Discovery
- T1083 - File and Directory Discovery
- T1135 - Network Share Discovery
- T1021.002 - Remote Services: SMB/Windows Admin Shares
- T1080 - Taint Shared Content
- T1486 - Data Encrypted for Impact
- T1489 - Service Stop
- T1490 - Inhibit System Recovery
Actor Details
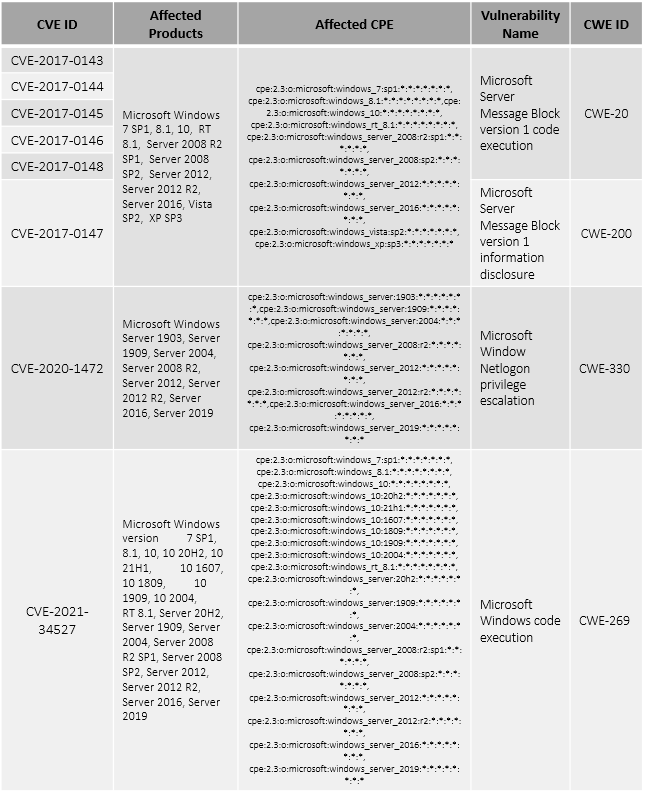
Vulnerability Details
Indicators of Compromise (IoCs)
| Type | Value |
|---|---|
| IPV4 | 162.244.80[.]235 |
| 85.93.88[.]165 | |
| 185.141.63[.]120 | |
| 82.118.21[.]1 |
Patch Links
<https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010>
<https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527>
<https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-1472>
References
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C