
Grafana releases an emergency patch for a Zero-Day vulnerability
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:N/A:N
THREAT LEVEL: Amber.
For a detailed advisory, download the pdf file here.
A vulnerability in Chrome and Microsoft Edge (Chromium-based) exists as a result of a use-after-free
Grafana, a database analyzing, and monitoring tool used by major companies has been affected by a high severe zero-day vulnerability.
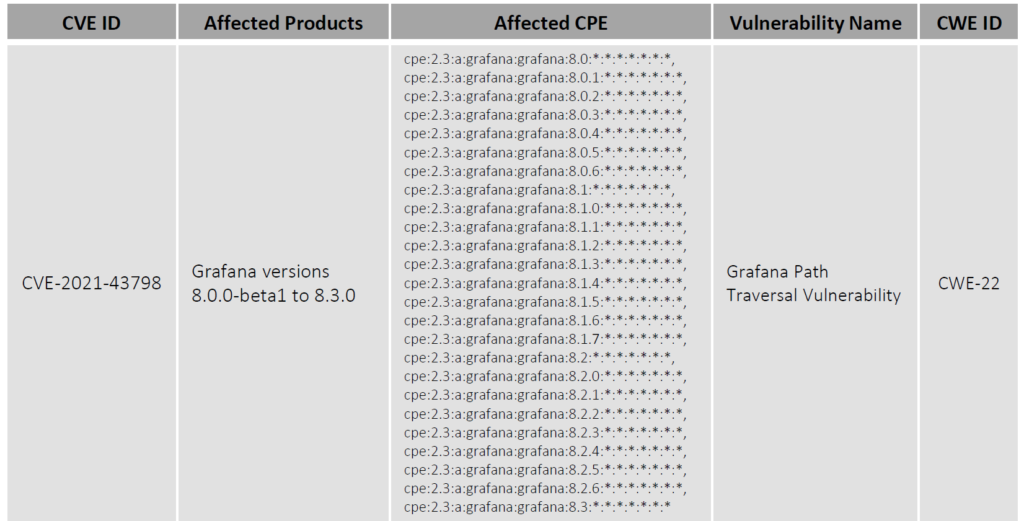
CVE-2021-43798 is a path traversal vulnerability that allows an attacker to traverse outside the Grafana folder and remotely access restricted files.
Grafana comes with some pre-installed plugins like graph, MySQL etc. The vulnerability affects the URL path of the plugins. So, all the Grafana instances are vulnerable. The vulnerable URL path is: <grafana_host_url>/public/plugins/<“plugin-id”> where <“plugin-id”> is the plugin ID for any installed plugin.
This vulnerability affects versions 8.0.0-beta1 through 8.3.0. and has been fixed in versions 8.3.1, 8.2.7, 8.1.8, and 8.0.7. An emergency patch has been released by Grafana Labs after exploits started circulating over Twitter and GitHub. Grafana has advised to update the affected systems as soon as possible. However, the organizations that cannot upgrade their systems can run a reverse proxy in front of Grafana that normalizes the PATH of the request which will eliminate this flaw.
Vulnerability Detail
Patch Link
Reference
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:N/A:N