
What is Penetration Testing❓ Definition, Stages, Techniques, Pros and Cons
The general concept is that penetration testing, frequently known as upright hacking, separates network security weaknesses by mimicking endeavors to penetrate protections. If it’s anything but, a real aggressor may exploit similar imperfections. Pen testing may manage a creation system or one which is put something aside for the analyzers.
The tests may be automated or manual, or analyzers may use a mix of the two. Mechanized instruments appreciate the advantages of caution and consistency. They cover all normal issues that could arise in a given environment. The tests are repeatable, so they can measure advance or investigate different foundations. The manual procedure permits analyzers to use their sense. Each site is extraordinary, and analyzers may consider likely weaknesses that the standard suite doesn’t cover.
Penetration testing definition
The procedure of scrutinizing your IT foundation’s security is called penetration testing. Penetration techniques are utilized to survey the wellbeing and security of an association in a controlled way. Working structures, organizations, applications, and, maybe most shockingly, end-customer conduct are totally examined to endorse flow security instruments and the sufficiency of end-customer security procedures.
There are different clarifications why penetration assessments ought to be managed consistently (or “pen tests”). As a primary goal, penetration testing may help guarantee the security of customer information, find security shortcomings, discover get away from provisions in the system, and break down the general strength of present defensive strategies. Also, infiltration testing can help a business keep alert to date with each new programming release. Lastly, as risks rise, it is important to get financial and PI data iteratively-transferring data between multiple end centers demands continual monitoring and assessment for security consistency when new devices are introduced to a structure.
In like manner, penetration testing has a couple of crucial advantages:
- It’s anything but an MSP to exhibit their mastery and ably oversee weaknesses proactively. It sets aside cash by permitting associations to keep away from personal network time.
- Penetration testing strategies can help MSP’s clients meet administrative necessities and stay away from fines.
- Toward the day’s end, it’s anything but a significant device to protect an MSP’s picture, notoriety, and client faithfulness.
Pen testing may sound like a weakness evaluation. However, the two online protection measures are not the equivalent-a weakness appraisal centers around distinguishing security issues inside an association. A rundown of weaknesses is created from an assessment of online protection and information stockpiling weaknesses. As it may, a penetration test utilizes assault mimicked situations in an objective, arranged way to deal with network safety. The test is intended to hit explicit targets, like a data set, stockpiling strategy, or assigned record. The consequence of a pen test isn’t just a rundown, yet a process and guide of precise places of shortcoming.
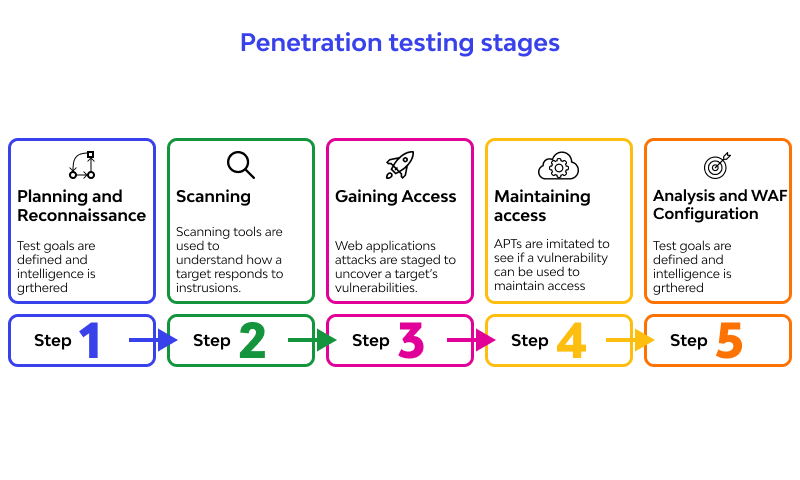
What are penetration testing stages?
You can conduct penetration analysis in five stages. Reconnaissance, scanning, and revelation, attack and obtaining admission, sustaining access and penetration, and hazard examination and disclosure are the five categories. Depending on the frequency and type of infiltration testing you wish to do, these steps may vary slightly from MSP to MSP;
- Reconnaissance
Accumulate, however, much data about the objective as could be expected from public and private sources to illuminate the assault technique. Sources incorporate web look, area enrollment data recovery, social designing, nonintrusive organization checking, and some of the time even dumpster jumping. This data helps the pen analyzer map out the objective’s assault surface and potential weaknesses. Observation can change with the extension and targets of the pen test, and maybe just about as essential as settling on a telephone decision to stroll through the usefulness of a framework.
2. Scanning
The checking and revelation stage is attempted to discover how the target system will respond to various undertakings at the interference. The passageway analyzer will certainly use mechanized penetration test instruments to check for basic shortcomings. Static examination and dynamic assessment are two kinds of approaches utilized by the penetration analyzer. The static examination inspects an application’s code, attempting to anticipate how it will react to an intrusion. Dynamic assessment sees an application’s code as anything besides a consistent viewpoint on how it performs. Alternate points of view that a pen analyzer will discover join association systems, laborers, and devices, similarly as an association has.
3. Gaining access
When the pen analyzer has acquired a total comprehension of the extension and segments to be tried, they will assault in a recreated and controlled climate. Impersonating a genuine cyberattack, the analyzer may assume responsibility for a gadget to separate information; play out a web application assault, for example, cross-website prearranging or SQL infusion; or play out an actual assault, as referenced beforehand. The objective of this stage is to perceive how far the analyzer can get into an IT climate without recognition. The extent of the task ought to figure out where the constraints of the test should end to ensure PI and other touchy information.
4. Maintaining access
When a pen analyzer has effectively undermined their objective, they should attempt to extend their penetration and keep up their quality to the extent that this would be possible. Once more, the aim is to mirror a true agitator, however much as could be expected. The penetration analyzer in this stage will attempt to grow their authorizations, discover client information, and stay secretive while running their projects further into the IT foundation. For instance, the penetration analyzer may attempt to heighten its advantages to the part of the head. The objective here is to stay undetected in the framework to the extent that this would be possible and attempt to get at the most touchy information (as indicated by the venture extension and objectives).
5. Analysis
The last stage of penetration testing is the evaluation and detailing stage. When the entrance analyzer has been “found,” or the timetable for the undertaking has been finished, it will produce the last report. The report ought to give a synopsis of the testing, subtleties of each progression the pen analyzer took to penetrate frameworks and cycles, subtleties, everything being equal, how they tidied up after the pressure test, and ideas for security fixes. A decent entrance analyzer can likewise decide the worth of the undermined frameworks — i.e., what amount monetary effect could their invasion cost? To do this, an infiltration analyzer utilizes some entrance testing instruments.
What are the top 5 penetration testing techniques?
Pen analyzers utilize at least one of the following strategies or a blend of them much of the time. The choice depends on the objectives and what you consider satisfactory.
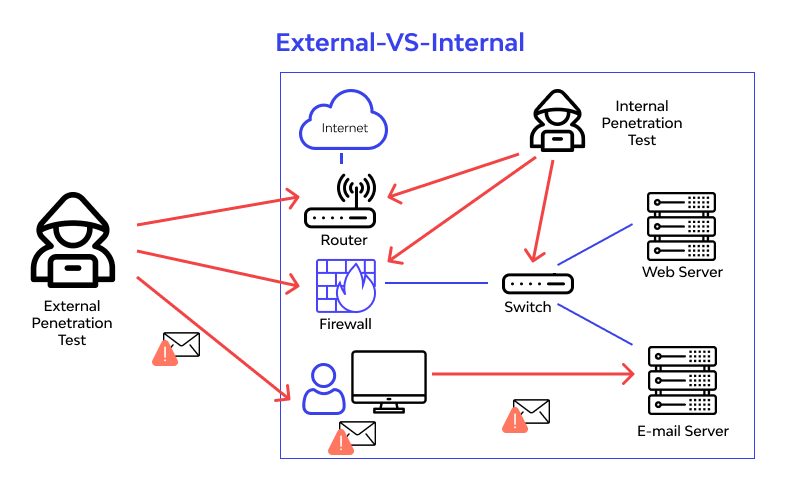
External testing
External testing is carried out from the standpoint of an external attacker, with no immediate system advantages. The analyzers can see workers and gadgets that are visible on the Internet. Web, mail, and FTP workers, as well as firewalls and other devices that may be accidentally exposed to access, are all included. The test incorporates checking passages for open ports, examining administrations, login tries, and filtering for spilled data.
Internal testing
The analyzer provides a client account for internal testing. The analyzer analyzes if the record can move or access assets that it shouldn’t. Besides evaluating how much mischief a maverick worker can do, it estimates what can occur if a pariah takes the accreditations for a record. In frameworks that reliably utilize the rule of most minor advantage, an ordinary record can make just restricted mischief.
Blind testing
Blind tasting is a type of outside testing that simulates the actions of an assailant who has chosen a goal at random. The analysts begin with minimal information, such as the organization’s name or the location. There aren’t many circumstances in which this type of test is valid. The analyzer needs to invest extra energy gathering data in cutting to the chase of an ordinary outside analyzer.
Double-blind testing
The concept of double blind testing is fascinating. The analyzer and the customer association are both operating blindly. A few people on the client side are considering the test, and they are excluding IT, professors. Whatever happens in the IT world is regarded as a severe attack. This sort of test assesses its capacity and security to react to an interruption endeavor. It conveys a few dangers since the tech group may isolate frameworks or limit activities trying to stop the “assault.”
Targeted testing
Designated penetration testing is led by the customer’s IT or security group and the testing group cooperating. Everybody realizes what is happening, and nobody is shocked. This methodology causes at least interruption since the IT group will not confuse a test with a simple assault. It takes into account speedy input in two ways.
What are the main aims of penetration testing?
The principle aim of a penetration test is to distinguish security shortcomings in an organization, machine, or piece of programming. When that is clear, you can kill the weaknesses, or the shortcomings can be decreased before threatening gatherings find them and endeavor them. To make that particular to your circumstance, you need to think about a few inquiries:
- What sorts of dangers would you say you are generally worried about?
- Do you have explicit consistency necessities dependent on the work you do and the data you handle?
- What level of information insurance do you require?
- What dangers are intrinsic in the sort of business you do?
- Determining Your Cyber Security Objectives
Whenever you have evaluated your requirements, you can make an interpretation of them into destinations. You might be basically worried about surveying your specialized guards, for example, web application firewalls (WAFs). There might be a specific application you need to test. You might need to be sure that a particular sort of data (for example, individual or charge card information) has satisfactory assurance.
Every goal suggests a particular security testing situation. Various methodologies will have their objectives and strategies. They will change in system and inclusion.
What are the pros and cons of penetration testing?
With the recurrence and intensity of safety breaks expanding a seemingly endless amount of time after a year, associations have never had a more prominent requirement for permeability into how they can withstand assaults. Guidelines, for example, PCI DSS and HIPAA command periodic pen testing to stay current with their prerequisites. Because of these critical factors, here are a few advantages and disadvantages for this sort of deformity revelation procedure:
Pros of pen testing
Usually, your association has planned its product and system from the beginning fully intent on killing hazardous security blemishes. A pen test gives knowledge into how well you’ve accomplished that point. Pen testing upholds the accompanying security exercises, among others:
- Discovers openings in upstream security confirmation rehearses, like mechanized instruments, setup and coding guidelines, design investigation, and other lighter-weight weakness appraisal exercises
- Finds both known and obscure programming defects and security weaknesses, including little ones that, without help from anyone else, will not raise a lot of concern; however, could cause material damage as a feature of a mind-boggling assault design
- Can assault any framework, imitating how most malevolent programmers would act, reenacting as close as conceivable a certifiable foe

Cons of pen testing
- They have the potential to do a lot of damage if not done correctly.
Tests that aren’t carried out correctly might cause employees to crash, reveal sensitive information, degrade crucial creation data, and a slew of other unfavorable consequences associated with simulating a criminal hack.
- You are needed to confide in the penetration analyzer.
Penetration testing basically implies that you’re welcoming somebody to hack into your frameworks, so you depend on the analyzer not to mishandle their abilities and information.
If you don’t hire someone you can trust to execute the job, your security efforts might backfire spectacularly.
- The results will be misleading if you don’t use realistic test circumstances.
Representatives are probably going to get ready for a test that they know will occur, implying that the association seems, by all accounts, to be more grounded than it really is.
An actual assault will come abruptly and in manners that are inventive and difficult to get ready for.
Originally published at https://www.wallarm.com.