
Credential Stuffing Attack: ❗️ Definition and Protection
Introducing
A new SecureAuth study discovered that 53% of shoppers reuse similar secret phrase for various accounts. When login credentials are presented to programmers, even once, they can be utilized to get to a large number of records, regardless of whether it is an email account, medical coverage, or online store.
What is a credential stuffing?
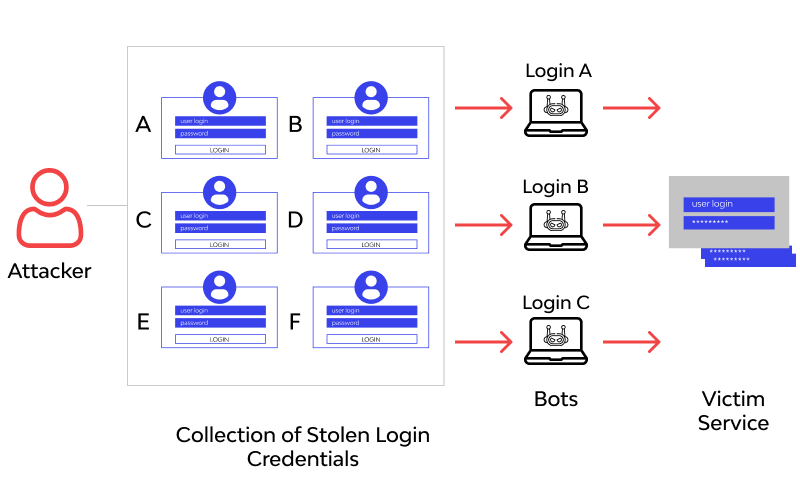
Credential stuffing is a kind of cyberattack where cybercriminals take huge data sets of usernames and passwords, regularly taken through late information breaks, and endeavor to “stuff” the record logins into other web applications utilizing a mechanized cycle. In a Credential stuffing assault, the fraudster utilizes admittance to buyer records to make deceitful buys, lead phishing assaults, and take data, cash, or both. Qualification stuffing is particularly hazardous for customers who utilize the equivalent username and secret word mixes for more than one record, giving a digital criminal admittance to those records at one swipe.
In July of 2020, various data sets containing the taken data of more than 386 million buyers were posted online in a programmer discussion — just for nothing. Cyberthieves took the uncovered information from eighteen organizations, and albeit the Personally Identifiable Information (PII) in every data set fluctuates, it regularly contained names, client names, email locations, and passwords. These days, programmers can unravel hashed passwords, further uncovering a break casualty to account takeover and Credential stuffing assaults. Around the same time, the internet-based shopping for food administration, Instacart, reported an inner examination demonstrated that Instacart “was not compromised or penetrated.” Instead, more than 250,000 clients succumbed to an accreditation stuffing assault.
Signs of a Credential Stuffing Attack
- You can’t get to your record on the grounds that the login data is inaccurate.
- You are advised that your record has been locked due to “an excessive number of login endeavors,” which you have not made.
- You get an email affirmation that your secret phrase has been refreshed without your assent.
- You recognize deceitful charges made utilizing the ledgers connected to specific web-based records.
- You quit getting email notices for accounts in light of the fact that your email was changed to guide warnings to the programmer.
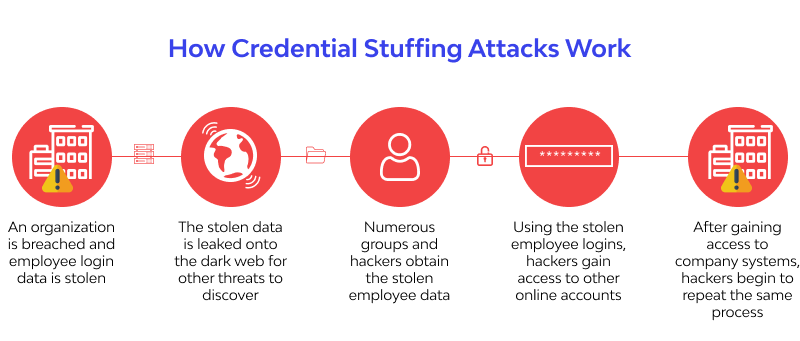
How Credential Stuffing Attacks Work
Here is a common interaction followed by an aggressor in a huge scope qualification stuffing assault. The aggressor:
- Sets up a bot that can naturally sign into numerous client accounts in equal, while faking distinctive IP addresses.
- Runs a computerized interaction to check whenever taken qualifications work on numerous sites. By running the interaction in equal across different destinations, lessening the need to over and over sign into a solitary help.
- Screens for fruitful logins and acquires actually recognizable data, charge cards or other significant information from the compromised accounts.
- Holds account data for later use, for instance, phishing assaults or different exchanges empowered by the compromised administration.
Credential stuffing vs Password spraying
- Brute force attacks attempt to figure certifications with no unique situation, utilizing irregular strings, usually utilized secret word examples or word references of normal expressions
- Brute force assaults succeed if clients pick straightforward, guessable passwords
- Brute power attacks need setting and information from past breaks, thus their login achievement rate is a lot of lower
Credential stuffing is like a brute force attack, yet there are a few significant contrasts:
In an advanced web application with essential safety efforts set up, savage power assaults are probably going to come up short, while accreditation stuffing assaults can succeed. The explanation is that regardless of whether you authorize solid passwords, clients might share that secret word across administrations, prompting a compromise.
How To Prevent Credential Stuffing Attacks
- Use a CAPTCHA
CAPTCHAs also known as Manual human test, which expects clients to play out an activity to demonstrate they are human, can lessen the adequacy of accreditation stuffing. Be that as it may, programmers can undoubtedly sidestep CAPTCHA by utilizing headless programs. Like MFA, CAPTCHA can be joined with different strategies and applied uniquely in explicit situations.
2. Passwordless Authentication
Passwordless confirmation can forestall credential stuffing by and large since it checks a client with something they have (a gadget or another record) or something they are (biometrics) rather than a secret key (something they know). Passwordless likewise makes a superior login experience for clients and sets aside associations time and cash from managing secret key resets.
3. Continuous Authentication
This framework uses factors like biometrics or personal conduct standards to confirm a client’s character continuously (while they utilize an application) rather than a secret key. Thus, certification stuffing assaults (just as various other cyberattacks) are presently not a feasible strategy for cybercriminals to acquire unapproved admittance to a client’s record.
4. Multi-Factor Authentication (MFA)
Expecting clients to confirm with something they have, as well as something they know, is the best protection against certification stuffing. Assailant bots cannot give an actual validation strategy, for example, a cell phone or access token. By and large, it isn’t doable to require multifaceted verification for a whole client base. Provided that this is true, it very well may be joined with different strategies, for instance, MFA can be applied distinctly in mix with gadget fingerprinting.
5. Use IP rate limiting
This security control blocks IP tends to that endeavor logins at a higher rate than a preset edge, for example, more than three every second. This is clearly beyond what a human could enter physically, most likely demonstrating robotized endeavors.
6. IP Blacklisting
Assailants will regularly have a restricted pool of IP addresses, so another compelling safeguard is to obstruct or sandbox IPs that endeavor to sign into numerous records. You can screen the last a few IPs that were utilized to sign into a particular record and contrast them with the speculated terrible IP, to lessen bogus up-sides.
7. Use device and browser fingerprints
You can utilize JavaScript to gather data about client gadgets and make a “unique mark” for every approaching meeting. The unique mark is a mix of boundaries like working framework, language, program, time region, client specialist, and so on On the off chance that similar mix of boundaries signed in a few times in grouping, it is probably going to be a beast power or accreditation stuffing assault.
On the off chance that you utilize a severe finger impression with various boundaries, you can authorize more serious measures, such as forbidding the IP. To catch more assaults, you can utilize a blend of 2–3 normal boundaries, and authorize less serious measures like an impermanent boycott. A typical unique mark blend is an Operating System + Geolocation + Language.
8. Disallow Email Addresses as User IDs
Credential stuffing depends on the reuse of the equivalent usernames or record IDs across administrations. This is considerably more prone to occur if the ID is an email address. By keeping clients from utilizing their email address as a record ID, you significantly lessen the shot at them reusing a similar client/secret key pair on another site.
Credential stuffing depends on the reuse of the equivalent usernames or record IDs across administrations. This is considerably more prone to occur if the ID is an email address. By keeping clients from utilizing their email address as a record ID, you significantly lessen the shot at them reusing a similar client/secret key pair on another site.
How Wallarm can help with a Credential Stuffing Attack
Wallarm’s industry-driving bot the executives arrangement carries out the very accepted procedures above to secure against malevolent bots. Also, it adds a layer of mechanized security rationale, to forestall qualification stuffing, checking, tagging, and numerous other computerized assaults performed by means of noxious bots.
Notwithstanding vindictive bot insurance, Wallarm gives diverse assurance to ensure sites and applications are accessible, effectively available and safe. The Imperva application security arrangement incorporates:
- DDoS Protection
Keep up with uptime in all circumstances. Forestall any kind of DDoS assault, of any size, from forestalling admittance to your site and organization framework.
2. CDN
Improve site execution and lessen data transfer capacity costs with a CDN intended for engineers. Store static assets at the edge while speeding up APIs and dynamic sites.
3. WAF
Cloud-based arrangement licenses authentic traffic and forestalls terrible traffic, defending applications at the edge. Entryway WAF keeps applications and APIs inside your organization safe.
Our API Security Platform secures by guaranteeing just wanted traffic can get to your API endpoint, just as identifying and obstructing exploits of weaknesses. Read the interesting article “How to hack API”
5. Record Takeover Protection
Utilizes a plan-based recognition cycle to distinguish and safeguards against endeavors to assume control over clients’ records for noxious purposes.
6. RASP
Guard your applications from inside against known and zero‑day assaults. Quick and precise insurance with no signature or learning mode.
Originally published at https://www.wallarm.com.