
Explanation of the zero-day attack
What is a zero-day vulnerability?
A zero-day weakness is an obscure security weakness or programming blemish that a danger entertainer can focus with noxious code. The expression “Zero-Day” is utilized in light of the fact that the product merchant was uninformed of their product weakness, and they’ve had “0” days to deal with a security fix or an update to fix the issue.
By and large, when a zero-day weakness is found it gets added to the Common Vulnerabilities and Exposures (CVE) list. CVE is a word reference that gives definitions to openly revealed network safety weaknesses.
The objective of CVE is to make it simpler to share information across independent weakness capacities (instruments, data sets, and administrations) with these definitions. CVE Records are involved an ID number, a depiction, and something like one public reference.
What is a zero-day attack?
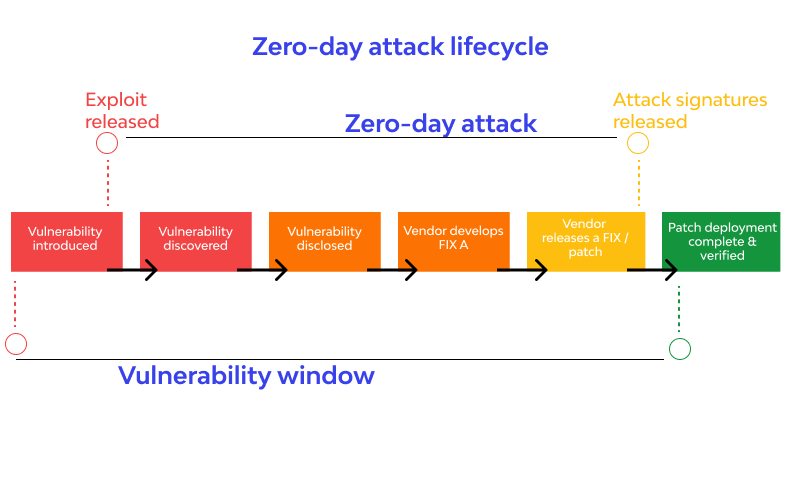
A zero-day assault happens when somebody abuses a product weakness that is obscure to engineers or the general population at the hour of the assault. It’s known as a “zero-day” assault since engineers had zero days to fix the imperfection before the weakness was misused or spread the word about for general society.
Fixing zero-day weaknesses can consume a large chunk of the day. Microsoft and other significant programming engineers carry out patches just about one time per month. The less regularly you update your product (or, maybe, the less every now and again refreshes are made accessible for basic programming), the more weak you are to security penetrates.
What is a zero-day exploit?
A zero-day weakness, at its center, is a blemish. It is an obscure adventure in the wild that uncovered a weakness in programming or equipment and can make convoluted issues a long time before anybody understands something isn’t right. Truth be told, a zero-day misuse leaves absolutely no chance for location from the outset.
How do zero-day attacks work and why are they dangerous?
Programming frequently has security weaknesses that programmers can endeavor to cause ruin. Programming designers are continually paying special mind to weaknesses to “fix” — that is, foster an answer that they discharge in another update.
Be that as it may, some of the time programmers or noxious entertainers recognize the weakness before the product engineers do. While the weakness is as yet open, aggressors can compose and carry out a code to exploit it. This is known as endeavor code.
The endeavor code might prompt the product clients being deceived — for instance, through data fraud or different types of cybercrime. When assailants recognize a zero-day weakness, they need a method of arriving at the weak framework. They frequently do this through a socially designed email — i.e., an email or other message that is apparently from a known or authentic reporter however is really from an aggressor. The message attempts to persuade a client to play out an activity like opening a document or visiting a vindictive site. Doing as such downloads the aggressor’s malware, which invades the client’s documents and takes secret information.
At the point when a weakness becomes known, the designers attempt to fix it to stop the assault. In any case, security weaknesses are frequently not found straight away. It can at times require days, weeks, or even a long time before designers distinguish the weakness that prompted the assault. And surprisingly once a zero-day fix is delivered, not all clients rush to execute it. Lately, programmers have been quicker at misusing weaknesses before long revelation.
Adventures can be sold on the dull web for huge amounts of cash. When an adventure is found and fixed, it’s as of now not alluded to as a zero-day danger. Zero-day assaults are particularly hazardous in light of the fact that the solitary individuals who think about them are simply the assailants. Whenever they have invaded an organization, hoodlums can either assault quickly or sit and trust that the most favorable time will do as such.
Zero-day assaults are a significant danger in light of the fact that there’s no “fix” until a fix is delivered, and this can take some time. You could be utilizing programming that probably won’t be fixed for quite a long time or even months. Furthermore, numerous individuals are delayed to refresh their product even after a fix is delivered.
During this time, assailants are tenacious as they attempt to focus however many individuals as could be allowed before a fix carries out. This can put your own information at a much higher danger than ordinary.
Limit your security hazards by continually refreshing your product when patches are free. What’s more, don’t depend on patches alone — with a solid antivirus from a supplier you trust, you’ll get every minute of every day assurance against malware, hacking, and a wide scope of other online dangers.
How to detect a zero-day attack?
The more drawn out a zero-day assault stays undetected, the more extended the programmer can keep assaulting, and zero-day misuses are frequently difficult to recognize. Engineers pay special mind to the accompanying notice indications of a zero-day abuse.
icon_01Strange programming conduct. Programming merchants dissect how projects reacted to past endeavors and attempt to recognize comparable conduct in different projects. Examples arise in hack endeavors, similar to a prominent series of abnormal orders paving the way to code execution. In case these are recognized, it may mean an assault is occurring.
icon_02Statistics of perilous figuring. At the point when information moves at a similar speed or volume as it did during a past assault, something may not be right. Assaults are bound to happen the day after a significant security update is delivered, and this is a variable that plays into this method of location.
icon_03Signatures of past security patches. Designers can take a gander at the marks for recently abused weaknesses. They’re similar to unique finger impression tests — qualities will undoubtedly show up again somewhere else. Engineers would then be able to examine for these insufficiencies and eliminate them.
Every one of the above methods has blindspots, however, which is the reason they’re frequently utilized in show.
Since assaults can come through so a wide range of covered up roads, an expansive protection may be the solitary thing holding an assault back from focusing on and getting to you. Avast Free Antivirus screens your gadget progressively to recognize any indications of an assault, in a flash impeding programmers from introducing malware on your PC or telephone.
Zero-day attack protection
Since zero-day assaults occur abruptly, the best zero-day assault avoidance technique incorporates these following precaution measures:
Keep all product and working frameworks forward-thinking. This is on the grounds that the merchants incorporate security patches to cover recently distinguished weaknesses in new deliveries. Staying up with the latest guarantees you are safer.
• Utilize just fundamental applications. The more programming you have, the more potential weaknesses you have. You can decrease the danger to your organization by utilizing just the applications you need.
• Utilize a firewall. A firewall assumes a fundamental part in ensuring your framework against zero-day dangers. You can guarantee greatest assurance by arranging it to permit just important exchanges.
• Inside associations, instruct clients. Many zero-day assaults exploit human mistake. Showing representatives and clients great wellbeing and security propensities will assist with guarding them on the web and shield associations from zero-day misuses and other computerized dangers.
• Utilize a thorough antivirus programming solution.
By recognizing and obstructing malware and different dangers, a top-level enemy of malware apparatus can help guard against zero-day assaults. Avast Free Antivirus utilizes a heuristic assurance model, which implies that it examines for normal assault examples or marks to distinguish possible dangers.

Examples of zero-day attacks in the world
Stuxnet is a PC worm that utilizes a rootkit, and it managed an extensive hit to Iran’s atomic program in 2009 by abusing weaknesses in a piece of programming that a significant number of us utilize each day: Microsoft Windows. Believe it or not — the working framework that permits us to send email and peruse the web all day was controlled to obliterate atomic axes and cause international distress. In the event that that sounds wild, this is on the grounds that it is.
Sony Pictures was the objective of a zero-day assault in 2014 when they experienced a monstrous break of unreleased substance and delicate individual data. That, however whole corporate frameworks were eradicated, bringing about huge number of dollars in harms.
Those assaults don’t concern us, correct? Lamentably, the zero-day abuse list isn’t restricted to corporate and government targets. How about we take a gander at a zero-day assault model that straightforwardly influenced normal individuals like you and me.
In 2017, Microsoft Word was hit with a zero-day abuse that compromised individual ledgers. The casualties were regular individuals who accidentally opened a malignant Word report. The report showed a “heap distant substance” brief, showing them a spring up window that mentioned outer access from another program.
At the point when a casualty clicked “yes,” the report introduced a hazardous piece of malware called Dridex on their PC. When this occurred, Dridex could tell when the casualty was signing into their financial balance and catch their login certifications.
It’s not all awful information — the gathering with the most ability to forestall these assaults is you. As we found in the Microsoft Word assault, casualties expected to really make a move (click a catch) before the contaminated report could introduce the malware onto their PC.
Originally published at https://www.wallarm.com.