
Apple Safari automatically installs Dashboard widgets
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.005 Low
EPSS
Percentile
77.0%
Overview
Apple Safari on Mac OS X Tiger automatically installs Dashboard widgets without user intervention or notice.
Description
Dashboard
Dashboard is a new feature introduced in Apple Mac OS X Tiger 10.4. Dashboard is a collection of applications called “widgets.” The system-installed widgets are located in /Library/Widgets and user-installed widgets are located in ~/Library/Widgets.
Widgets
A widget is an application that is created using a combination of HTML, CSS, and JavaScript. Although the content of a widget is similar to a web page, a widget that executes within the context of Dashboard has additional privileges that are not available within a web browser. For example, a Dashboard widget can make system calls via widget.system() or execute a plug-in that contains native OS X code.
Execution warning
The first time a user runs a widget that requests certain privileges, such as those required to make system calls, a warning dialog is displayed. Note that this dialog is displayed for all widgets except those in /Library/Widgets (system-installed widgets) and ~/Library/Widgets (user-installed widgets). For example, if a user attempts to run a widget called “Stickies” for the first time, and that widget requests certain privileges, the following dialog will be displayed:
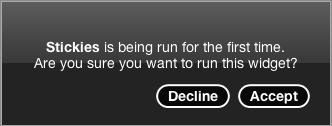
The problem
Apple Safari automatically opens certain files by default, including widgets. When Safari opens a widget it actually performs an installation of the widget. The installation of a widget involves extracting the widget archive and copying the contents to ~/Library/Widgets. Because Safari installs the widget to the user’s widget directory, the execution warning dialog is not presented when the user runs the widget for the first time.
Impact
An attacker may be able to install arbitrary code on a vulnerable system. Since OS X executes user-installed widgets over system-installed widgets with the same bundle identifier (VU#983429), a user may be more likely to unknowingly execute the code.
Solution
Upgrade or patch
With the Mac OS X 10.4.1 Update, Safari will prompt the user before installing a widget, thus preventing automatic widget installation. Please note that the dialog used in this prompt is somwhat misleading. The dialog asks “Are you sure you want to download the application ‘<widgetname>’?” For example:

By the time the dialog is displayed, Safari has already downloaded, extracted, and examined the contents of the widget archive. If the user clicks “Download,” the widget is not “downloaded” in the expected sense. It is installed into the user’s widget directory.
Disable “Open ‘safe’ files after downloading”
By default, Safari will open “safe” files after downloading them. This includes movies, pictures, sounds, documents, disk images, and widgets. By disabling this option, Safari will not automatically install widgets. This appears to be a more effective solution than upgrading to 10.4.1 by itself. By not automatically opening files, Safari will not automatically execute other software to handle downloaded files. Other software may contain vulnerabilities, and some “safe” files may contain code, place content in a known location, or otherwise contribute to an attack. To disable this option, select “Preferences” from the Safari menu and uncheck the option “Open ‘safe’ files after downloading,” as specified in the Securing Your Web Browser document.
Vendor Information
775661
Filter by status: All Affected Not Affected Unknown
Filter by content: __ Additional information available
__ Sort by: Status Alphabetical
Expand all
Javascript is disabled. Click here to view vendors.
Apple Computer, Inc. __ Affected
Notified: June 08, 2005 Updated: June 08, 2005
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
Addendum
US-CERT has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23775661 Feedback>).
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- <http://www.macworld.com/news/2005/05/09/dashboard/>
- http://www.macworld.co.uk/news/index.cfm?home&NewsID=11531
- <http://www1.cs.columbia.edu/~aaron/files/widgets/>
- <http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/index.html>
- [[<a href=“http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101”>http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/ Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101</a>]](<[<a href=“http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101”>http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/ Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101</a>]>)
- <http://www.apple.com/macosx/features/dashboard/>
- <http://www.appleinsider.com/article.php?id=1073>
- <http://securitytracker.com/alerts/2005/May/1014012.html>
- <http://www.securityfocus.com/bid/13694>
- <http://docs.info.apple.com/article.html?artnum=301630>
Acknowledgements
This vulnerability was publicly reported by stephan.com.
This document was written by Will Dormann.
Other Information
| CVE IDs: | CVE-2005-1474 |
|---|---|
| Severity Metric: | 17.06 Date Public: |
References
developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/index.html
docs.info.apple.com/article.html?artnum=301630
securitytracker.com/alerts/2005/May/1014012.html
www.apple.com/macosx/features/dashboard/
www.appleinsider.com/article.php?id=1073
www.macworld.co.uk/news/index.cfm?home&NewsID=11531
www.macworld.com/news/2005/05/09/dashboard/
www.securityfocus.com/bid/13694
www1.cs.columbia.edu/~aaron/files/widgets/
[<a href="developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101">http://developer.apple.com/documentation/AppleApplications/Conceptual/Dashboard_Tutorial/ Security/chapter_10_section_1.html#//apple_ref/doc/uid/TP40001340-CH210-TPXREF101</a>]
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.005 Low
EPSS
Percentile
77.0%