
SISCO OSI stack fails to properly validate packets
CVSS2
Attack Vector
NETWORK
Attack Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:N/I:N/A:C
EPSS
Percentile
89.6%
Overview
A vulnerability exists in the SISCO OSI stack for Windows. If successfully exploited, an attacker could cause a denial-of-service condition.
Description
Inter-control Center Communications Protocol (ICCP)
The Inter-control Center Communications Protocol (ICCP) is a protocol that is used to communicate data between control centers that operate SCADA networks.
Manufacturing Message Specification (MMS)
According to SISCO,
MMS (Manufacturing Message Specification) is an internationally standardized messaging system for exchanging real-time data and supervisory control information between networked devices and/or computer applications in a manner that is independent of: 1) the application function being performed or 2) the developer of the device or application. MMS is an international standard (ISO 9506) that is developed and maintained by Technical Committee Number 184 (TC184), Industrial Automation, of the International Organization for Standardization (ISO).
ISO Transport Service over TCP (TPKT, RFC 1006)
RFC 1006 specifies how to run the OSI transport protocol on top of TCP/IP. In the layered protocol model, RFC 1006 is situated between the TCP and OSI transport layers.
The Problem
The SISCO OSI stack for Windows fails to properly handle malformed packets. A remote, unauthenticated attacker may be able to exploit this vulnerability to cause a denial-of-service condition. The SISCO OSI stack for Windows is used in the MMS-EASE, ICCP Toolkit for MMS-EASE, AX-S4 MMS, and AX-S4 ICCP products.
Impact
A remote, unauthenticated attacker may be able to cause a denial-of-service condition.
Solution
Upgrade
SISCO has addressed this vulnerability. Contact them for a list of unaffected or patched software. According to SISCO, the following versions of software are affected:
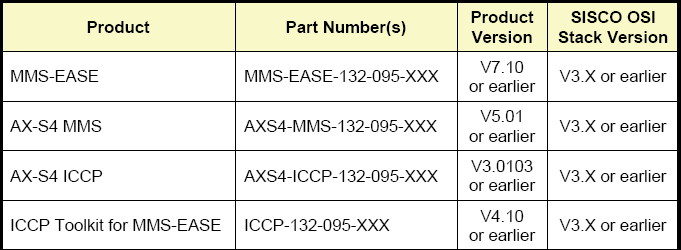
SISCO Vulnerability Announcement
Restrict Access
Restrict remote access to only trusted hosts by using firewalls or only connecting them to private networks.
Vendor Information
468798
Filter by status: All Affected Not Affected Unknown
Filter by content: __ Additional information available
__ Sort by: Status Alphabetical
Expand all
Javascript is disabled. Click here to view vendors.
SISCO - Systems Integration Specialists Company, Inc. __ Affected
Notified: June 24, 2006 Updated: September 18, 2006
Status
Affected
Vendor Statement
Anyone with questions regarding SISCO’s products should contact SISCO directly at: <http://www.sisconet.com/contact.htm>.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- <http://www.sisconet.com/downloads/NESSUS_Vulnerability_Announcement.pdf>
- <http://www.faqs.org/rfcs/rfc1006.html>
- <http://www.sisconet.com/downloads/mmsovrlg.pdf>
Acknowledgements
This vulnerability was reported by SISCO.
This document was written by Ryan Giobbi, based on information from SISCO.
Other Information
| CVE IDs: | CVE-2005-4812 |
|---|---|
| Severity Metric: | 0.92 Date Public: |
CVSS2
Attack Vector
NETWORK
Attack Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:N/I:N/A:C
EPSS
Percentile
89.6%