
TCP/IP implementations handle unusual flag combinations inconsistently
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:N/I:N/A:P
0.004 Low
EPSS
Percentile
73.4%
Overview
Various vendors’ TCP/IP implementations handle packets containing unusual flag combinations in different ways, which may lead to a violation of implicit or explicit security policies.
Description
Background on TCP/IP Connection Semantics
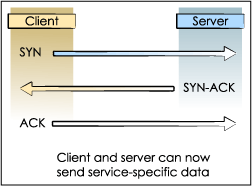
To establish a TCP connection, a client and server must participate in a three-way handshake (as outlined in RFC793 - “Transmission Control Protocol”):
1. The client system sends a packet with the SYN flag set to the server.
2. The server acknowledges the client by sending a packet back with the SYN and ACK flags set.
3. The client completes the connection by sending a packet with the ACK flag set.
The connection between the client and the server is then open, and the service-specific data can be exchanged between the client and the server. The following diagram depicts the connection setup sequence:
A firewall inserted between a client and a server can be used to manage the connection setup and subsequent traffic flow between the two systems. In general, firewalls are of two types: packet-filtering firewalls, and application-level firewalls. Packet filters look at the source, destination, types, and options associated with the packet, while an application level firewall can “look inside” the packet to examine application-specific attributes. This document is concerned primarily with packet-filtering firewalls.
Section 3.4 (Establishing a connection) of RFC793 describes the three-way handshake as the standard procedure used to establish a connection. Firewalls will typically not allow this process between hosts that are not permitted to communicate with each other. For example, if an attacker sends a packet with the SYN bit set to a victim server, the firewall will not relay this packet to the victim because the firewall’s rules only allow packets with the SYN bit set to come from certain hosts. As a result, the three-way handshake will not be completed, and the attacker will not be able to establish a connection with a host behind the firewall. This method of filtering SYN packets is typically the method used by packet-filtering firewalls to prevent certain hosts from “getting past the firewall.”
How the Attacker Can Bypass the Firewall
An attacker is free to set whatever flags he chooses to set on any packet. RFC793 defines the meaning of most flag combinations, but it does not address all scenarios in which odd or unexpected flag combinations may be encountered. The method for handling the packet is largely left up to the TCP implementer, and each implementation handles flag combinations differently. For example, T/TCP (RFC1644) recognizes a packet with both the SYN and FIN flags set as being valid. Some implementations are even more liberal in what they accept and choose to treat any packet with the SYN flag set (regardless of what other flags are set or unset) as the opening in the three-way handshake. Other implementations are more conservative and drop packets with unexpected combinations of flags.
This ambiguity results in a vulnerability in certain situations. Suppose you have a firewall that passes packets if the RST flag is set, regardless of the state of the SYN flag. Furthermore, suppose you have a host that accepts a SYN flag as the opening of the three-way handshake even if the RST flag is set. An intruder can now send a packet with the SYN and RST flags set and establish a connection with the host behind the firewall in violation of the expected behavior.
A change introduced in the Linux Kernel (version 2.4.20) ensures that at least packets with both the SYN and RST flags set are discarded. This change was made within the function tcp_input.c.
Finally, research has indicated that multiple TCP implementations will allow a TCP session to be established with hosts by setting certain combinations of flags in an initial packet. The researchers go on to indicate that, “Other OSes than those tested above are expected to behave in a similar manner after obtaining such a discouraging result…”
Note that while the “detailed” research implies it is incorrect for a TCP implementation to accept a SYN with certain other bits set, it is actually a perfectly legal but rarely implemented behavior. Unfortunately, many firewalls either do not specify firewall rules that account for this (a documentation or user bug) or can not specify such firewall rules (an firewall implementation bug).
Impact
The impact of this vulnerability is that an attacker may be able to establish connections with hosts behind firewalls in violation of implied security policies. As a result, an attacker can send data to hosts and services that he ordinarily cannot reach. An intruder could also leverage this flaw to exploit a vulnerability in passive software listening promiscuously on the inside of the firewall (e.g., vulnerability in tcpdump or some similar vulnerability). Note that the specific kinds of packets that may bypass a firewall are highly dependent on the implementation of the firewall.
Solution
Apply a vendor patch. If a vendor patch is not available for your TCP implementation (and even if one is), you may wish to:
* create filtering rules designed to drop and/or reject packets with certain combinations of bits set in initial synchronization packets
* not use routable IP space except inside your DMZ
* if possible, switch to stateful filtering; however, you shouldn't do this unless you know your network traffic well enough to be sure that it has the required properties (symmetric routing, not too many flows, not too much idle time per flow)
Vendor Information
464113
Filter by status: All Affected Not Affected Unknown
Filter by content: __ Additional information available
__ Sort by: Status Alphabetical
Expand all
Javascript is disabled. Click here to view vendors.
The SCO Group (SCO Linux) __ Affected
Notified: October 24, 2002 Updated: May 01, 2003
Statement Date: April 30, 2003
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
Please see <ftp://ftp.sco.com/pub/security/OpenLinux/CSSA-2003-019.0.txt>.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Apple Computer, Inc. __ Not Affected
Notified: October 24, 2002 Updated: October 28, 2002
Statement Date: October 23, 2002
Status
Not Affected
Vendor Statement
The built-in firewall on Mac OS X and Mac OS X Server does not contain the vulnerabilty described in this report. Customers who have installed other firewall products should check with their third-party vendor for information.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Check Point __ Not Affected
Notified: October 24, 2002 Updated: October 25, 2002
Statement Date: October 24, 2002
Status
Not Affected
Vendor Statement
Check Point VPN-1/FireWall-1 products are engineered to provide the highest levels of security. VPN-1/FireWall-1 will automatically drop any invalid packet flag combinations including, but not limited to, those described in CERT VU# 464113. In addition, the Check Point SmartDefense product will provide additional logging and alerting if this type of attack is attempted.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Clavister __ Not Affected
Updated: April 01, 2003
Statement Date: March 21, 2003
Status
Not Affected
Vendor Statement
Clavister Firewall: Not vulnerable.
Clavister Firewall only allows plain SYN packets to create new states, and, as such, also protects hosts behind it.
In addition, thorough packet scrubbing is performed. The default settings for packets where the SYN flag is set are:
SYN+URG: Drop and log the packet
SYN+RST: Drop and log the packet
SYN+FIN: Drop and log the packet
SYN+PSH: Strip the PSH flag and log
Although SYN+PSH is very uncommon, some TCP stacks have been observed to use them. Early versions of MacTCP is one such stack.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Cray Inc. __ Not Affected
Notified: October 24, 2002 Updated: October 30, 2002
Statement Date: October 30, 2002
Status
Not Affected
Vendor Statement
Cray, Inc. is not vulnerable as we provide no software that performs this type of function.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Finjan Software __ Not Affected
Updated: October 25, 2002
Statement Date: October 24, 2002
Status
Not Affected
Vendor Statement
This issue isn’t relevant to any of our products.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Foundry Networks Inc. __ Not Affected
Updated: April 01, 2003
Statement Date: March 27, 2003
Status
Not Affected
Vendor Statement
Foundry Networks does not produce stateful or packet filtering firewalls, but do support high speed packet filtering ACLs on its products. An ACL with the “established” operator turned on will filter on all TCP packets with the ACK (Acknowledgment) or RST (Reset) bits set to “1” (on) in the control filed of the TCP packet header. Current versions of shipping software will not permit unexpected combinations of SYN flags.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Fujitsu __ Not Affected
Notified: October 24, 2002 Updated: December 03, 2002
Statement Date: December 03, 2002
Status
Not Affected
Vendor Statement
Fujitsu’s UXP/V OS is not vulnerable, because the relevant function is not supported under UXP/V.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Funk Software __ Not Affected
Updated: October 25, 2002
Statement Date: October 24, 2002
Status
Not Affected
Vendor Statement
While we are a vendor of a variety of products that involved network security, none of the products currently include firewall functionality that would be susceptible to the type of attack described below. We will keep this notification on file to ensure that any new products we might develop in the future are not susceptible to this attack.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Hewlett-Packard Company __ Not Affected
Notified: October 24, 2002 Updated: May 10, 2005
Statement Date: March 17, 2003
Status
Not Affected
Vendor Statement
SOURCE:
Hewlett-Packard Company
HP Services
Software Security Response Team
x-ref:SSRT2391
As further information becomes available HP will provide notice of the availability of any necessary patches through standard security bulletin announcements and be available from your normal HP Services support channel.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
IBM Corporation __ Not Affected
Notified: October 24, 2002 Updated: April 01, 2003
Statement Date: April 01, 2003
Status
Not Affected
Vendor Statement
The IBM AIX operating system is not vulnerable to the issues discussed in CERT Vulnerability Note VU#464113.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Ingrian Networks, Inc. __ Not Affected
Updated: March 18, 2003
Statement Date: March 17, 2003
Status
Not Affected
Vendor Statement
Ingrian Networks products are application-level proxies. The type of attack detailed in VU#464113 cannot be used to bypass their security.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Lotus Software __ Not Affected
Notified: October 24, 2002 Updated: March 14, 2003
Statement Date: March 13, 2003
Status
Not Affected
Vendor Statement
Lotus does not ship firewalls or packet filters, so there is no vulnerability due to TCP/IP connection open semantics.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Microsoft Corporation __ Not Affected
Notified: October 24, 2002 Updated: October 29, 2002
Statement Date: October 28, 2002
Status
Not Affected
Vendor Statement
Microsoft has thoroughly investigated this issue, and found that Microsoft’s ISA Server firewall product is not affected by the scenario described in this report.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
NetScreen __ Not Affected
Updated: March 14, 2003
Statement Date: March 13, 2003
Status
Not Affected
Vendor Statement
NetScreen is not vulnerable to this issue.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
OpenBSD __ Not Affected
Notified: October 24, 2002 Updated: March 14, 2003
Statement Date: October 25, 2002
Status
Not Affected
Vendor Statement
The stateful packet filter (pf) that ships with OpenBSD 3.0 and later is not vulnerable to the attacks described.
pf uses real stateful TCP filtering and keeps track of established connections using a state table. It doesn’t use any TCP flags to associate a packet with an established connection, instead it uses source and destination addresses and ports to find matching state entries (and verifies sequence numbers against narrow windows).
Filter rules specify which packets create state table entries, and the required TCP flags can be specified freely. It’s possible to create state only for plain SYN packets or allow any combination of other TCP flags to do so.
In no case any packet with any combination of TCP flags can bypass the policy defined in the rule set (due to the packet filter wrongly assuming it is part of an established connection), as only explicit rules can create state tables entries.
To prevent SYN+RST packets from creating state, the option ‘flags S/SAR’ can be used (meaning ‘SYN must be set, ACK and RST must not be set’). But even the common ‘flags S/SA’ will only create state when the remaining rule matches, allowing SYN+RST packets to establish only connections which are already allowed for plain SYNs.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Sun Microsystems, Inc. __ Not Affected
Notified: October 24, 2002 Updated: November 11, 2004
Status
Not Affected
Vendor Statement
+ Solaris is not vulnerable to this issue.
+ The SunScreen Firewall products only pass packets with the SYN bit set to a host that it has been configured to allow a connection to. Setting extra bits in a packet will not change this behaviour. In addition, the SunScreen TCP state engine will check that the following conform to RFC 793 before passing them:
- Packets in the three-way handshake.
- Packets with FIN bit set.
- Packets with RST bit set.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Trend Micro __ Not Affected
Notified: October 24, 2002 Updated: October 29, 2002
Statement Date: October 28, 2002
Status
Not Affected
Vendor Statement
TrendMicro has been aware for some time of the potential problems that this TCP-Flag combination issue contains. TrendMicro has two products which make use of the network-layer, where these flags are used to identify the current session status. These products are GateLock <<http://www.gatelockglobal.com>> and PC-cillin <<http://www.pccillin.com>>. Neither product is affected.
PC-cillin is an antivirus and antihacker security solution for computers and PDAs. It includes a personal firewall. This firewall does not pass through undefined SYN,FIN combination packets to the protected local services/ports.
TrendMicro GateLock is an all-in-one, plug-and-play Internet appliance designed for home and SOHO networks that uses a broadband connection. This appliance includes a stateful inspection firewall which does not allow the establishment of a session to the protected hosts in case of a SYN,FIN combination packet.
All other TrendMicro gateway products are categorized as application-level firewalls. These products running in the application-layer. The underlaying OS is responsible for the three-way handshake.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Xerox Corporation __ Not Affected
Notified: October 24, 2002 Updated: May 30, 2003
Statement Date: December 10, 2002
Status
Not Affected
Vendor Statement
A response to this vulnerability is available from our web site:
<http://www.xerox.com/security>.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
3Com Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
AT&T Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Alcatel Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Avaya Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Berkeley Software Design, Inc. Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Cisco Systems, Inc. __ Unknown
Notified: October 24, 2002 Updated: July 28, 2004
Statement Date: January 22, 2004
Status
Unknown
Vendor Statement
A new feature has been added to Cisco IOS starting from the IOS release 12.3(4)T. This feature provides a flexible mechanism for filtering on TCP flags. The new syntax can be found at the following URL:
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Cistron Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Command Software Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Computer Associates Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Covalent Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
D-Link Systems Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Data Fellows Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Data General Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Debian Linux Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Engarde Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
F-Secure Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
F5 Networks, Inc. Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
FreeBSD, Inc. Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Intel Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Interlink Networks Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Juniper Networks, Inc. Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Lachman Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Lucent Technologies Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Macromedia Inc. Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Mandriva, Inc. Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Mandriva, Inc. Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
MontaVista Software, Inc. Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Motorola Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Multinet Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
NEC Corporation Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
NetBSD Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Network Appliance Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Nortel Networks, Inc. Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Openwall GNU/*/Linux Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Oracle Corporation Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
RADIUSClient Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Red Hat, Inc. Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Riverstone Networks Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
SGI __ Unknown
Notified: October 24, 2002 Updated: March 14, 2003
Statement Date: March 13, 2003
Status
Unknown
Vendor Statement
SGI acknowledges the vulnerabilities reported by CERT VU#464113 and is currently investigating. This is being tracked as SGI Bug# 871383. No further information is available at this time.
For the protection of all our customers, SGI does not disclose, discuss or confirm vulnerabilities until a full investigation has occurred and any necessary patch(es) or release streams are available for all vulnerable and supported IRIX operating systems. Until SGI has more definitive information to provide, customers are encouraged to assume all security vulnerabilities as exploitable and take appropriate steps according to local site security policies and requirements. As further information becomes available, additional advisories will be issued via the normal SGI security information distribution methods including the wiretap mailing list on <http://www.sgi.com/support/security/>.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
SUSE Linux Unknown
Notified: October 24, 2002 Updated: October 28, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Sequent Computer Systems, Inc. Unknown
Notified: October 24, 2002 Updated: October 25, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Sony Corporation Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Sophos Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Symantec Corporation Unknown
Notified: October 24, 2002 Updated: April 01, 2003
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
The SCO Group (SCO Unix) Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Unisphere Networks Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Unisys Unknown
Notified: October 24, 2002 Updated: October 24, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Wind River Systems, Inc. Unknown
Notified: October 24, 2002 Updated: October 27, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
Wirex Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
XTRADIUS Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
YARD RADIUS Unknown
Notified: October 24, 2002 Updated: October 31, 2002
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Addendum
The CERT/CC has no additional comments at this time.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23464113 Feedback>).
View all 70 vendors __View less vendors __
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- <http://hypermail.idiosynkrasia.net/linux-kernel/archived/2002/week46/1137.html>
- <http://www.securityfocus.com/archive/1/296122/2002-10-19/2002-10-25/2>
- <http://www.securityfocus.com/archive/1/296558/2002-10-19/2002-10-25/1>
- <http://www.uwsg.iu.edu/hypermail/linux/kernel/0210.3/0365.html>
- <http://www.cis.ohio-state.edu/cgi-bin/rfc/rfc1644.html>
- <http://www.packetfactory.net/projects/nemesis/>
- <http://www.ibiblio.org/pub/docs/rfc/rfc793.txt>
- <http://www.kb.cert.org/vuls/id/776781>
- <http://www.kohala.com/start/ttcp.html>
Acknowledgements
This issue was initially described by Paul Starzetz in a mail message sent to the Bugtraq mailing list. We also thank Florian Weimer, Avi Freedman, Alan Cox, and David Waitzman for their invaluable feedback on this subject.
This document was written by Ian A Finlay.
Other Information
| CVE IDs: | CVE-2002-2438 |
|---|---|
| Severity Metric: | 32.25 Date Public: |
References
hypermail.idiosynkrasia.net/linux-kernel/archived/2002/week46/1137.html
www.cis.ohio-state.edu/cgi-bin/rfc/rfc1644.html
www.ibiblio.org/pub/docs/rfc/rfc793.txt
www.kb.cert.org/vuls/id/776781
www.kohala.com/start/ttcp.html
www.packetfactory.net/projects/nemesis/
www.securityfocus.com/archive/1/296122/2002-10-19/2002-10-25/2
www.securityfocus.com/archive/1/296558/2002-10-19/2002-10-25/1
www.uwsg.iu.edu/hypermail/linux/kernel/0210.3/0365.html
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:N/I:N/A:P
0.004 Low
EPSS
Percentile
73.4%