Microsoft Windows Metafile handler SETABORTPROC GDI Escape vulnerability
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.974 High
EPSS
Percentile
99.9%
Overview
Microsoft Windows is vulnerable to remote code execution via an error in handling files using the Windows Metafile image format. Exploit code has been publicly posted and used to successfully attack fully-patched Windows XP SP2 systems. However, other versions of the Windows operating system also may be at risk.
Description
Windows Graphic Display Interface (GDI)
Windows GDI is an interface that “enables applications to use graphics and formatted text on both the video display and the printer.” GDI functions can be used to draw lines, text, curves, and other graphical elements.
GDI Escape function
The GDI Escape function allows an application to access capabilities of a device that are not directly available through GDI. For example, a print job can be cancelled via a GDI Escape call.
Windows Metafile (WMF)
Microsoft Windows Metafile (WMF) format images are graphical files that can contain both vector and bitmap-based picture information. WMF files contain a sequence of GDI function calls. The image is created by executing the GDI functions.
The problem
Certain GDI functions can have unexpected security implications. According to the MSDN document Security Considerations: GDI:
Bitmaps, metafiles, and fonts are complex structures that could become corrupted. It is good practice to try to ensure that these items are uncorrupted and from a trustworthy source.Current public exploits use the SETABORTPROC GDI Escape function to execute arbitrary code when viewed. The SETABORTPROC GDI Escape is obsolete, and is provided only for compatibility with 16-bit versions of Windows. Other GDI functions, in particular the GDI Escape functions, may also have similar vulnerabilities.
The public exploits currently use the Windows Picture and Fax Viewer (SHIMGVW.DLL) as an attack vector. However, please note that disabling the Windows Picture and Fax Viewer will not eliminate this vulnerability. Limited testing has shown that any application that makes the SetWinMetaFileBits GDI function call may be used to trigger the SETABORTPROC GDI Escape on Windows NT, Windows 2000, Windows XP, and Windows Server 2003. The GDI implementation of Windows 98 and Windows Me appears to be different in that the PlayMetaFile GDI function seems to trigger the SETABORTPROC GDI Escape.
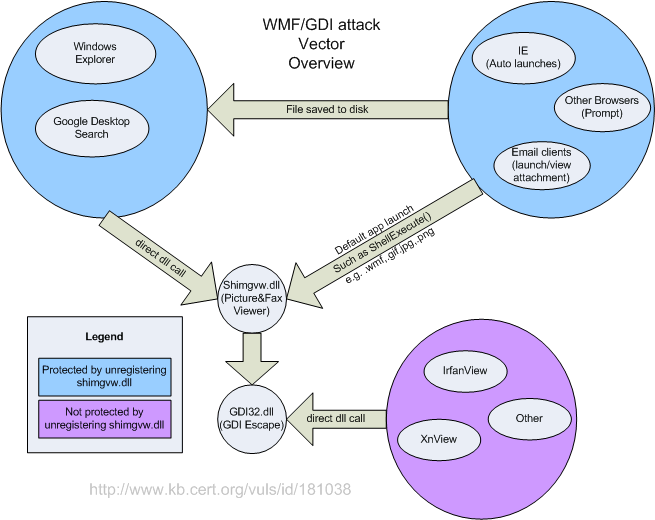
Any application that can open a file with the associated program for that file type, such as one that uses ShellExecute, can be used as an attack vector. Most email clients can be used as an attack vector for this vulnerability in this way. Windows Picture and Fax Viewer is the application that is associated with WMF and other graphic files by default on Windows XP and Windows Server 2003.
Internet Explorer is a common attack vector for this vulnerability because, in its default configuration, it can automatically launch the Windows Picture and Fax Viewer as the result of viewing a web page. Google Desktop Search (GDS) can also trigger the vulnerability if a malicious WMF file is placed in a location that is indexed. Other content indexing software may also be vulnerable.
The following diagram illustrates several attack vectors for this vulnerability:
Impact
A remote, unauthenticated attacker may be able to execute arbitrary code if the user is persuaded to view a specially crafted Windows Metafile.
Solution
Apply a patch from your vendor
Microsoft addresses this issue with the updates listed in Microsoft Security Bulletin MS06-001. This update disables support for SETABORTPROC in a WMF image.
Note**:** If Windows Picture and Fax Viewer was un-registered as a workaround, it can be re-registered after installation of the MS06-001 update with the following command:
regsvr32 ``%windir%\system32\shimgvw.dll
If an unofficial hotfix was installed as a workaround, it should be uninstalled after the installation of the MS06-001 update.
Workarounds:
Disable or reset the file association for Windows Metafiles
Disabling or remapping Windows Metafile files to open a program other than the default Windows Picture and Fax Viewer may prevent exploitation via some attack vectors. Microsoft has suggested taking the following steps to disable shimgvw.dll in Microsoft Security Advisory (912840):
Microsoft has tested the following workaround. While this workaround will not correct the underlying vulnerability, it will help block known attack vectors. When a workaround reduces functionality, it is identified in the following section.
* `Un-register the Windows Picture and Fax Viewer (Shimgvw.dll) on Windows XP Service Pack 1; Windows XP Service Pack 2; Windows Server 2003 and Windows Server 2003 Service Pack 1`
To un-register Shimgvw.dll, follow these steps:
Click Start, click Run, type "regsvr32 -u %windir%\system32\shimgvw.dll" (without the quotation marks), and then click OK.A dialog box appears to confirm that the un-registration process has succeeded. Click OK to close the dialog box.
Impact of Workaround: The Windows Picture and Fax Viewer will no longer be started when users click on a link to an image type that is associated with the Windows Picture and Fax Viewer.
To undo this change, re-register Shimgvw.dll by following the above steps. Replace the text in Step 1 with "regsvr32 %windir%\system32\shimgvw.dll" (without the quotation marks).
Install an unofficial hotfix
Ilfak Guilfanov has provided a hotfix to intercept calls to the Escape function in GDI32.DLL. With this hotfix installed, calls to the obsolete SETABORTPROC GDI Escape will reportedly fail. This appears to prevent exploitation of this vulnerability. Note that this is not an official fix from Microsoft. Please take the appropriate risk assessment steps to determine whether such a hotfix should be installed in your environment.
Do not access Windows Metafiles from untrusted sources
Exploitation occurs by accessing a specially crafted Windows Metafile. By only accessing Windows Metafiles from trusted or known sources, the chances of exploitation are reduced.
Attackers may host malicious Windows Metafiles on web sites. In order to convince users to visit their sites, those attackers often use a variety of techniques to create misleading links including URL encoding, IP address variations, long URLs, and intentional misspellings. Do not click on unsolicited links received in email, instant messages, web forums, or internet relay chat (IRC) channels. Type URLs directly into the browser to avoid these misleading links. While these are generally good security practices, following these behaviors will not prevent exploitation of this vulnerability in all cases, particularly if a trusted site has been compromised or allows cross-site scripting.
Please note that Windows Metafile data may be saved with an extension other than WMF. A file with any extension that is associated with Windows Picture and Fax Viewer can be used to exploit this vulnerability. By default, Windows Picture and Fax Viewer is associated with the following file extensions:
BMP DIB GIF EMF JFIF JPE JPEG JPG PNG TIF TIFF WMFBlock access to Windows Metafiles at network perimeters
By blocking access to Windows Metafiles using HTTP proxies, mail gateways, and other network filter technologies, system administrators may also limit potential attack vectors.
Please be aware we have confirmed that filtering based just on the WMF file extensions or MIME type application/x-msMetafile will not block all known attack vectors for this vulnerability. Filter mechanisms should be looking for any file that Microsoft Windows recognizes as a Windows Metafile by virtue of its file header. Please check with your network vendor for updated signatures. WMF files can begin with various byte sequences such as:
01 00 09 00 ...
02 00 09 00 ...
D7 CD C6 9A ...Disable downloads in Internet Explorer
Disabling downloads in the Internet Explorer Internet Zone (or any zone used by an attacker) appears to help prevent exploitation of this vulnerability. This can be achieved by changing the Internet Zone security setting to “High.” Instructions for changing zone security settings can be found in the Malicious Web Scripts FAQ. While this change does not remove the vulnerability, it does help to prevent a common attack vector.
Vendor Information
181038
Filter by status: All Affected Not Affected Unknown
Filter by content: __ Additional information available
__ Sort by: Status Alphabetical
Expand all
Javascript is disabled. Click here to view vendors.
Google Affected
Notified: December 28, 2005 Updated: December 30, 2005
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
IrfanView Affected
Updated: January 04, 2006
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
Microsoft Corporation __ Affected
Notified: December 28, 2005 Updated: January 05, 2006
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
Addendum
Microsoft addresses this issue with the updates listed in Microsoft Security Bulletin MS06-001. This update disables support for SETABORTPROC in a WMF image.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23181038 Feedback>).
XnView Affected
Updated: January 04, 2006
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
Lotus Software __ Unknown
Notified: December 30, 2005 Updated: January 04, 2006
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
Addendum
Please see IBM Support Document 21227004.
If you have feedback, comments, or additional information about this vulnerability, please send us [email](<mailto:[email protected]?Subject=VU%23181038 Feedback>).
Mozilla, Inc. Unknown
Notified: December 28, 2005 Updated: December 28, 2005
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
The vendor has not provided us with any further information regarding this vulnerability.
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- <http://www.microsoft.com/technet/security/advisory/912840.mspx>
- <http://support.microsoft.com/kb/81497>
- <http://blogs.technet.com/msrc/archive/2006/01/13/417431.aspx>
- <http://www.hexblog.com/2005/12/wmf_vuln.html>
- <http://support.microsoft.com/kb/84984>
- <http://msdn.microsoft.com/library/en-us/gdi/prntspol_0d6b.asp>
- <http://windowssdk.msdn.microsoft.com/library/en-us/gdi/prntspol_9kok.asp>
- <http://msdn.microsoft.com/library/en-us/gdi/prntspol_0883.asp>
- <http://msdn.microsoft.com/library/en-us/dnanchor/html/gdi.asp>
- <http://msdn.microsoft.com/library/en-us/gdi/sec_gdi.asp>
- <http://msdn.microsoft.com/library/en-us/gdi/metafile_0hmb.asp>
- <http://msdn.microsoft.com/library/en-us/gdi/metafile_1xwz.asp>
- <http://isc.sans.org/diary.php?storyid=994>
- http://isc.sans.org/diary.php?rss&storyid=972
- <http://isc.sans.org/diary.php?storyid=975>
- <http://secunia.com/advisories/18255/>
- <http://www.securityfocus.com/bid/16074>
- <http://vil.mcafeesecurity.com/vil/content/v_137760.htm>
- <http://www.f-secure.com/weblog/archives/archive-122005.html#00000753>
- <http://www.symantec.com/avcenter/venc/data/bloodhound.exploit.56.html>
- <http://www.ciac.org/ciac/bulletins/q-085.shtml>
- <http://www.juniper.net/security/auto/vulnerabilities/vuln2830.html>
- <http://www.osvdb.org/displayvuln.php?osvdb_id=21987>
- <http://xforce.iss.net/xforce/alerts/id/211>
- <http://securitytracker.com/alerts/2005/Dec/1015416.html>
- <http://www.sysinternals.com/blog/2006/01/inside-wmf-backdoor.html>
Acknowledgements
This document was written by Jeffrey S. Havrilla and Will Dormann.
Other Information
| CVE IDs: | CVE-2005-4560 |
|---|---|
| Severity Metric: | 53.58 Date Public: |
References
blogs.technet.com/msrc/archive/2006/01/13/417431.aspx
isc.sans.org/diary.php?rss&storyid=972
isc.sans.org/diary.php?storyid=975
isc.sans.org/diary.php?storyid=994
msdn.microsoft.com/library/en-us/dnanchor/html/gdi.asp
msdn.microsoft.com/library/en-us/gdi/metafile_0hmb.asp
msdn.microsoft.com/library/en-us/gdi/metafile_1xwz.asp
msdn.microsoft.com/library/en-us/gdi/prntspol_0883.asp
msdn.microsoft.com/library/en-us/gdi/prntspol_0d6b.asp
msdn.microsoft.com/library/en-us/gdi/sec_gdi.asp
secunia.com/advisories/18255/
securitytracker.com/alerts/2005/Dec/1015416.html
support.microsoft.com/kb/81497
support.microsoft.com/kb/84984
vil.mcafeesecurity.com/vil/content/v_137760.htm
windowssdk.msdn.microsoft.com/library/en-us/gdi/prntspol_9kok.asp
www.ciac.org/ciac/bulletins/q-085.shtml
www.f-secure.com/weblog/archives/archive-122005.html#00000753
www.hexblog.com/2005/12/wmf_vuln.html
www.juniper.net/security/auto/vulnerabilities/vuln2830.html
www.microsoft.com/technet/security/advisory/912840.mspx
www.osvdb.org/displayvuln.php?osvdb_id=21987
www.securityfocus.com/bid/16074
www.symantec.com/avcenter/venc/data/bloodhound.exploit.56.html
www.sysinternals.com/blog/2006/01/inside-wmf-backdoor.html
xforce.iss.net/xforce/alerts/id/211
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.974 High
EPSS
Percentile
99.9%