What is a CVE: Meaning & Common Vulnerabilities and Exposures in Security

In this article we will understand what a CVE is, what information it contains and where it can be found. CVE is a fundamental concept in information security and the details of this information directly affect the business processes of modern organizations. Every day, many cybersecurity professionals discover and conduct research on new CVE, so it is important to have a good understanding of what it is.
- What is a CVE
- What is the Difference Between Vulnerabilities and Exposures?
- What Qualifies for a CVE?
- CVE Identifiers Understanding
- How Does Vulners Work With CVEs?
- CVE History
- Pros and Cons of CVEs
- How does the Global CVE system work?
- Why Should You Try the Vulners Database?
- Open CVE Databases & RSS
- How Many CVEs Are There?
- Conclusion
- FAQ
What is a CVE
The Common Vulnerabilities and Exposures (CVE) is a system that identifies all vulnerabilities in any software. To do this, a unique identifier is assigned to each vulnerability.
CVE was firstly launched in 1999 by the MITRE corporation and maintained by the National Cybersecurity FFRDC (Federally Funded Research and Development Center) to identify and categorize vulnerabilities in software. CVE provides organizations with free threat information to enhance their cybersecurity.
What is the Difference Between Vulnerabilities and Exposures?
A vulnerability is a weakness that can be used in a cyberattack to gain access to perform unauthorized actions on a computer system, or disrupt its default operation. The vulnerability allows an attacker to execute arbitrary code locally or remotely, installing malware, modifying sensitive data, etc. It is even possible to use a chain of vulnerabilities in combination to compromise the target system.
An exposure is a mistake that gives an attacker access to a system or computer network. Some of the biggest data breaches were caused by exposure rather than sophisticated cyberattacks.
What Qualifies for a CVE?
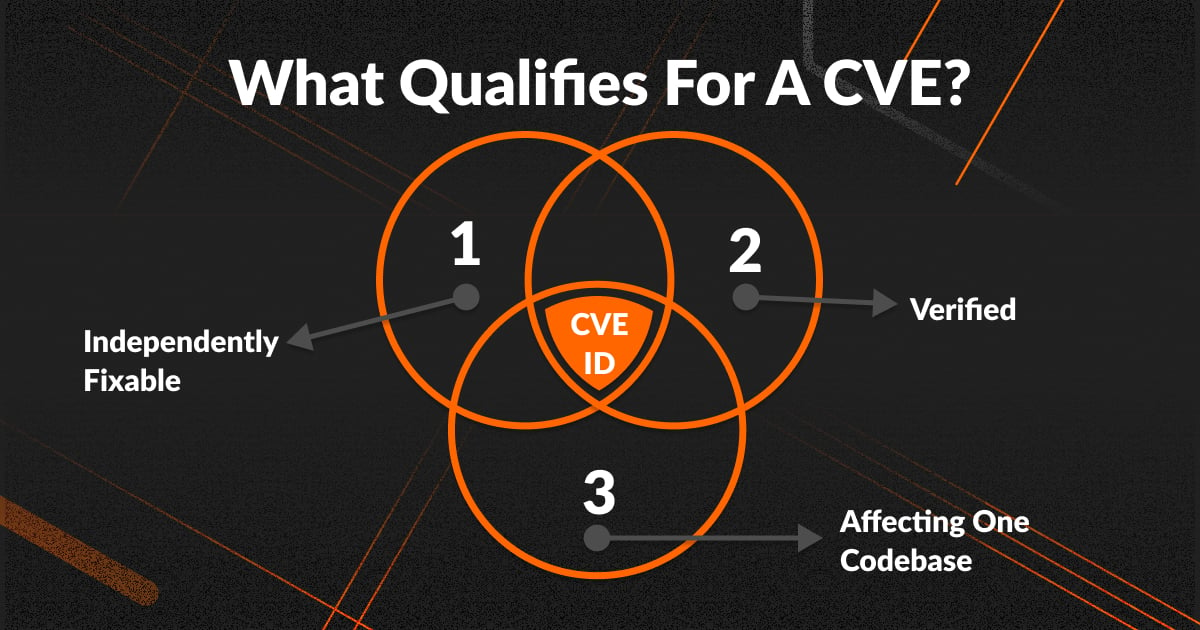
CVE IDs are assigned to flaws that meet a specific set of criteria:
1. Independently fixable
The flaw can be fixed independently of any other flaws.
2. Verified
The software or hardware vendor verified the bug and that it has a negative impact on its security. Or, the reporter have to share a vulnerability report that demonstrates negative impact of possible vulnerability AND that it violates the security policy of the affected system.
3. Affecting one codebase
Flaws that impact more than one product get separate CVEs. Otherwise, each affected codebase or product gets a unique CVE.
CVE Identifiers Understanding

How Does Vulners Work With CVEs?
Vulners provides the most complete information on the newest vulnerabilities. This is ensured by continuous monitoring of 200 different sources, information from which is correlated with each other. also, the enrichment of each vulnerability is used: mentions on Twitter, AI score, in the wilt or not etc. Also, based on this information through the Vulners API, it is possible to carry out a continuous process of vulnerability management based on the collected information: installed packages, security updates and software versions.
CVE History
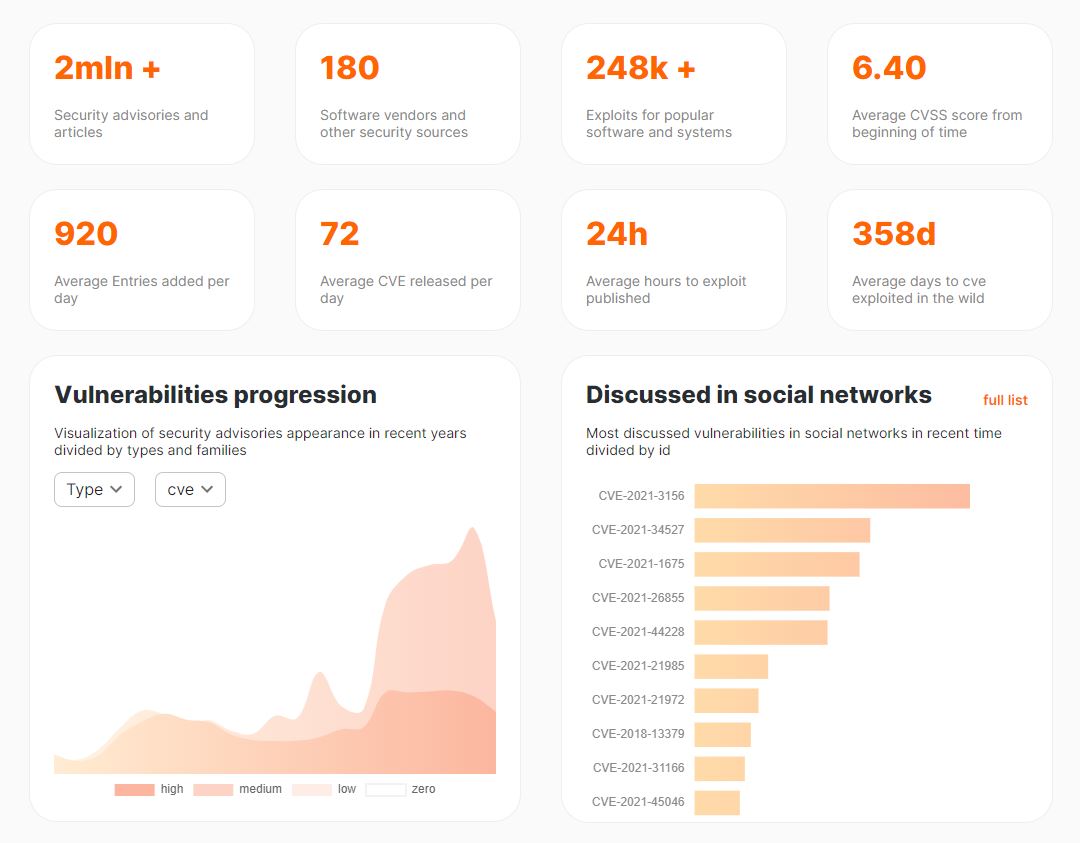
Vulners has an excellent historical heat map and statistics based on its own largest database of vulnerabilities:
Pros and Cons of CVEs
CVE identifier is not a perfect format for indicating vulnerabilities.
Pros:
- This is a universal identifier
- Transparent system for assigning an identifier for each vulnerability
- After assigning a CVE ID, the vendor releases an official fix
Cons:
- To assign an identifier, you must meet the conditions (see above)
- Attackers can start exploiting the vulnerability before assigning an identifier
- After assigning an identifier, a description of the details is not guaranteed for a long time, except for the name of the vulnerability and the software version
Limitations of CVE
The CVE is not intended to be used as a vulnerability database, so it does not initially contain sufficient information to run a comprehensive vulnerability management program. In addition to the CVE id, the entry contains only a brief description of the vulnerability and links to additional information about the CVE, such as recommendations from the software vendor.
How does the Global CVE system work?
Let's clarify some details a bit, where the vulnerability identifiers come from, who is involved in this process and why they do it.
Who Reports CVEs?
Anyone can report a CVE. Most commonly, researchers, white hat hackers, and vendors find and submit CVE reports to one of the CNAs. Many vendors actively encourage people to look for vulnerabilities as a "free" way to improve the security posture of their products. Many even offer bug bounties and other forms of benefits to encourage the community to test and find security flaws in their products.
What is the CVE Board?
The CVE Board is a list of contributors and organizations related to cybersecurity, research institutes, government organizations and many other security experts are also present. Additionally, there are individuals with the status of "Emeritus" who have made a really significant contribution. And you can find full list here.
What are CNAs and a Root CNA?
CVE identifiers are assigned by a CVE Numbering Authority (CNA). There are currently 104 CNAs in 18 countries including many household names like Microsoft, Adobe, Apple, Cisco, Google, Hewlett Packard Enterprise, Huawei, IBM, Intel, Mozilla, Oracle, Red Hat, Siemens, Symantec, VMWare, Atlassian, Autodesk, Cloudflare, Elastic, GitHub, Kubernetes, Netflix and Salesforce. You can see the full list of CVE numbering authorities here.
In many cases, a root CNA is when a large company like Apple publishes vulnerabilities in their products. In other cases, the root CNA may focus on open source vulnerabilities.
Where Can I Find all the Latest Versions of Vulnerability?
The latest version of the resume list can always be found at vulners.com. Even though the CVE list is publicly available, it can be difficult to determine which vulnerabilities affect your organization without additional tools. That's why many organizations are now using tools that track changes in the CVE list that affect them.
Why Should You Try the Vulners Database?
The Vulners team continuously expands and maintains the largest database of vulnerabilities. You should try Vulners if you want to keep up with the latest news in the world of cybersecurity, keep track of the latest vulnerabilities in your software, or are looking for an easy solution to build your own vulnerability management process.
Open CVE Databases & RSS
There are 2 main sources for listing CVEs: cve.mitre.org and nvd.nist.gov. There are a huge number of other sources where information about vulnerability appears earlier. Therefore, without additional tools, it can be difficult to determine which vulnerabilities affect your organization.
New CVE identifiers are added daily and getting up-to-date information is problematic. Despite all the difficulties, Vulners database continuously monitors almost 200 different sources using automation, robots, RSS and more.
How Many CVEs Are There?
Thousands of new CVEs appear every year. Since the launch of the CVE program in 1999, over 130,000 CVE IDs have been issued. Over the past few years, 12,000–15,000 new CVEs have been introduced annually.
There are several dashboards that provide CVE counts:
Conclusion
In the article, we analyzed what CVE is and showed how important timely information about vulnerabilities is. Vulners database was created to collect complete information about any vulnerability that the user receives as soon as the vendor publishes information about it. Also, if we analyze the information from the dashboards, we can conclude that the number of CVEs is increasing, which confirms the importance of the existence of a huge database of vulnerabilities from Vulners.
FAQ
What is the meaning of CVE?
CVE is short for Common Vulnerabilities and Exposures, which means a list of publicly disclosed security flaws.
What is the Difference Between CVE and CVSS?
CVE is a vulnerability identifier.
CVSS score or Common Vulnerability Scoring System is an open standard used to calculate quantitative vulnerability scores.
What is a cybersecurity vulnerability?
A cybersecurity vulnerability is a vulnerability of a host or computer system that cybercriminals can use to compromise an IT resource, advance the path of attack and achieve their goals.
What is a cybersecurity exposure?
Exposure is an error that gives an attacker access to a system or computer network. Some of the biggest data leaks were caused by exposure, not sophisticated cyberattacks.
Why is CVE useful?
CVE is a universal identifier that is convenient to use in various computer systems.
Who maintains the CVE database?
There are many vendors of well-known products, various cybersecurity experts and researchers. Also, there are ethical hackers and bug bounty, who are paid to hunt for vulnerabilities in systems and resources.
